SAML Authentication via Cloud
What is SAML authentication?
Security Assertion Markup Language (SAML) is a widely used protocol for single sign-on authentication where users are able to access multiple applications and services with a single set of credentials. Endpoint Central offers support for SAML 2.0 authentication. By enabling this feature, users can login to Endpoint Central Cloud via a Single Sign-On (SSO) service, which supports SAML authentication.
What are the entities involved in SAML authentication?
There are three main entities involved in SAML authentication namely an identity provider (IdP) like Okta, OneLogin etc, a service provider (SP) and the user. SAML authentication works in the following manner:
- First, the user initiates the login process by accessing a service provider application
- The Service provider generates a SAML authentication request and redirects the user to the identity provider
- The user enters his or her credentials which is authenticated by the identity provider which prompts the user to verify his or her identity
- Once the user is authenticated, the identity provider generates a SAML response containing certain security assertions ( a digitally signed XML document) that contains all the information about the user's identity and attributes.
- The identity provider sends the SAML response back to the service provider
- The Service provider verifies the digital signature on the SAML response to verify it and extracts the user's identity and attributes from the assertion
- Finally, if the user's identity is verified, the service provider grants access to the requested application or service
What are the benefits of SAML authentication?
SAML authentication offers many advantages such as centralized user management, reduced authentication complexity and improved security. It eliminates the need for individual application-specific credentials.
How to configure SAML authentication in Endpoint Central cloud?
Prerequisites:
- Since, the IdP redirection happens via HTTPS port, the HTTPS port must be kept open. The ACS URL is generated using HTTPS only.
- Identity Provider should support HTTP POST binding.
- Certificates from the Identity Provider should not have been tampered with, encrypted or expired and should be encoded in base 64 format.
Data provided by Endpoint Central Cloud that has to be entered in IdP
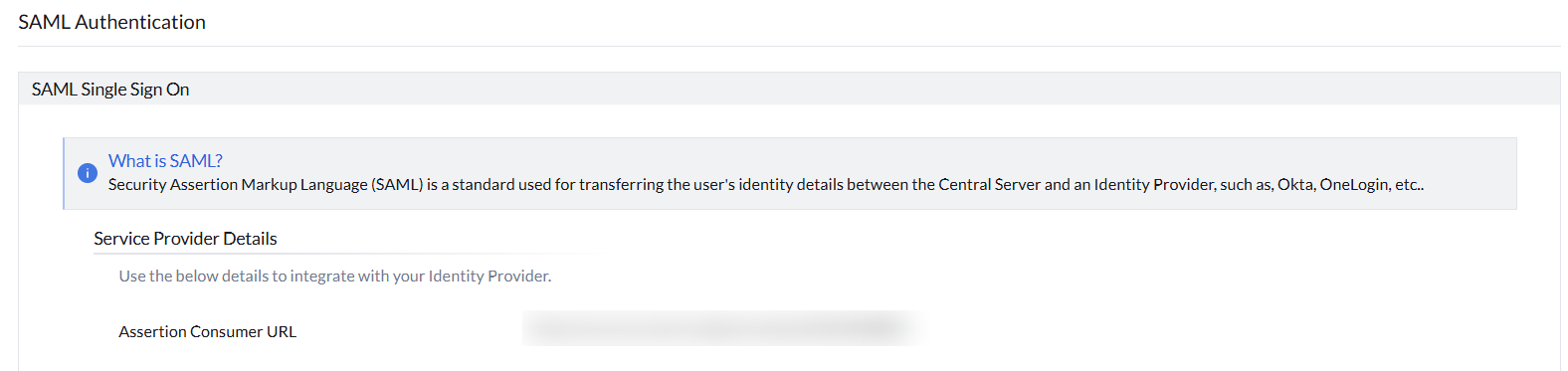
After logging into Endpoint Central Cloud, go to the Admin tab and select SAML Authentication under User Admninistration. Here, you can find the details that are provided by Endpoint Central Cloud to be entered in IdP's side.
- Entity ID
Entity ID is a Globally-Unique Identifier used to represent your Endpoint Central Cloud instance. zoho.com is the entity ID to be configured in IdP.
- Assertion Consumer Service URL (ACS URL)
The ACS URL or Reply URL is an endpoint pointing to your Endpoint Central Cloud instance that tells the IdP where to send the SAML response.
Data required by Endpoint Central from IdP
After logging into the product console, Navigate to the Admin tab > User Administration> SAML Authentication. At the bottom, you have to enter the IdP's details.
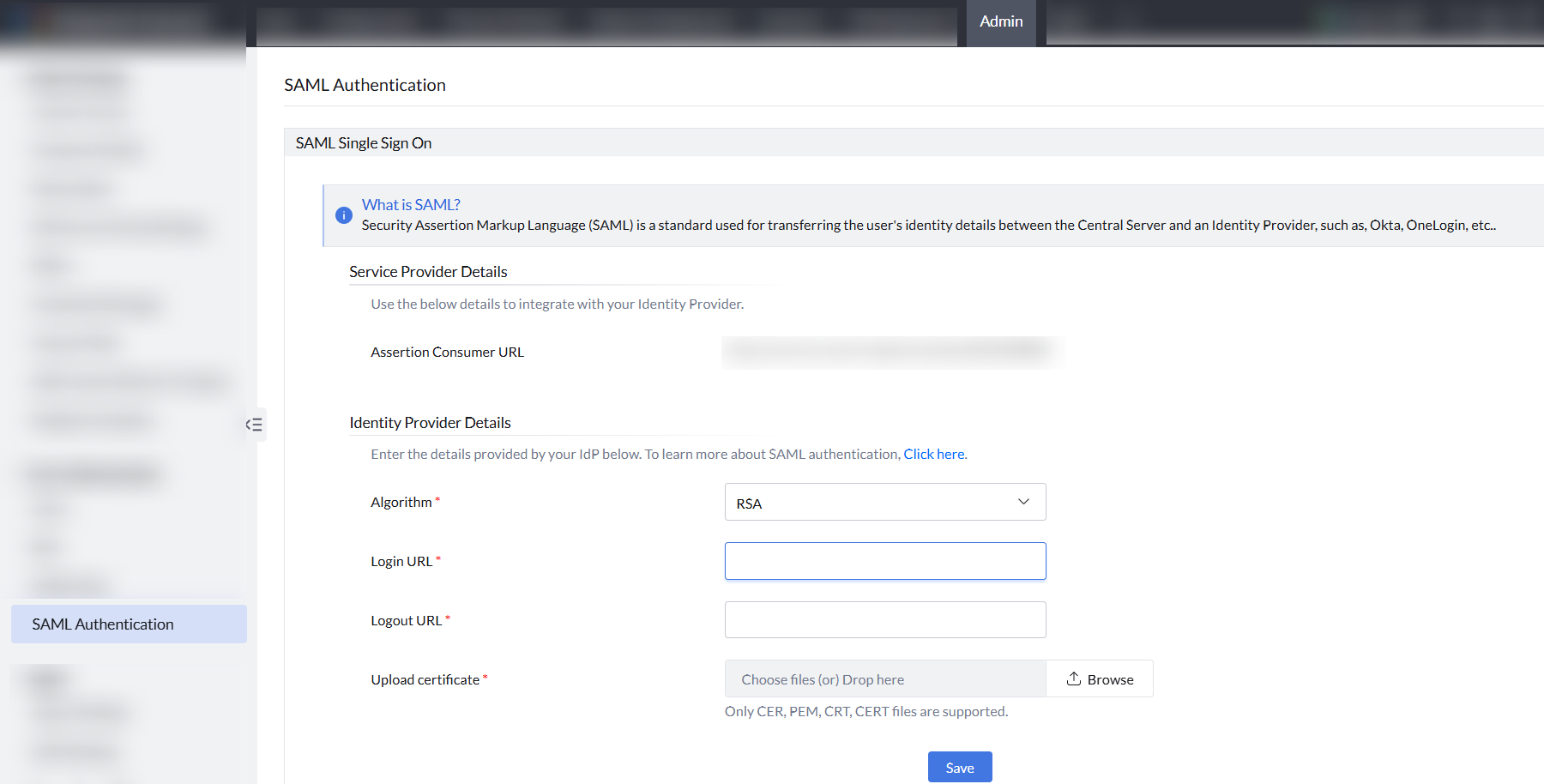
- Login URL
The Login URL is an endpoint pointing to your IdP that tells Endpoint Central Cloud where to send the SAML request.
- Logout URL
The Logout URL is the IdP URL where the sign out request will be sent when the user signs out from Endpoint Central Cloud.
- Certificate
A certificate from the IdP, used by Endpoint Central Cloud to verify future SAML requests from the IdP.
Note: We accept only the following certificate formats: based-64 coded .cer, .crt, .cert, or .pem file. Make sure to upload the certificate in one of these formats.
Here are a few videos that can help you configure SAML authentication via cloud:
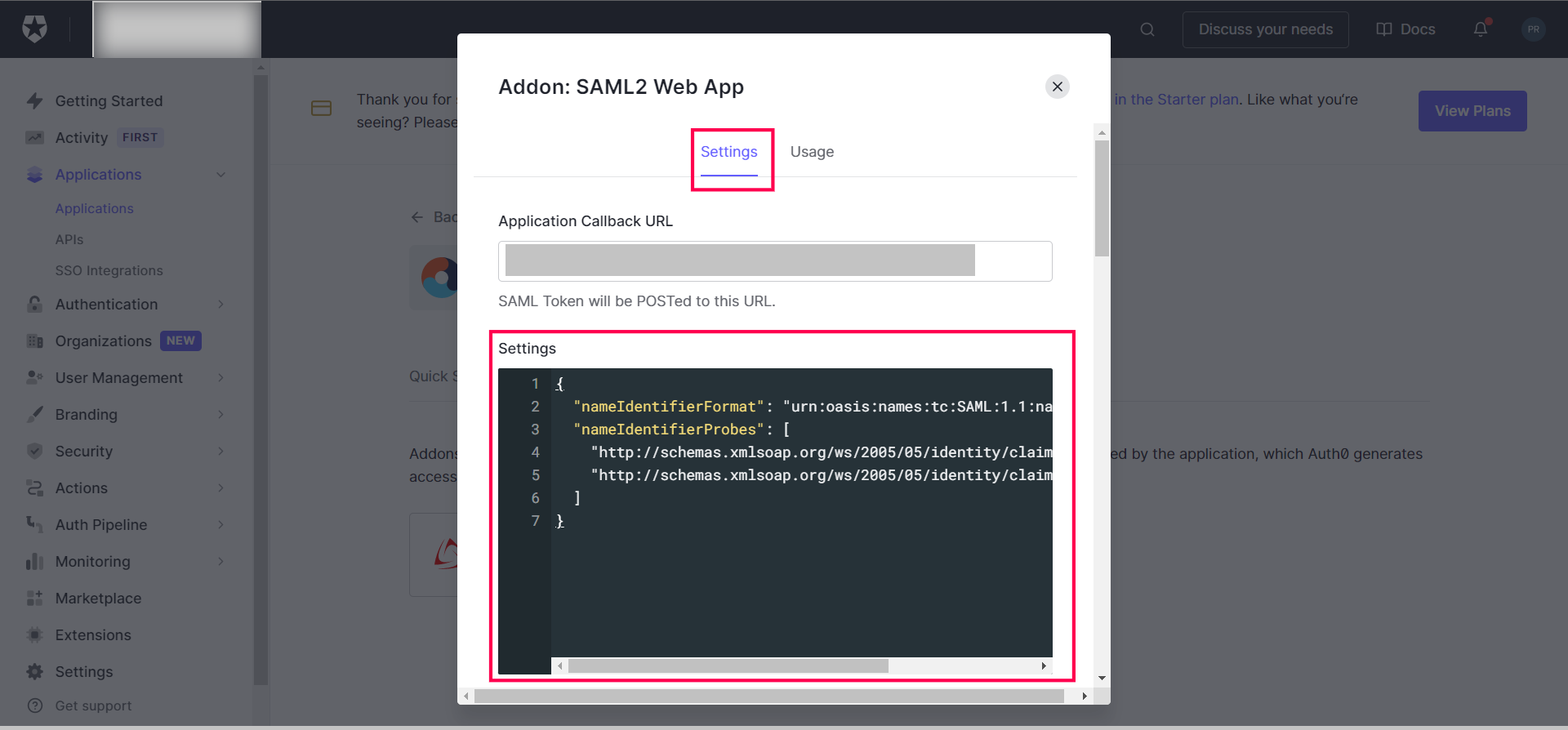
Enter the following JSON code in the settings window for Auth0 configuration as shown:
{
"nameIdentifierFormat": "urn:oasis:names:tc:SAML:1.1:nameid-format:emailaddress",
"nameIdentifierProbes": [
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"
]
}
Note:
- To successfully log in using SAML, the user must be present both in the IdP and Endpoint Central Cloud.
- SAML authentication may not work in browsers that are not supported by the Identity Provider.
- Currently SAML Logout is not supported.
- All accounts should have a unique email ID associated with them in Endpoint Central Cloud.
- The Email ID should be selected in the Identity Provider for authenticating users.



