 Free Edition
Free Edition - Quick Links
- Solutions
- Features
- Integrated compliance management
- Real-time Active Directory change auditing
- File Server Data Security Governance
- User & Entity Behavior Analytics
- AD object-based reporting
- File integrity monitoring
- Privileged user and session activity monitoring
- SQL and IIS auditing
- Network device auditing
- Endpoint log auditing
- Microsoft 365 auditing
- Exchange Server auditing
- Cloud log alerting and incident management
- VPN monitoring
- IT Compliance
- AWS Security
- Salesforce Security
- Login activity monitoring
- Content activity monitoring
- Report activity monitoring
- User activity monitoring
- Salesforce log analysis
- Apex execution monitoring
- Audit Trail Reports
- Recent custom object event reports
- Manage user events reports
- User management settings reports
- Application event reports
- Connected apps event reports
- Salesforce threat management
- URI monitoring
- API calls monitoring
- Microsoft Azure Security
- Google Cloud Platform Security
- Google Cloud log retention
- Google Cloud platform log management
- Google Cloud storage monitoring
- Google Cloud Filestore Monitoring
- Google Cloud compute monitoring
- Google Cloud network security monitoring
- Google Cloud VPC activity monitoring
- Google Cloud functions monitoring
- Google Cloud app engine monitoring
- What's new in cloud version
- Integration & partnership
- Related Products
- EventLog Analyzer Real-time Log Analysis & Reporting
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Hybrid AD, cloud, and file auditing and security
- ADSelfService Plus Self-Service Password Management
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Active Directory Backup & Recovery Tool
- SharePoint Manager Plus SharePoint Management and Auditing Solution
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- AD360 Integrated Identity & Access Management
- AD Free Tool Active Directory FREE Tools
Every organization has its own unique security and compliance goals. In today’s security landscape, visibility is only as valuable as its relevance. Most security dashboards are crowded with data points—including login attempts, threat alerts, and policy violations—but often lack the flexibility to reflect your organization’s priorities. This disconnect between generic dashboards and actual operational needs leads to wasted time, slower investigations, and missed insights.
As IT environments become more complex, security teams are increasingly relying on external telemetry sources like endpoint protection platforms, vulnerability scanners, and threat intelligence feeds. However, integrating these into a unified view often requires switching between portals or manual correlation; activities that add friction to already time sensitive workflows.
What if your security platform could adapt to you? What if it could act not just as a monitoring layer, but a custom built control panel tailored to your exact environment, risk model, and third party integrations?
This is exactly what custom widgets do.
What are custom widgets?
Custom widgets are user-built, embeddable components that let you extend a platform’s default capabilities by introducing custom views, third-party integrations, and tailored visualizations.
These widgets can typically be developed using frontend languages like JavaScript and integrated into the platform through APIs or SDKs. Unlike standard widgets, which are bound by predefined data types and structures, custom widgets give you the freedom to fetch, manipulate, and render data from virtually any source, internal or external.
Custom widgets serve a wide range of purposes:
- Displaying real-time metrics from external platforms (like EDRs, cloud firewalls, or SaaS apps)
- Overlaying contextual intelligence (like Geo IP data or CVE threat scores)
- Embedding search driven dashboards
- Creating executive summaries and compliance views
Enhance your security dashboards with Log360’s custom widgets
Log360 is a comprehensive security platform designed to help you secure your IT environments. By unifying log management, security analytics, threat detection, and incident response, it empowers security teams to gain end-to-end visibility, respond to incidents swiftly, and ensure continuous compliance.

Every dashboard in Log360 is customizable, enabling SOCs to tailor views according to operational priorities, investigative needs, or regulatory requirements. Whether it is real-time monitoring, forensic analysis, or compliance auditing, Log360 ensures that security teams have access to the right data, at the right time, with the right context.
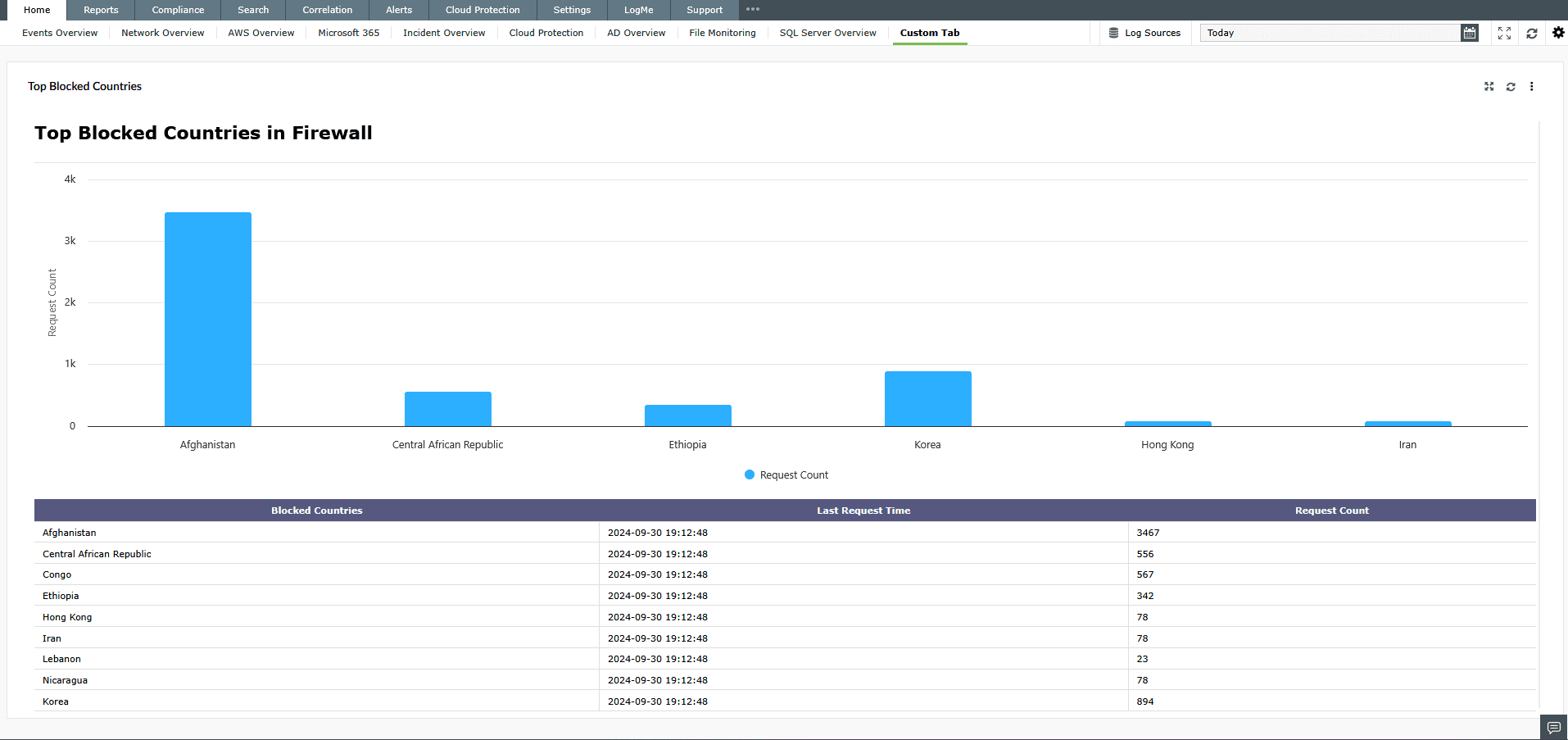
Building tailored dashboards with custom widgets in Log360
To empower deeper operational flexibility, Log360 provides a custom widget framework that allows security teams to design their own data visualizations and investigation panels. Custom widgets can be created and embedded into any dashboard across the product.
Users can define custom widgets by specifying the log source, constructing queries based on specific fields, setting dynamic filters, and choosing output formats such as tables, charts, counters, or graphs. This allows security teams to monitor highly specific KPIs, correlate event data across systems, or visualize security events exactly the way their workflows demand.
A critical prerequisite when building custom widgets that involve third-party applications is that these applications must expose open APIs. Log360 uses these APIs to query, fetch, and visualize external data seamlessly. Whether it's pulling email metadata from security gateways like Mimecast, fetching device posture information from endpoint solutions like Endpoint Central, or retrieving access events from SaaS apps, the presence of an accessible API ensures that external telemetry can be integrated natively into Log360’s dashboards.
Use case: Accelerating threat investigations with custom widgets
One of the most impactful uses of custom widgets within Log360 is during threat investigations.
Imagine a scenario where a suspicious file hash, such as a known malware SHA256, is flagged in an initial alert.
During such incidents, SOCs need to identify:
- Where else is this hash present inside the network (on which devices)
- Who else received or sent this file through email
This requires manually running queries on multiple systems separately, which is time consuming.
Leveraging Log360’s custom widget framework, an analyst can create a dashboard panel that pulls real-time data from an email security solution like Mimecast (through its open APIs).
First, a custom widget is configured to pull live file inventory data from Endpoint Central, targeting the specific hash. This widget retrieves key fields such as device name, associated user, file path, detection timestamp, and current file status (e.g., quarantined, active). Also, the Mimecast’s email security platform is queried via its open APIs to identify any emails where the same hash appears as an attachment. This surfaces metadata such as sender address, recipient list, email subject line, delivery time, and attachment status.
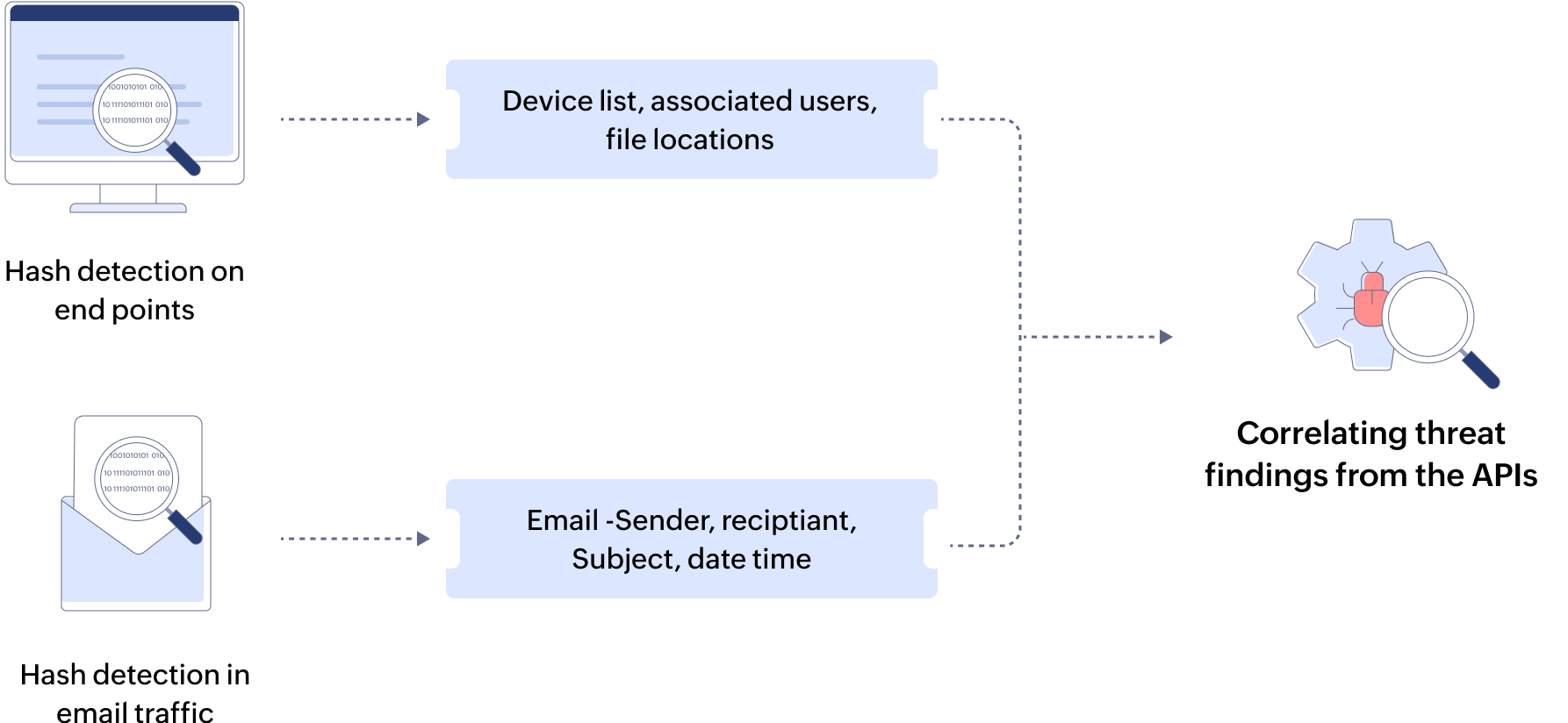
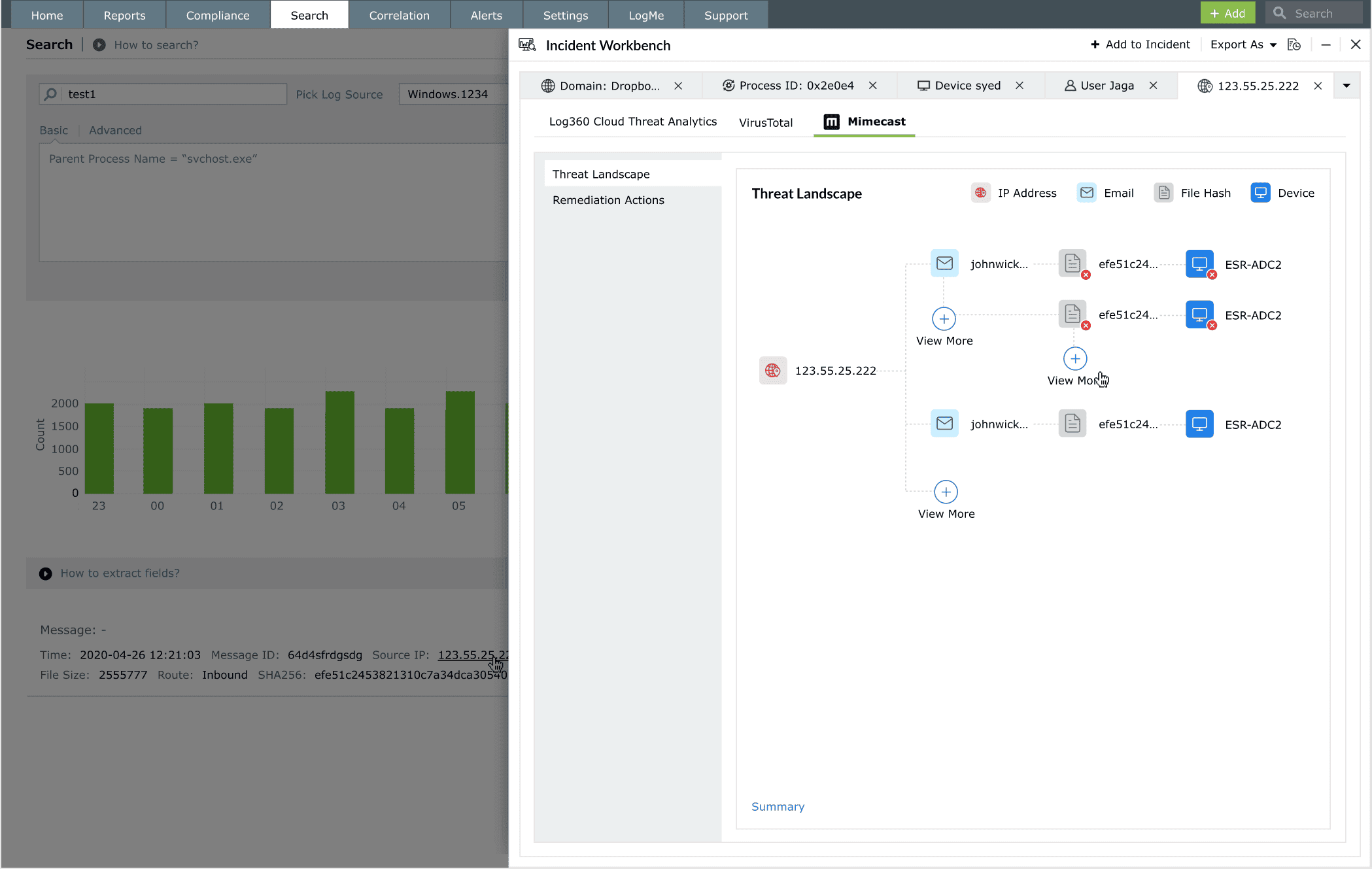
Both widgets are placed within the same investigation dashboard, allowing the analyst to immediately view a correlated map of endpoint infections and email distribution trails. Analysts can visually pivot between endpoints and users, identify lateral movement risks, and prioritize systems for isolation based on infection depth.
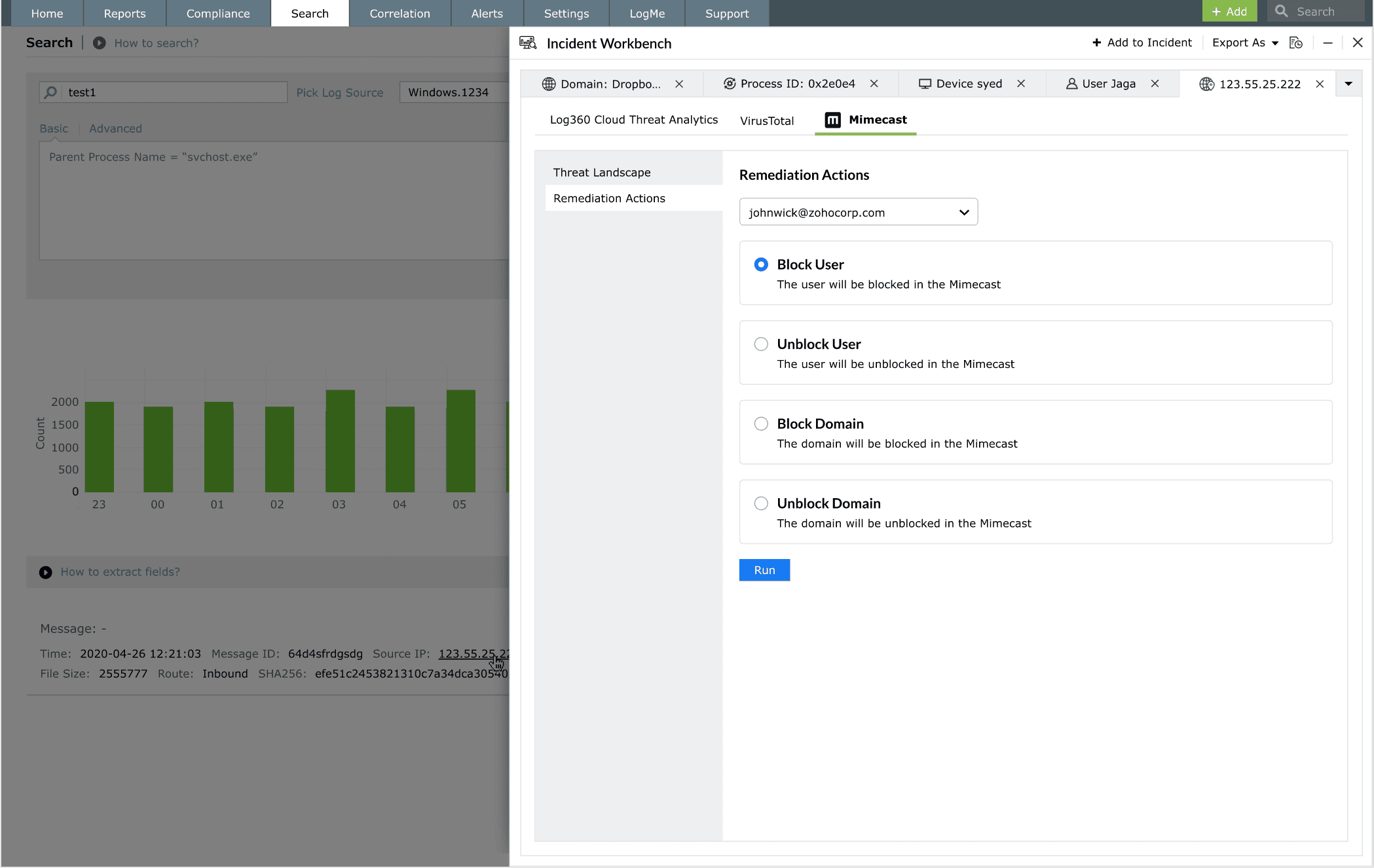
Log360’s Incident Workbench empowers analysts to not only investigate threats but also initiate immediate remediation actions.
- Block User: Immediately block a compromised or suspicious user account at the email gateway level.
- Unblock User: Restore access if a user is later verified to be safe.
- Block Domain: Prevent all future communications from a suspicious or malicious domain.
- Unblock Domain: Re-enable communications if necessary.
The remediation panel is tightly coupled with the investigation context, enabling security teams to take swift, decisive actions directly from the Log360's console.
Why use custom widgets?
1. Align dashboards with context and build role based views
Every team tracks different metrics. A compliance team might focus on audit logs and policy changes, while a threat hunting team might track lateral movement or privilege escalation attempts. Custom widgets allow you to create views tailored to specific stakeholders:
- SOC analysts can get threat intelligence and detection context
- CISOs can get visual KPIs for risk trends and SLA adherence
- IT admins can track configuration drifts or system health
- Compliance officers can monitor audit trail gaps or control violations
2. Break data silos
Security data rarely exists in isolation. You likely use multiple platforms: email security, DLP, network monitoring, vulnerability scanning, etc. Custom widgets allow you to surface data from these disparate sources into one view, closing the gap between detection and context.
3. Accelerate investigation and response
By embedding custom widgets into investigation panels, such as an Incident Workbench, you give analysts instant access to supporting context, including IP reputation, user risk score, asset inventory data, right alongside the alert. This reduces investigation time and improves decision-making.




