Juniper Firewall Log Analyzer, Configuration and Rule Management
Firewall Analyzer is a Juniper firewall analyzer tool. With it's reporting capability for Juniper devices, you can now collect and analyze Juniper firewall logs and generate security and forensic reports with ease.
- Juniper firewall log forensics
- Juniper firewall VPN monitoring
- Juniper firewall policy management
- Juniper firewall bandwidth monitoring
- Juniper firewall configuration management
Juniper firewall log forensics
Firewall Analyzer is a Juniper firewall management software. It enables you to search Juniper firewall raw logs to track errors whenever a security event occurs. You can convert Firewall Analyzer's advanced search option, which focuses on raw Juniper firewall logs, into report profiles for easier analysis. You can also import archived logs to perform security incident mining on raw logs.
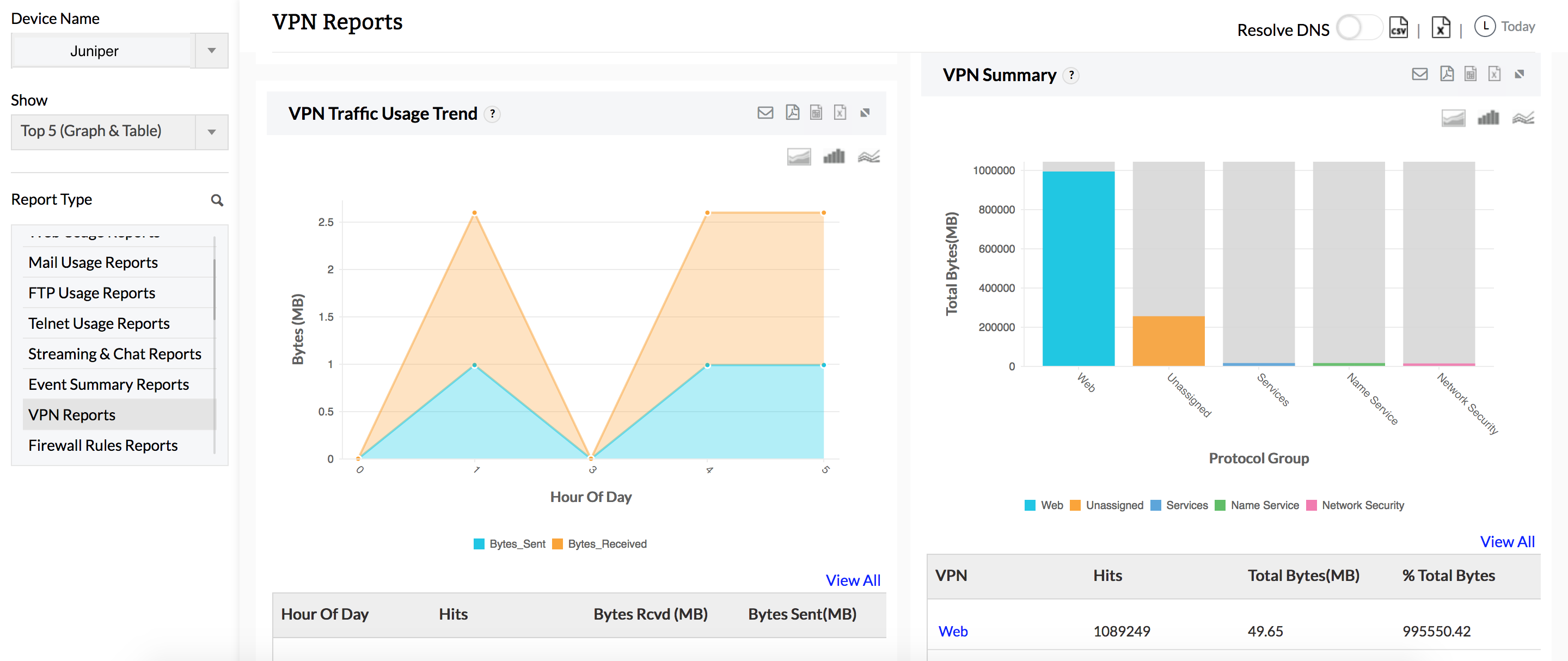
Juniper VPN monitoring
Juniper VPN Reports give detailed statistics on Juniper VPN usage. Juniper VPN usage reports include drill down details on top VPN hosts, top protocols used by the VPN, and bandwidth used by the VPN during peak and off-peak hours. Juniper VPN trend reports show trends in the number of VPN connections accessed through the Juniper firewall on a historical and current basis. VPN trends are especially useful in troubleshooting VPN connections, and identifying security risks.
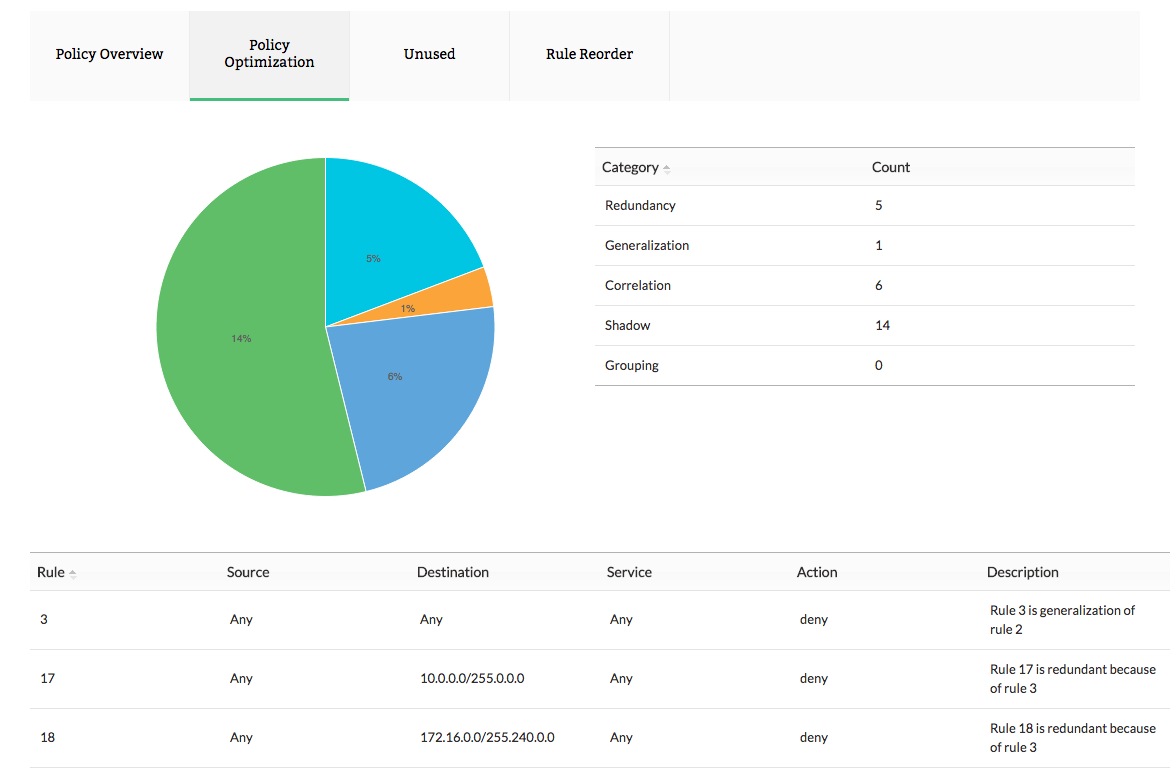
Juniper firewall policy management
Firewall policy anomaly reporting captures and rectifies anomalies in Juniper firewall rules, policies and securing the network from external attacks. Firewall Analyzer, a Juniper firewall monitoring tool, generates Juniper firewall rules, policy reports. These reports help you not only optimize policies and plug security holes, but also enhance the performance of your firewalls. The less complex you can make the rule set, the faster traffic will be evaluated by the system, and the easier it will be for network engineers to manage access on a day-to-day basis.
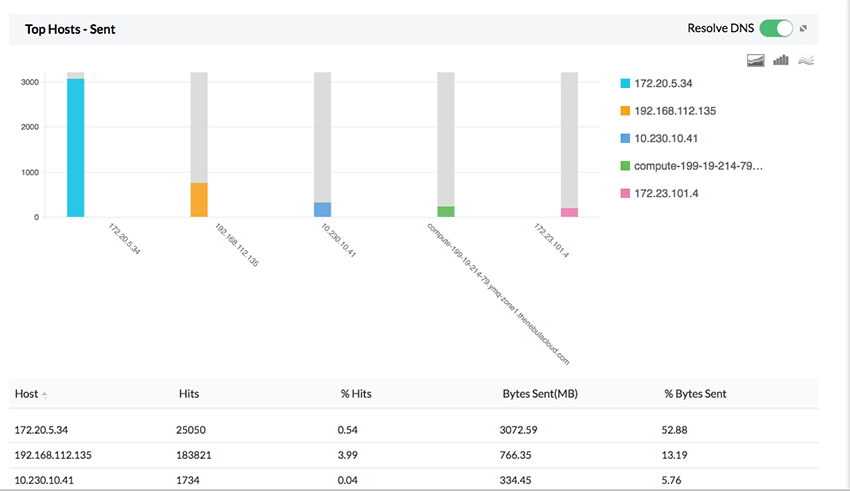
Juniper firewall bandwidth monitoring
Monitor internet traffic in real-time with Firewall Analyzer Live Reports. Using the Juniper firewall logs Firewall Analyzer, you'll get granular reports on user-based and protocol-based bandwidth consumption, and you'll be able to identify intranet and internet traffic usage, which host is taking up the most bandwidth, and so on. The Juniper Firewall Traffic Reports can help you determine which employees are misusing their internet allotment, and will notify you about anomalies such as sudden spikes in their bandwidth usage.
Request for a free personalized demo
Juniper firewall configuration management
Monitor and track any changes on implementation details in SRX devices. Firewall Analyzer, a Juniper configuration tool, offers an exhaustive set of configuration reports that help address security audit, configuration audit, and compliance audit requirements. The change tracker ensures that all the configurations and subsequent changes made in the devices are captured periodically, and are stored in the database.
The Change Management Report provides detailed information on various categories of reports such as the:
Running Configuration Changes Report, which provides information on differences between any two running configuration changes.
Configuration Changes Report, which helps track the changes between running (current) configurations and startup (default) configurations.
Refer the help document to configure Juniper firewalls to forward logs to Firewall Analyzer.
Thank you for your feedback!