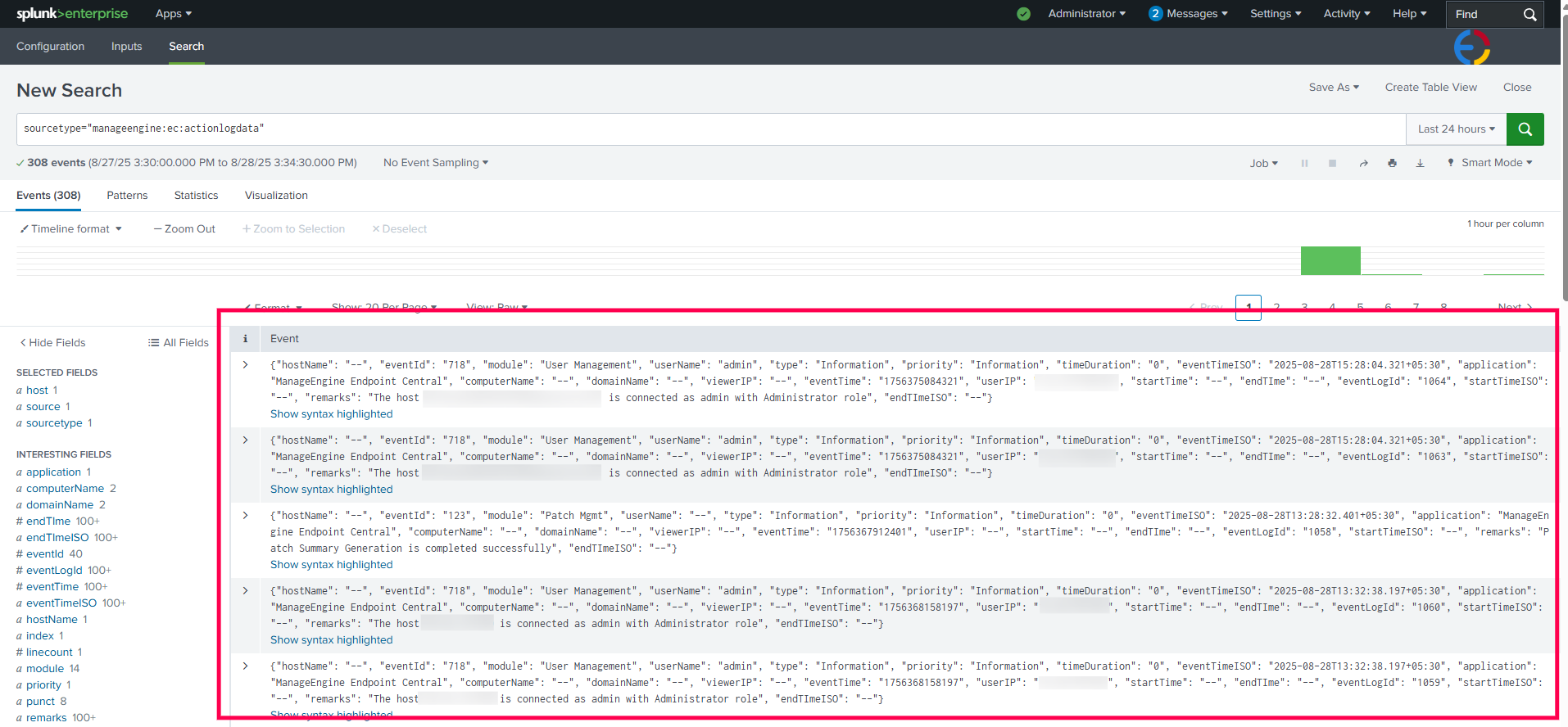
When Endpoint Central is integrated with Splunk, both vulnerability data and audit logs are forwarded to Splunk. This provides administrators with a consolidated view of all detected vulnerabilities and records of actions performed through the console, such as configuration changes, deployments, and administrative activities. Splunk’s analytics can then be used to monitor these events, identify patterns or anomalies, and generate reports and dashboards for auditing, compliance, and security monitoring purposes.
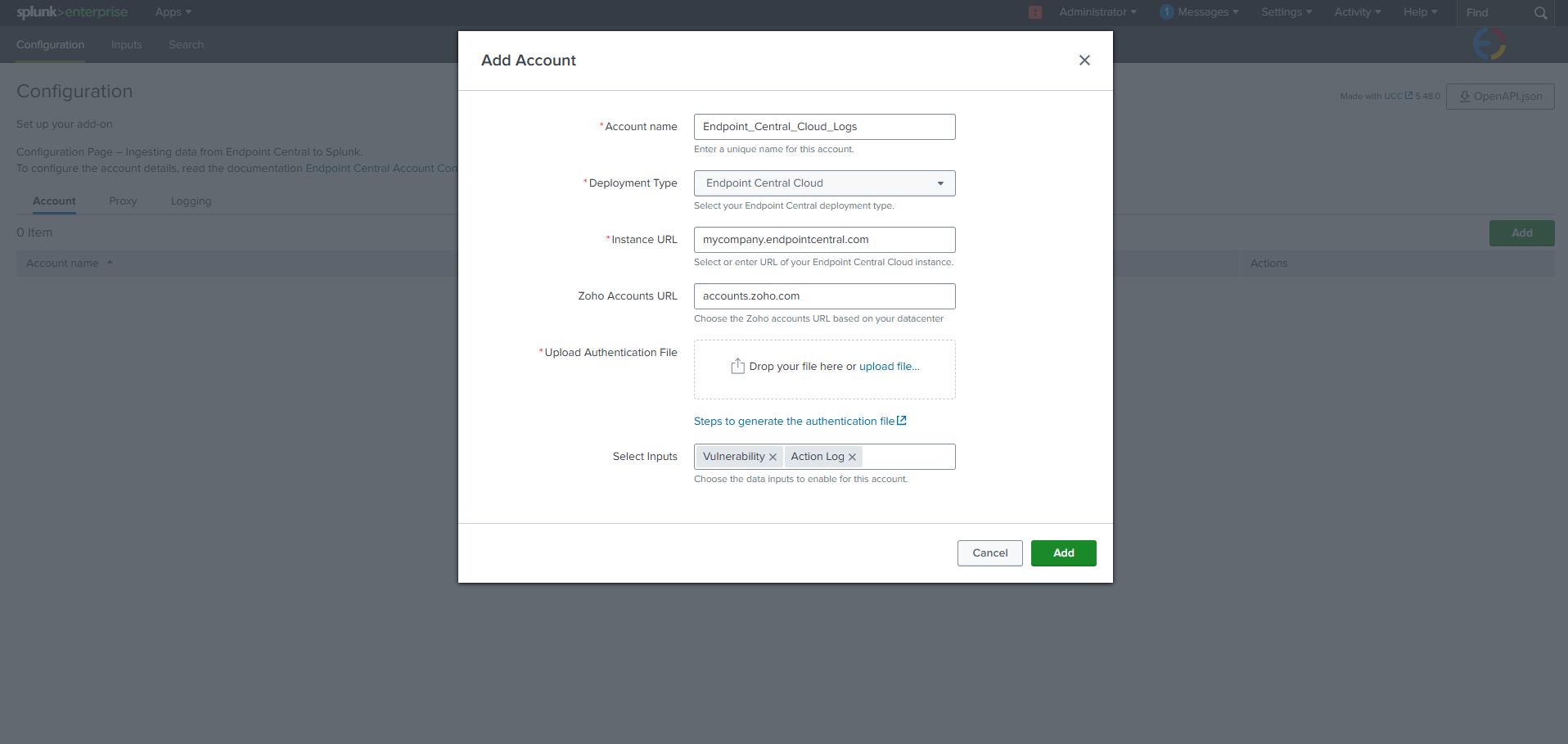
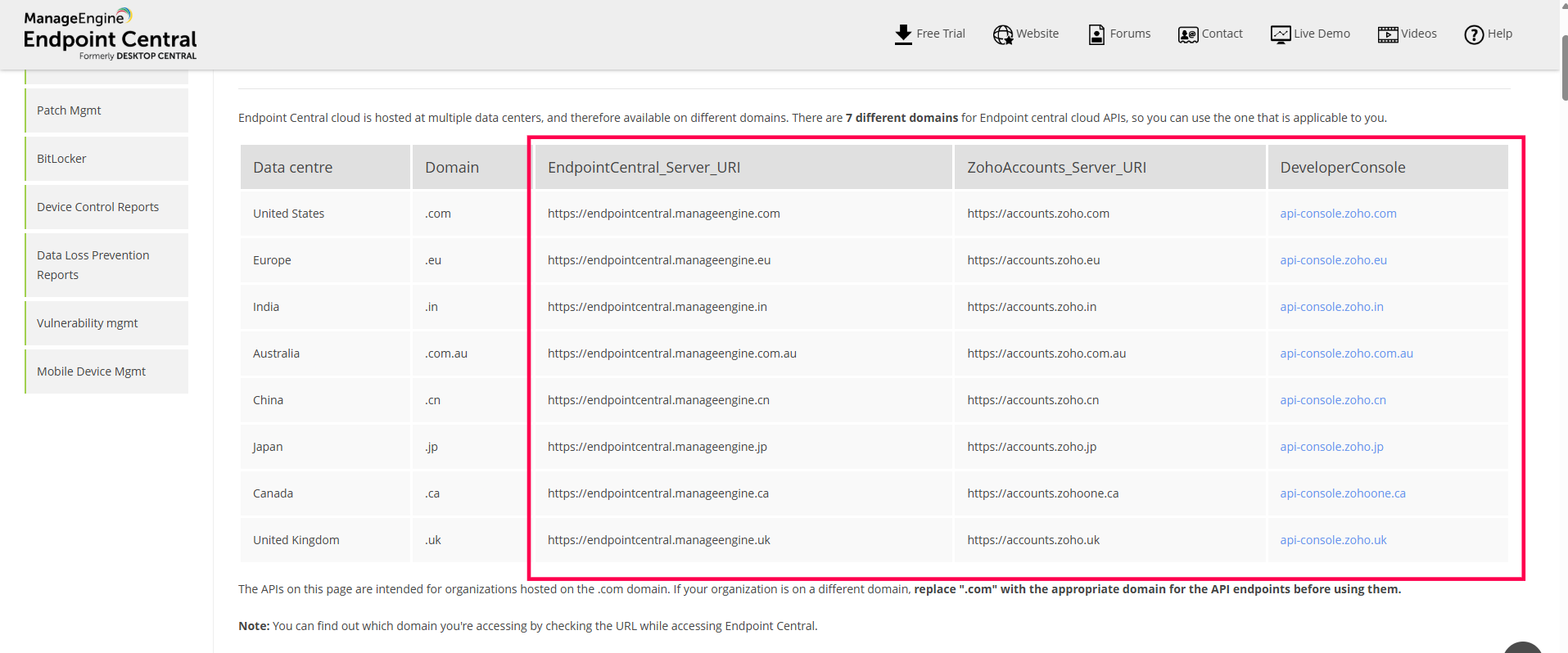
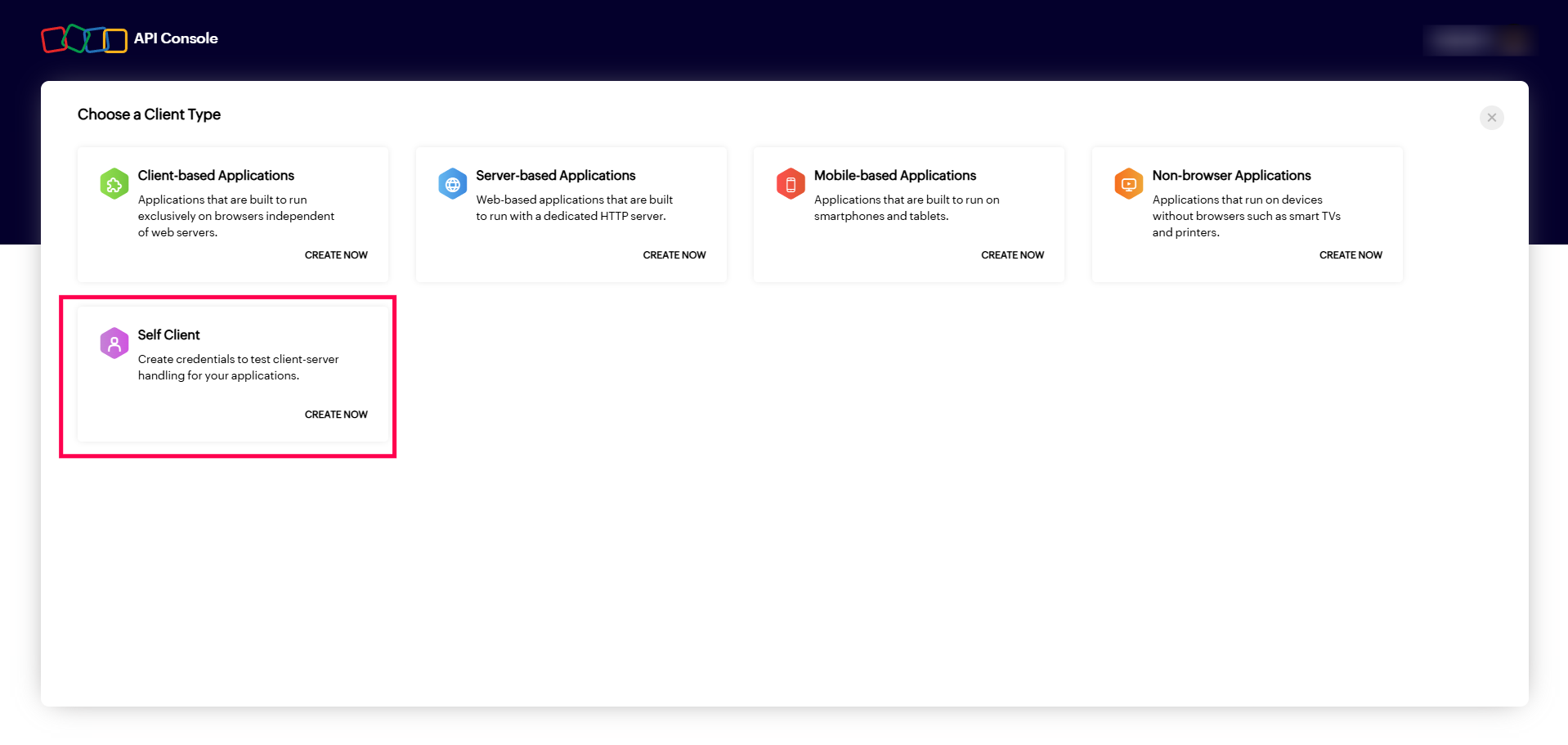
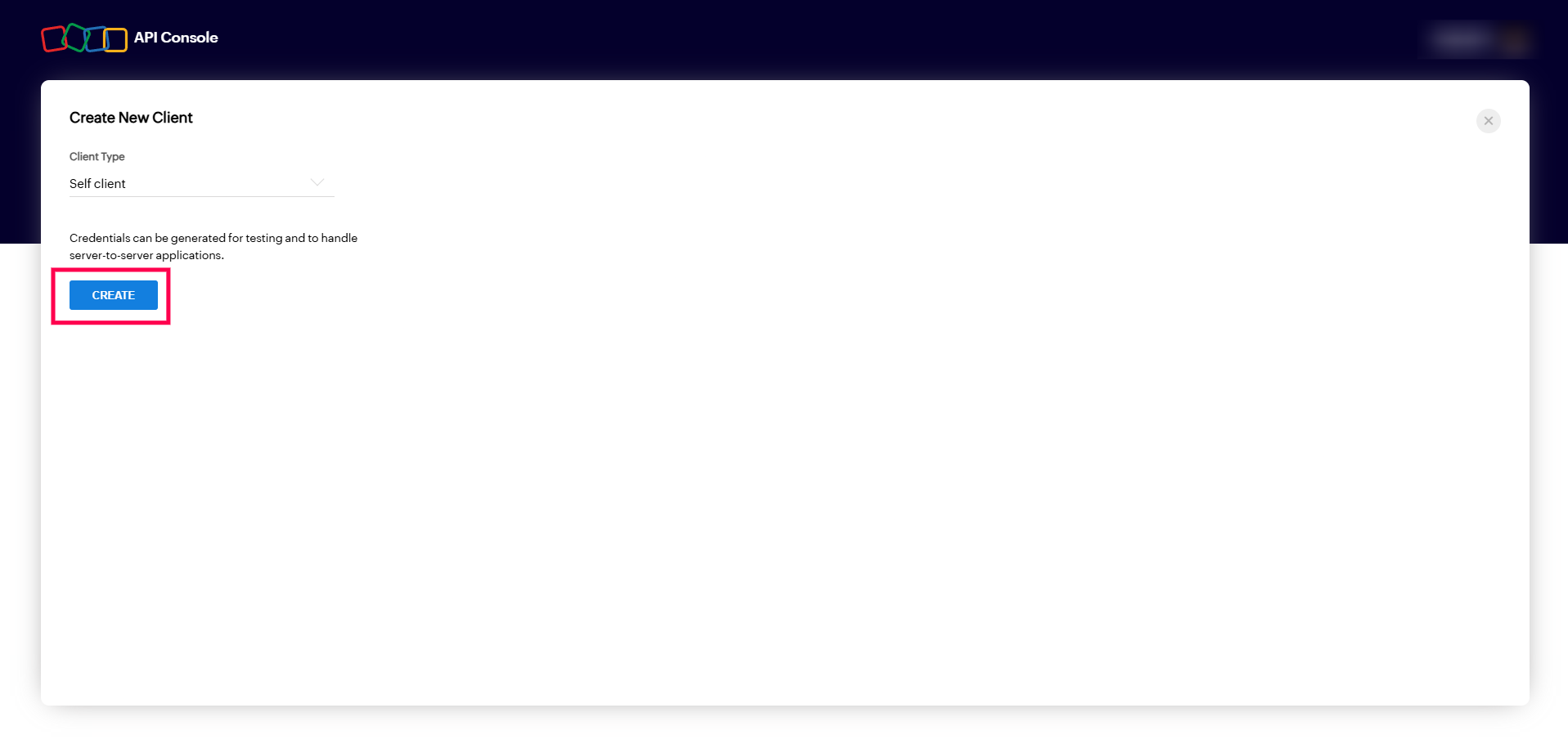
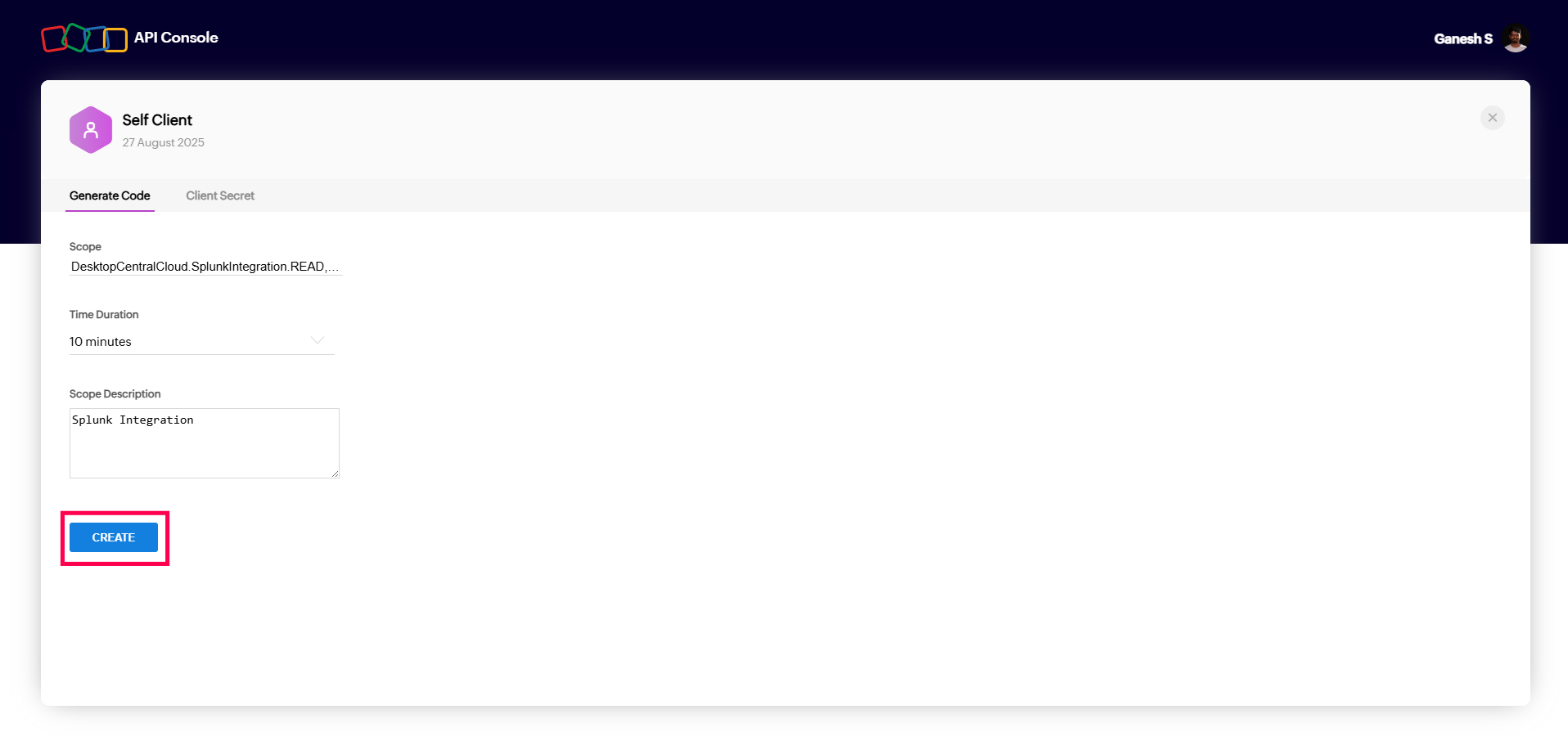
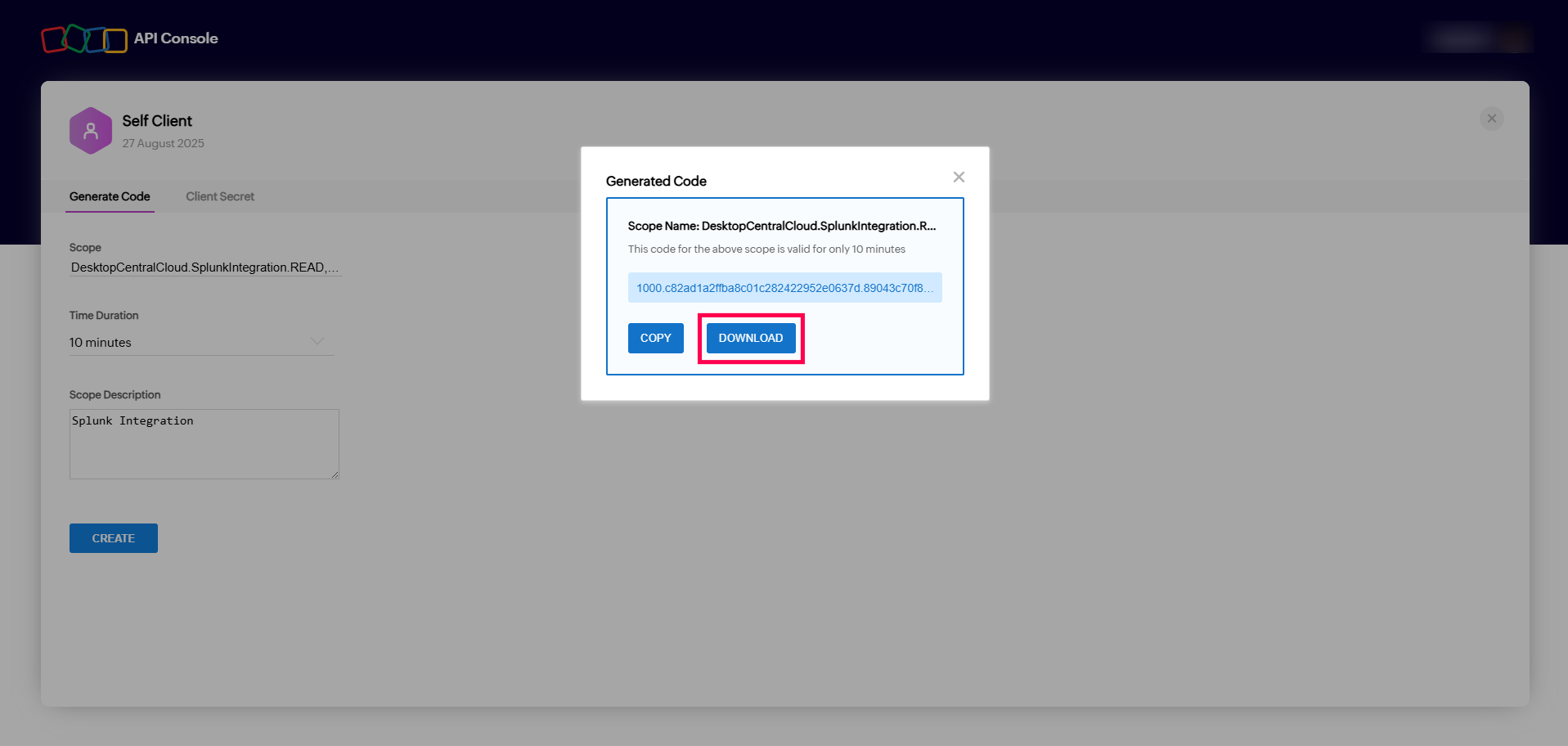
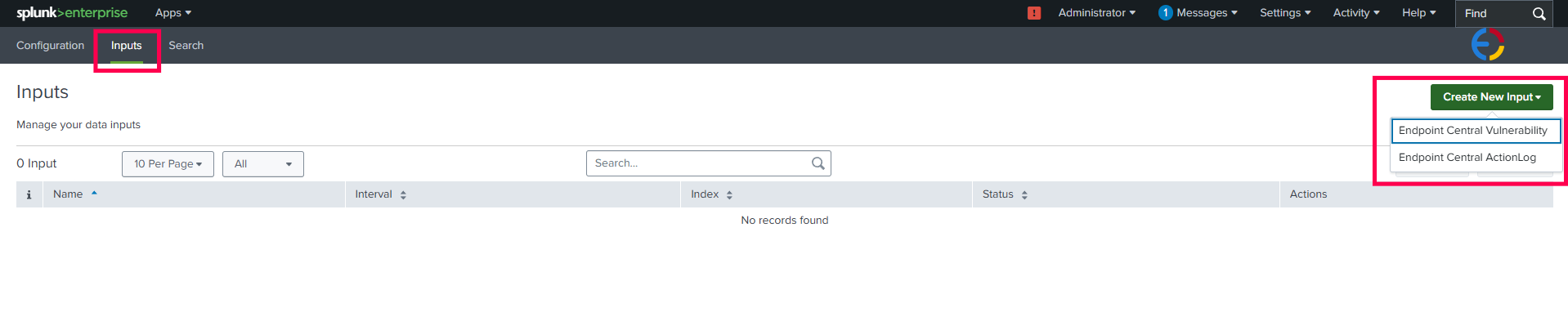
Valid Inputs:
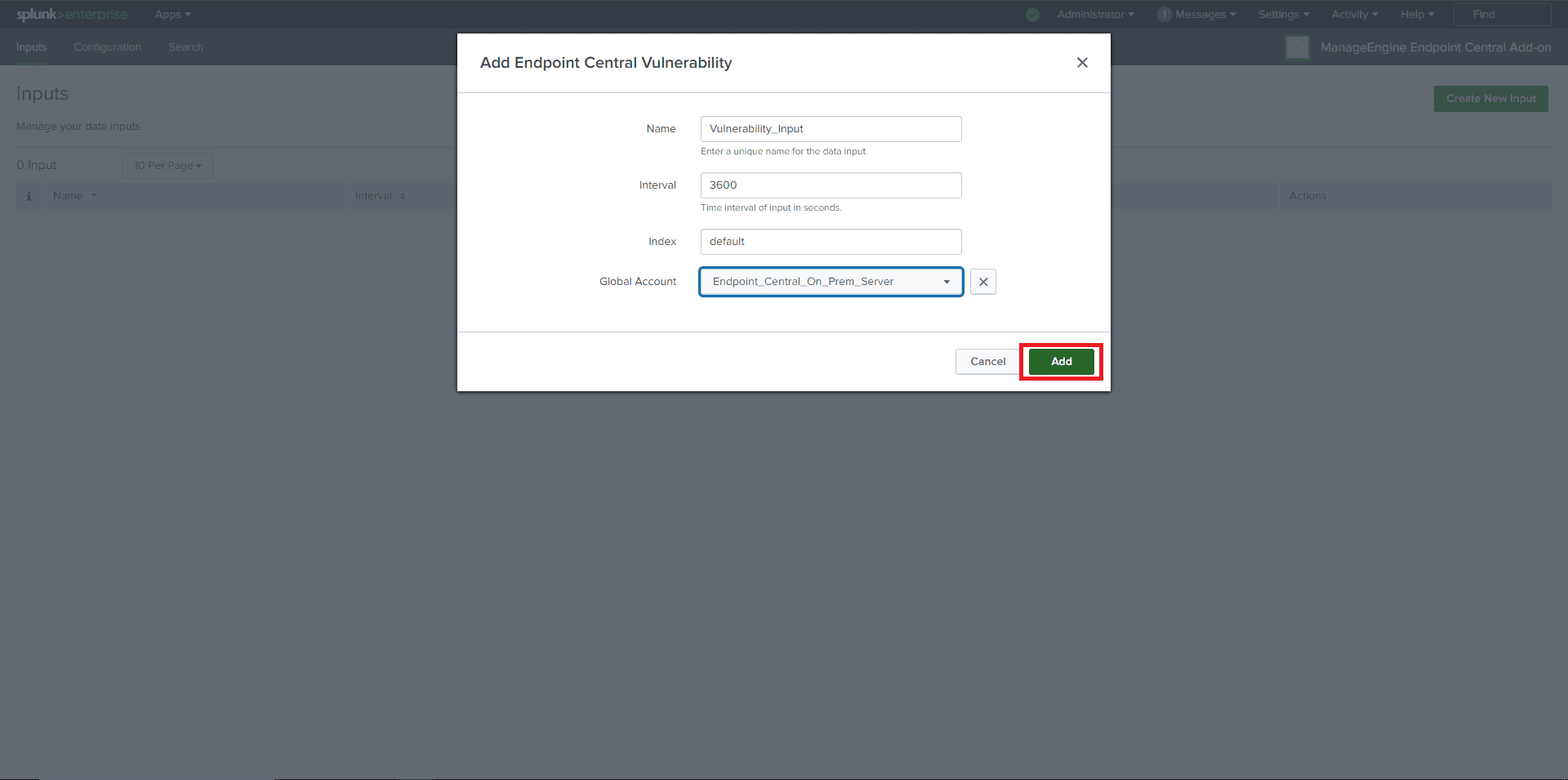
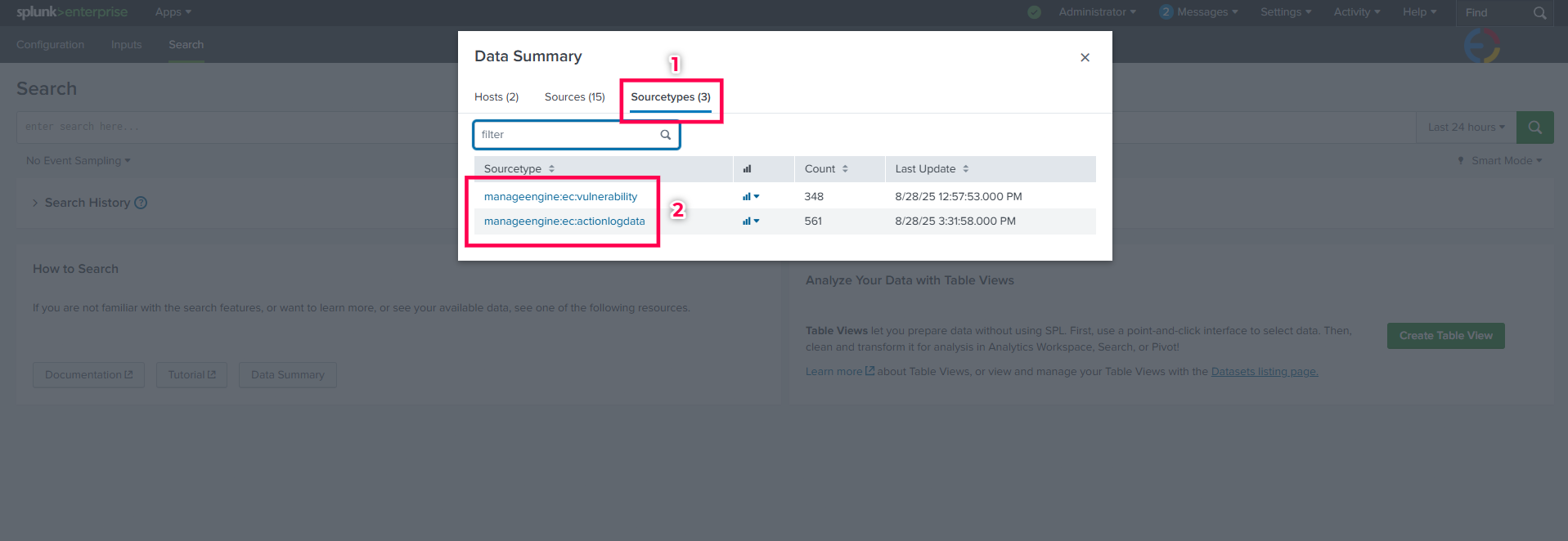
manageengine:ec:vulnerabilitymanageengine:ec:actionlogdata