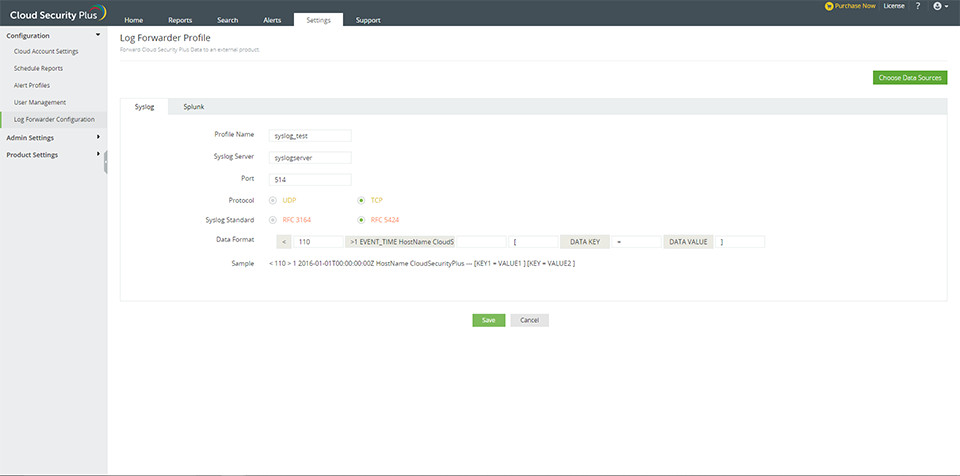
Log forwarder configuration
The SIEM integration option allows you to forward log data from Cloud Security Plus to an external SIEM product or to a Syslog server in real time.
Forwarding collected logs to a Syslog server
Syslog is the event logging service in unix systems.You may also use this setting to forward to your SIEM's UDP or TCP receiver.
Configuring a Syslog Server
Syslog daemon runs by default in UDP, port 514.
The default settings can be modified in its configuration file/etc/syslog.conf. Restart Syslog daemon for the changes to take effect.
Steps to enable log forwarding to Syslog server in Cloud Security Plus
- Navigate to Settings → Configuration → Log Forwarder Configuration → Syslog.
- Enter the profile name and Syslog server name. Ensure that the Syslog server is reachable from the Cloud Security Plus server.
- Enter the Syslog port number and choose the protocol.
- Choose Syslog standard and data format as required by your SIEM Parser.
- Choose the data sources
- Click Save.
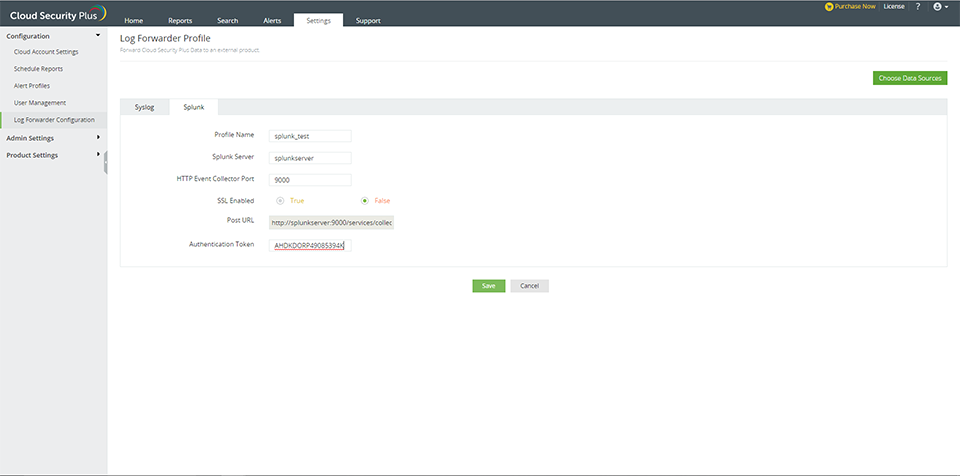
Forwarding collected logs to an external SIEM product : Splunk HTTP
Configuring Splunk HTTP event collector
- Navigate to Settings → Data Inputs → Http Event Collector → Global Settings.
Note: The Http port number and SSL settings can be customized in the Global Settings page.
- Enable All tokens. Restart your Splunk server.
- Click New Token in the Http Event Collector page, provide a name for the token(Preferably Cloud Security Plus) and leave the rest to the default values(Customize if required).
- Save the configuration and a token value will be generated. This token needs to be provided in the Cloud Security Plus configuration.
Steps to enable log forwarding to Splunk in Cloud Security Plus
- Navigate to Settings → Configuration → Log Forwarder Configuration → Splunk.
- Enter the profile name and Splunk server name. Ensure that the Splunk server is reachable from the Cloud Security Plus server.
- Enter the Splunk port number and enable/disable SSL.
- Enter the authentication token in the given field.
- Choose the data sources.
- Click Save.