Check Point Firewall Analyzer
Firewall Analyzer can analyze, report, and archive logs from your Check Point Firewalls. Firewall Analyzer has been OPSEC™ certified by Check Point and has joined the OPSEC Alliance.
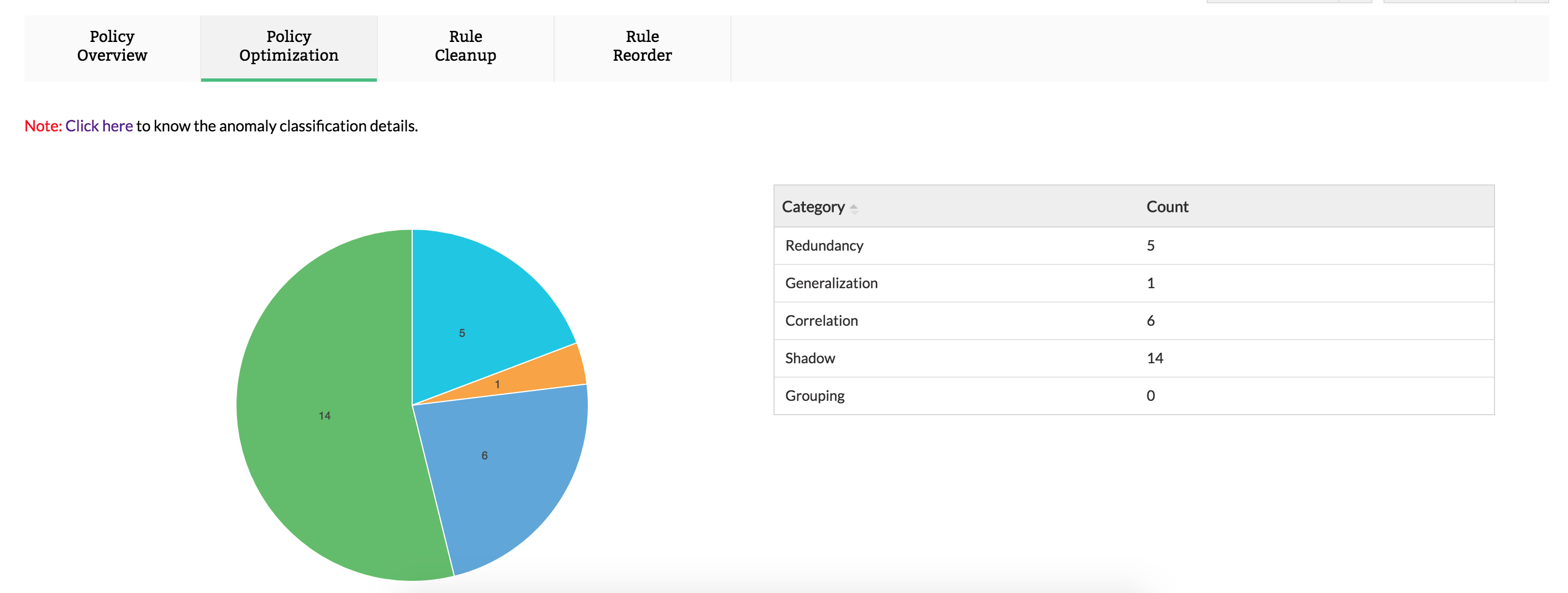
Check Point rule management
Firewall policies and rules control the traffic between your company's LAN and the internet. So, how they work determines whether your sensitive information remains inside the company's domain or gets out into the world. Firewall Analyzer allows you to monitor the effectiveness of the rules in Check Point. Use the policy overview report to get a snapshot of these different rules. You can also get a specialized report on the top rules that are used to govern enterprise traffic, or use the log report to identify anomalies that could make your system susceptible to security threats.
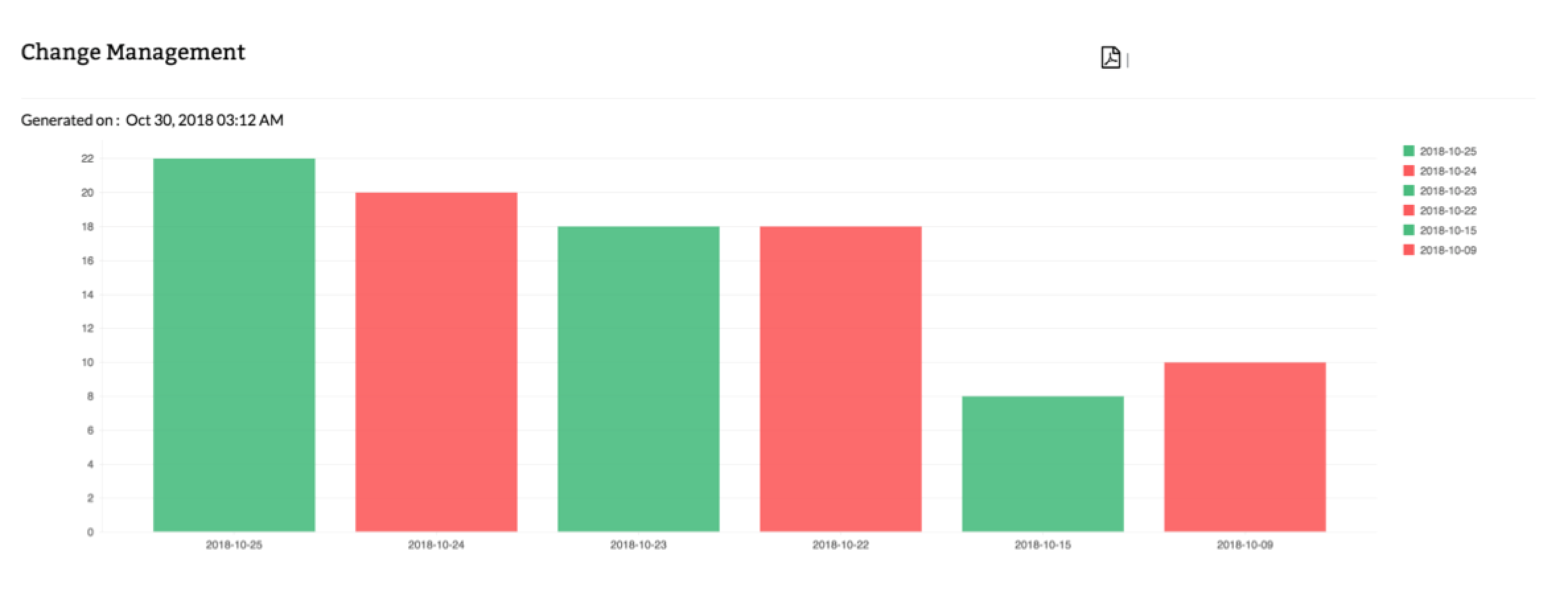
Check Point configuration change management
This report helps you find 'who' made 'what' changes, 'when' and 'why'. Not only that, it alerts you in real-time on your mobile phone when changes happen. This report ensures that all the configurations and subsequent changes made in the Firewall device are captured periodically and stored in the database.
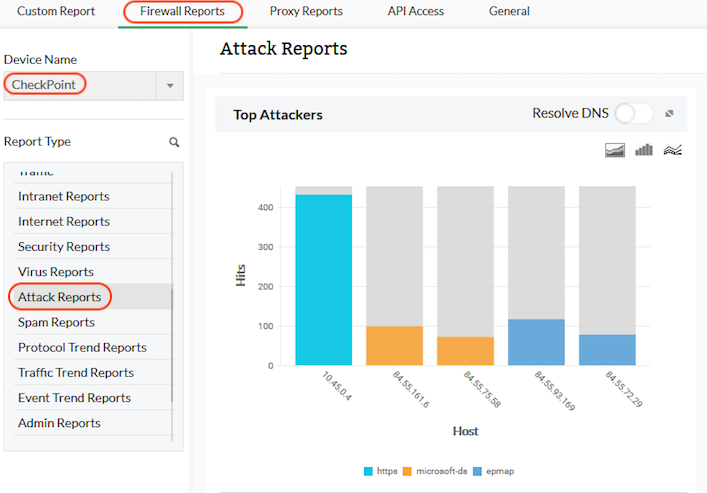
Check Point firewall rule analyzer
With Firewall Analyzer, you can access predefined Checkpoint firewall reports that help with analyzing bandwidth usage and understanding security and network activities. Study your firewall's vulnerability level using reports on top denied hosts, blocked URL hits, attacks, viruses, affected hosts, spam, and receiving hosts.
Request for a personalized demo
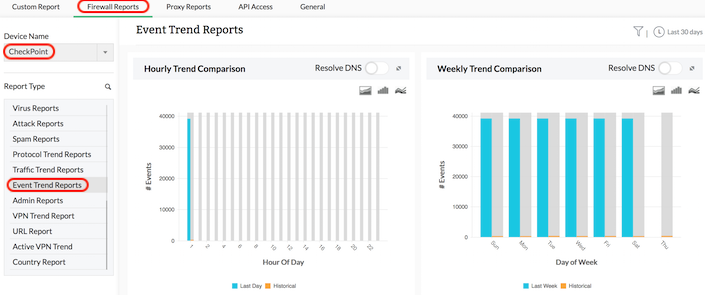
Check Point trend analysis
Trend reports in Firewall Analyzer trace patterns in network behavior and bandwidth usage over time. Analyzing trend reports offers insight into the nature of website traffic or network traffic, which helps you make better decisions on capacity planning, business risk assessment, bandwidth management, traffic shaping, and the security posture of your network.
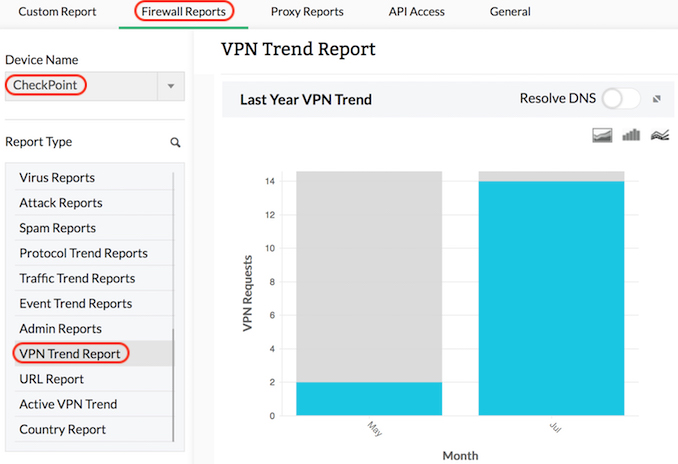
Check Point VPN monitoring
VPN trend reports show trends in the number of VPN connections accessed through the Check Point firewall on a historical and current basis. VPN trends are especially useful in troubleshooting VPN connections, and identifying security risks.
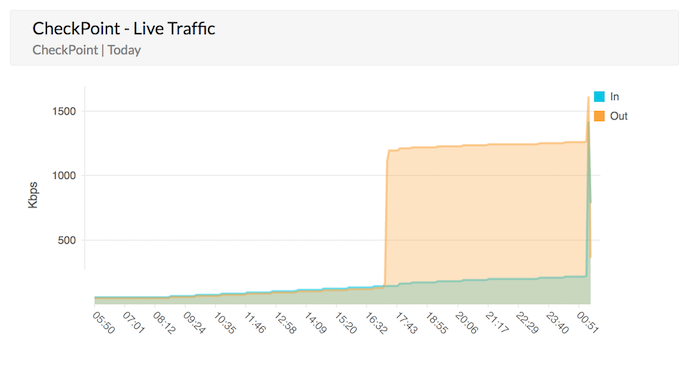
Check Point real-time bandwidth monitoring
Firewall Analyzer provides a unique way to monitor the internet traffic of your network in real time. Firewall traffic data is collected and analyzed to get granular details about the traffic through each firewall. You don't need any probes or collection agents to get these traffic details.
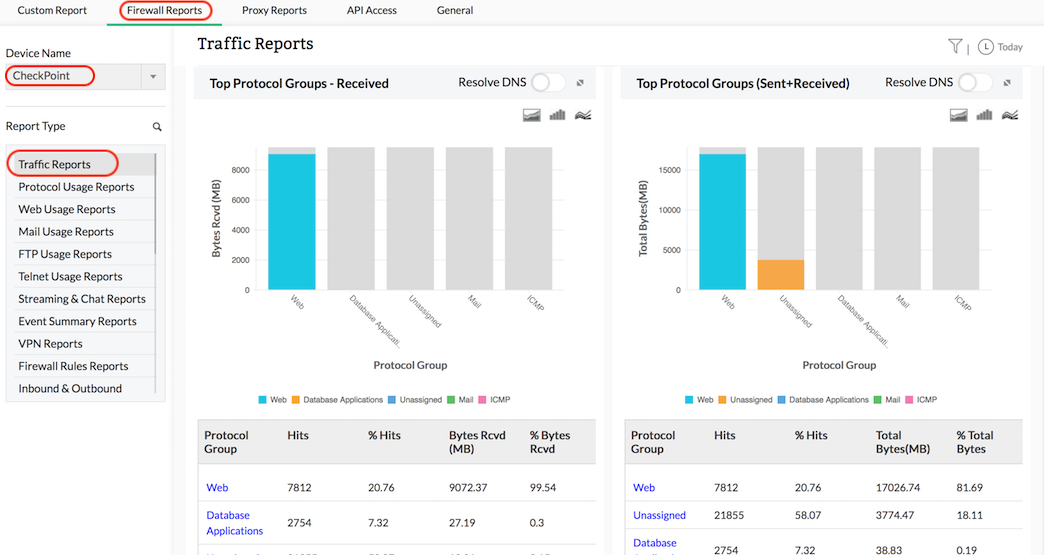
Check Point network traffic analyzer
Firewall Analyzer evaluates logs from different network firewalls to measure network traffic. Firewall logs are collected, archived, and analyzed to get granular details about traffic across Check Point firewall devices.
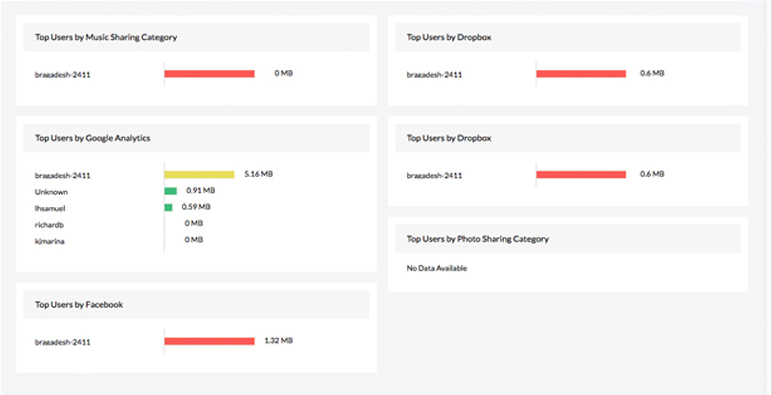
Check Point firewall monitoring
You can minimize the use of bandwidth by monitoring the internet activity of your employees. Fine-tune firewall policies to block or restrict bandwidth-guzzling websites, which helps control employee internet use. This will help ensure there's plenty of bandwidth to keep your business running smoothly.
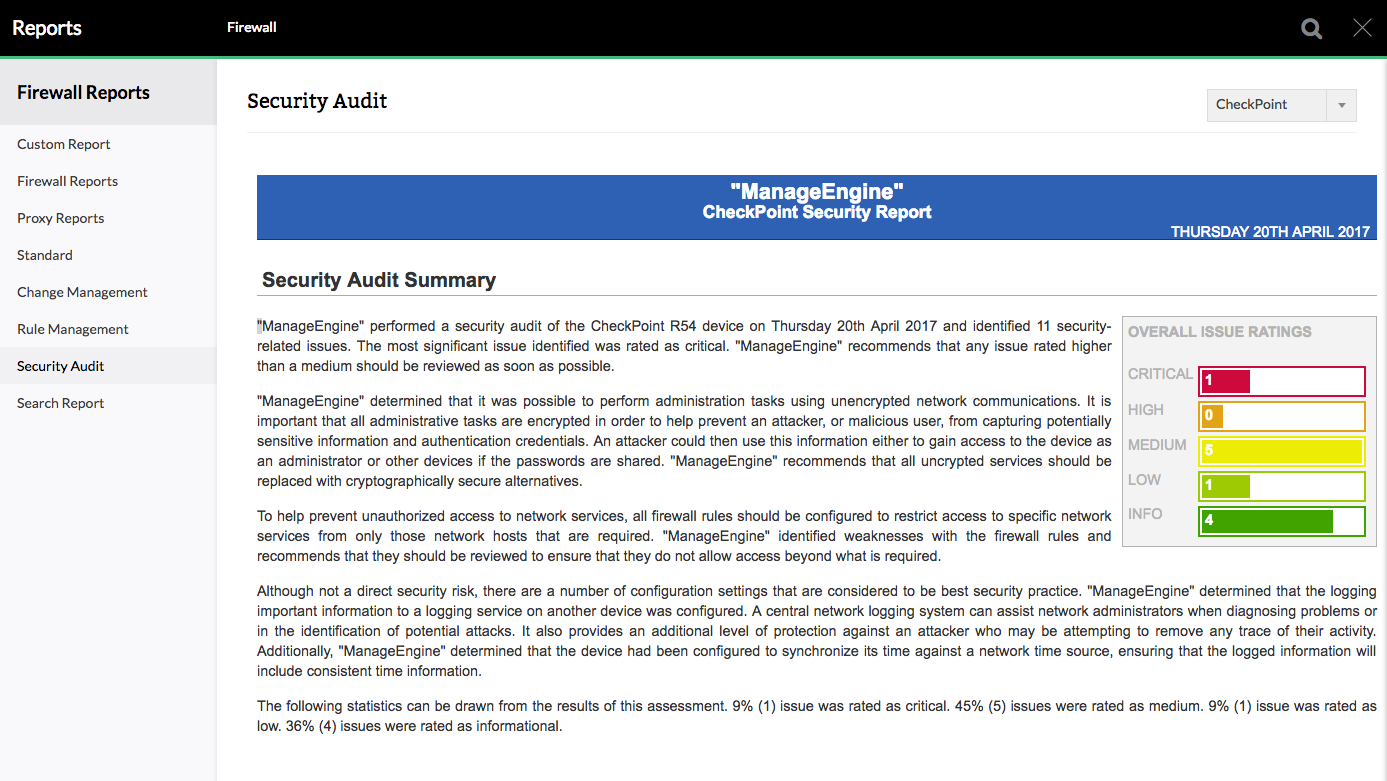
Check Point firewall audit checklist
Firewall Analyzer provides elaborate Check Point firewall compliance reports. These reports help you configure the Firewall rules, which will prevent potentially dangerous access to network and allow only those network hosts that are required. The issues are assessed and the results are presents as statistics.
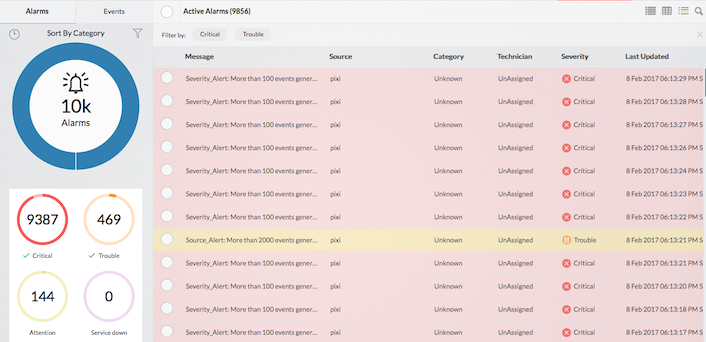
Check Point firewall alerts
Apart from exhaustive firewall reports on network security, Firewall Analyzer offers comprehensive alarms and notifications. Generate email or SMS alarms for any security criteria of interest as well as when bandwidth breaches a set value. These alarms can trigger a script to achieve various threat mitigation activities. Alarms are also displayed in Firewall Analyzer's UI.
Check Point supported versions
| Company | Firewall/Version | WELF Certified | Other Log Format |
|---|---|---|---|
| Checkpoint | Log import from all versions and LEA support for R54 and above VSX Firewalls - Virtual Edition supported |  |
Steps to Configure
For detailed steps about how to configure Firewall Anlayzer with Checkpoint's firewall appliance you can refer this link here
Featured links
Firewall Reports
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!