What is a denial-of-service attack?
A network's performance is only as good as its network traffic management system. With the increasing reliance on technology, it is becoming more important to ensure the security and efficient management of every element in your network.
An organization's network, no matter the size, is always prone to network security threats, and having a reliable network security system is crucial to establishing data integrity. The lack of a reliable, strong network security system leaves an enterprise vulnerable to many internal and external security threats, such phishing, malware, and data breaches. One such common threat is the denial-of-service (DoS) attack.
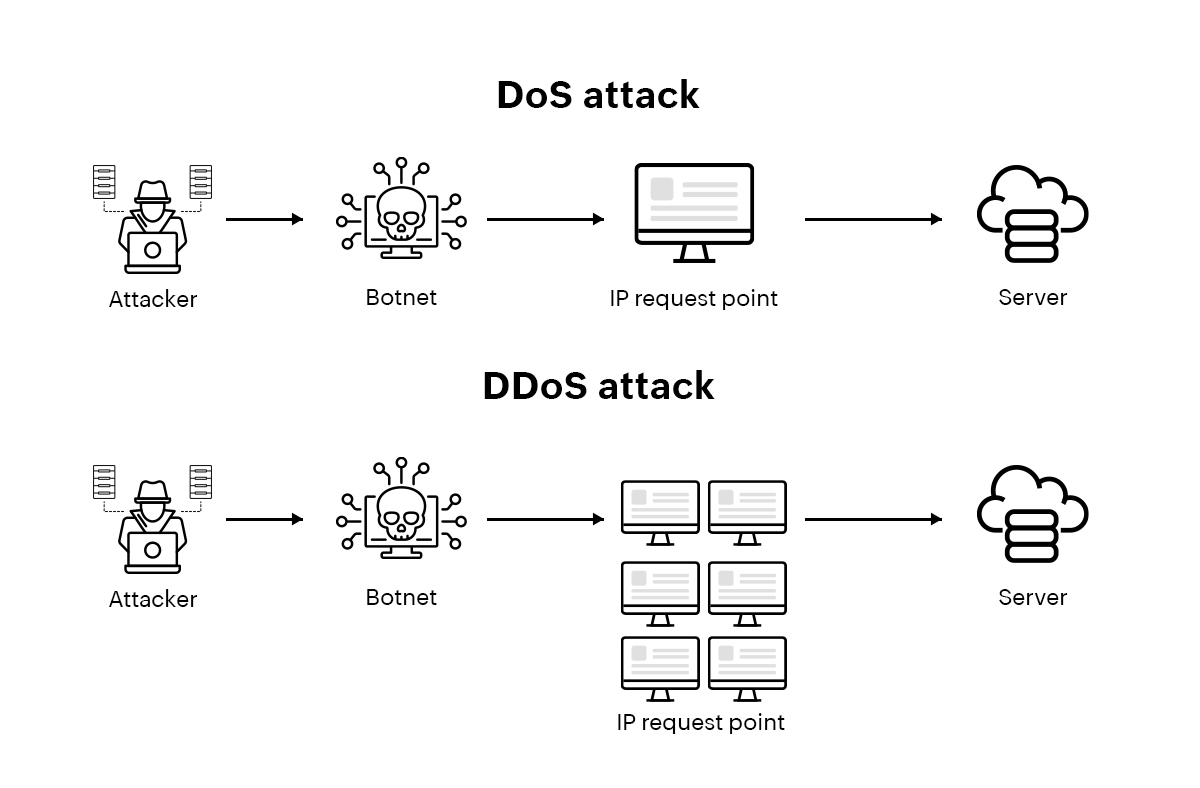
A denial-of-service attack is a type of cyberattack that disrupts connectivity to a machine, network, website, server, or any other network resource by flooding it with traffic or requests. The DoS attack overloads the targeted resource, making it unavailable to its intended users.
How does a DoS attack work?
A denial-of-service attack is performed by sending a huge volume of requests or traffic to the host server, by attacking vulnerable services, or even by bombarding network resources with requests from multiple sources (known as a distributed denial-of-service (DDoS) attack), temporarily or indefinitely disrupting services. While a denial-of-service attack primarily works by blocking the targeted machine or network from its intended users and requests by flooding it with traffic, there are different methods and types of DoS attacks that attackers implement.
Denial-of-service attacks
Flood attacks
These saturate the targeted network's resources by overwhelming it with large volumes of traffic, rendering it incapable of responding to legitimate requests.
SYN flood attacks
In a synchronize or SYN flood attack, the attacker sends a large number of incomplete requests to the targeted system. Here, the requests sent do not complete the handshake process. This way, the attacker overloads the resources, making them unresponsive to legitimate requests.
Smurf attacks
Smurf attacks, named after The Smurfs due to their ability to take down larger targets, involve sending ping requests to broadcast addresses. This results in all of the hosts in the network responding to the requests, thereby flooding the targeted system.
Ping of death
The attacker causes the targeted system to crash by sending ping packets that are larger than the size permitted by the protocol.
DDoS attacks
The attacker uses a network of computers to carry out the attack, making it all the harder to detect or stop.
Although they are carried out through these different methods with varying impacts based on different factors, DoS attacks all have one outcome and typically one intent: rendering the host or targeted resource unavailable to its legitimate requests and users. DoS attacks can be detected and mitigated with a strong network security system that incorporates firewalls, intrusion detection and prevention systems, and behavior analysis systems.
What is a DDoS attack?
In a DDoS attack, unlike a DoS attack, the incoming traffic flooding the victim originates from multiple different sources, making it impossible to stop the attack by blocking a single source of traffic. DDoS attacks are usually carried out using botnets.
Preventing a DoS or DDoS attack
The first known DDoS attack was a SYN flood targeting internet service provider Panix in 1996. DDoS attacks have gotten more and more sophisticated since then, with the Cloudflare and GitHub attacks in the early 2010s and the AWS and Google attacks in the 2020s. According to Research and Markets, "the global DDoS protection and mitigation security market is projected to grow from USD 3.9 billion in 2022 to USD 7.3 billion by 2027, at a CAGR of 13.2% during the forecast period."
Preventing and mitigating a DoS or DDoS attack can be extremely challenging. There are, however, various steps organizations can take to reduce the risks and impacts of DoS and DDoS attacks.
DDoS best practices: Detection, prevention, and mitigation
Implement network security best practices
A strong network security system that employs firewalls, intrusion detection and prevention systems, and traffic filtering techniques is vital to any organization's network. A network behavioral analysis tool that can carefully record and study the type, frequency, and size of these attacks helps reduce their impacts and plays an active role in prevention. An antimalware solution protects against malware infections that turn devices into part of a botnet.
Separate networks
Network segmentation involves dividing the network into smaller sub-networks to better compartmentalize monitoring and improve network performance and security. This is often effective in limiting the impacts of DoS and DDoS attacks.
Regularly update software and systems
Organizations should keep their network management and security systems up to date and equipped to deal with known attacks as well as weak links and vulnerabilities in their systems.
Deploy content delivery networks (CDNs)
CDNs help distribute traffic and reduce the load on the targeted system, making it more resistant to DDoS attacks.
Test incident response
Organizations should have an incident response plan in place for dealing with attacks as severe as DoS or DDoS attacks. This includes mechanisms for detecting, analyzing, and mitigating attacks. Regular testing and simulation drills help network administrators identify gaps in the incident response plan.
Implement rate limiting
Rate limiting puts a cap on the number of requests and connections allowed from a single IP address to prevent the exhaustion of resources, making the network immune to DoS and DDoS attacks.
Use a DDoS mitigation service
Organizations can work with a DDoS mitigation service to detect and block threats before they reach the targeted system. Such a service combines various techniques, including traffic analysis, rate limiting, and content filtering, to identify and restrict malicious traffic.
Implementing these measures can help network administrators and organizations reduce the risks of DoS and DDoS attacks as well as curtail the impacts if an attack does occur.
How ManageEngine NetFlow Analyzer helps
ManageEngine NetFlow Analyzer is a flow-based, highly scalable, full-featured bandwidth monitoring and network traffic analysis solution. It acts as an advanced network behavior analysis tool for small, medium-sized, and large organizations and runs on both Windows and Linux machines. It also supports a wide range of flow formats and devices.
NetFlow Analyzer's Security module enables network administrators to detect and analyze network security threats and anomalies. It uses state-of-the-art Continuous Stream Mining Engine™ technology for pattern matching and event correlation across multiple events, sensing attacks before they bring the entire network down. NetFlow Analyzer detects junk or anomalous traffic and classifies it into four problem classes based on predefined algorithms: suspect flows, bad source or destination, DDoS, and scans/probes.
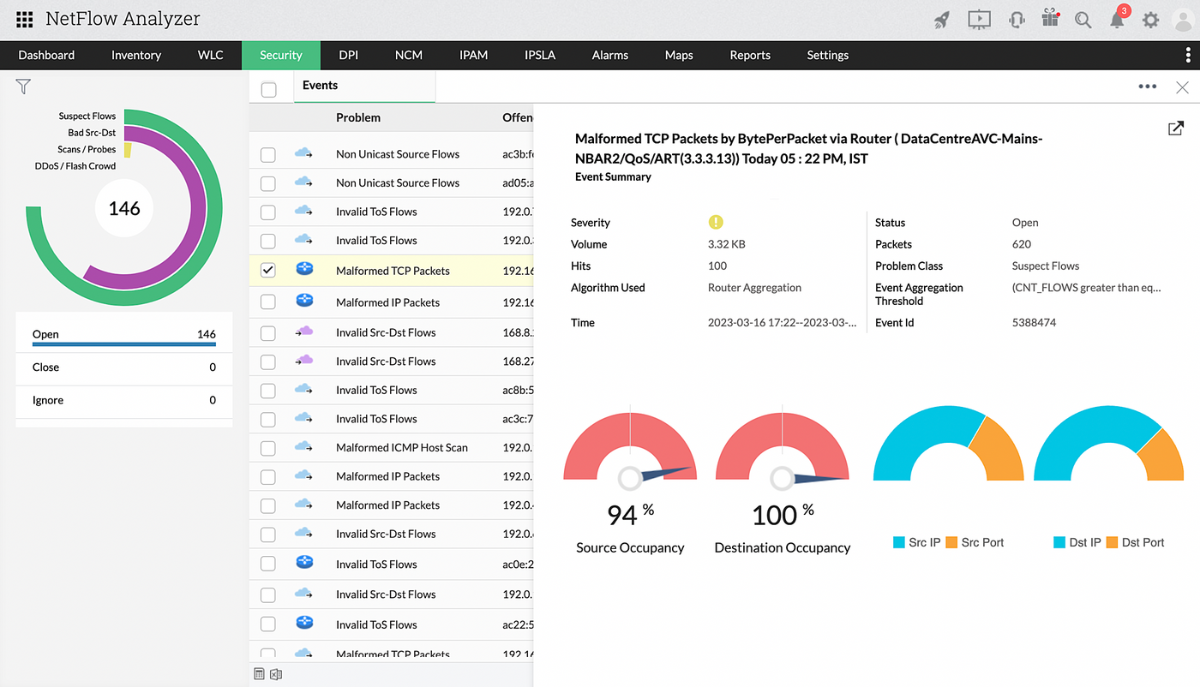
Click here to learn more about NetFlow Analyzer’s Security module. If you would like to learn more about implementing NetFlow Analyzer in your organization, we would love to speak with you about optimizing your network traffic management system with NetFlow Analyzer. Schedule a free, personalized demo or download a free, 30-day trial of NetFlow Analyzer now!