Conditional Access policies are central to securing Microsoft 365, allowing you to enforce the right controls depending on the user, device, location, and risk level. For IT admins, tracking these policies, understanding their scope, and ensuring they align with a Zero Trust strategy can quickly become complex. Fortunately, there are straightforward ways to retrieve and review them, making policy management far more manageable.
Connect-MgGraph -Scopes "Policy.Read.All", "Policy.ReadWrite.ConditionalAccess"
Get-MgDomainFederationConfiguration
Get-MgIdentityConditionalAccessPolicy -ConditionalAccessPolicyId <PolicyID>
Example query
Connect-MgGraph -Scopes "Policy.Read.All","Policy.ReadWrite.ConditionalAccess"
Get-MgIdentityConditionalAccessPolicy -ConditionalAccessPolicyId "d5b4e1c3-72ab-4c2f-9c8b-0f8f4a3fba56"
Example output
Id : d5b4e1c3-72ab-4c2f-9c8b-0f8f4a3fba56
DisplayName : Require MFA for Admins
State : enabled
Conditions : Microsoft.Graph.PowerShell.Models.MicrosoftGraphConditionalAccessConditionSet
GrantControls : Microsoft.Graph.PowerShell.Models.MicrosoftGraphConditionalAccessGrantControls
SessionControls : Microsoft.Graph.PowerShell.Models.MicrosoftGraphConditionalAccessSessionControls
CreatedDateTime : 18-08-2025 05:42:15
ModifiedDateTime : 18-08-2025 05:45:01
Description : This policy requires all global admins to use MFA when accessing Microsoft 365 services.
The syntax is as follows:
Get-MgIdentityConditionalAccessPolicy
[-ExpandProperty <String[]>]
[-Property <String[]>]
[-Filter <String>]
[-Search <String>]
[-Skip <Int32>]
[-Sort <String[]>]
[-Top <Int32>]
[-ResponseHeadersVariable <String>]
[-Headers <IDictionary>]
[-PageSize <Int32>]
[-All]
[-CountVariable <String>]
[<CommonParameters>]
Example query
Connect-MgGraph -Scopes 'Policy.Read.All'
Get-MgIdentityConditionalAccessPolicy -ConditionalAccessPolicyId '5e7615b8-dbe4-4cc1-810c-26adb77a3518' |
Example output
Conditions : Microsoft.Graph.PowerShell.Models.MicrosoftGraphConditionalAccessConditionSet
CreatedDateTime : 1/13/2022 6:35:35 AM
Description :
DisplayName : Exchange Online Requires Compliant Device
GrantControls : Microsoft.Graph.PowerShell.Models.MicrosoftGraphConditionalAccessGrantControls
Id : 5e7615b8-dbe4-4cc1-810c-26adb77a3518
ModifiedDateTime : 7/29/2022 9:08:10 AM
SessionControls : Microsoft.Graph.PowerShell.Models.MicrosoftGraphConditionalAccessSessionControls
State : enabled
AdditionalProperties : {[@odata.context, https://graph.microsoft.com/v1.0/$metadata#identity/conditionalAccess/policies/$entity]}
The output shows a Conditional Access policy in Microsoft Entra ID called Exchange Online Requires Compliant Device. It's currently enabled and was first created on Jan. 13, 2022, then last updated on July 29, 2022. The policy kicks in under certain Conditions, and when it does, the GrantControls and SessionControls decide what access rules or restrictions get applied. The Id is its unique identifier, and there's also some extra metadata pulled in from Microsoft Graph under AdditionalProperties.
ADManager Plus makes it easier for admins to manage Microsoft 365 with a simple, centralized console.
Create, modify, and manage users, groups, contacts, and licenses at scale. Perform bulk management, adjust memberships, assign or revoke licenses, and streamline day-to-day admin work.
Schedule and export over 200 prebuilt reports, including logon activity and account status reports. Take quick actions directly from reports, such as unblocking accounts.
Track privilege assignments, and identify risky accounts and track the potential attack path and assign compliance, and strengthen your Zero Trust strategy.
Automate recurring Microsoft 365 tasks by orchestration workflows, such as assigning or removing Conditional Access policies during user provisioning based on role or department.
Use role-based access delegation to distribute responsibilities safely. Empower teams to handle day-to-day tasks while you maintain visibility and control.
Review which users and groups are targeted by Conditional Access policies to confirm they align with your security and compliance goals.
Run policies in a report only mode and evaluate their impact before rolling them out broadly.
Keep dedicated emergency admin accounts excluded from restrictive policies to ensure you can always access and manage the environment in case of other admins' accounts getting locked out due to outage or misconfigurations.
Use the What If feature in Microsoft Entra ID to safely test your Conditional Access policies before enforcing them. By simulating sign-ins with chosen conditions like user, device, or location, you can see exactly which policies would apply and why, helping you fine-tune settings and avoid accidental lockouts.
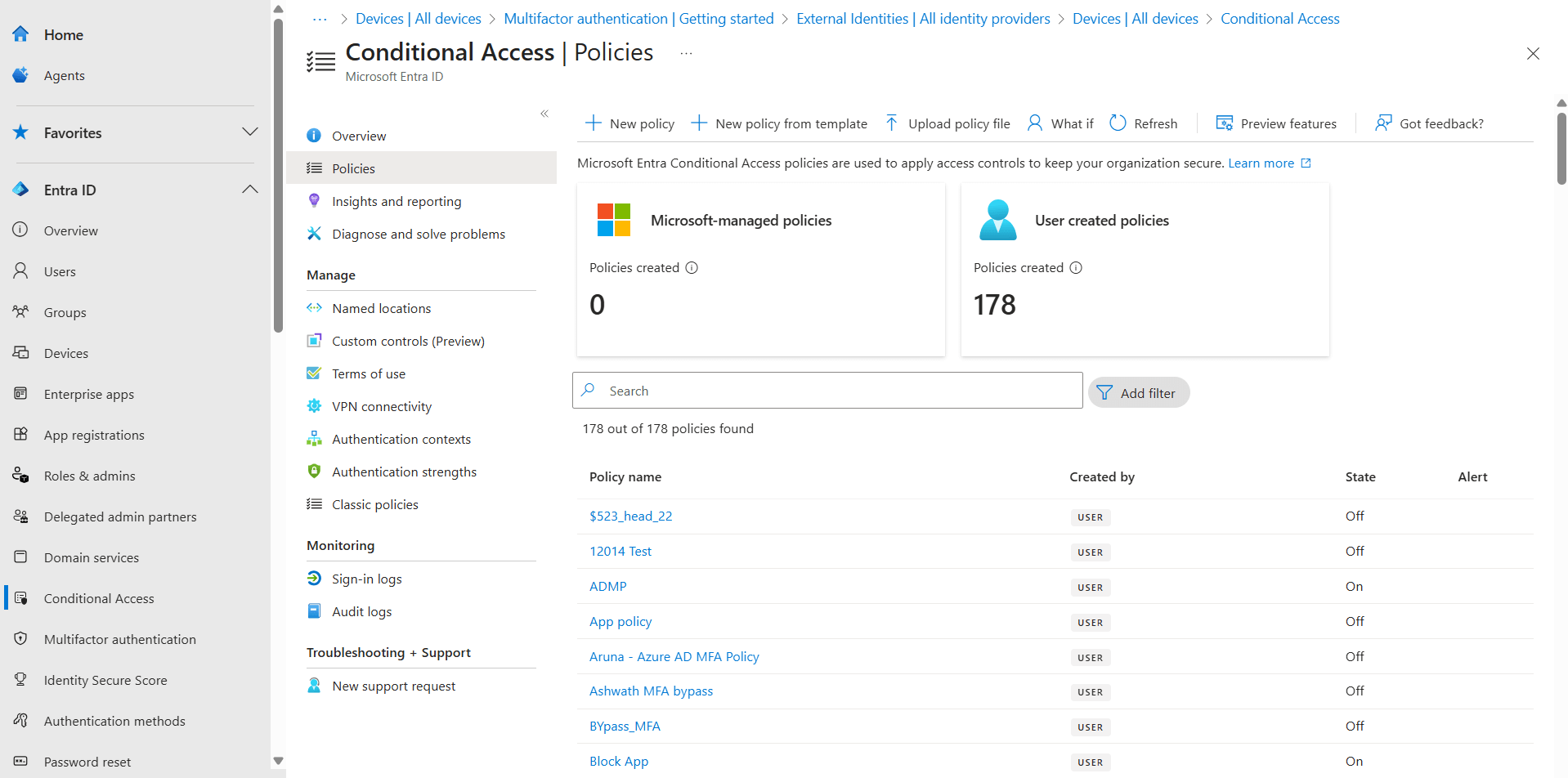
Using Entra admin center
Using PowerShell
After retrieving the policies, you can export using the below command.
Get-AzureADMSConditionalAccessPolicy | ConvertTo-Json -Depth 10 | Out-File "CAPolicies.json"
Using Graph PowerShell
After retrieving the policies, export them using the command below
Get-MgIdentityConditionalAccessPolicy | ConvertTo-Json -Depth 10 | Out-File "CAPolicies.json"
Go to Entra ID > Monitoring & health > Sign-in logs, select a sign-in record, and view the Conditional Access tab to see which policies were triggered for that event.
You can track policy changes in the Audit logs.
Entra admin center
Graph PowerShell
While Conditional Access policies themselves don't directly store “last modified by,” you can query audit logs through Microsoft Graph.
Get-MgAuditLogDirectoryAudit -Filter "activityDisplayName eq 'Update conditional access policy'" -Top 10
This returns the most recent modifications and includes initiatedBy with the user who made the change.
You can check Conditional Access policy changes using two methods.
Entra admin center
Graph PowerShell
Get-MgAuditLogDirectoryAudit -Filter "activityDisplayName eq 'Update conditional access policy'" | Select-Object activityDateTime, targetResources, initiatedBy, additionalDetails
The additionalDetails field captures what properties were changed.