Securepoint Firewall Log Analyzer
With a package of features, Firewall Analyzer's reporting capability for Securepoint firewall appliance fit like a glove enabling you to secure and strengthen Network security. Firewall Analyzer let's you to centrally collect, archive, analyze Securepoint's security device logs and generate forensic reports out of it.
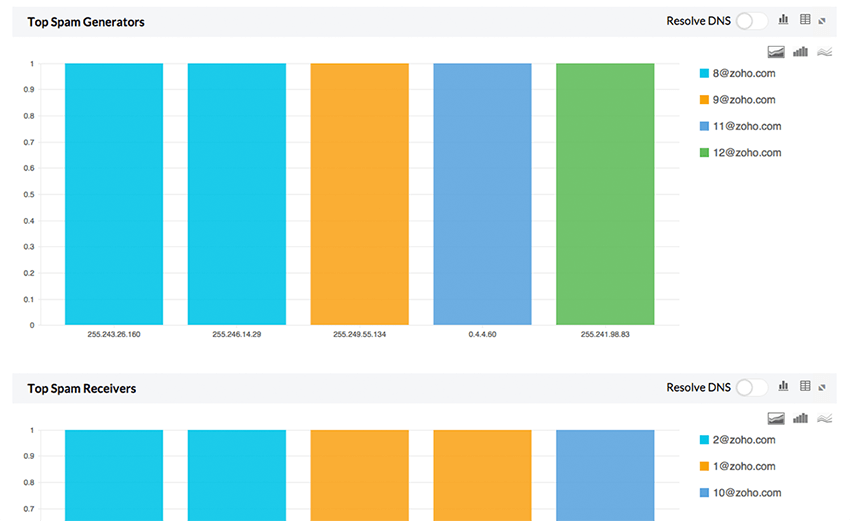
Securepoint bandwidth monitoring reports
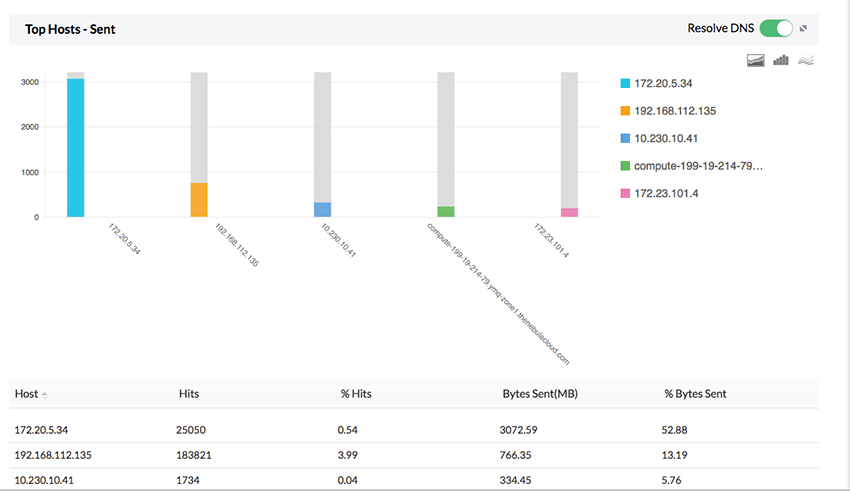
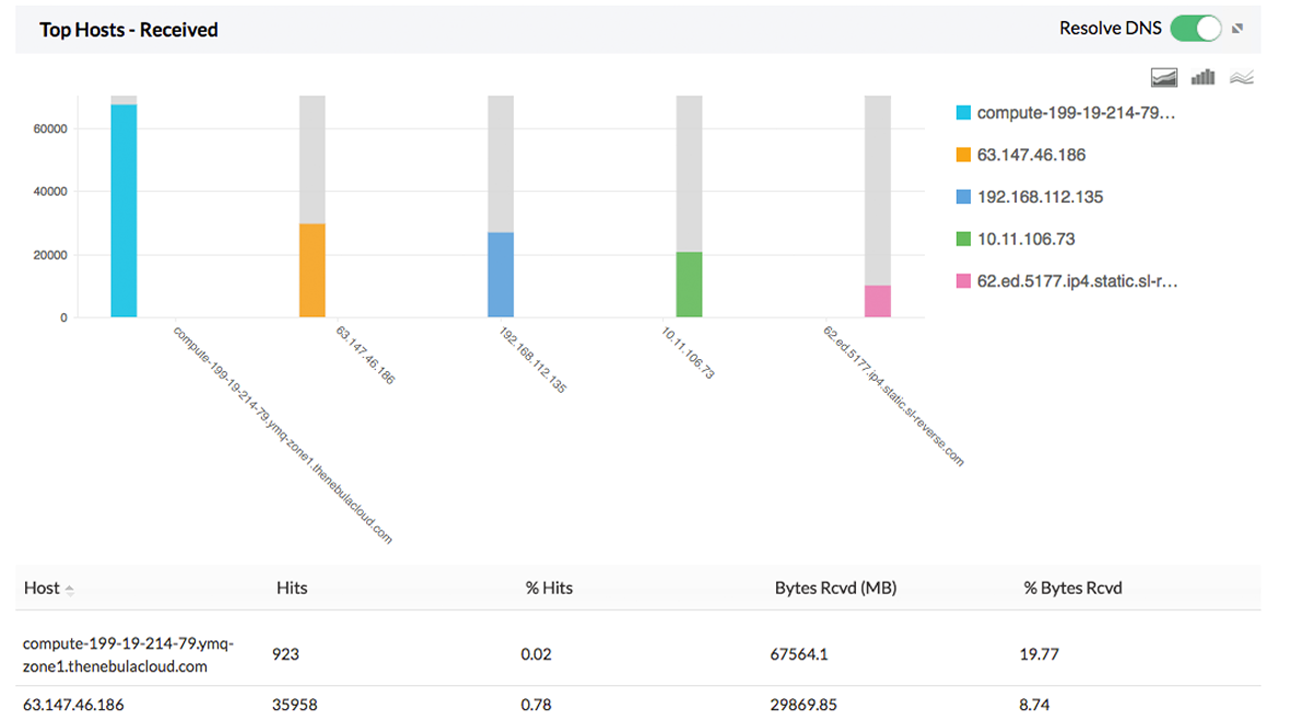
Firewall Analyzer for Securepoint provides you an unique way to monitor the bandwidth usage of the network. Firewall Analyzer measures network bandwidth based on the analysis of logs received from Securepoint. Firewall logs are collected, archived, and analyzed to get granular details about bandwidth across Securepoint firewall. You need not deploy any hardware probes or collection agents to get these details on bandwidth.
Securepoint security reports
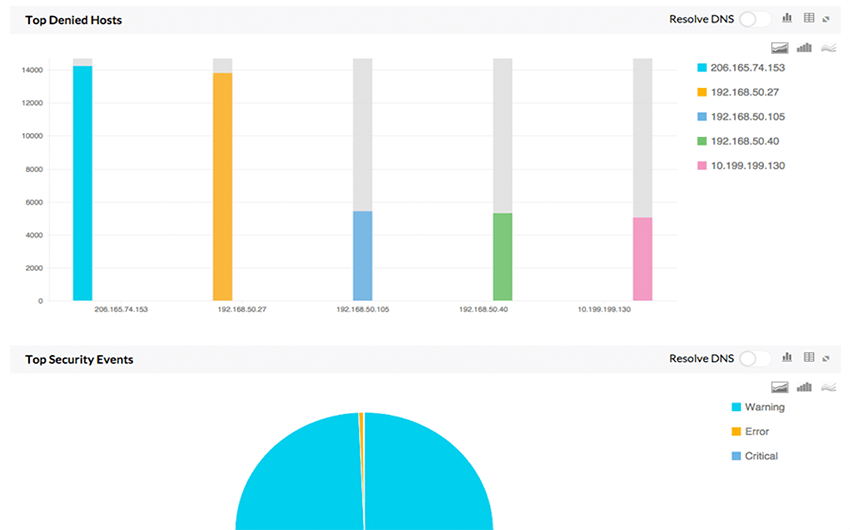
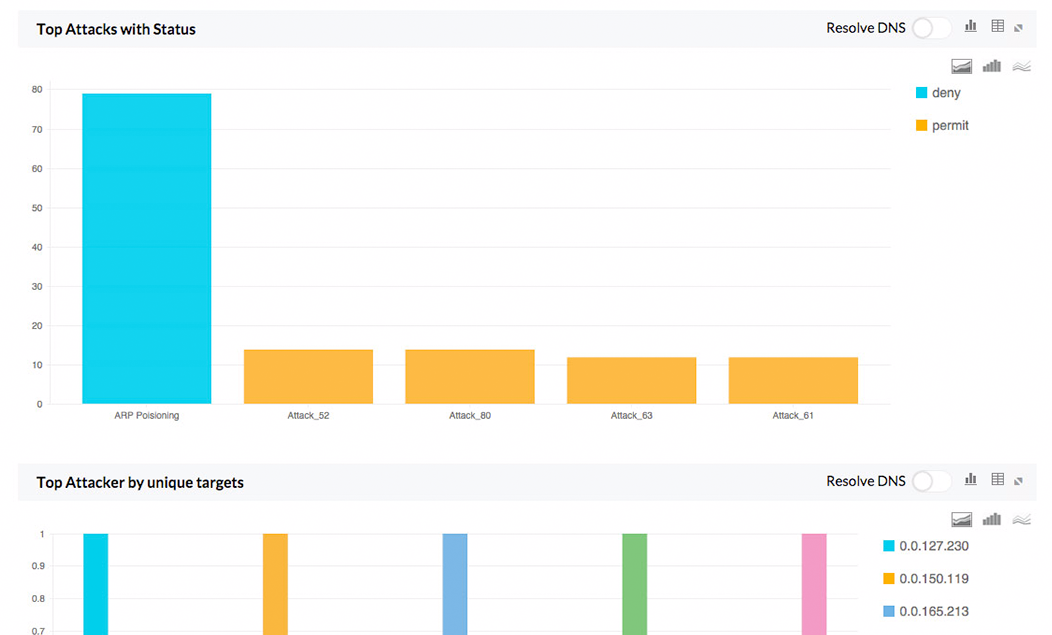
Firewall Analyzer for Securepoint provides instant security reports on viruses, attacks and security breach in your network. These reports instantly show you the viruses active on the network, the hosts that have been affected, and more. With these reports it is easier for IT to do business risk assessment, detect problems and resolve them as soon as they are found.
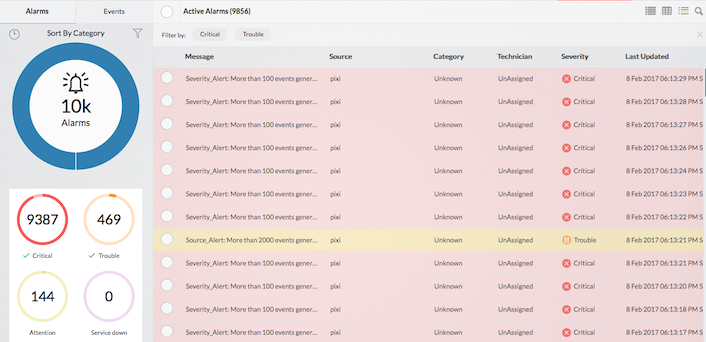
Securepoint firewall alerts
Apart from exhaustive firewall reports with respect to network security, Firewall Analyzer offers comprehensive alarms and their notifications.
Alarms can be generated for an anomalous security criteria, bandwidth values, and any normal criteria of security interest.
Alarms can be notified via email and SMS. It can trigger a script to achieve various threat mitigation activities. Alarms are also displayed in the UI screen.
Securepoint supported versions
| Company | Firewall Version | Other Log |
|---|---|---|
| Securepoint | Securepoint UTM Firewalls |  |
Thank you for your feedback!