

The policies created in the BitLocker module must be associated with specific targets for deployment. To know more about creating and configuring BitLocker policies, refer to this page. This document outlines the steps for creating and configuring BitLocker policies, as well as automating BitLocker deployment.
Once a policy is created, associate it with specific targets. Supported target types include static computer groups (CG), static unique CG, and dynamic CG. To learn more about custom groups and their configuration, refer to this page. Kindly follow these steps to deploy Bitlocker policies:
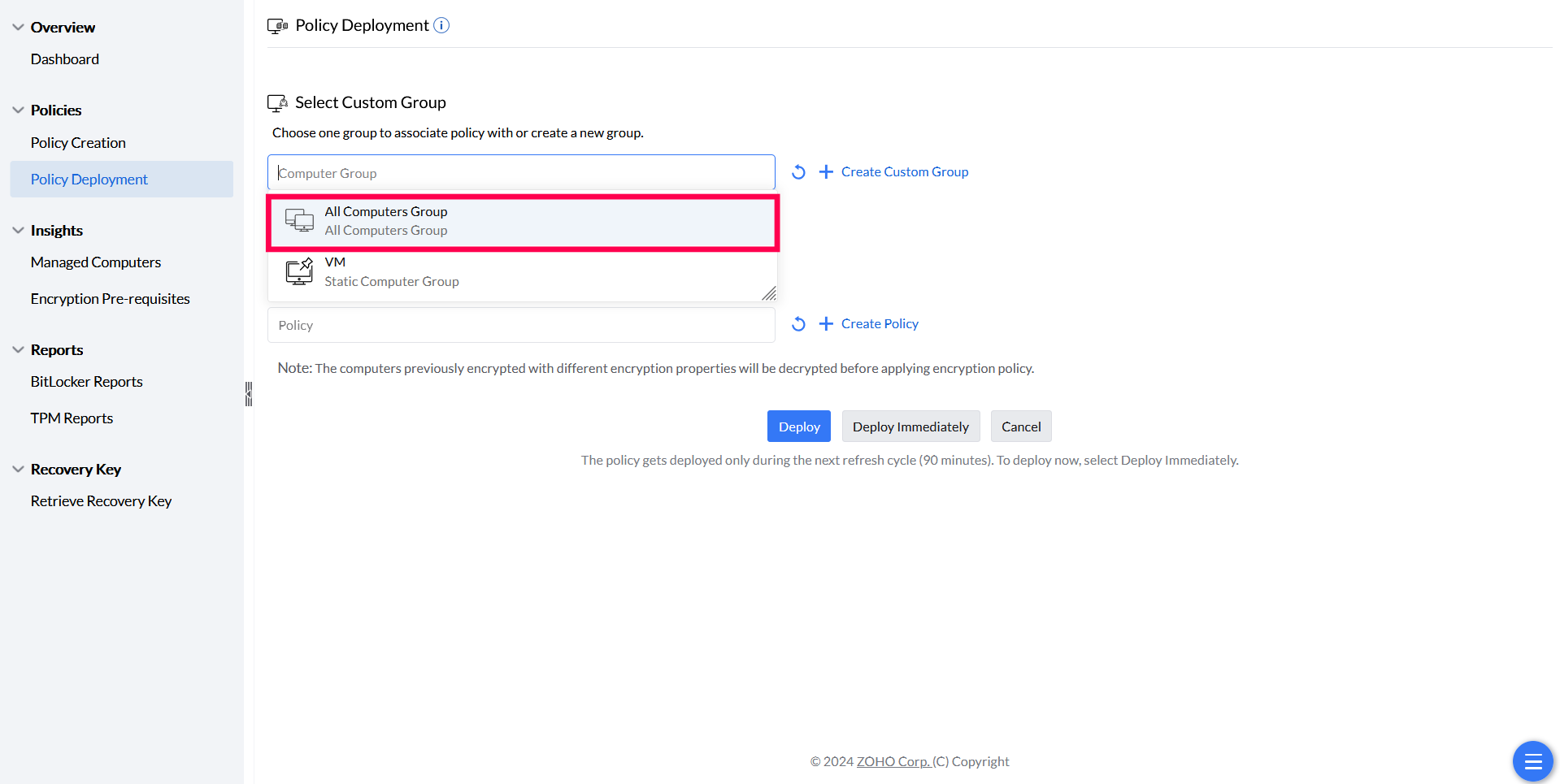
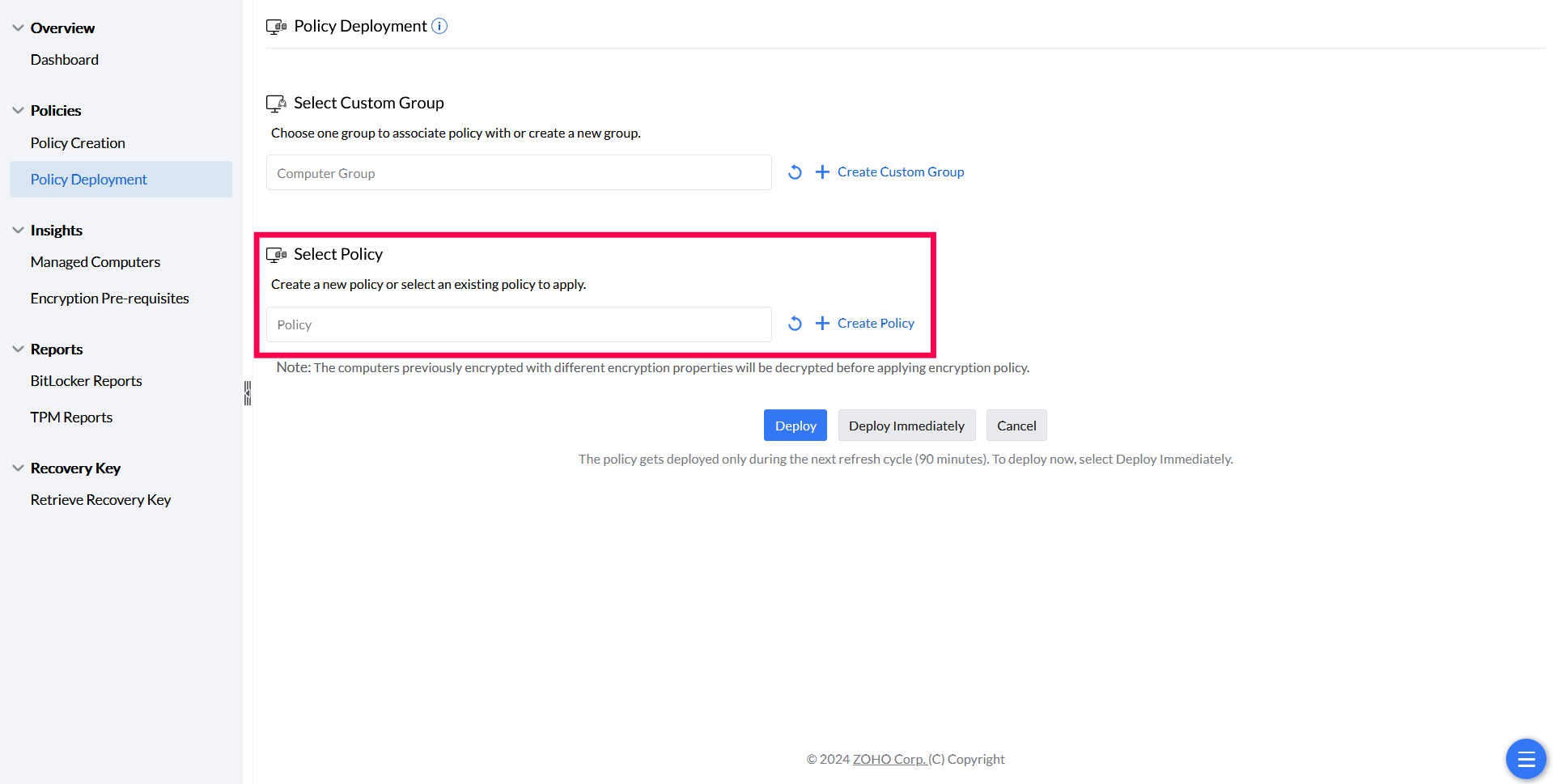
Point to note: There is an upper limit of 200 computers for this option
After deployment, you can view the list of associated computers and their policy deployment status. This section also includes remarks or reasons for any failures. Ensure that encryption is either in progress or fully completed.
You can check the encryption status for each machine in the Managed Computers section.
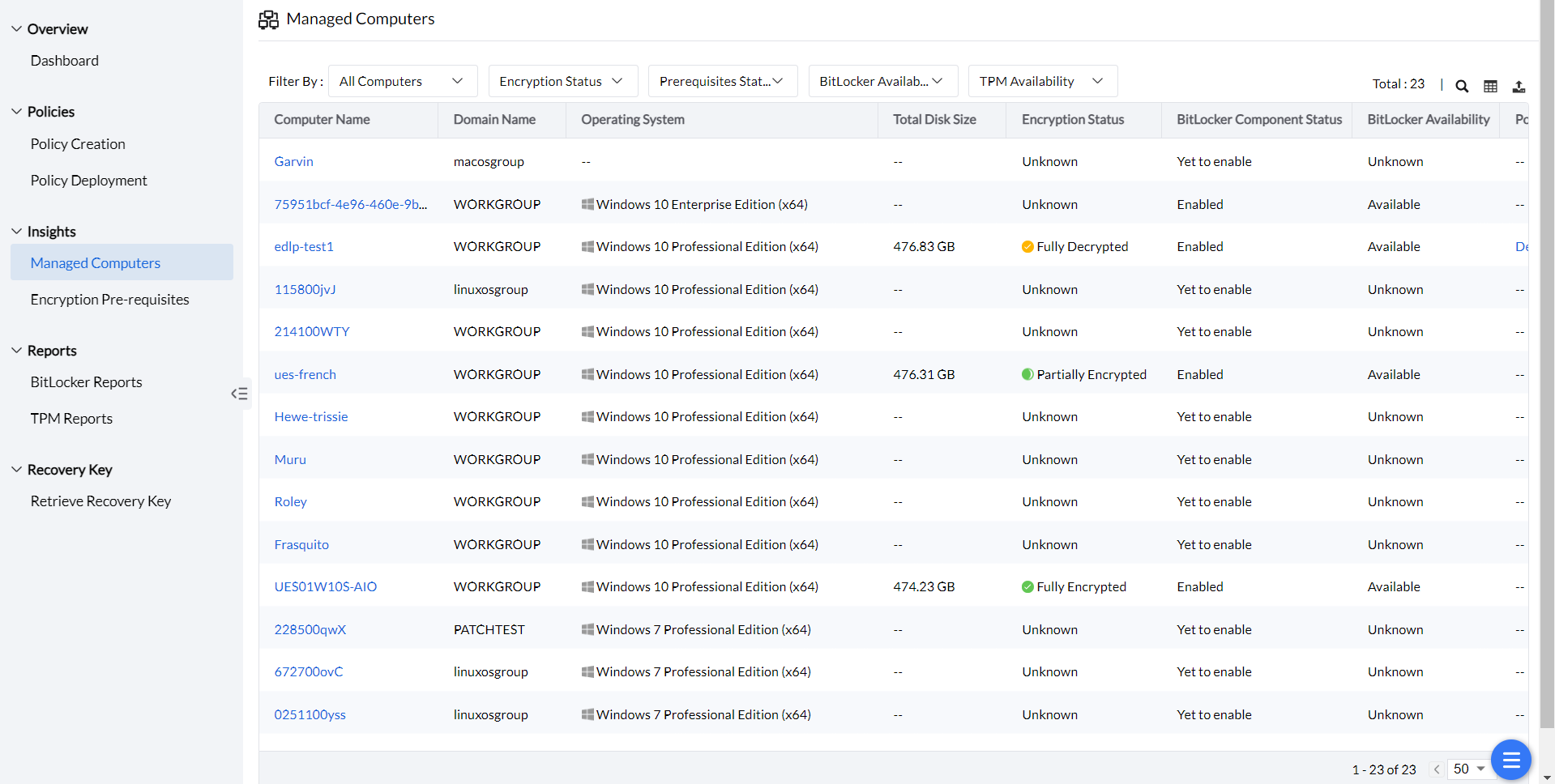
If a machine remains fully decrypted even after successful policy deployment, it may be due to two reasons: The encryption setting requires user input of a PIN or passphrase, or it is a non-TPM machine where a passphrase is mandatory. Encryption failures may also arise from environmental issues, leading us to the next section, Encryption Pre-requisites.
In the encryption pre-requisites section, you can view machines that cannot proceed with encryption due to errors such as BIOS mode incompatibility, WMI failures, or TPM ownership issues. Each case is documented, with remediation steps provided. The machines are also differentiated based on the errors.
The encryption process begins only once the password has been set. The criteria for creating a password is as follows:
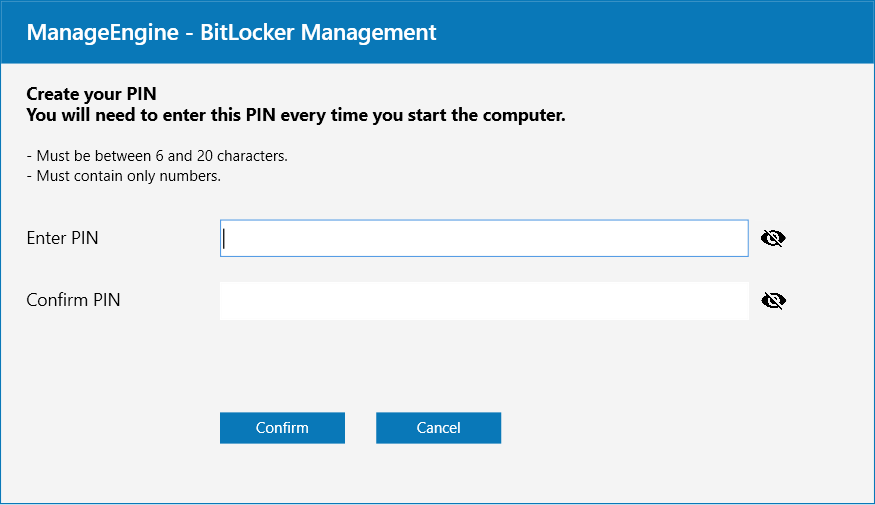
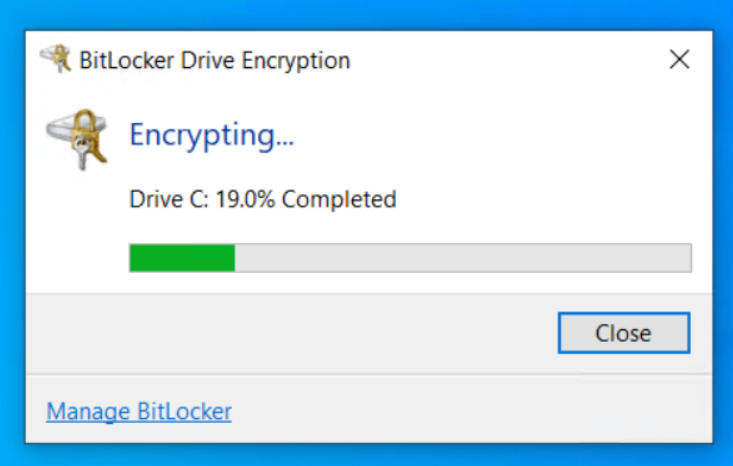
Once encrypted, the password has to be input on every bootup.
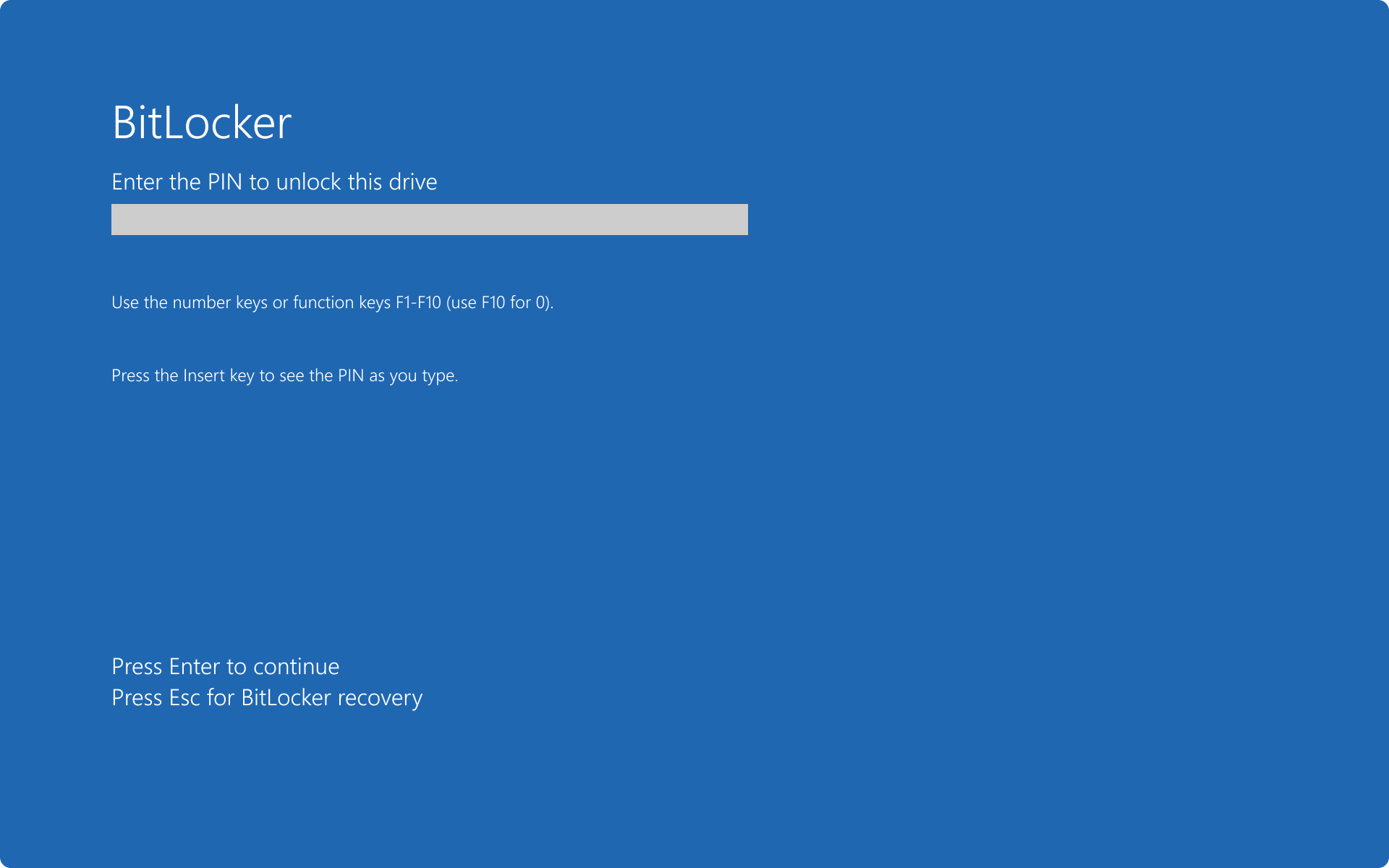
If you have any further questions, please refer to our Frequently Asked Questions section for more information.