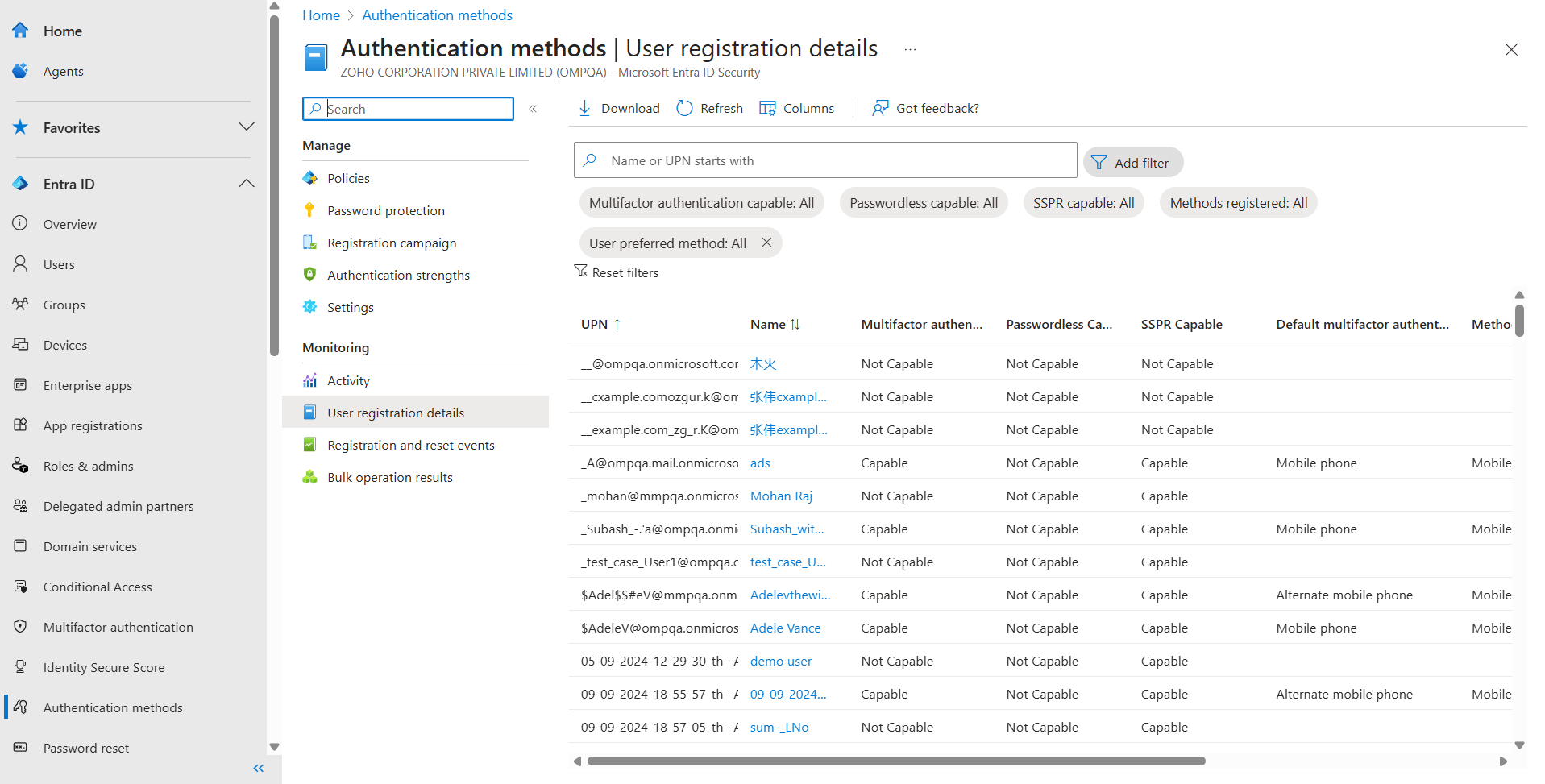
Authentication methods play a critical role in protecting user accounts and meeting compliance needs. For IT admins, tracking who has registered MFA, which methods they use, and whether they meet policy requirements can be overwhelming, especially across a large directory. But, there are practical ways to make this easier.
Connect to the Azure AD PowerShell.
Connect-MgGraph -Scopes "UserAuthenticationMethod.Read.All"
Get-MgUserAuthenticationMethod -UserId <userUPN or ObjectId>
Get-MgUserAuthenticationMethod -UserId <userUPN> | Where-Object {$_.OdataType -eq "#microsoft.graph.phoneAuthenticationMethod"}
Connect-MgGraph -Scopes "UserAuthenticationMethod.Read.All"
Get-MgUserAuthenticationMethod -UserId John@contoso.com
Get-MgUserAuthenticationMethod -UserId John@contoso.com |
Where-Object {$_.OdataType -eq "#microsoft.graph.phoneAuthenticationMethod"}
Id : 3a1a5e12-64d4-4a11-91e4-4a6f54b35ef9
OdataType : #microsoft.graph.phoneAuthenticationMethod
PhoneType : mobile
PhoneNumber : +91 9876543210
SmsSignInState : enabled
Here's the syntax:
Get-MgUserAuthenticationMethod
-UserId <String>
[-ExpandProperty <String[]>]
[-Property <String[]>]
[-Filter <String>]
[-Search <String>]
[-Skip <Int32>]
[-Sort <String[]>]
[-Top <Int32>]
[-ResponseHeadersVariable <String>]
[-Headers <IDictionary>]
[-PageSize <Int32>]
[-All]
[-CountVariable <String>]
[<CommonParameters>]
Example query
Get-MgUserAuthenticationMethod -UserId Jane@contoso.com |
Where-Object {$_.OdataType -eq "#microsoft.graph.microsoftAuthenticatorAuthenticationMethod"}
[<CommonParameters>]
Example output
Id : 91a43c8e-dcf3-47a1-9a6a-9983d93f5f77
OdataType : #microsoft.graph.microsoftAuthenticatorAuthenticationMethod
DisplayName : Microsoft Authenticator
DeviceTag : Pixel 7
DeviceId : 8f6b42c1-5abf-4931-8a21-57b8e5b3a7e1
This output shows that Jane has Microsoft Authenticator registered as her authentication method, with the OdataType showing it's the Authenticator app.
She has Microsoft Authenticator set up as their authentication method and it's tied to a Pixel 7 device, with the DeviceTag pointing to that phone model. The method is tracked in Entra ID with a unique DeviceId, and the ID confirms the specific record for this authentication method. DisplayName makes it clear the app in use is Authenticator.
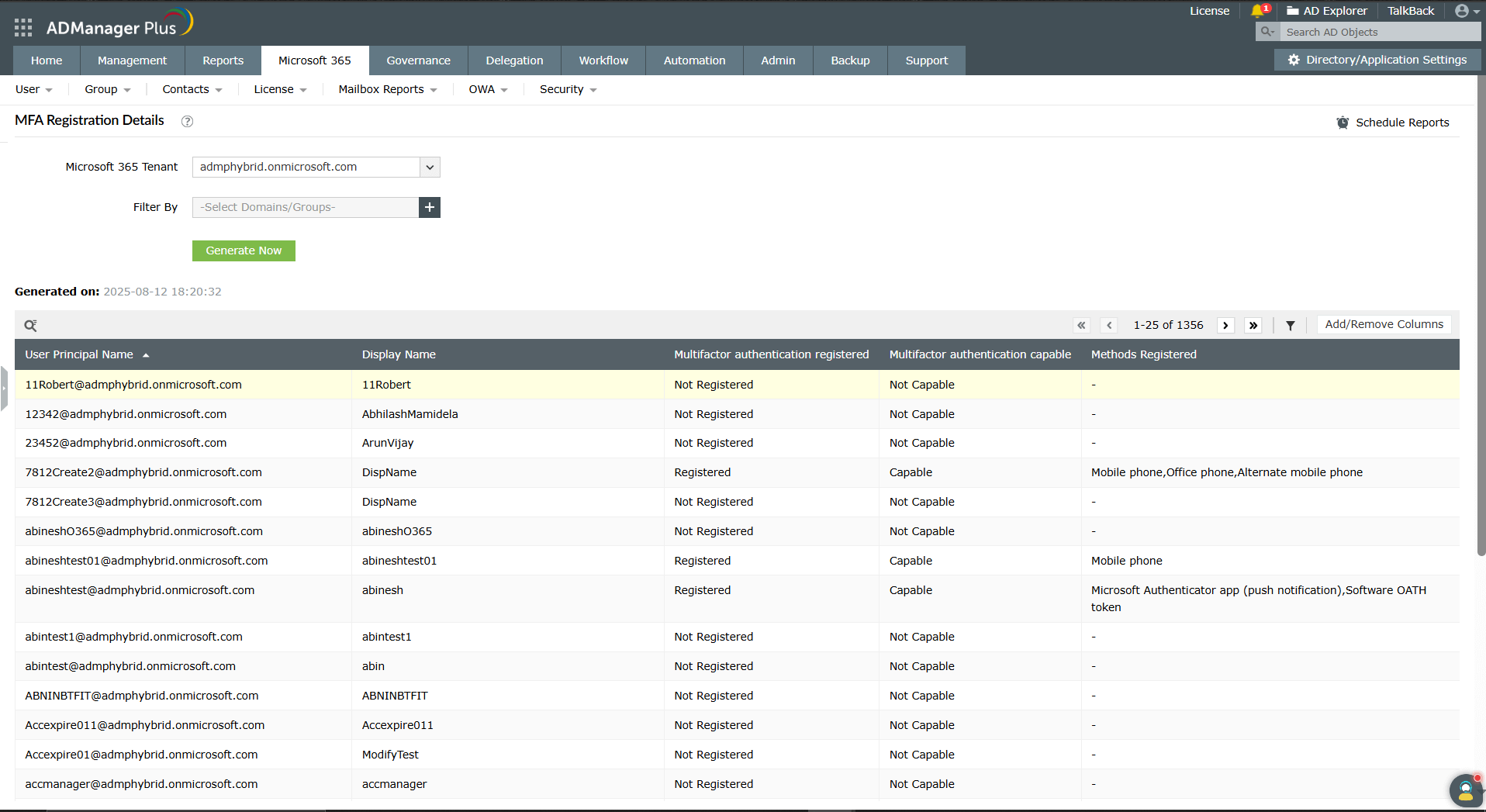
ADManager Plus' Microsoft 365 management and reporting offers a complete solution for Microsoft 365 admins, with a simple, user-friendly interface that allows you to easily get MFA status and other user reports instantly.
Update MFA settings for multiple users at once to save time and ensure consistency.
Track not just MFA registrations, but also password changes, expirations, and MFA status across your tenant.
Build custom dashboards for at-a-glance visibility into MFA adoption and password health and get updates in a scheduled frequency.
Automate MFA tasks and create approval-based workflows to streamline secure processes.
Assign MFA tasks to technicians with controlled permissions and oversight.
Track the potential attack flow on privileged accounts to reduce exposure.
Set up regular reports to track MFA adoption and spot gaps and modify quickly.
If users have multiple methods but they rely on just one, remove the unused ones and eliminate weaker options to reduce risk.
Prompt unregistered users to complete MFA setup at their next login.
Apply stricter MFA for admins and privileged accounts while keeping it user-friendly for standard accounts.
Yes. You can run Get-MgUserAuthenticationMethod or older Get-MsolUser commands to see who has MFA and what methods are registered. The downside is it requires scripting skills, and reports need manual formatting unless you plug them into something else.
Removing an MFA method may disrupt user access if that method was their sole MFA option. It's best practice to verify users have alternate methods registered before removal.
Use the “Security Info Registration” Conditional Access policy. Instead of excluding users from your location-based policies, configure the “Authentication methods registration policy” in Entra ID. This allows users to register MFA methods (like the Authenticator app) from untrusted locations without granting them broader access to other resources. That way, they can set up MFA at home but still respect your conditional access restrictions for app access.
You can check this in multiple ways:
Entra admin center:
Graph PowerShell:
Get-MgUserAuthenticationMethod -UserId user@domain.com
ADManager Plus
Entra admin center (ADMP):
Graph PowerShell:
ADManager Plus