The Reports section maintains a complete record of application control events and system actions, ensuring traceability, compliance, and informed decision-making through detailed, exportable logs and summaries. To access the reports, navigate to Reports under the Application Control module.
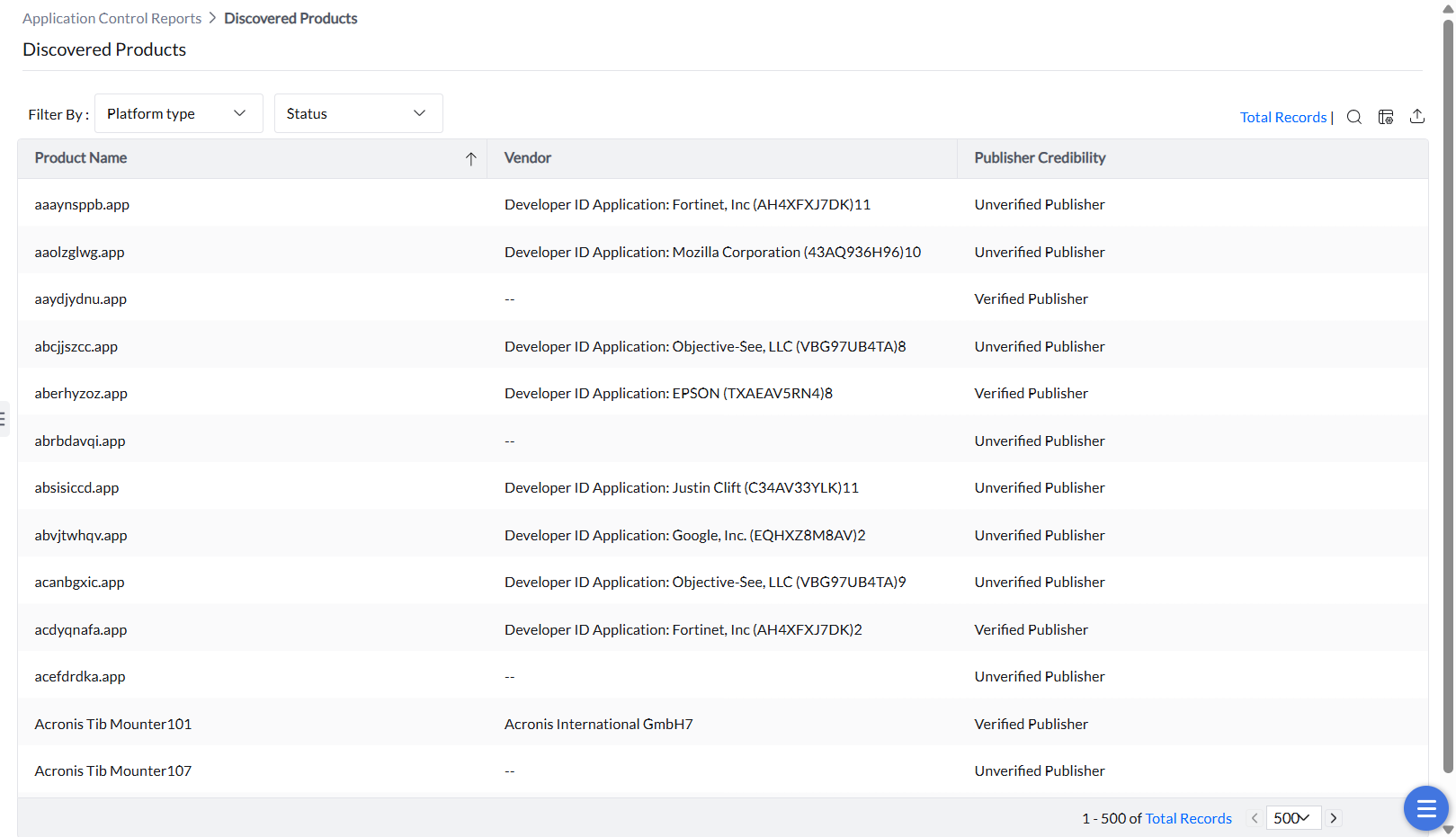
The reports under Discovered Applications summarize all the applications and executables detected in your network—giving administrators a concise view of applications appearing in the environment for assessment and policy action.
All the discovered applications of different vendors can be viewed under this report. They can be filtered by OS platform (Windows or Mac) and by whether they are associated or unassociated to an application control policy.
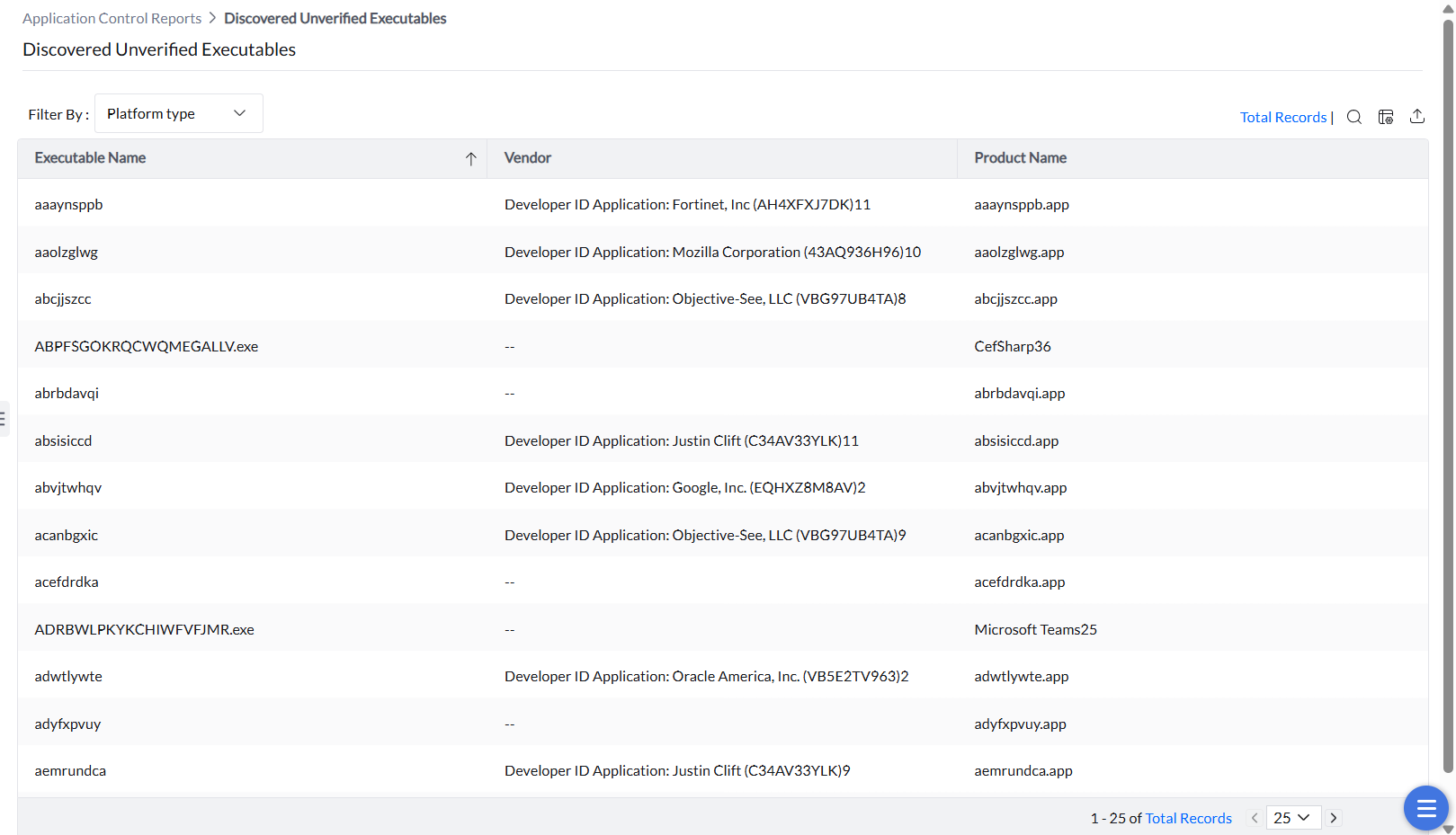
Applications are composed of several executable files. To ensure authenticity, each executable is digitally signed by the vendor. Under this report, the unverified executables detected can be viewed. This is crucial for network security, as any executable with a tampered digital signature will be prevented from executing. They can be filtered by OS platform (Windows or Mac).
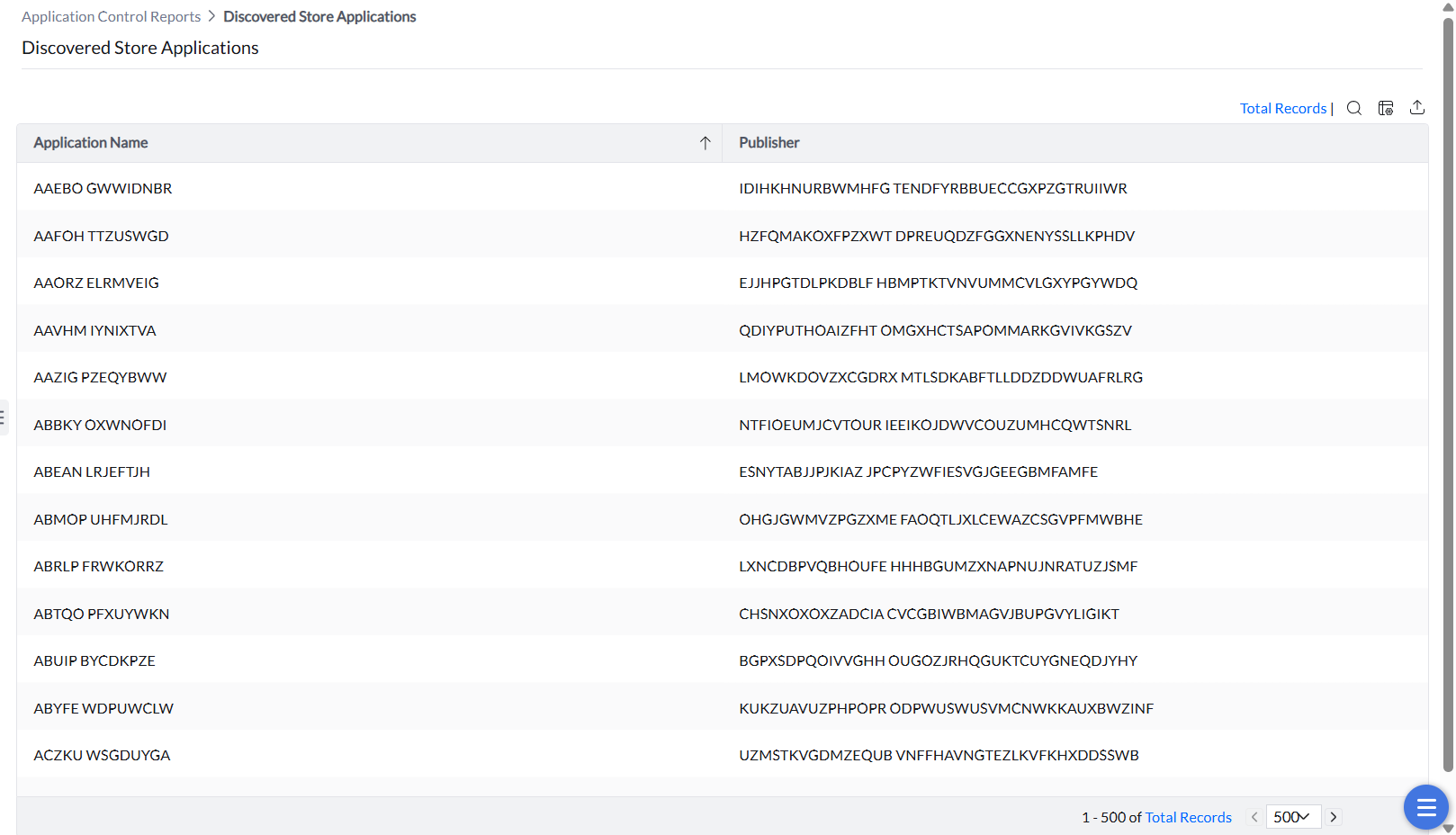
All the detected Windows 10 and 11 store applications that are running in the managed endpoints can be viewed under this report.
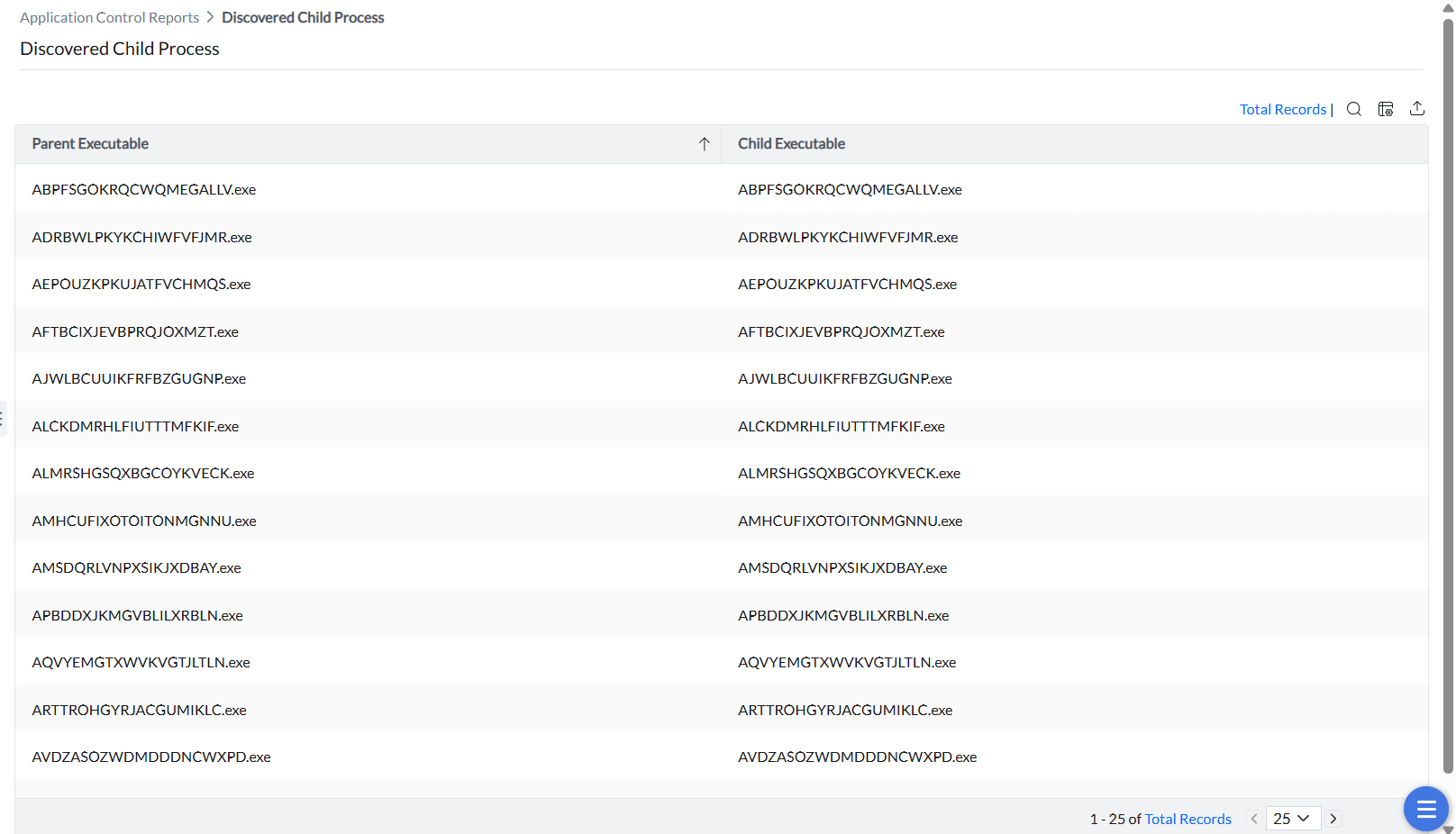
Child processes are processes initiated by running applications. While they can be vulnerable, this setting enables trusted applications to create child processes securely. By allowing only authorized applications to spawn child processes, you can significantly reduce the risk of security breaches. The child processes of the applications would run even if they are blocked.
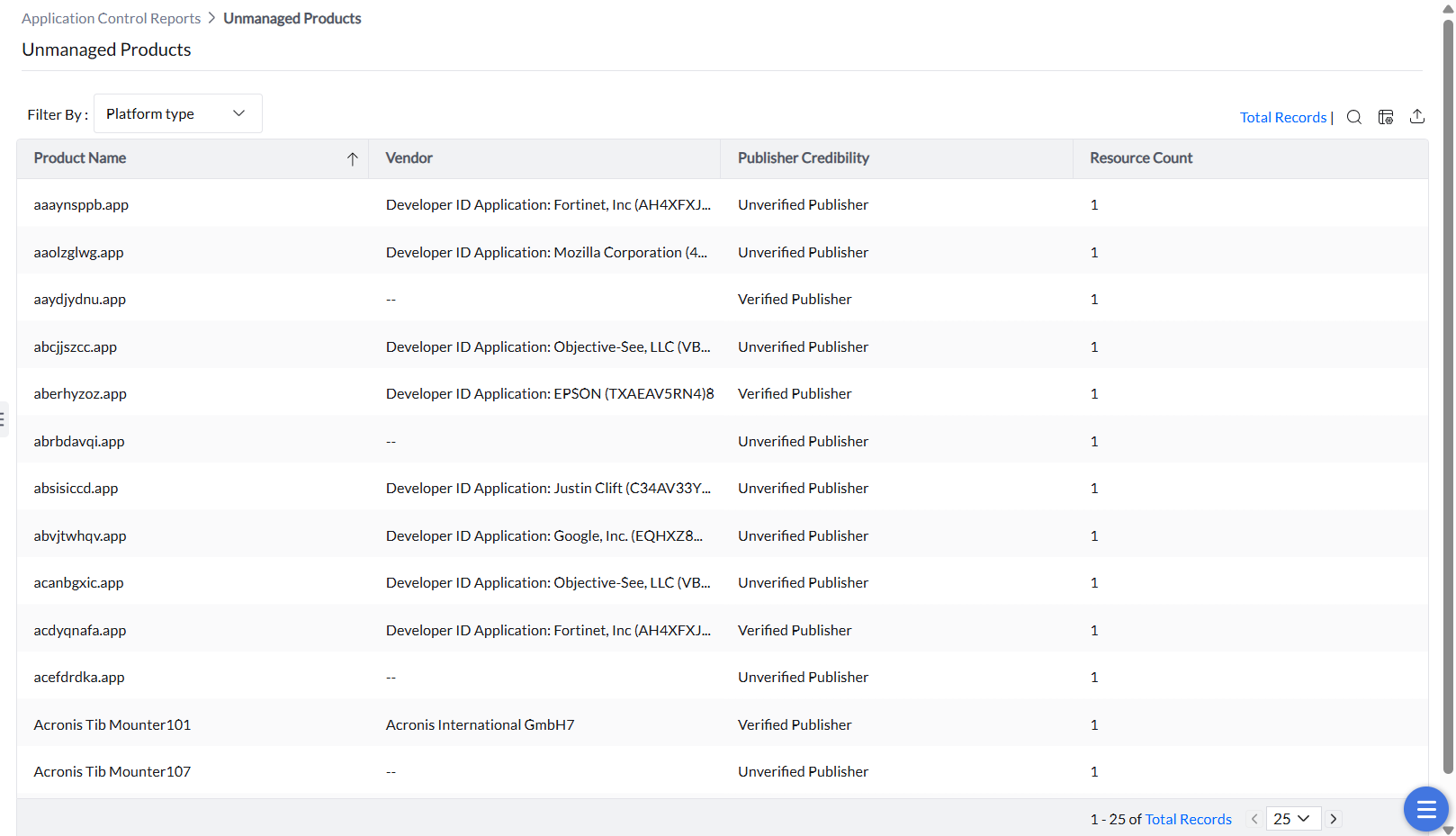
These reports summarize all the unmanaged applications, executables, and store apps in your network. They provide overview into the applications which are not included in any application control policy, helping administrators identify and bring unmanaged software under control.
All the unmanaged applications which are not governed by an application control policy can be viewed under this report. They can be filtered by OS platform (Windows or Mac).
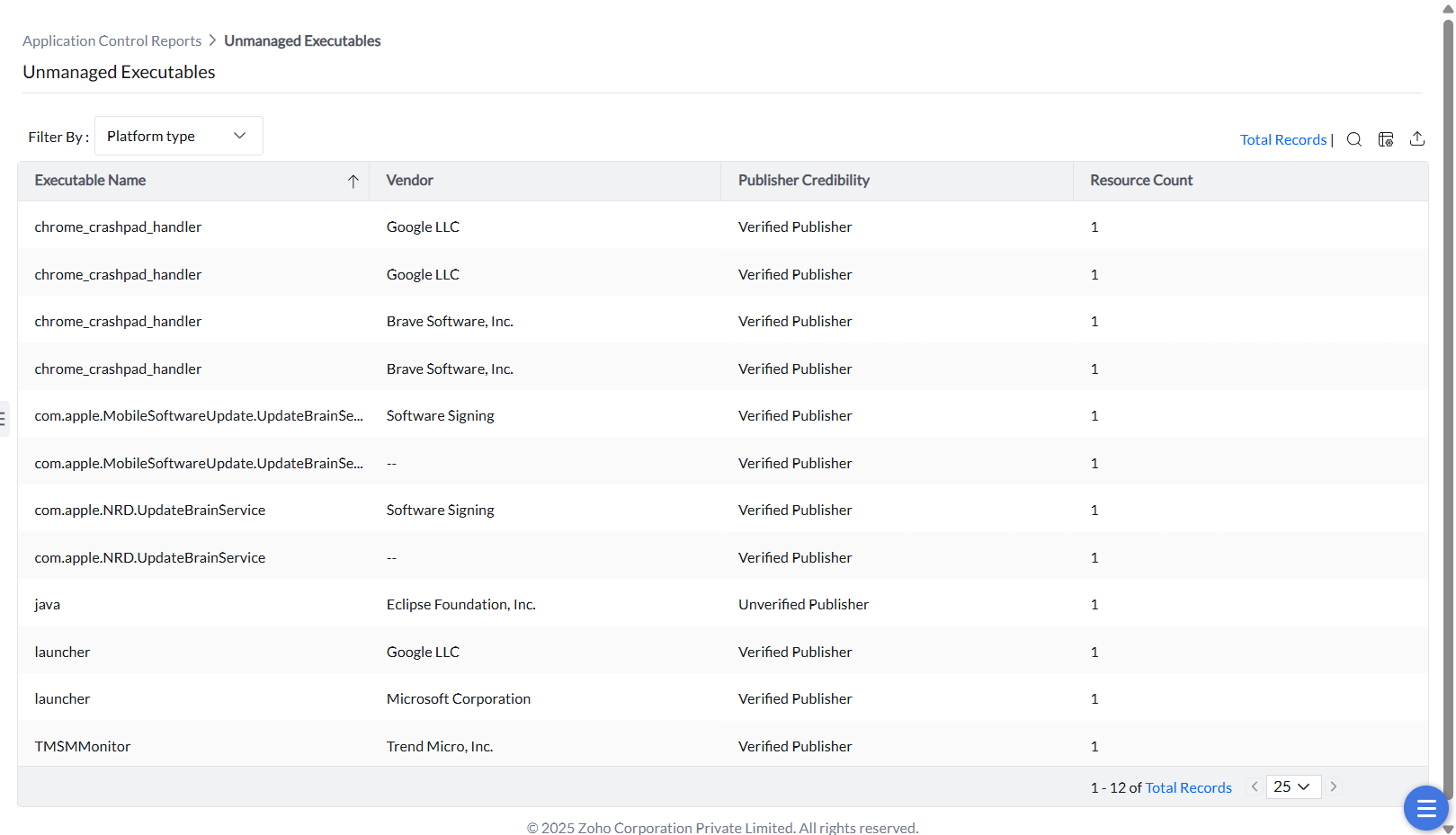
All the unmanaged executables which are not included in an application control policy can be viewed under this report. They can be filtered by OS platform (Windows or Mac).
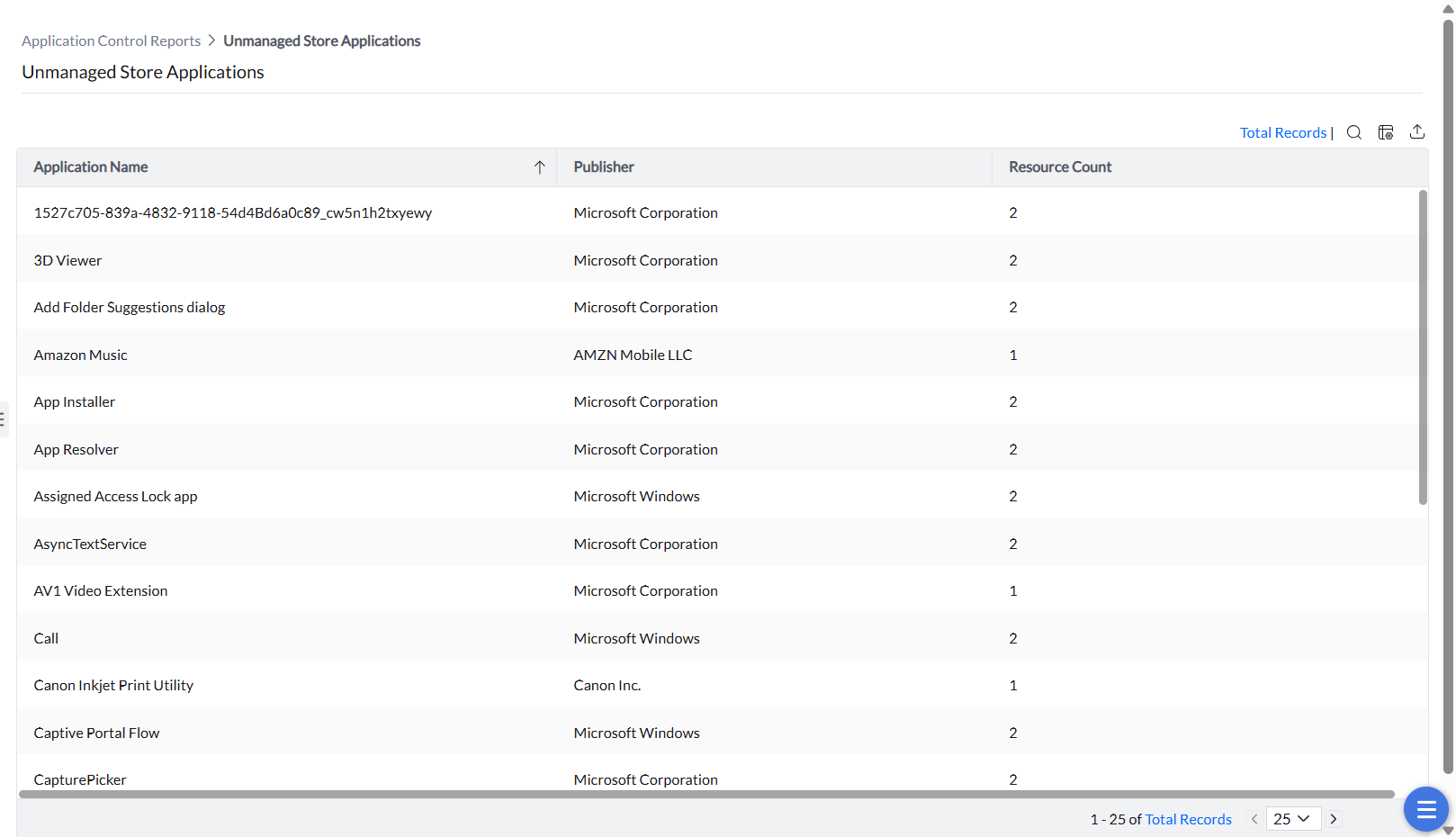
All the unmanaged Windows 10 and 11 store applications that are not governed by an application control policy can be viewed under this report.
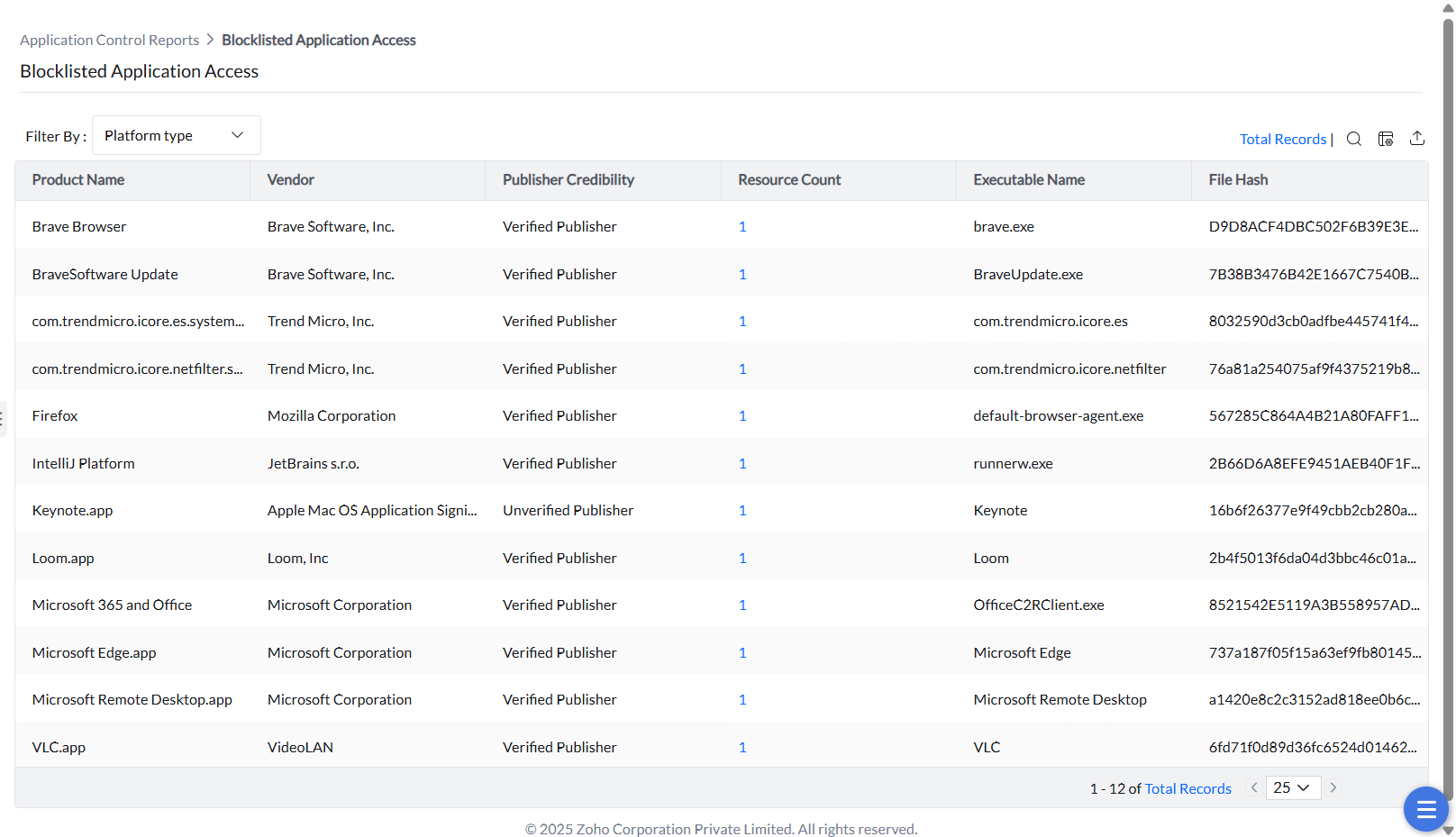
These reports track critical events such as access attempts to blocklisted apps or store apps, elevation requests with stated reasons, and applications running with administrator privileges, providing evidence for policy enforcement and security investigations.
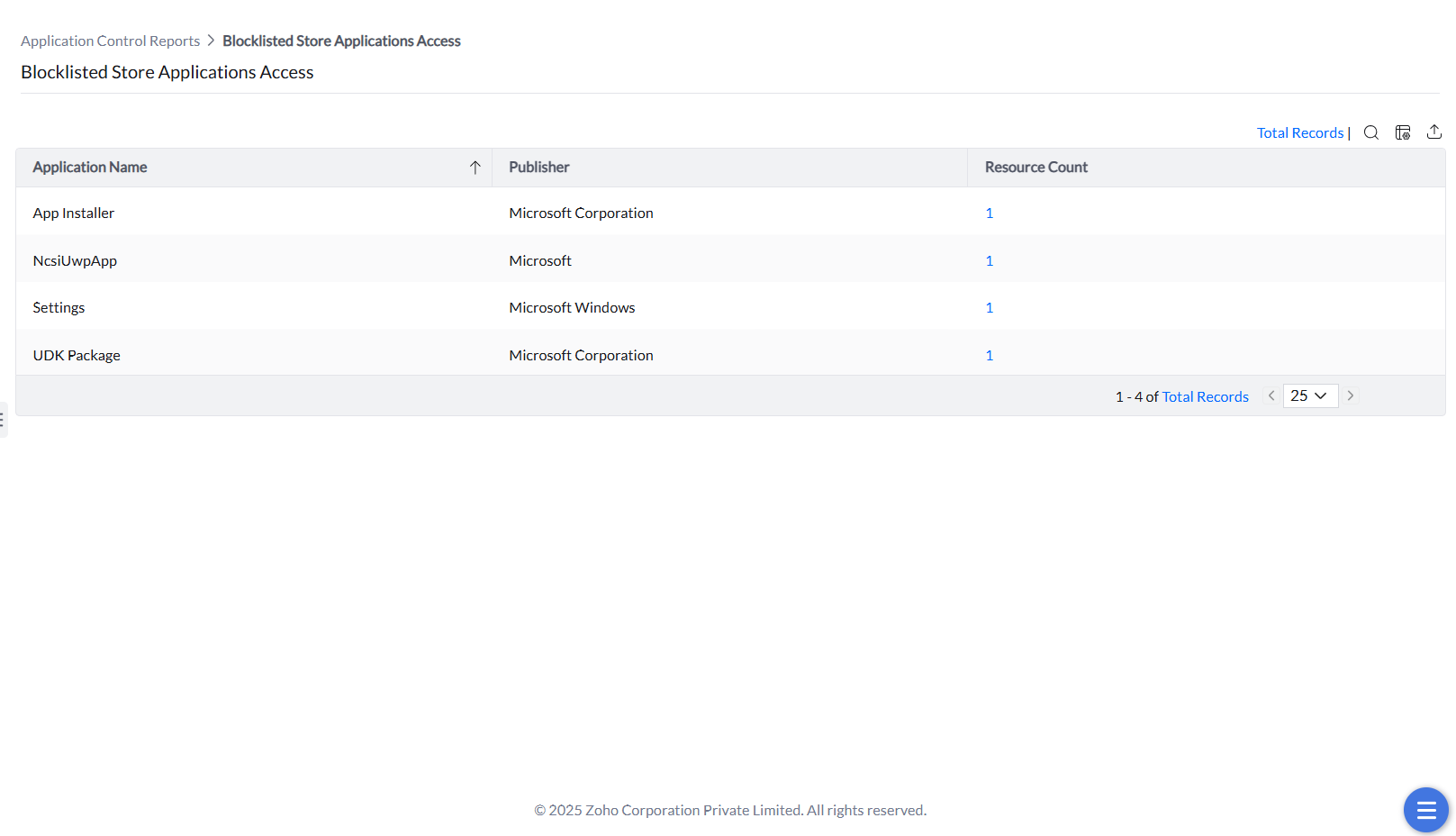
This report logs attempts to launch applications explicitly blocked by policy for compliance and threat monitoring.
This report tracks execution attempts of prohibited store apps to enforce store-specific restrictions.