Key features
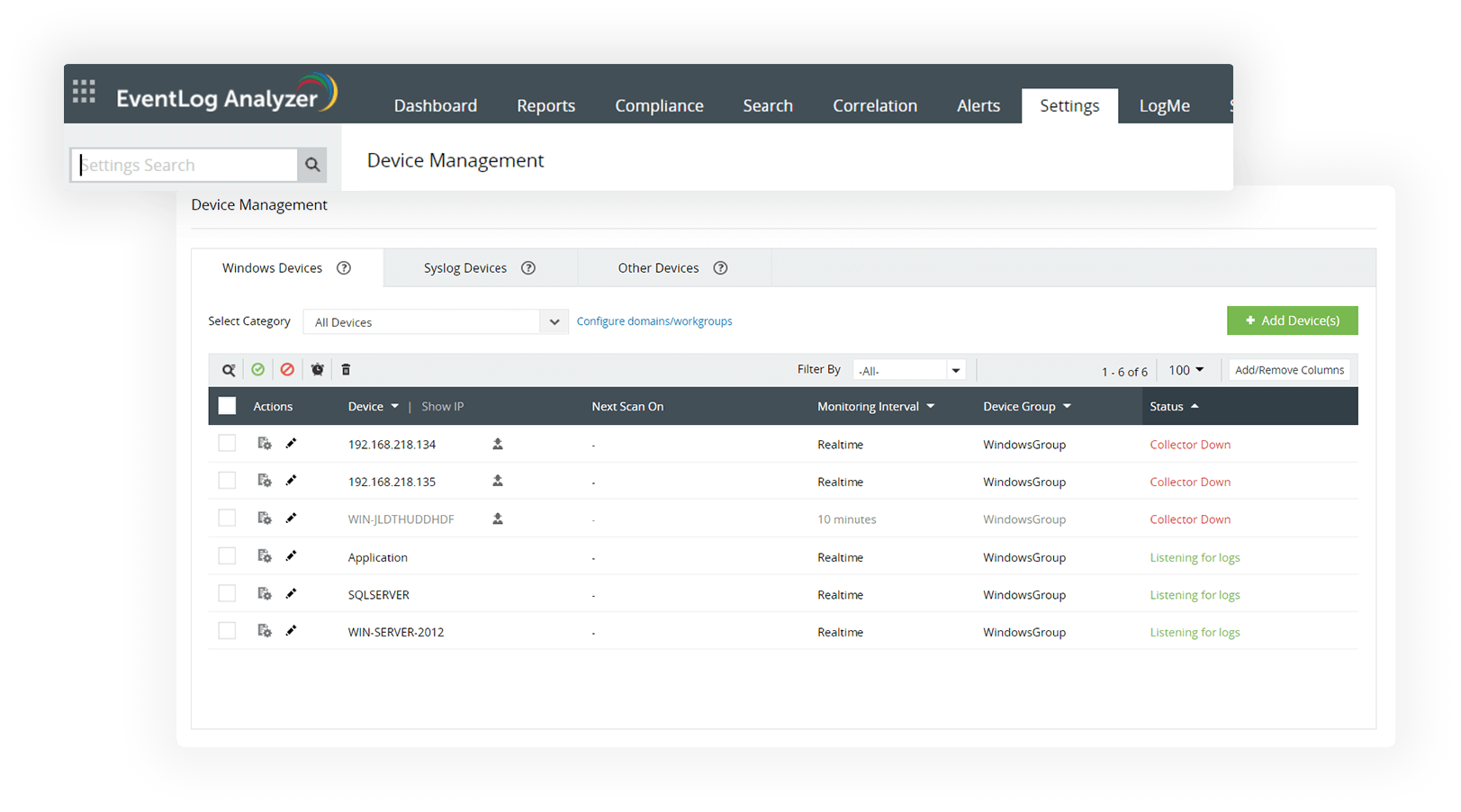
Comprehensive log collection
Leave no entity in your network unmonitored with ManageEngine EventLog Analyzer's agent-based and agentless methods of log collection. The centralized log management solution offers out-of-the-box support to over 750 log sources, which includes Windows systems, Unix and Linux systems, applications, servers, routers, switches, and IDS/IPS. The custom log parser of EventLog Analyzer parses and analyzes any human readable log format.
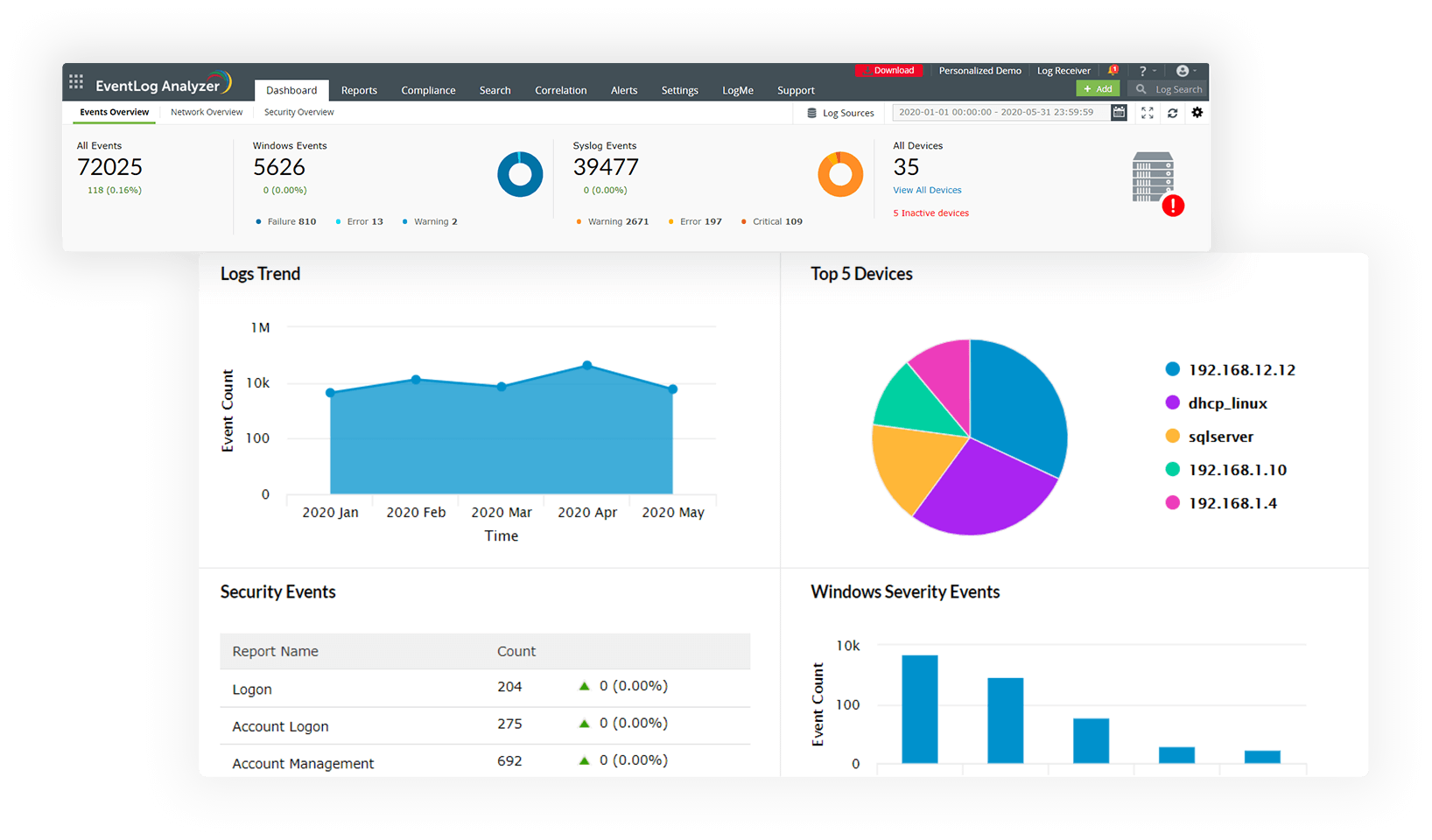
In-depth log analysis
Gain actionable insights from your network logs with the in-depth analysis and auditing capabilities of EventLog Analyzer. The security log file management tool parses, correlates, analyzes, searches, and archives log data to meet the security and auditing needs of the organization.
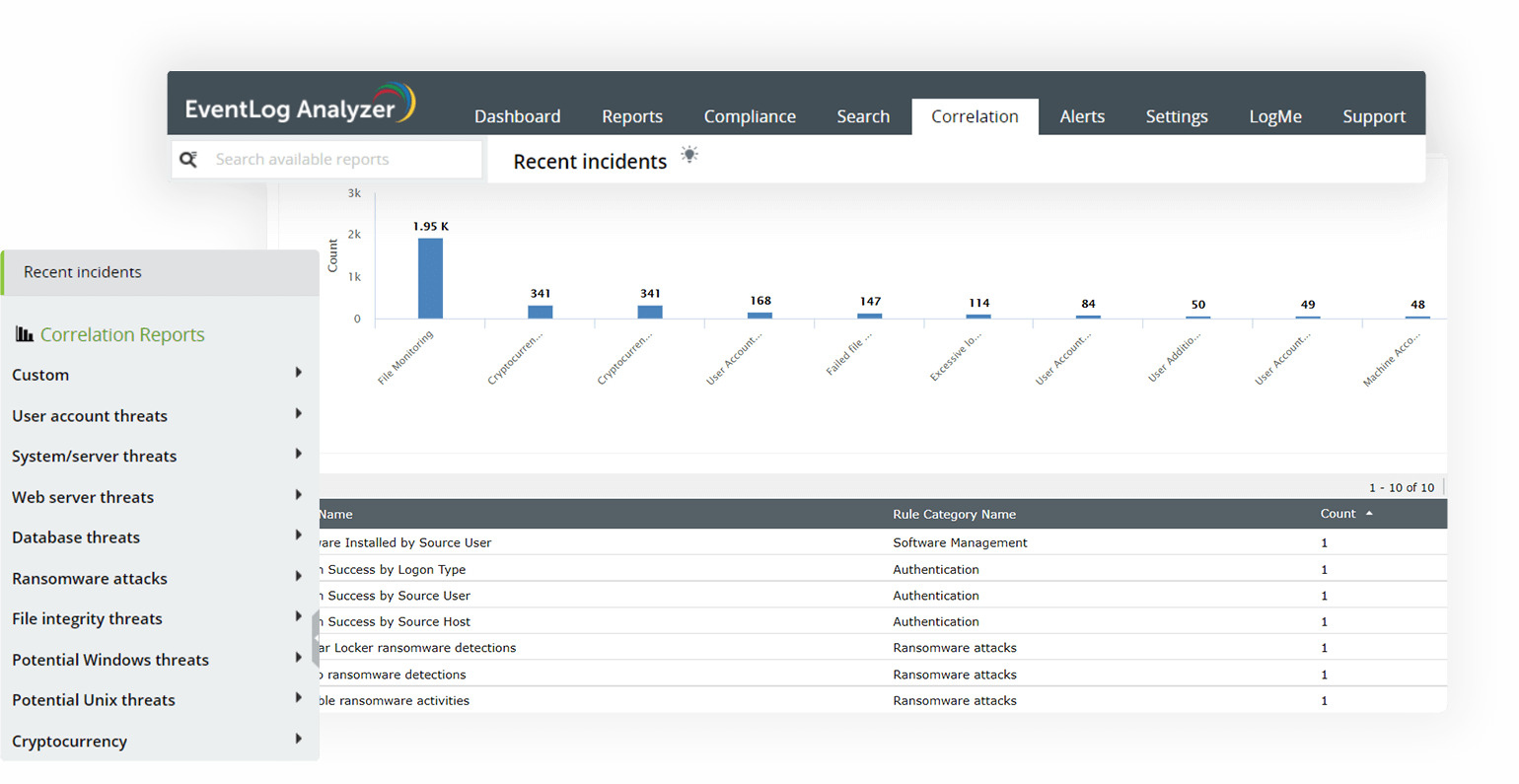
Complex log correlation
Detect malicious patterns by correlating log data from different log sources. Event correlation can detect security threats, anomalous user activities, or cyber attacks, which usually go unnoticed when viewed as a single activity. EventLog Analyzer has over 30 predefined correlation rules and a drag-and-drop custom correlation builder to detect cyber attacks such as brute force attacks, account lockouts, SQL injection, web server attacks, and more.
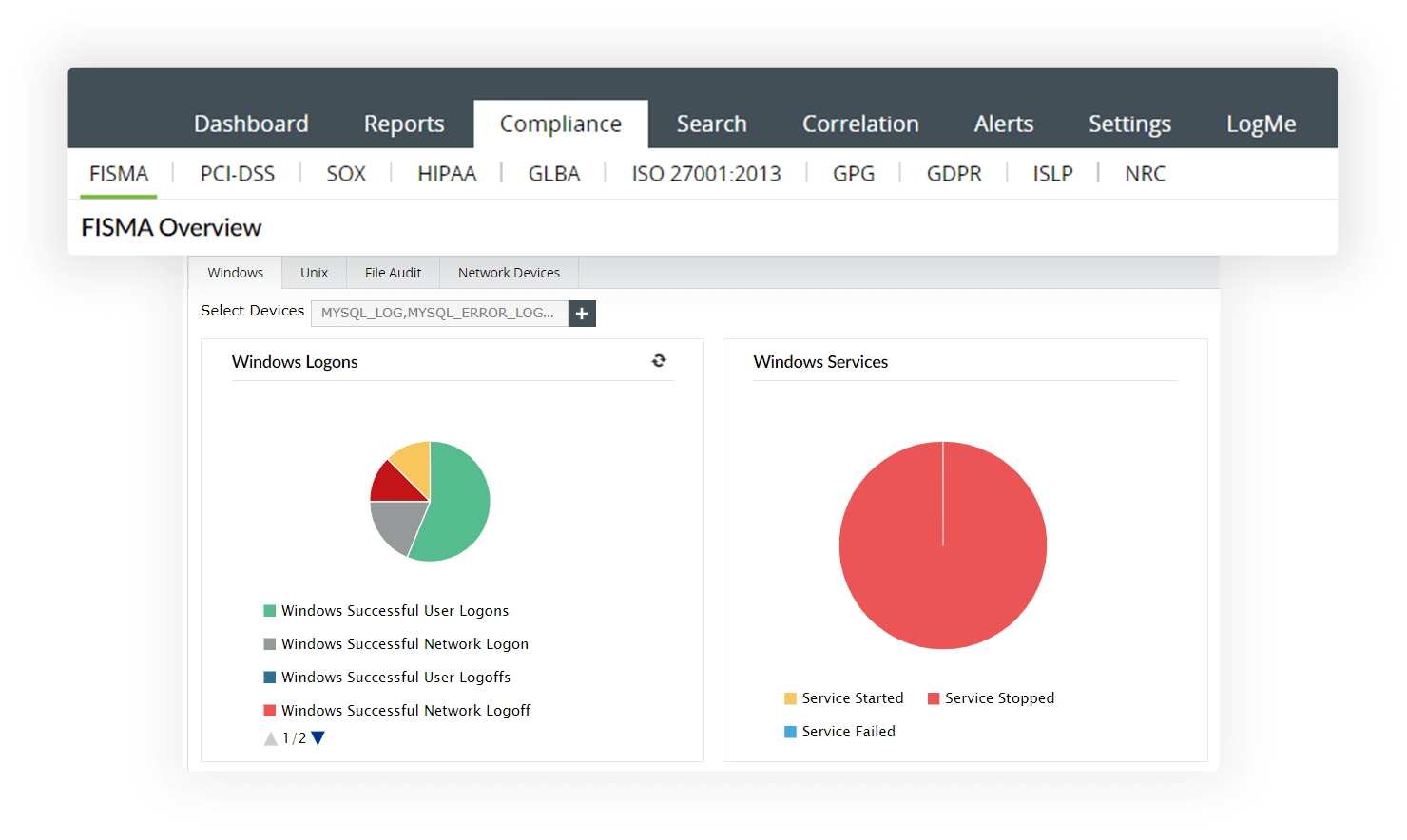
Integrated compliance management
Meet the IT compliance mandates of your organization with absolute ease with the incident and response management console. EventLog Analyzer provides audit-ready reports for all the major regulatory mandates, including PCI-DSS, SOX, HIPAA, GDPR, FISMA, and ISO 27001. This solution generates custom reports to address internal audit policies.
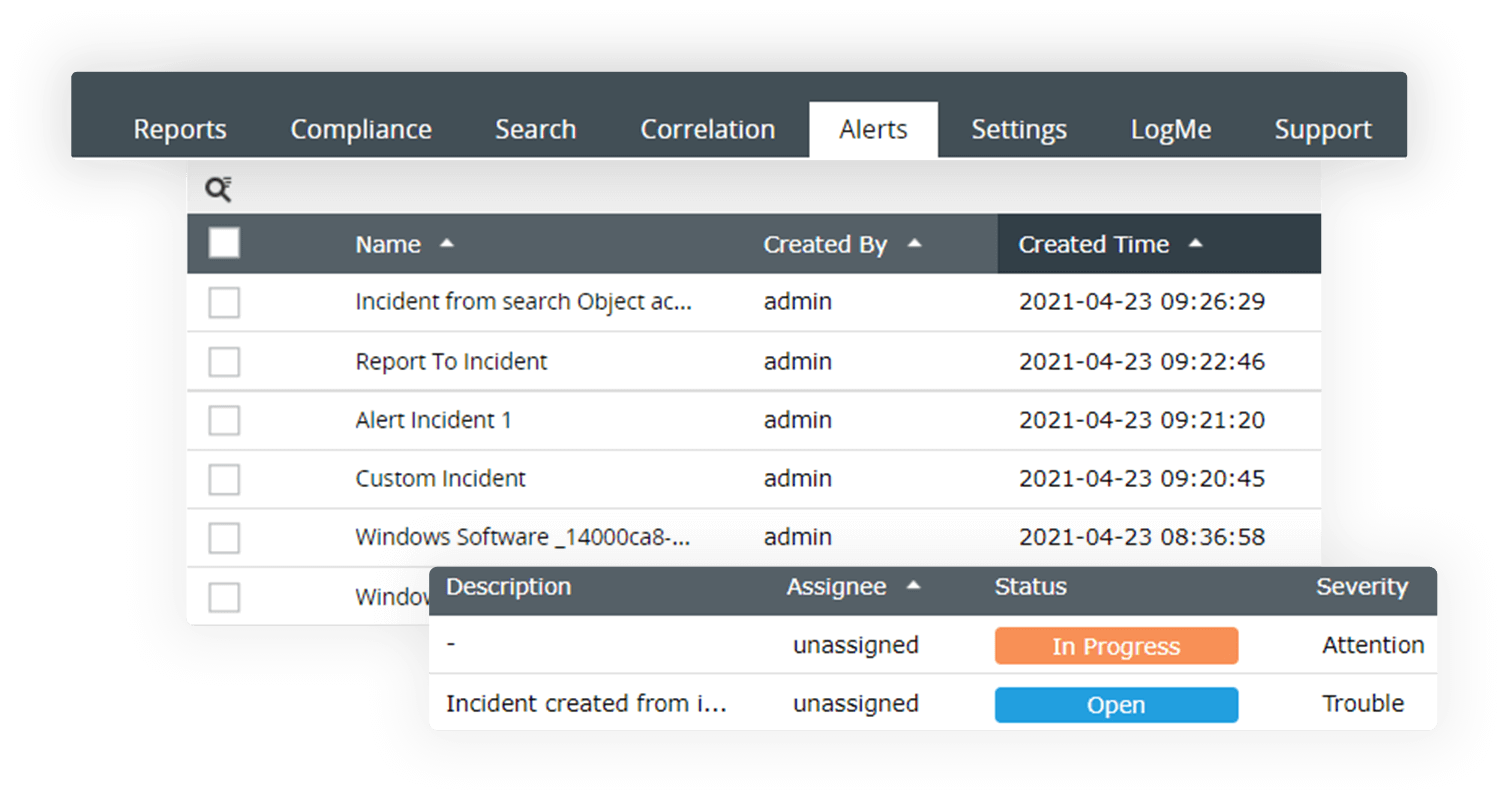
Automated incident management
Automatically respond to security events a by associating predefined and custom workflows with every detected incident. Raise and manage tickets for security incidents and automatically assign them to security analysts to speed up the resolution process. EventLog Analyzer integrates with IT help desk software such as ManageEngine ServiceDesk Plus, ServiceNow, JIRA, ZenDesk, and others for centralizing incident management process.