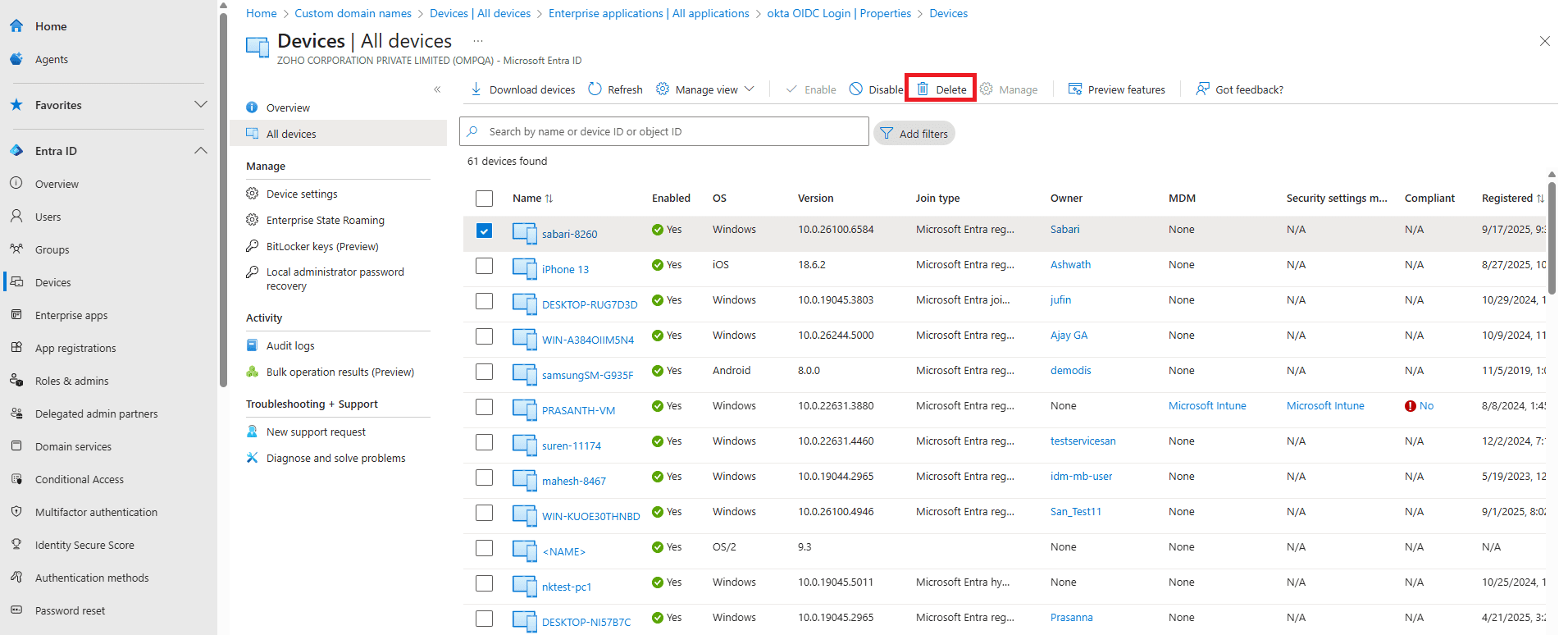
Device removal actions in Microsoft Entra ID determine how a device loses access to organizational resources and is purged from your directory. For IT admins, managing device deletions can be challenging, especially when dealing with stale, lost, or decommissioned endpoints across hybrid and cloud environments. However, there are straightforward ways to review, disable, and permanently remove devices from Microsoft Entra ID.
Connect-MgGraph
Get-MgDevice
Remove-MgDevice -ObjectId "<DeviceObjectId>"
Get-MgDevice -SearchString "MyLaptop"
Remove-MgDevice -ObjectId "a2b3c4d5-6789-40ab-9bcd-ef1234567890"
The syntax is as follows:
Remove-MgDevice
-DeviceId <string>
[-IfMatch <string>]
[-ResponseHeadersVariable <string>]
[-Break]
[-Headers <IDictionary>]
[-HttpPipelineAppend <SendAsyncStep[]>]
[-HttpPipelinePrepend <SendAsyncStep[]>]
[-PassThru]
[-Proxy <uri>]
[-ProxyCredential <pscredential>]
[-ProxyUseDefaultCredentials]
[-WhatIf]
[-Confirm]
[<CommonParameters>]
Get-MgDevice -Filter "displayName eq 'TestLaptop'"
Remove-MgDevice -DeviceId "a2b3c4d5-6789-40ab-9bcd-ef1234567890"
Example output:
Confirm
Are you sure you want to perform this action?
[Y] Yes [N] No [S] Suspend [?] Help (default is "Y"):
After confirmation, the device is deleted.
You can verify the action by running:
Get-MgDevice -DeviceId "a2b3c4d5-6789-40ab-9bcd-ef1234567890"
This will return nothing, confirming the device was removed.
ADManager Plus empowers Microsoft 365 admins with a clear, easy-to-navigate interface, streamlining routine tasks for greater efficiency.
Locate dormant or inactive accounts using ready-made reports and quickly remove them to keep your directory safe and well-organized.
Simplify bulk user provisioning and deprovisioning to assure appropriate access at all times and eliminate abandoned accounts.
Monitor group memberships and privileges to block unauthorized entry and uphold least-privilege principles.
Leverage over 200 built-in reports covering users, groups, licenses, and directory health for complete oversight. Export data to CSV, PDF, or HTML to enhance auditing and compliance processes.
Automate bulk user operations, license assignments, group management, and other repetitive administrative tasks, saving valuable time.
Spot and review users with excessive permissions, evaluate privilege pathways, and gain actionable security insights. ADManager Plus reveals risks and guides you to the right remediation steps, enabling stronger protection and operational resilience.
Check last sign-in timestamps or activity reports to find devices that haven't connected for a chosen period (e.g., 30, 90, or 180 days). Review details such as owner and operating system before removing them to avoid accidentally offboarding devices still in use.
Follow a two-step process: disable the device first to block access, then allow a grace period before deleting it. This reduces the chance of mistakes and ensures the device is truly unnecessary.
Before deleting a device, make sure BitLocker recovery keys and other important dependencies are handled. If the device is managed through MDM solutions like Intune, retire or disenroll it from the management console to prevent leaving behind orphaned records.
No, removing a device from Intune does not automatically delete it from Microsoft Entra ID. Devices must also be manually removed from Microsoft Entra ID to ensure they are fully deleted. For Autopilot and hybrid-joined devices, additional steps may be needed in their respective management platforms.
Deleting an Entra-registered device immediately revokes its access to organizational resources and removes its identity from the directory. For devices synced from on-premises AD (hybrid-joined), deletion should occur in the local AD first; otherwise, the object may be re-synced back into Microsoft Entra ID.
Microsoft Intune offers device cleanup rules to automatically purge devices that have not checked in for a specified period, but Microsoft Entra ID does not have native automated cleanup—device removal must be manual or scripted. For Hybrid Microsoft Entra joined devices, deletions should begin in on-premises AD and then be synchronized to Microsoft Entra ID. Regularly review device activity and establish clear policies to keep your directory up to date.