Access control lists (ACLs) define permissions for users and groups on OUs, containers, and other Active Directory (AD) objects. Checking ACLs helps admins audit current permissions, troubleshoot access issues, and plan delegation or security changes. This page covers steps to get ACLs for AD folders and subfolders using PowerShell, the Active Directory Users and Computers (ADUC) console, and ManageEngine ADManager Plus, with clearly explained prerequisites, steps, examples, and supported parameters.
The Get-Acl cmdlet in PowerShell is used to retrieve the security descriptor of a resource, such as a file, folder, or registry key. This security descriptor contains the ACLs, which explicitly detail the permissions granted to users or groups for that specific resource. Get-Acl lets an admin check who has what kind of access, like Read, Write, or Full Control, to an item. The output is a PowerShell object that can then be analyzed, filtered, or piped to other cmdlets, often serving as the first step before using the Set-Acl cmdlet to modify permissions.
Using the AD module's Get-Acl cmdlet, admins can extract permissions on OUs and child objects with detailed access entries.
Import-Module ActiveDirectory
Use the Get-Acl cmdlet with a folder path like C:\ExampleFolder to retrieve the NTFS permissions (ACL) applied to the folder.
$folderPath = "C:\ExampleFolder"
Get-Acl -Path $folderPath | Format-List
This command retrieves and displays all ACEs set on the user account “John Smith.”
$userDN = "CN=John Smith,OU=Users,DC=domain,DC=com"
Get-Acl -Path "AD:$userDN" | Format-List
This command retrieves and displays the ACL defined on the OU named "Sales" in the domain "domain.com."
$ADFolderPath = "AD:\OU=Sales,DC=domain,DC=com"
Get-Acl -Path $ADFolderPath | Format-List
This script retrieves the ACL for a specified parent OU and all its immediate child OUs, helping you audit delegation and access structure within that branch of AD.
$ParentOU = "OU=Sales,DC=domain,DC=com"
$ChildOUs = Get-ADOrganizationalUnit -SearchBase $ParentOU -Filter *
foreach ($ou in $ChildOUs) {
Write-Output "ACL for OU: $($ou.DistinguishedName)"
Get-Acl -Path ("AD:\" + $ou.DistinguishedName) | Format-List
}
This script collects ACLs for a target OU and all its sub-OUs recursively and exports the permission details into a CSV file.
$OUPath = "OU=Sales,DC=domain,DC=com"
$AllOUs = Get-ADOrganizationalUnit -SearchBase $OUPath -Filter * -SearchScope Subtree
$results = foreach ($ou in $AllOUs) {
$acl = Get-Acl -Path ("AD:\" + $ou.DistinguishedName)
foreach ($ace in $acl.Access) {
[PSCustomObject]@{
ObjectDN = $ou.DistinguishedName
Identity = $ace.IdentityReference
AccessControlType = $ace.AccessControlType
ActiveDirectoryRights = $ace.ActiveDirectoryRights
InheritanceType = $ace.InheritanceType
}
}
}
$results | Export-Csv -Path "AD_OUs_ACL_Report.csv" -NoTypeInformation
The following essential parameters can be used with the Get-Acl cmdlet:
| Parameters | Description |
|---|---|
| -Path | Specifies the AD path to the object (e.g., "AD:\OU=Sales,DC=domain,DC=com"). |
| -SearchBase | Defines the root container for Get-ADOrganizationalUnit queries. |
| -Filter | Filters objects for retrieval (e.g., * for all objects). |
| -SearchScope | Specifies scope of search: base, onelevel, or subtree. |
| -IdentityReference | The security principal (user or group) for an ACE entry. |
| -AccessControlType | Allows filtering or inspection of Allow or Deny access types. |
| -ActiveDirectoryRights | The specific right assigned by the ACE (e.g., WriteProperty). |
ADUC offers a GUI-based way to view permissions on OUs and child objects:
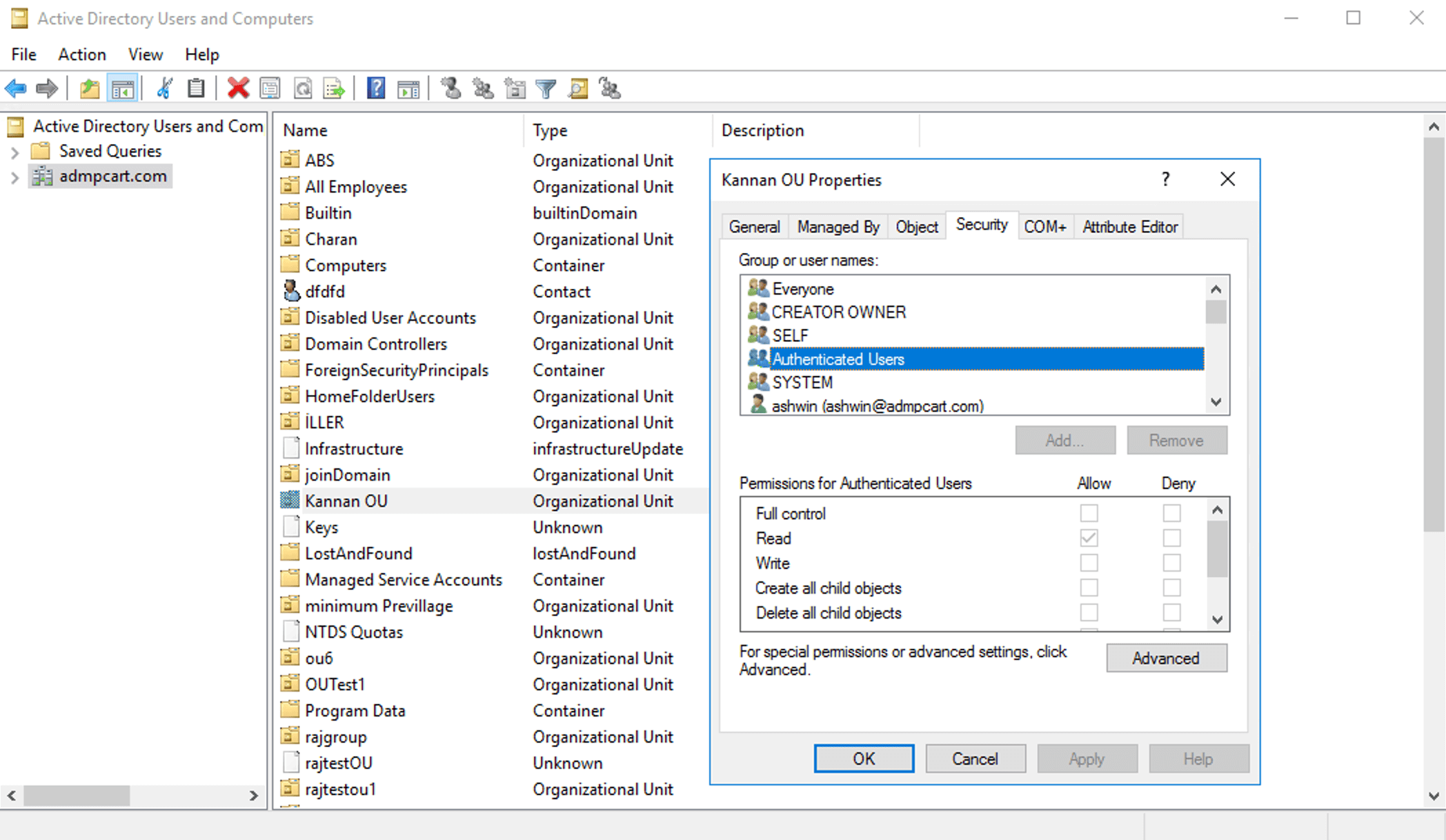
Export the report in different formats like CSV, XLS, PDF, and HTML.
Customize folder levels and permissions to refine the result
While PowerShell and ADUC are powerful, relying solely on these native tools can present challenges:
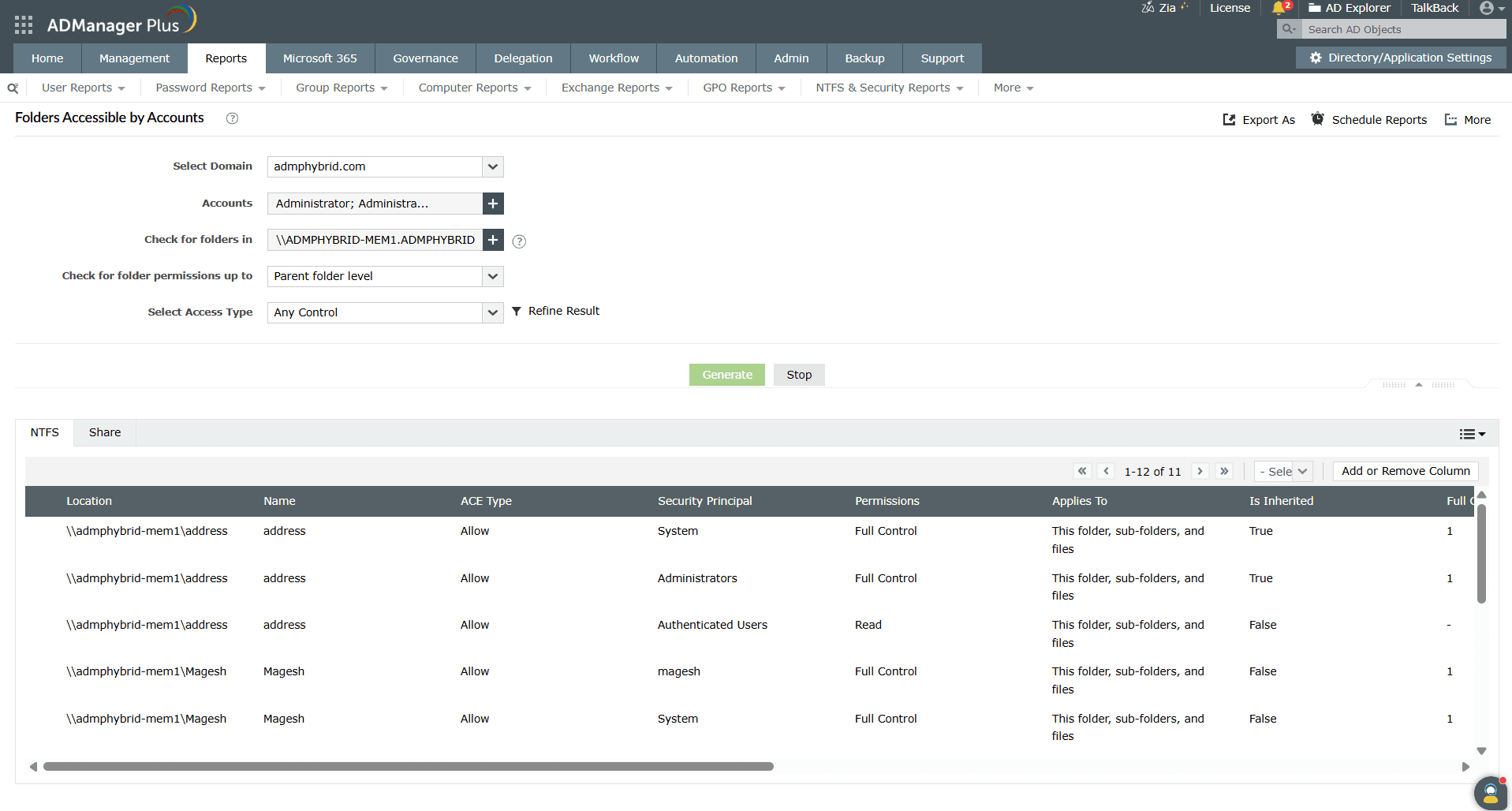
ADManager Plus is an all-in-one AD, Exchange, and Microsoft 365 management solution that lets you retrieve ACLs and more, in a script-free, unified console.
An access control ilst (ACL) is a core component of an AD object's Security Descriptor, essentially functioning as the rule book that governs permissions for that object, such as a user account, group, or OU. It is composed of Access Control Entries (ACEs) and is split into two primary lists: the Discretionary Access Control List (DACL), which explicitly grants or denies permissions to specific users and groups; and the System Access Control List (SACL), which is used exclusively for auditing by defining which successful or failed access attempts must be logged to the security event viewer. This granular structure ensures tight security by letting admins precisely control and track who can perform what actions on every item within the directory structure.
Active Directory has two types of ACLs (DACL and SACL), and within them, permissions are represented as Access Control Entries (ACEs), which come in two forms: explicit and inherited.
Discretionary Access Control List (DACL): This is the most common type in AD. It defines the specific permissions (Read, Write, Create/Delete Child, etc.) that different security principals (users, groups, computers) have on an AD object (like a user account, group, or Organizational Unit). The DACL is the list an admin modifies as needed to manage access.
System Access Control List (SACL): This list is used for auditing. It defines which access attempts (both successful and failed) by specific users or groups should be logged to the Windows security event log. It is not for granting or denying access, but for tracking it.
Inherited Access Control Entries (ACEs): These are permission rules that an object automatically receives from its parent container like an OU higher up in the AD hierarchy. These are crucial for managing permissions at scale.
Explicit Access Control Entries (ACEs): These are permission rules that are manually and directly assigned to a specific AD object, overriding or supplementing any inherited permissions.
The Set-Acl cmdlet is used to apply a modified security descriptor (ACL) to a file, folder, or other securable object. The workflow generally involves three steps:
Here's an example script to grant an user Modify permission on a folder:
$path = "C:\Data\Reports"
$user = "DOMAIN\John.Doe"
$acl = Get-Acl -Path $path
$permission = $user, "Modify", "ContainerInherit,ObjectInherit", "None", "Allow"
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule $permission
$acl.AddAccessRule($accessRule)
Set-Acl -Path $path -AclObject $acl
Write-Host "Permission applied successfully."
For a script-free approach, ADManager Plus helps you manage ACLs to files and folders in bulk.