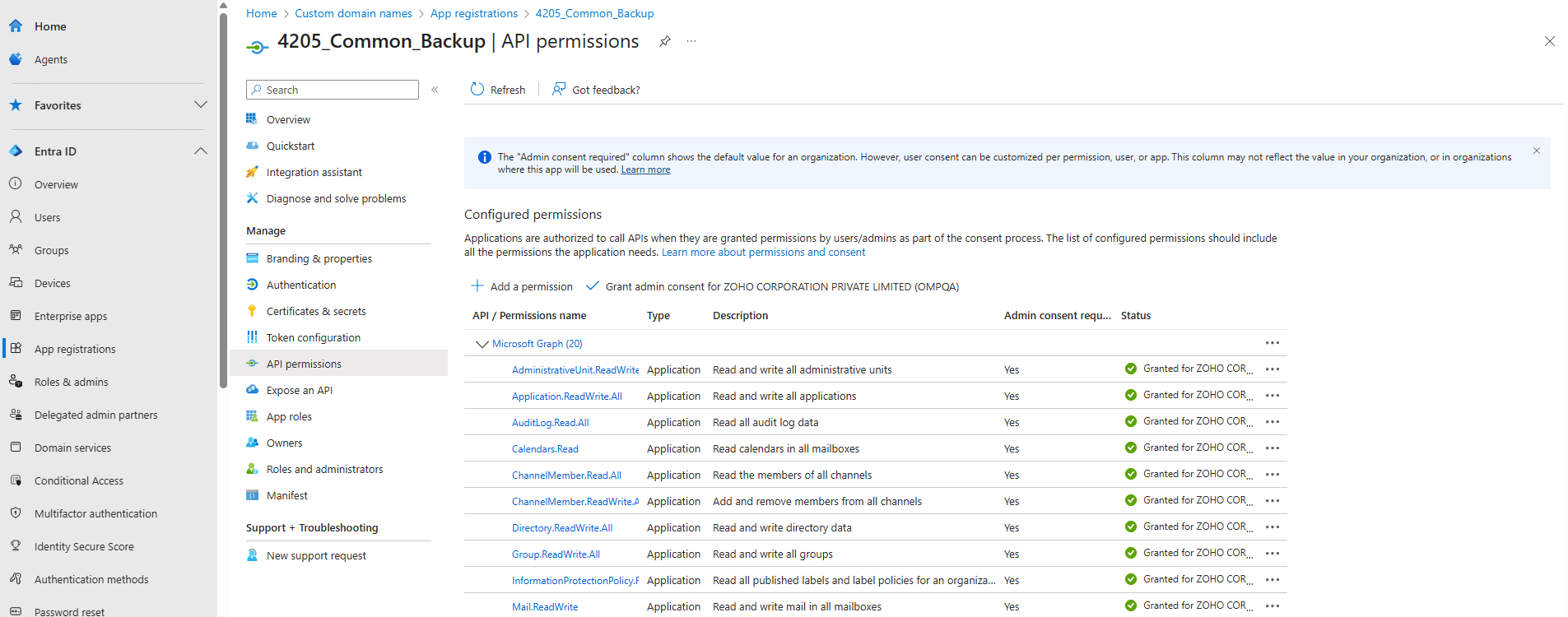
Delegated permissions let apps access company resources on behalf of users. As an organization grows, admins need to know which apps have what permissions and how user consent is handled. There are some easy ways to view and manage these permissions for any application.
Connect-MgGraph -Scopes "Application.Read.All"
Get-MgApplication -Filter "DisplayName eq 'AppName'"
Get-MgOauth2PermissionGrant -Filter "ClientId eq '<AppObjectId>'"
Example query
Connect-MgGraph -Scopes "Application.Read.All"
$appId = "8c4e912b-1b7d-4e55-b8b3-19f0c8d7a3f5"
Get-MgOauth2PermissionGrant -Filter "clientId eq '$appId'"
Example output:
Id: f12e34cd-5678-49ab-8f00-b3a2d9a45e2a
ClientId: 8c4e912b-1b7d-4e55-b8b3-19f0c8d7a3f5
ConsentType: AllPrincipals
PrincipalId:
ResourceId: 00000003-0000-0000-c000-000000000000
Scope: User.Read Mail.Send Mail.ReadWrite
StartTime: 10/21/2025 08:45:12
ExpiryTime: 10/21/2026 08:45:12
The syntax is as follows:
Get-MgOauth2PermissionGrant
[-ExpandProperty <string[]>]
[-Property <string[]>]
[-Filter <string>]
[-Search <string>]
[-Skip ]
[-Sort <string[]>]
[-Top <int>]
[-ResponseHeadersVariable <string>]
[-Break]
[-Headers <IDictionary>]
[-HttpPipelineAppend <SendAsyncStep[]>]
[-HttpPipelinePrepend <SendAsyncStep[]>]
[-Proxy <uri>]
[-ProxyCredential <pscredential>]
[-ProxyUseDefaultCredentials]
[-PageSize <int>]
[-All]
[-CountVariable <string>]
[<CommonParameters>]
Example query:
Connect-MgGraph -Scopes "DelegatedPermissionGrant.Read.All Application.Read.All"
Get-MgOauth2PermissionGrant -Filter "clientId eq '8c4e912b-1b7d-4e55-b8b3-19f0c8d7a3f5'"
Example output
Id: a7f2b86c-5b4e-49f9-b7a1-fc76d8b1f423
ClientId: 8c4e912b-1b7d-4e55-b8b3-19f0c8d7a3f5
ConsentType: AllPrincipals
PrincipalId:
ResourceId: 00000003-0000-0000-c000-000000000000
Scope: User.Read Mail.ReadWrite Calendars.Read
StartTime: 10/22/2025 09:15:27
ExpiryTime: 10/22/2026 09:15:27
The client application Your-Mail-App is identified by the unique ClientId 8c4e912b-1b7d-4e55-b8b3-19f0c8d7a3f5. It has been granted delegated permissions User.Read, Mail.ReadWrite, and Calendars.Read to access Microsoft Graph (ResourceId: 00000003-0000-0000-c000-000000000000). The ConsentType is set to AllPrincipals, meaning the permissions apply to all users within the tenant. These permissions were granted on October 22, 2025, and are valid until October 22, 2026, confirming that the app has the necessary delegated access to act on behalf of users within the organization.
ADManager Plus gives admins a single, easy-to-use console to manage Microsoft 365 efficiently.
Create, update, and manage users, groups, contacts, and licenses in bulk. Add or remove members, assign or revoke licenses, and handle everyday admin work faster.
Access over 200 built-in reports on logon activity, account status, and more. Schedule and export them anytime, and take actions right from the reports.
Keep track of privilege assignments, detect risky accounts, and identify possible attack paths. Strengthen compliance and reinforce your Zero Trust approach.
Automate repetitive admin tasks like user updates, license assignments, and group management. Cut down manual effort and free up time for higher-value work.
Assign roles and delegate tasks securely using role-based access controls. Let teams manage daily operations while you retain full oversight.
Delegated permissions work only with OAuth 2.0 flows that include user sign-in—like authorization code, on-behalf-of, implicit, or device code flows. Pick the flow that best fits your app type and user experience needs before requesting tokens.
Control which users can grant permissions by adjusting the user consent settings under Microsoft Entra ID’s enterprise app configuration. Assign the Application Developer role only to trusted users who are approved to register and consent to applications.
Once your client app is set up, check the permissions included in its OAuth access token. Use tools like jwt.ms to inspect the token payload and confirm that the correct delegated scopes (for example, scp: "User.Read") are present. This helps ensure your app’s tokens carry the intended permissions.