Cisco IOS Firmware Upgrade
This article is about firmware upgrade in Cisco IOS devices. Before upgrading IOS, you should make sure to obtain the latest IOS version. You can do this by logging in here and selecting your device type and version. Once that is done, the downloaded file should be transferred to a flash drive of the device, usually via TFTP or FTP.
To upgrade firmware using Network Configuration Manager, you can create the corresponding Configlet commands and upgrade firmware in multiple devices.
If you don't have NCM installed, please click here to download and install the application. Also, make sure to download the Cisco IOS software image onto the TFTP Server in Network Configuration Manager.
Steps to upgrade firmware in Cisco IOS devices
- Transfer the file from the TFTP server to the flash memory of the switch. This can be done by issuing the copy command on the switch.
- Check if the file has been transferred successfully to the router by executing the commands given below:
- Configure the switch to load the new IOS version. If we reboot the system now, the old IOS file will be loaded.
- Instruct the switch to load the new file. The easiest way to do it is by using the boot system command.
- Save the configuration and reload the device. We can verify that the newer version of IOS is being used by issuing the show version command:
Router#copy tftp flash
Address or name of remote host []? 10.0.0.100
Source filename []? c2960-lanbasek9-mz.150-2.SE4.bin
Destination filename [c2960-lanbasek9-mz.150-2.SE4.bin]?
Accessing tftp://10.0.0.100/c2960-lanbasek9-mz.150-2.SE4.bin....
Loading c2960-lanbasek9-mz.150-2.SE4.bin from 10.0.0.100:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
[OK - 4670455 bytes]
4670455 bytes copied in 3.079 secs (121951 bytes/sec)
Router#
Router#show flash:
Directory of flash:/
1 -rw- 4414921 c2960-lanbase-mz.122-25.FX.bin
3 -rw- 4670455 c2960-lanbasek9-mz.150-2.SE4.bin
2 -rw- 1052 config.text
64016384 bytes total (54929956 bytes free)
Router#reload
Proceed with reload? [confirm]
C2960 Boot Loader (C2960-HBOOT-M) Version 12.2(25r)FX, RELEASE SOFTWARE (fc4)
Cisco WS-C2960-24TT (RC32300) processor (revision C0) with 21039K bytes of memory.
2960-24TT starting...
Base ethernet MAC Address: 000C.8536.AA3B
Router(config)#boot system c2960-lanbasek9-mz.150-2.SE4.bin
Router#show version
Cisco IOS Software, C2960 Software (C2960-LANBASEK9-M), Version 15.0(2)SE4, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2013 by Cisco Systems, Inc.
Compiled Wed 26-Jun-13 02:49 by mnguyen
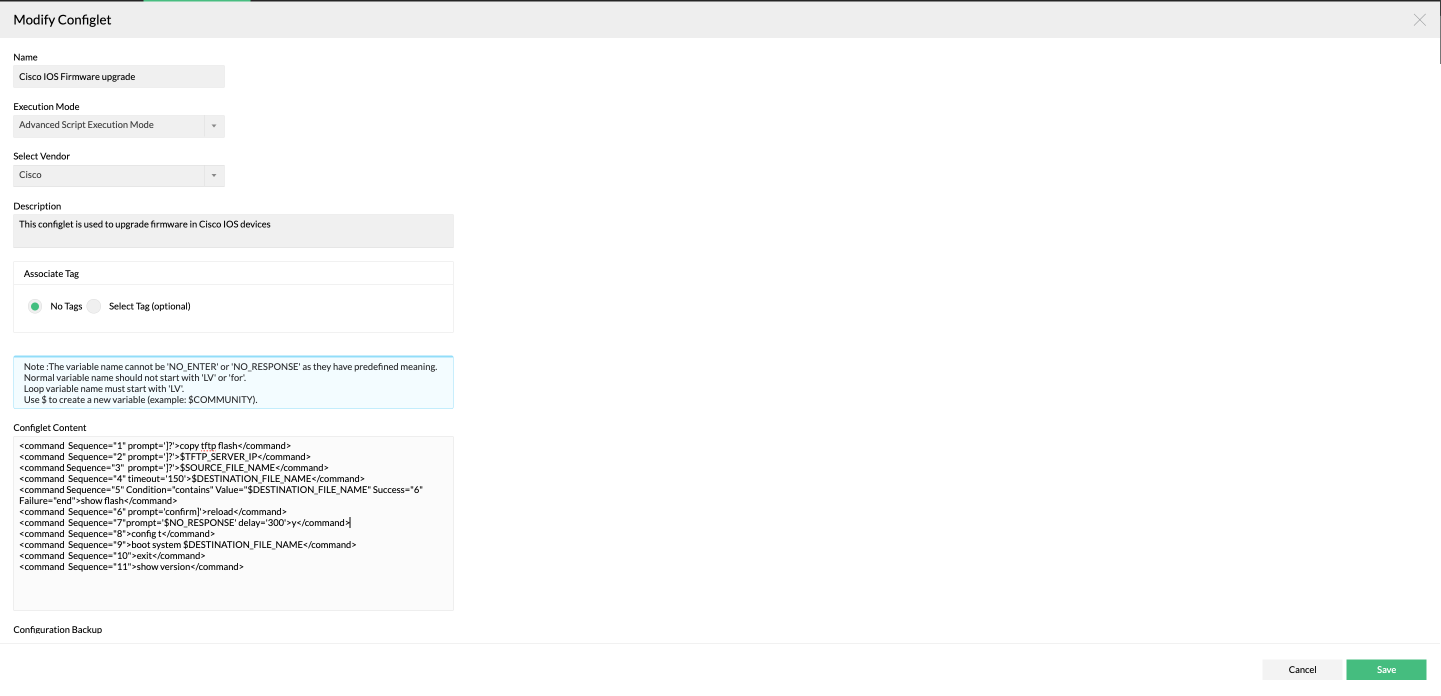
The corresponding configlet can be created in NCM application as shown in below screenshot.
Also you can click the below button to download the Configlet as XML and import it into NCM application using file import option.
| Configlet Name | Cisco IOS Firmware Upgrade |
|---|---|
| Description | This configlet is used to upgrade firmware in Cisco IOS devices. |
| Execution Mode | Advanced Script Execution Mode |
| Configlet Content | <command Sequence="1" prompt=']?'>copy tftp flash</command> |
Check out firmware vulnerability to identify potential vulnerabilities in your network and effective ways to fix them.
Thank you for your feedback!