Managed devices are essential for enforcing compliance, deploying configurations, and keeping endpoints healthy across your organization. However, for IT admins, tracking these devices to keep the directory secure, compliant, and clean can be a real challenge-especially across diverse groups. Fortunately, there are practical ways to make this easier. Let's look at some effective methods to monitor managed devices in Microsoft Entra ID.
Connect-AzureAD
Get-MgDevice
Get-MgDevice | Where-Object { $_.DeviceTrustType -eq "MDM" }
Example query
Connect-AzureAD
Get-MgDevice
Get-MgDevice | Where-Object { $_.DeviceTrustType -eq "MDM" }
Example output
Id : 6c12f7f1-0b1e-4b25-9c91-94af3f02d6a1
DisplayName : John-Laptop
OperatingSystem : Windows
OperatingSystemVersion : 10.0.22631.3593
DeviceTrustType : MDM
IsCompliant : True
IsManaged : True
ApproximateLastSignInDateTime : 18-08-2025 09:42:15
ProfileType : RegisteredDevice
EnrollmentType : Company
AccountEnabled : True
The syntax is as follows:
Get-MgDeviceManagementManagedDevice
[-ExpandProperty <String[]>]
[-Property <String[]>]
[-Filter <String>]
[-Search <String>]
[-Skip <Int32>]
[-Sort <String[]>]
[-Top <Int32>]
[-ResponseHeadersVariable <String>]
[-Headers <IDictionary>]
[-PageSize <Int32>]
[-All]
[-CountVariable <String>]
[<CommonParameters>]
Example query
Get-MgDeviceManagementManagedDevice -Filter "complianceState eq 'noncompliant'
Example output
Id : 6b25f26f-8812-42a9-9fd1-bcfeb193a940
DeviceName : HR-Tablet-02
OperatingSystem: iOS
OsVersion : 17.5
UserPrincipalName: Jane.ola@contoso.com
ComplianceState : noncompliant
ManagementAgent : mdm
LastSyncDateTime : 17-08-2025 21:04:12
The output shows Jane's iOS device called HR-Tablet-02. It's enrolled in Intune MDM, last synced on Aug. 17, 2025 at 21:04:12, but it's marked noncompliant with the organization's policies. That could be a risk because conditional access rules might block her from accessing Microsoft 365 apps until the device becomes compliant.
ADManager Plus management and reporting helps Microsoft 365 admins, with a clean, intuitive interface that makes everyday Microsoft 365 tasks simpler.
Identify inactive or stale accounts with ready-made reports and remove them instantly to keep your directory clean and secure.
Streamline bulk provisioning and deprovisioning to ensure users always have the right access and no orphaned accounts remain.
Track and control group memberships and privileges to prevent unauthorized access and maintain least-privilege policies.
Get over 200 prebuilt reports on users, groups, licenses, and directory health for complete visibility. Export in CSV, PDF, or HTML to simplify audits and stay compliant.
Save time by automating bulk user tasks, license management, group modifications, and other repetitive administrative tasks.
Detect over-permissioned identities, evaluate threat paths, and gain clear insights into potential exposures. ADManager Plus shows why an entity is at risk and guides you on remediation, helping you strengthen security and build resilience.
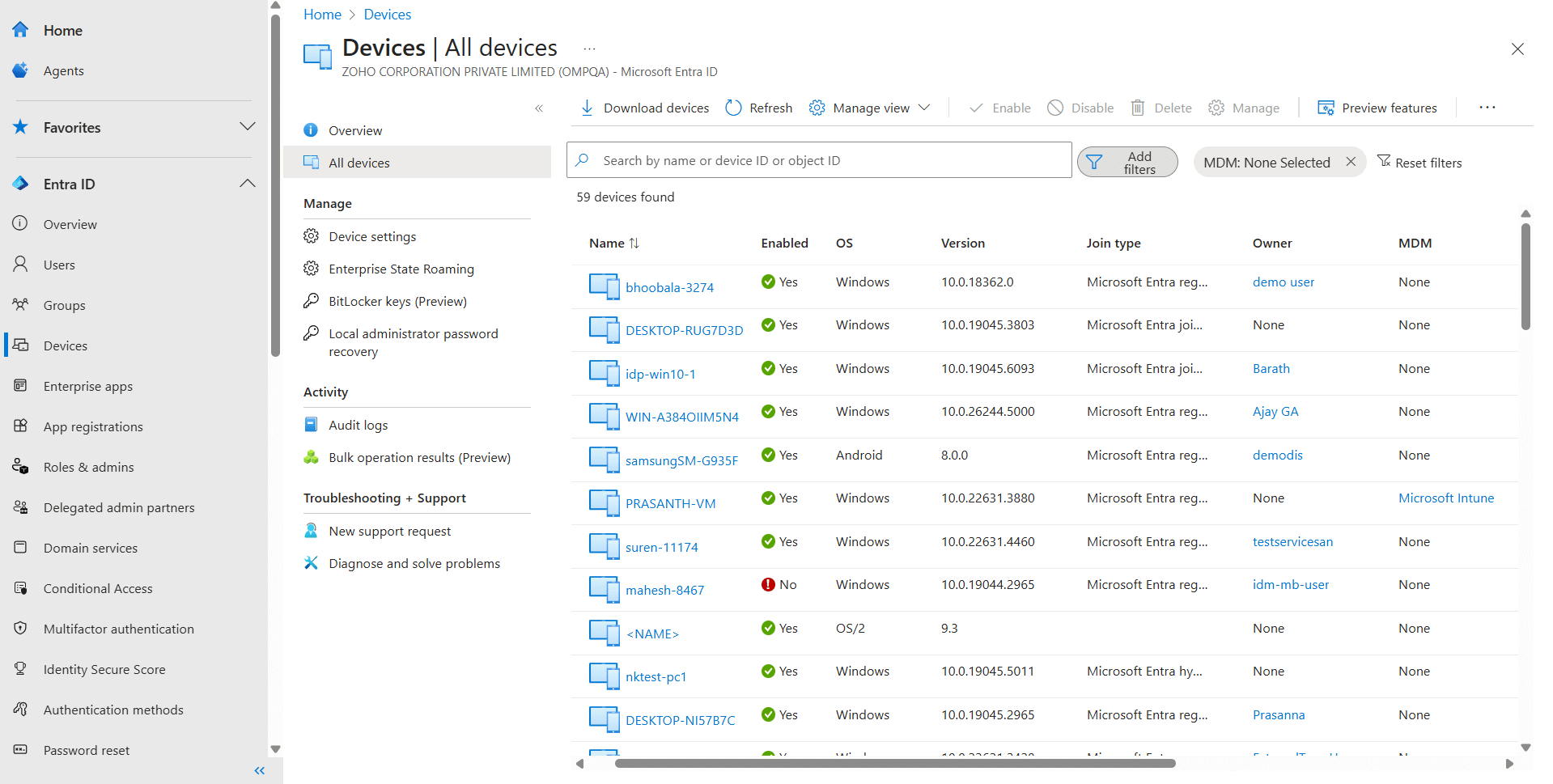
The Microsoft 365 admin center provides a central location for managing device identities, settings, and policies.
Remove devices that are no longer in use to minimize risk and reduce license bloat.
Restrict access based on device state, user role, or location to strengthen security.