| CoCo compliance requirements |
What is it? |
Predefined reports in EventLog Analyzer |
| Vulnerability management |
This requirement focuses on the management of vulnerabilities. It enforces the need for a defined policy and relevant processes for identifying, prioritizing, and mitigating vulnerabilities. The policy should specify time periods for patch application and a set process for auditing compliance. |
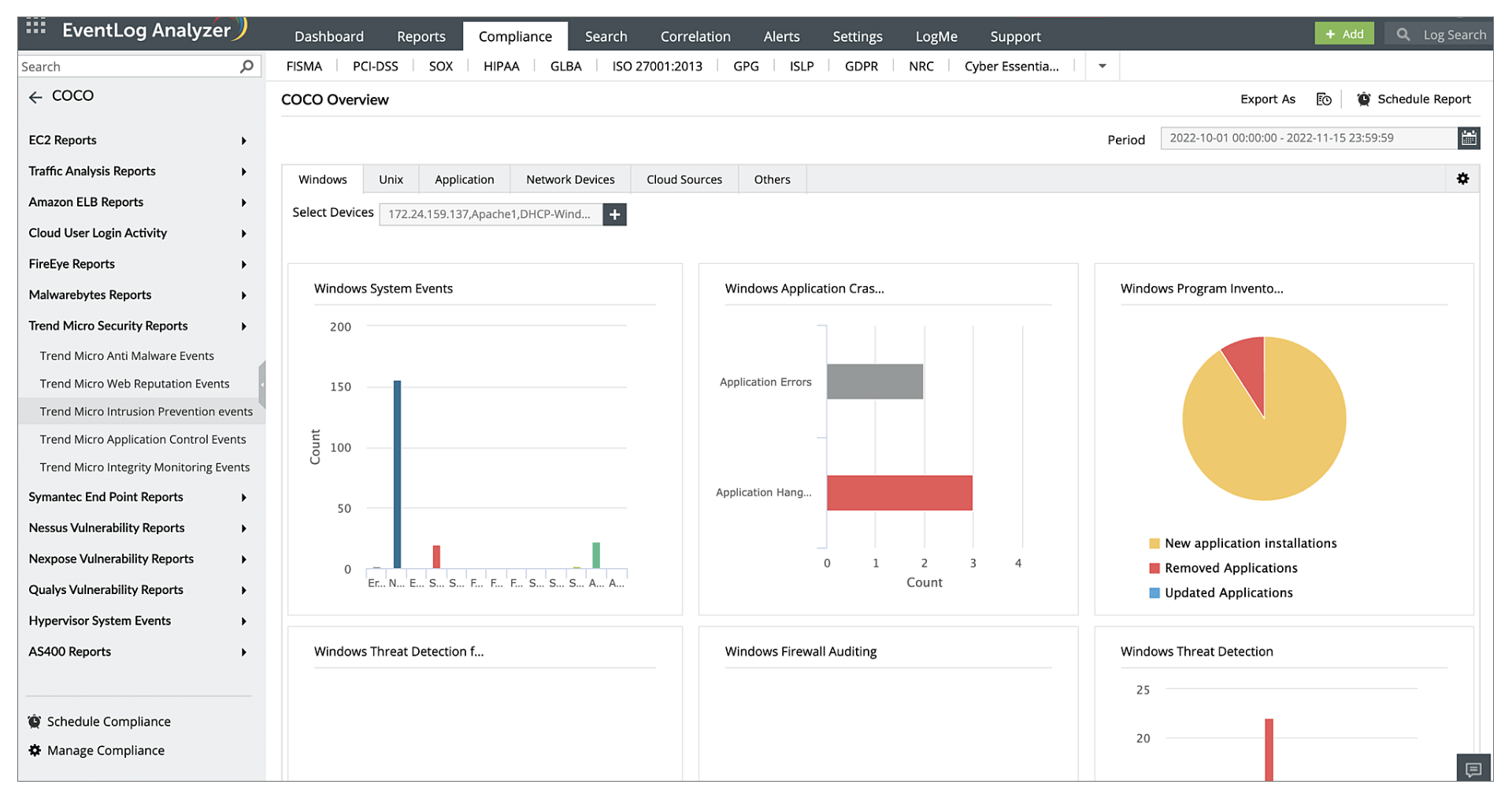
- Windows System Events
- Windows Services
- Nessus Vulnerability Reports
- Qualys Vulnerability Reports
- Nexpose Vulnerability Reports
|
| Secure configuration |
This requirement is about ensuring appropriate configurations for reducing the inherent vulnerability levels. Periodic checks should be performed to ensure that applications, services, processes, and ports that are not required are disabled. Devices, systems, and services should be able to detect, isolate, and respond to malicious software. |
- Windows System Events
- Windows Services
- Windows Application Crashes
- Windows Program Inventory
- Route 53
- WAF Reports
- AWS Network Security Groups
- AWS Config Reports
- Database Reports
- EC2 Reports
- Amazon ELB Reports
- Trend Micro Security Reports
- Symantec End Point Reports
|
| Physical security |
This requirement centers on secure accommodation and establishing appropriate policies and practices governing its use to protect personnel, hardware, programs, networks, and data from loss, damage, or compromise. |
- Windows Firewall Auditing
- Network Device Policy Management Reports
|
| Protective monitoring and intrusion detection |
This requirement is about the collection and retention of event data that will help detect security incidents. It enforces the presence of a monitoring policy describing the potential use cases, which can be used to define parameters for event data collection. The policy must include use cases for technical attacks as well as important abuses of business processes. |
- Windows Threat Detection from Antivirus
- Network Device Attack Reports
- File Changes Audit
- Route 53
- VPC Activity
- Storage Activity Reports
- WAF Reports
- AWS Network Security Groups
- AWS Config Reports
- EC2 Reports
- Traffic Analysis Reports
- Malwarebytes Reports
|
| Authentication and access control |
This requirement focuses on granting appropriate permissions to user accounts. It stresses the need to exercise prudence on provisioning accounts with administrator-level or higher privileges. Privileges should be periodically reviewed and removed when no longer required. Mechanisms for users to identify and authenticate to devices and services should be in place. |
- Unix Logon Reports
- Unix Account Management Reports
- Unix Failed Logon
- MSSQL Account Changes
- MSSQL Password Changes
- Oracle Security Changes
- IIS Web Server Errors Reports
- IIS FTP Server Reports
- PostgreSQL Account Changes
- IAM Activity
- AWS User Activity
- AWS Failed/Unauthorized Activity
- Cloud User Login Activity
- Hypervisor System Events
- AS400 Reports
|
| Boundary protection and interfaces |
This requirement is about the need for appropriately configured boundary protection between the organization's network and services and the internet or any other network. It enforces network traffic, services, and content to be limited to the business' needs. Services present outside the protected environment should be delivered from an appropriate architecture that can identify malware at the entry point. |
- Windows Threat Detection
- Network Device Security Reports
- Traffic Analysis Reports
- FireEye Reports
|