Firewall security auditing and configuration analysis
Firewall security auditing
Firewall security auditing is crucial for network security. EventLog Analyzer acts as a firewall security auditing tool by providing capabilities to:
Auditing firewall policies
Any unauthorized or accidental changes to firewall policies might result in malicious inbound and outbound network traffic. To avoid this security risk, you must keep track of changes made to your firewall policies. EventLog Analyzer, a comprehensive firewall security auditing tool, audits your firewall policies, reports on them, and instantly alerts you whenever policies are added, deleted, modified, enabled, or disabled.
Further, with this solution, you can also get notified about any unusual firewall policy modification, such as rule addition at an unusual hour. EventLog Analyzer spots this threat and notifies administrators over email and SMS.
You can find the audit reports in EventLog Analyzer for policy changes below:
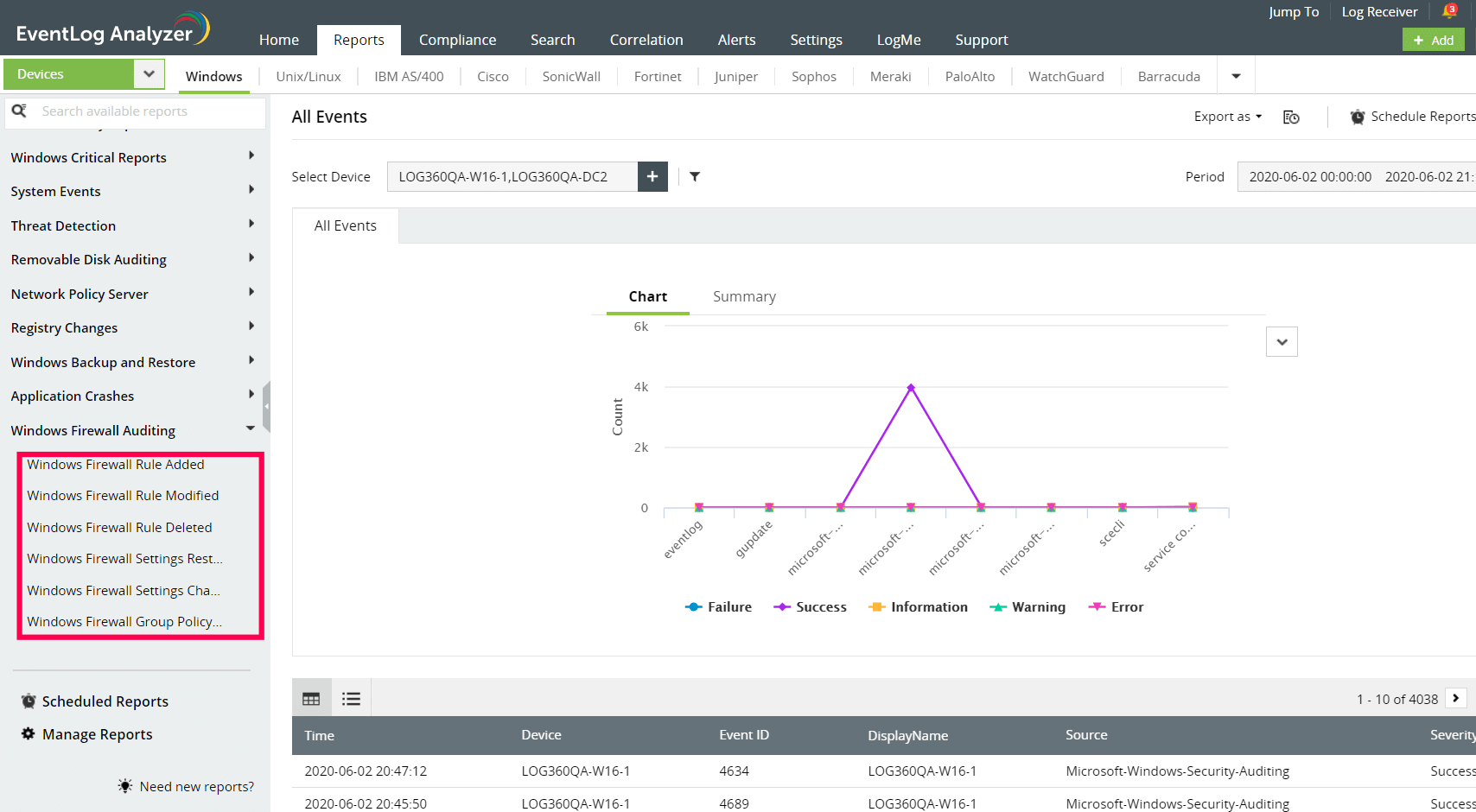
Auditing firewall accounts
Any changes made to the permissions and settings of firewall user and admin accounts have to be monitored closely and audited, as these firewall accounts can make changes to your firewall settings. EventLog Analyzer audits the firewall accounts to check for users added, users deleted, group policies added, and group policies deleted.
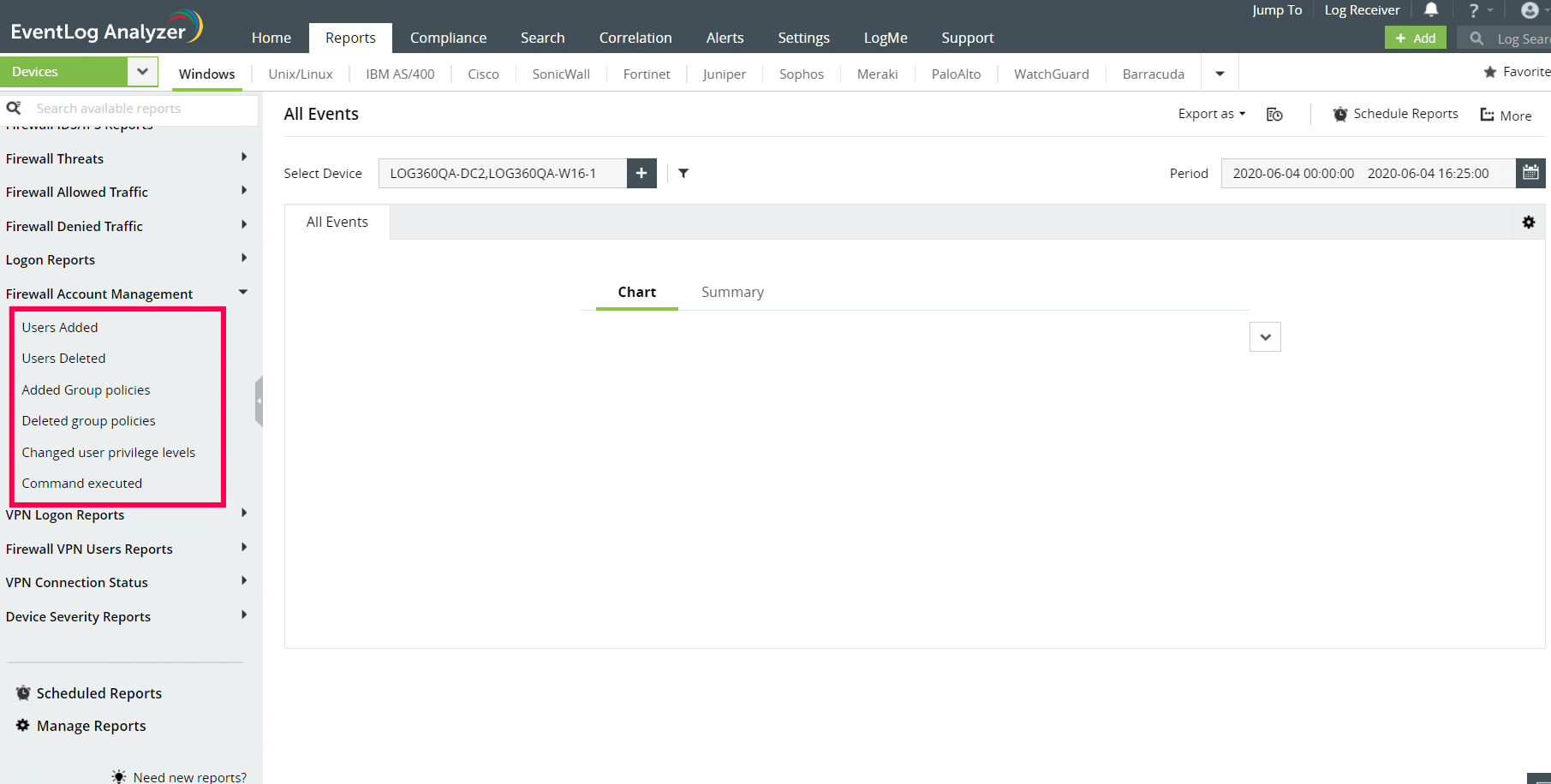
Auditing firewall user activities
EventLog Analyzer helps in auditing firewall user activities at a granular level. It can provide in-depth audit reports about firewall logons, firewall logoffs, logon trends, logoff trends, top logons based on users, and top failed logons based on users.
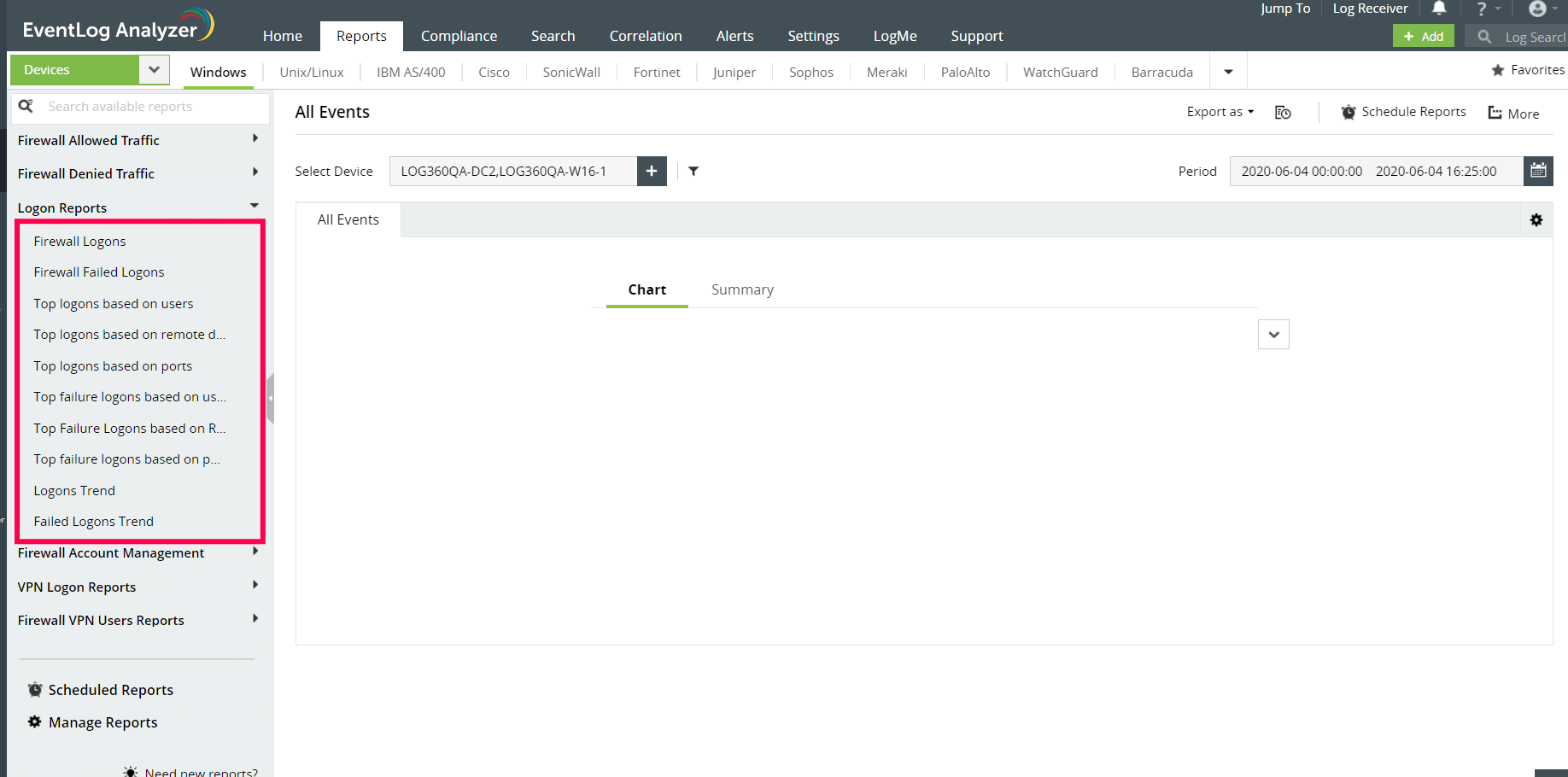
Auditing your firewall for the above activities can keep your network perimeter secure. EventLog Analyzer provides the below functions to enhance security:
- Helps ensure data loss prevention (DLP) by spotting malicious traffic within your network.
- Identifies and blocks malicious data and web intrusions.
- Detects distributed denial-of-service (DDoS) attacks by identifying web request flooding.
- Identifies and terminates botnet communications with untrusted C2 servers with automated workflow responses.














