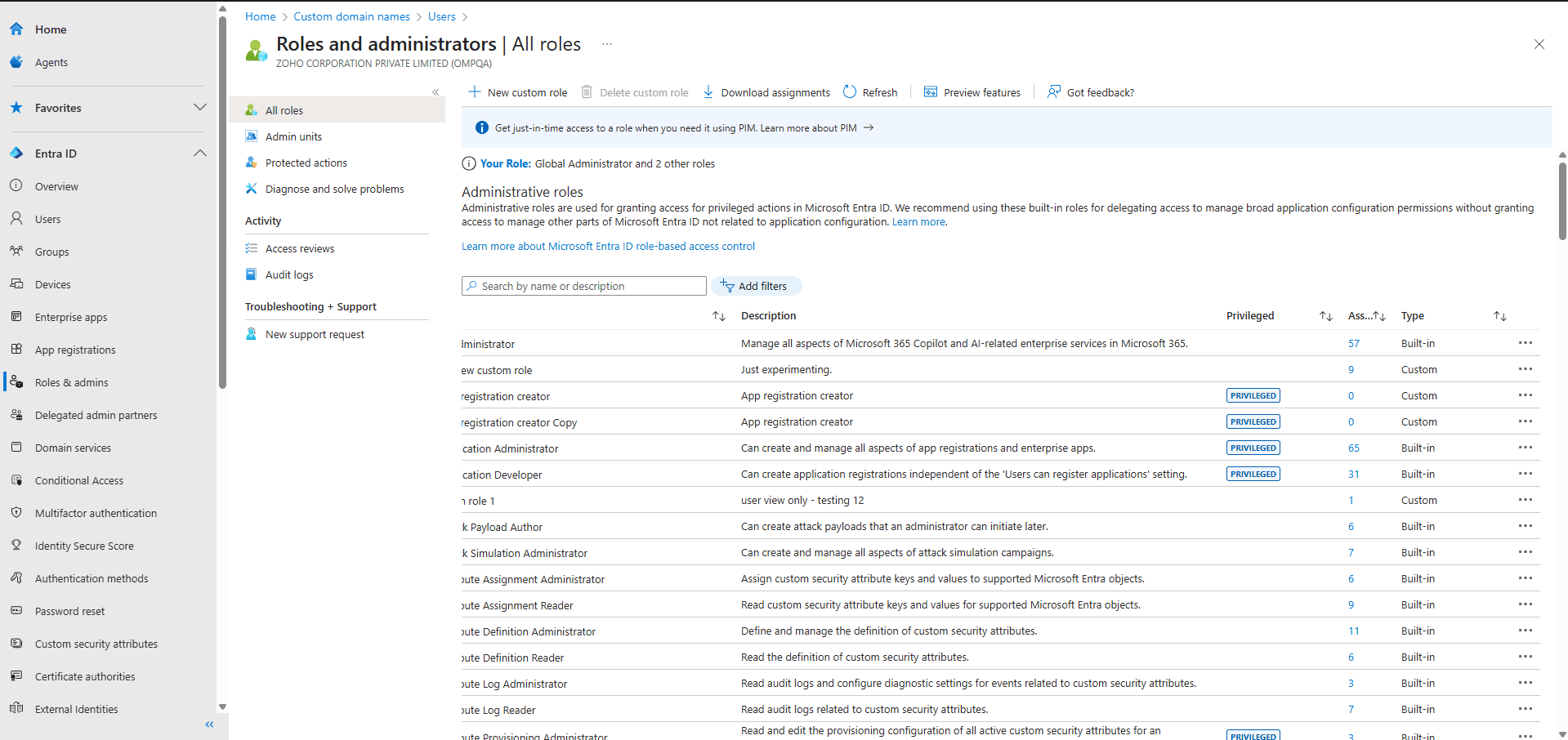
Directory roles in Microsoft Entra ID define what admin actions users and groups can take. For IT admins, knowing which roles exist, what they allow, and who holds them is key to governance. Since roles change as organizations grow, it helps to have a simple way to review them. Fortunately, there are reliable ways to retrieve all directory roles in Microsoft Entra ID.
Connect-MgGraph -Scopes "Directory.Read.All"
Get-MgDirectoryRole
Get-MgDirectoryRole -DirectoryRoleId "<RoleObjectId>"
Example query:
Connect-MgGraph -Scopes "Directory.Read.All"
Get-MgDirectoryRole
Example output:
Id: 12a34b56-cd78-90ef-gh12-3456abcd7890
DisplayName: Global Administrator
Description: Can manage all aspects of Microsoft Entra ID and Microsoft services
RoleTemplateId: 8e3af657-a8ff-443c-a75c-2a2b47c6fa7b
Id: 23b45c67-de89-01fg-hi23-4567bcde8901
DisplayName: User Administrator
Description: Can manage users and user-related aspects
RoleTemplateId: fe930be7-5e62-47db-91af-98c3a49a38b1
The syntax is as follows:
Get-MgDirectoryRole
[-ExpandProperty <string[]>]
[-Property <string[]>]
[-Filter <string>]
[-Search <string>]
[-Skip ]
[-Sort <string[]>]
[-Top ]
[-ResponseHeadersVariable <string>]
[-Break]
[-Headers <IDictionary>]
[-HttpPipelineAppend <SendAsyncStep[]>]
[-HttpPipelinePrepend <SendAsyncStep[]>]
[-Proxy <uri>]
[-ProxyCredential <pscredential>]
[-ProxyUseDefaultCredentials]
[-PageSize <int>]
[-All]
[-CountVariable <string>]
[<CommonParameters>]
Example query:
Get-MgDirectoryRole
Example output:
Id: a1b2c3d4-5678-90ab-cdef-111213141516
DisplayName: Global Administrator
RoleTemplateId: 62e90394-69f5-4237-9190-012177145e10
Id: f9e8d7c6-5432-10ab-cdef-171615141312
DisplayName: User Administrator
RoleTemplateId: fe930be7-5e62-47db-91af-98c3a49a38b1
Id: 12345678-abcd-90ef-1234-567890abcdef
DisplayName: Security Administrator
RoleTemplateId: 194ae4cb-b126-40b2-bd5b-6091b380977d
ADManager Plus helps you manage users, groups, and access quickly from a single, centralized interface.
Assign daily admin tasks safely with role-based delegation. Teams can manage users and groups while you retain oversight and control.
Automate repetitive tasks like user provisioning, group updates, and license management. Save time while ensuring consistent, reliable processes.
Create and modify users and groups individually or in bulk, making sure the right people have access while avoiding orphaned accounts or unused groups.
Easily modify multiple groups at once. Adjust memberships, tweak settings, or reorganize groups to keep up with changing business needs.
Choose from over 200 prebuilt reports covering group memberships, license usage, and user activity. Gain full visibility to support audits, monitor access patterns, and spot anomalies.
Conduct regular access reviews to remove unnecessary privileges, retire outdated memberships, and maintain least-privilege access across your tenant.
When reviewing directory roles, make sure each user or group has only what they need. Assign roles at the narrowest scope possible. Prefer administrative units or resource-specific scopes over tenant-wide roles to minimize risk.
Start by evaluating built-in roles and use them whenever they meet your requirements. Create custom roles only when a built-in role doesn't fit. This keeps role management simpler and helps prevent accidental over-provisioning.
Leverage automation and regular access reviews to assign, revoke, and monitor directory roles. Scheduled audits and automated reports help you spot stale, unnecessary, or over-privileged roles, keeping your environment secure and compliant.
Microsoft recommends keeping the total number of privileged role assignments in a tenant to around 60. Following this guidance helps maintain a secure and manageable environment, thereby reducing attack surface and improving governance.