Revoking current user access in Microsoft Entra ID is a vital security step to make sure only authorized individuals can reach critical resources. Situations such as compromised accounts or insider threats often require admins to act quickly. As it happens, there are established procedures and tools that help admins review and revoke access efficiently, minimizing delays and security risks.
Connect-MgGraph -Scopes "User.ReadWrite.All"
Get-MgApplication
Revoke-MgUserSignInSession -UserId "<UserObjectId or UPN>"
This invalidates the user’s refresh tokens, forcing them to re-authenticate on their next sign-in attempt.
Example query:
Connect-MgGraph -Scopes "User.ReadWrite.All"
Revoke-MgUserSignInSession -UserId "jane@contoso.com"
Example output:
Status: Success
Message: All active refresh tokens for user jane@testdomain.com have been revoked.
UserId: 7e4a123b-92d7-4f83-91a1-3b1a7f9a9e6f
The syntax is as follows:
Revoke-MgUserSignInSession
-UserId <string>
[-ResponseHeadersVariable <string>]
[-Break]
[-Headers <IDictionary>]
[-HttpPipelineAppend <SendAsyncStep[]>]
[-HttpPipelinePrepend <SendAsyncStep[]>]
[-Proxy <uri>]
[-ProxyCredential <pscredential>]
[-ProxyUseDefaultCredentials]
[-WhatIf]
[-Confirm]
[<CommonParameters>]
Example query:
Connect-MgGraph -Scopes "User.ReadWrite.All"
$john = Get-MgUser -Filter "DisplayName eq 'John'"
Revoke-MgUserSignInSession -UserId $john.Id
Example output:
Confirm
Are you sure you want to perform this action?
Performing the operation "Revoke-MgUserSignInSession" on target "John".
[Y] Yes [A] Yes to All [N] No [L] No to All [?] Help (default is "Y"):
Once confirmed, John's refresh tokens are invalidated, forcing him to reauthenticate across all applications and devices. Any ongoing sessions tied to those tokens will stop working until he signs back in.
ADManager Plus helps admins proactively manage security by monitoring risky accounts, reviewing access periodically, and enforcing least-privilege policies. Its centralized console simplifies user and group management giving you the tools to reduce potential security risks and ensure compliance across your Microsoft 365 environment.
Identify accounts with high-risk activity or excessive privileges. By spotting potential security threats early, you can prevent unauthorized access, data breaches, and compliance violations before they escalate.
Schedule regular access reviews for users and groups. Detect stale or unnecessary access and remove it proactively to maintain least-privilege policies and stay audit-ready.
ADManager Plus offers a unified console to efficiently perform bulk management, enabling you to add or remove users, modify group memberships, and handle license assignments or revocations.
Automate routine user provisioning, deprovisioning, and role changes. Event-driven automation ensures that when an action triggers, revoking of user session happens automatically lowering security risk without manual intervention.
Use role-based delegation to empower teams to handle day-to-day Microsoft 365 tasks safely. You retain oversight while distributing responsibilities, reducing errors that could create risky access scenarios.
Gain insights from over 200 prebuilt reports covering sign-in activity, license usage, group memberships, and more. Use these reports to spot anomalies, validate access policies, and act proactively before a security incident occurs.
Continuously monitor sign-in logs and enable security alerts for suspicious activity or risky sign-ins, enabling rapid response to potential security incidents.
Quickly disable the Microsoft 365 account to prevent new authentication attempts and halt access to all resources tied to Microsoft Entra ID and connected applications.
Identify and disable devices registered to the user, further minimizing risks of lingering access through mobile or workstation endpoints.
Assign the User.ReadWrite.All permission to your account or role, as this delegated permission gives your application or session the ability to manage users and invoke sign-in session revocation.
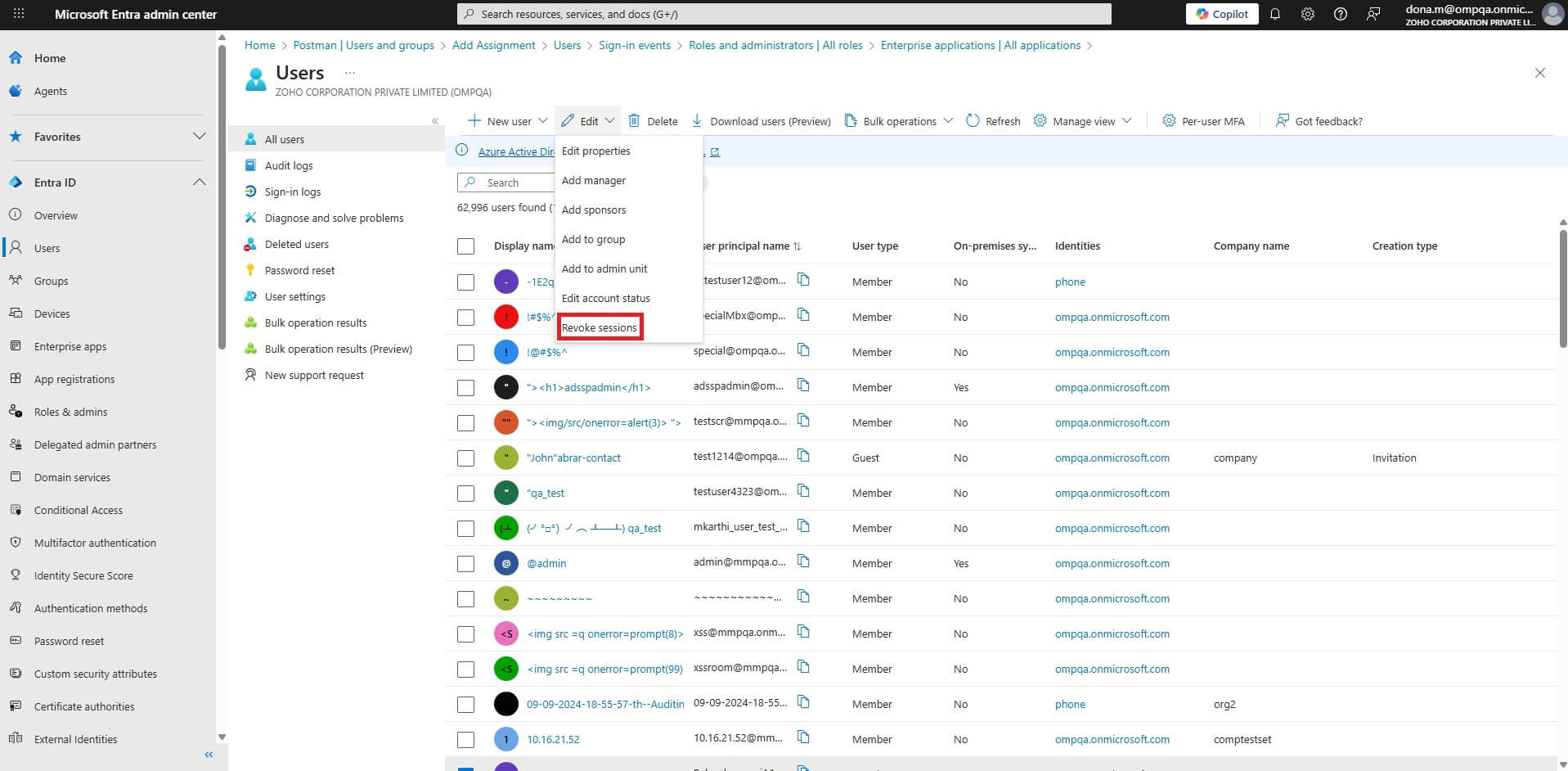
There is no native revoke all button. Instead, you can use Microsoft Graph PowerShell, the Microsoft Entra admin center, or ADManager Plus.
Using Microsoft Graph PowerShell
The following script revokes sessions for every user in the tenant:
Get-MgUser | ForEach-Object { Revoke-MgUserSignInSession -UserId $_.Id }
Using the Microsoft Entra admin center
In the Microsoft Entra admin center, you can select up to 60 users at once for bulk session revocation, allowing multiple user operations but with a maximum selection limit per action.
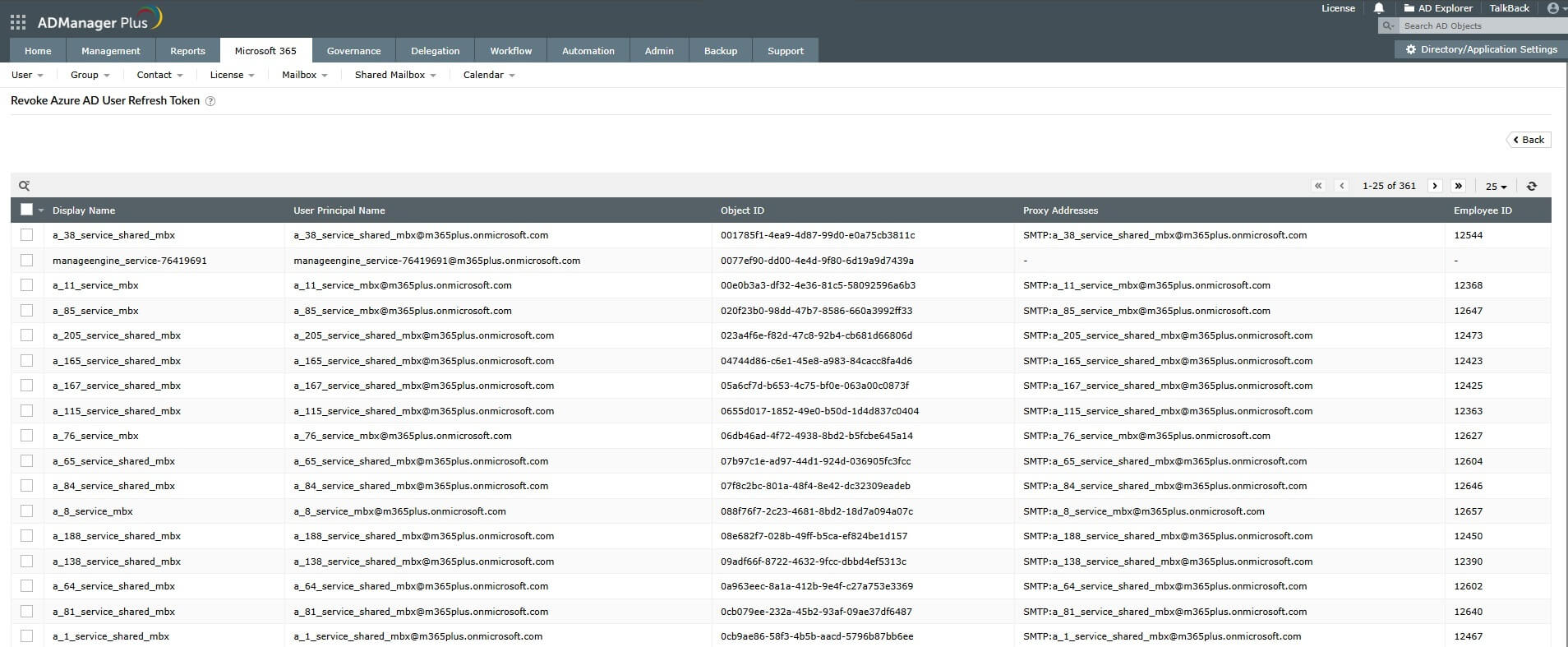
Using ADManager Plus
In ADManager Plus, you can select any number of users without limitation, or import a CSV to perform session revocation actions on an unlimited user set in a single workflow.
Direct revocation of access tokens is not supported in Microsoft Entra ID or ADManager Plus. Only refresh tokens can be revoked, stopping new sessions. Access tokens expire naturally. For urgent response, you can block sign-in or disable the user to cut off access immediately.