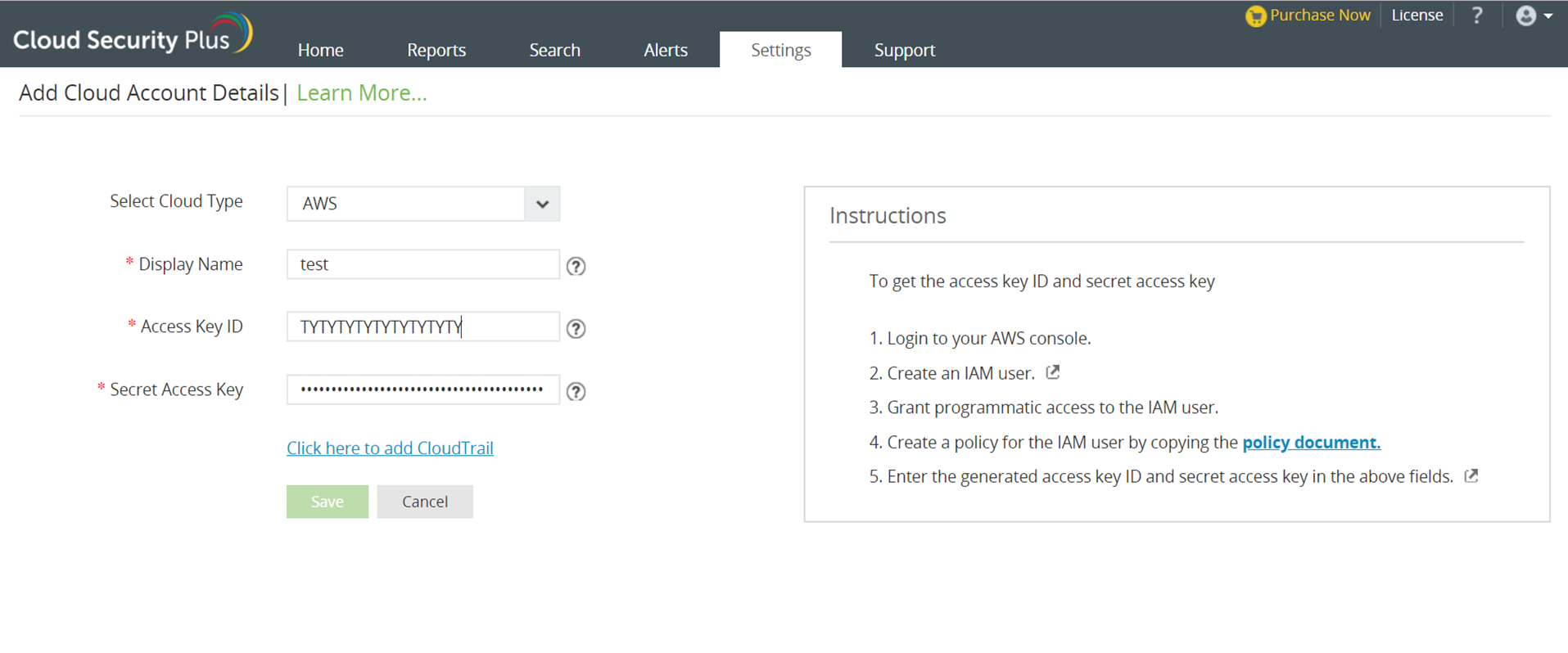
To monitor your AWS environment, Cloud Security Plus requires a valid IAM user with necessary permissions. The solution will use the designated IAM user to collect logs from your AWS environment.
Note: Cloud Security Plus supports all AWS regions, except the AWS China (Beijing) region.
An IAM user is an entity that you create in AWS to represent the person or service that uses it to interact with AWS
To create a new IAM user, follow these steps.
The generated access key and secret key pair should be used inside Cloud Security Plus to configure the AWS account.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1486278063000",
"Effect": "Allow",
"Action": [
"cloudtrail:DescribeTrails",
"cloudtrail:GetTrailStatus",
"cloudtrail:CreateTrail",
"cloudtrail:StartLogging",
"cloudtrail:StopLogging"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1486278045000",
"Effect": "Allow",
"Action": [
"s3:GetBucketTagging",
"s3:PutBucketLogging",
"s3:GetBucketLogging",
"s3:PutBucketPolicy",
"s3:CreateBucket",
"s3:ListBucket",
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:DeleteBucket",
"s3:GetBucketPolicy",
"s3:ListAllMyBuckets",
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1486278214000",
"Effect": "Allow",
"Action": [
"sns:GetEndpointAttributes",
"sns:GetSubscriptionAttributes",
"sns:GetTopicAttributes",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTopics",
"sns:Publish",
"sns:Unsubscribe",
"sns:SetTopicAttributes",
"sns:DeleteTopic",
"sns:CreateTopic",
"sns:Subscribe",
"sns:ConfirmSubscription",
"sns:SetSubscriptionAttributes",
"sns:AddPermission"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1486278276000",
"Effect": "Allow",
"Action": [
"sqs:DeleteMessage",
"sqs:GetQueueAttributes",
"sqs:GetQueueUrl",
"sqs:ReceiveMessage",
"sqs:SendMessage",
"sqs:PurgeQueue",
"sqs:CreateQueue",
"sqs:DeleteQueue",
"sqs:SetQueueAttributes",
"sqs:AddPermission"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1490256161000",
"Effect": "Allow",
"Action": [
"iam:GenerateCredentialReport",
"iam:GetAccountAuthorizationDetails",
"iam:GetCredentialReport"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1490256161001",
"Effect": "Allow",
"Action": [
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeAccountLimits",
"elasticloadbalancing:ModifyLoadBalancerAttributes",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeTags"
],
"Resource": [
"*"
]
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1486278063000",
"Effect": "Allow",
"Action": [
"cloudtrail:DescribeTrails",
"cloudtrail:GetTrailStatus"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1486278045000",
"Effect": "Allow",
"Action": [
"s3:DeleteObject",
"s3:GetObjectAttributes",
"s3:PutObject",
"s3:GetObject",
"s3:PutBucketLogging",
"s3:DeleteBucket",
"s3:PutObjectAcl",
"s3:ListBucket",
"s3:CreateAccessGrantsInstance",
"s3:GetBucketAcl",
"s3:ListAllMyBuckets",
"s3:PutBucketPolicy",
"s3:GetBucketLocation",
"s3:GetDataAccess",
"s3:GetBucketPolicy",
"s3:CreateAccessPoint",
"s3:GetBucketTagging",
"s3:GetBucketLogging",
"s3:CreateAccessGrant",
"s3:PutBucketAcl",
"s3:GetObjectAcl",
"s3:CreateBucket"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1486278214000",
"Effect": "Allow",
"Action": [
"sns:GetEndpointAttributes",
"sns:GetPlatformApplicationAttributes",
"sns:GetSMSAttributes",
"sns:GetSubscriptionAttributes",
"sns:GetTopicAttributes",
"sns:ListEndpointsByPlatformApplication",
"sns:ListPhoneNumbersOptedOut",
"sns:ListPlatformApplications",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTopics",
"sns:Publish"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1486278276000",
"Effect": "Allow",
"Action": [
"sqs:DeleteMessage",
"sqs:GetQueueAttributes",
"sqs:GetQueueUrl",
"sqs:ListQueues",
"sqs:ReceiveMessage",
"sqs:SendMessage"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1490256161000",
"Effect": "Allow",
"Action": [
"iam:GenerateCredentialReport",
"iam:GetAccountAuthorizationDetails",
"iam:GetCredentialReport"
],
"Resource": [
"*"
]
},
{
"Sid": "Stmt1490256161001",
"Effect": "Allow",
"Action": [
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeLoadBalancerAttributes",
"elasticloadbalancing:DescribeAccountLimits",
"elasticloadbalancing:ModifyLoadBalancerAttributes",
"elasticloadbalancing:DescribeTags"
],
"Resource": [
"*"
]
}
]
}
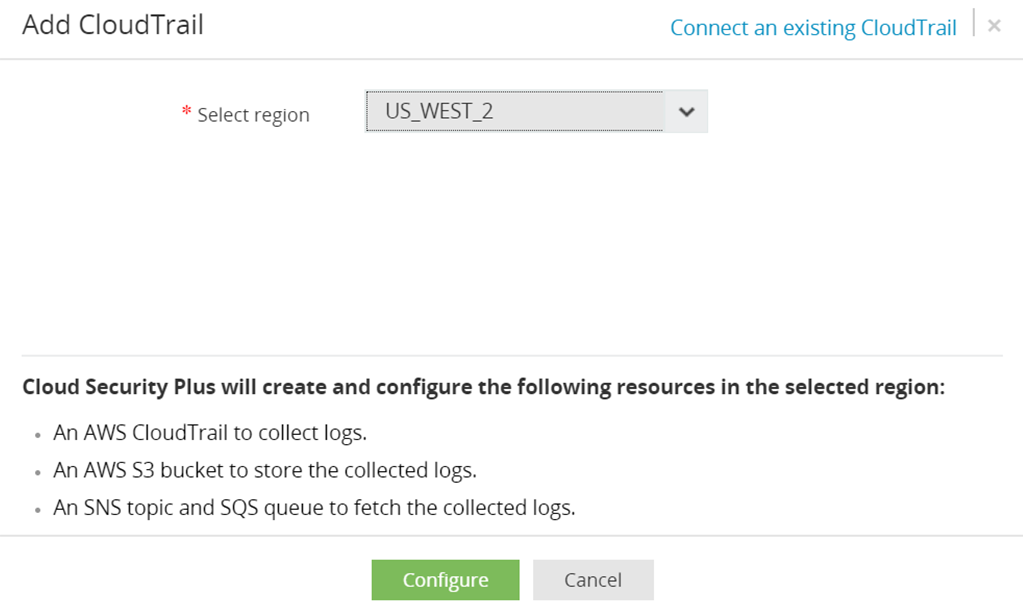
Note: Cloud Security Plus will create the following resources:
To setup logging for your AWS environment, refer S3 server access logging and ELB access logging .