- Free Edition
- What's New?
- Quick Links
- Log Management
- Application Log Management
- Application log monitoring
- IIS log analyzer
- IIS web log analyzer
- IIS FTP log analyzer
- IIS log parser
- VMware log analyzer
- Hyper V event log auditing
- SQL database auditing
- SQL server auditing
- MySQL log analyzer
- Apache log analyzer
- DHCP server auditing
- Database activity monitoring
- Database auditing
- Oracle database auditing
- IT Compliance Auditing
- IT Compliance Auditing
- SOX Compliance Audit
- GDPR Compliance Audit
- ISO 27001 Compliance Audit
- HIPAA Compliance Audit
- PCI Compliance Audit
- FISMA Compliance Audit
- GLBA Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- CCPA Compliance Reports
- CCPA Compliance Software
- NERC Compliance Audit Reports
- Cyber Essentials Compliance Reports
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
- PDPA compliance audit reports
- CMMC Compliance Audit
- SIEM
- Security Information and Event Management (SIEM)
- Threat Intelligence
- STIX/TAXII feed processor
- Server Log Management
- Event Log Monitoring
- File Integrity Monitoring
- Linux File Integrity Monitoring
- Threat Whitelisting
- Advanced Threat Analytics
- Security Log Management
- Log Forensics
- Incident Management System
- Application log management
- Real-Time Event Correlation
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Linux Log Analyzer
- Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Cisco Logs Analyzer
- VPN log analyzer
- IDS/IPS log monitoring
- Solaris Device Auditing
- Monitoring user activity in routers
- Monitoring Router Traffic
- Switch Log Monitoring
- Arista Switch Log Monitoring
- Firewall Log Analyzer
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet log analyzer
- Endpoint Log Management
- System and User Monitoring Reports
- More Features
- Resources
- Product Info
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
SQL injection (SQLi) is a prevalent attack technique where attackers use malicious SQL queries to access sensitive business information without proper authorization. To detect and mitigate SQLi attack, you need a comprehensive network security tool that analyzes and correlates log data from your web servers and databases. EventLog Analyzer, an SQL injection attack detection and mitigation tool, can alert you to the attack and quickly mitigate it before the data leaves your network.
Learn how EventLog Analyzer serves as an SQL injection mitigation tool
Detects traces of SQL injection attacks
Protect your network from data breaches by detecting traces of SQL injection attacks through real-time monitoring of database and web server activities. EventLog Analyzer serves as an SQL injection prevention tool and runs regular audit trails on web server and database server activities. You get in-depth insights into server usage, access patterns, permission changes, activity trends, and attack attempts in the forms of graphs and reports.
EventLog Analyzer's attack reports provide information on SQL injection attack attempts detected on your IIS and Apache web servers. Our solution also comes with prebuilt alert profiles that can be configured to trigger instant alerts when such attacks are detected.
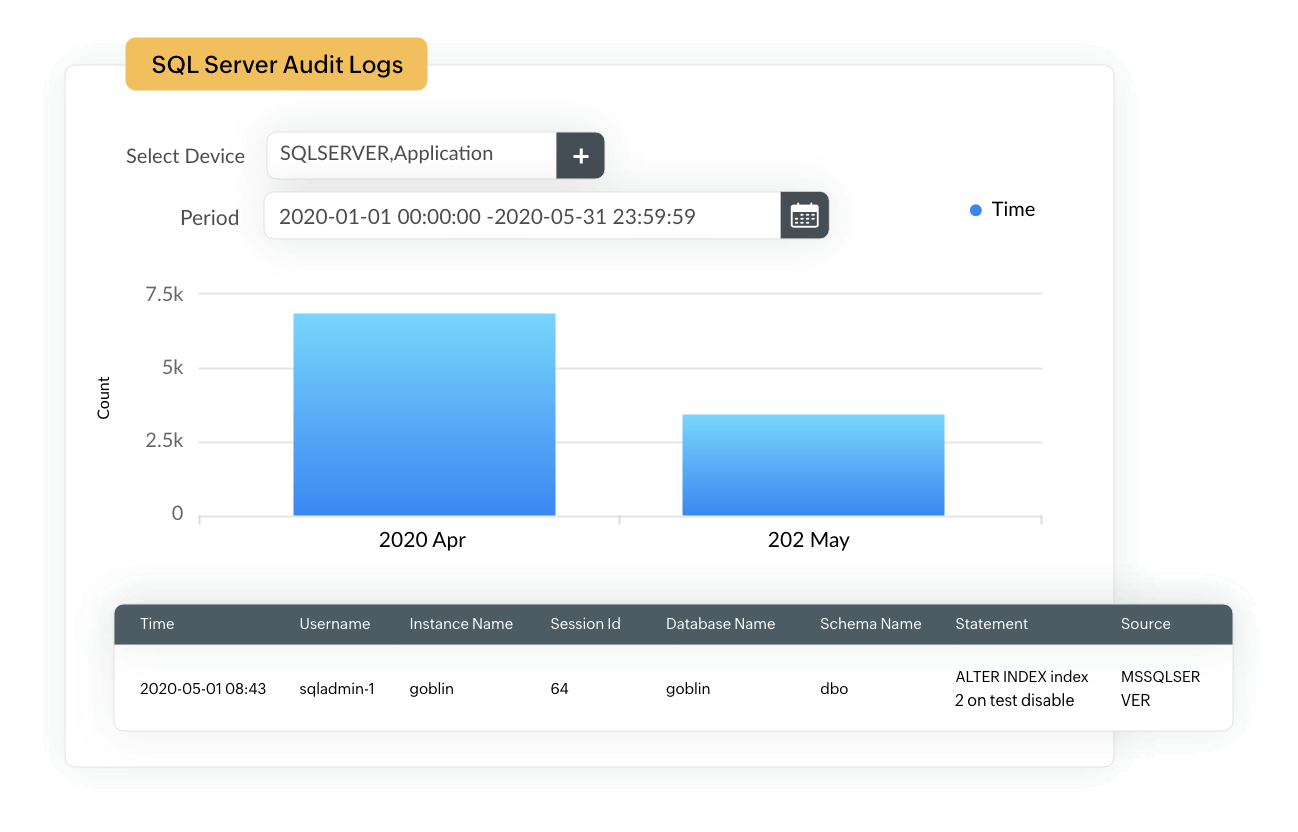
Correlates web server events
The powerful correlation engine of EventLog Analyzer is built to detect signs of suspicious activities in the network based on predefined correlation rules. The incident timeline report for every rule gives detailed insights into the sequence of events that caused the solution to trigger the correlation alert. This will give you a clear understanding of where the attack originated and how the attacker progressed through the network.
Our solution facilitates this breakdown with predefined correlation rules that are formulated to spot attack vectors in common cyberattacks, including SQLi. EventLog Analyzer's correlation rules encompass database events, web server events, Microsoft SQL Server security incidents, Oracle security incidents, IIS web server events, and Apache web server events for SQLi detection. You can configure the threshold limit and the time span of SQLi attempt logs from the same device type and name. Once the limit is reached, the solution triggers an alert.
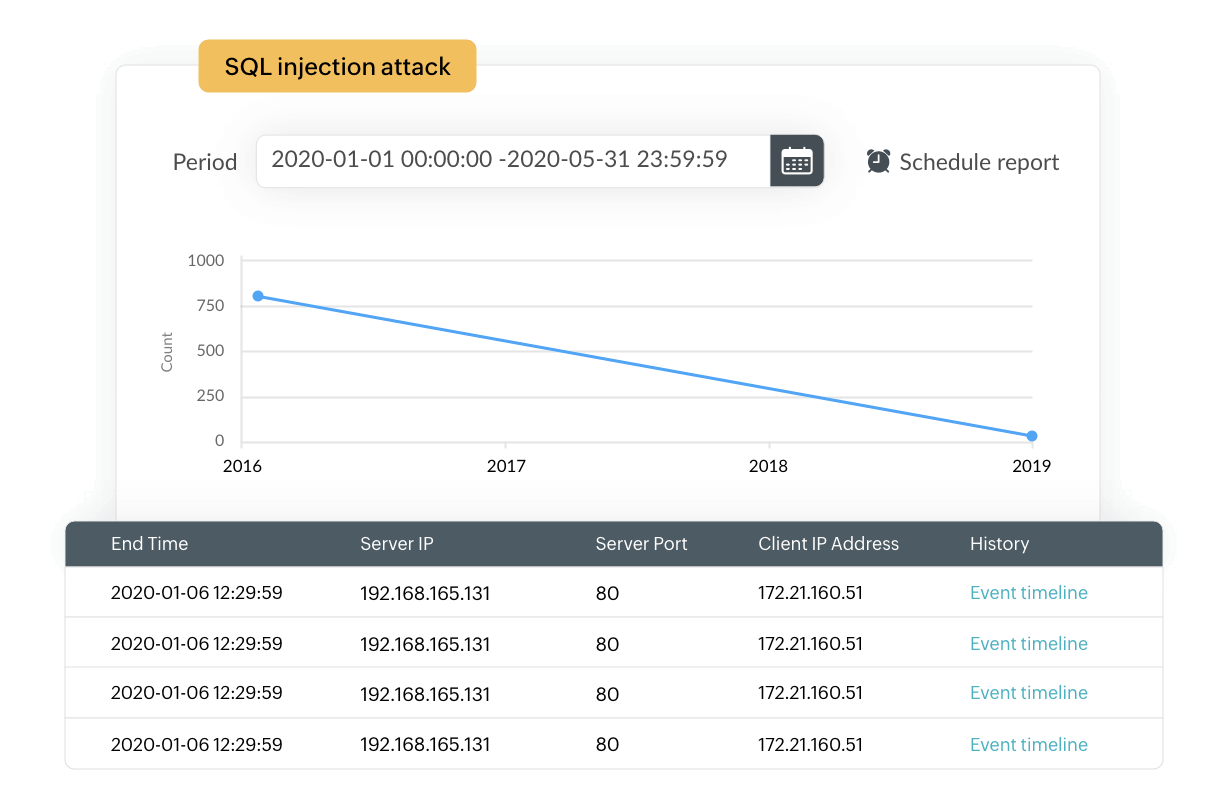
EventLog Analyzer helps neutralize the impacts of SQL injection attacks
Lateral movement
If an attacker gains access to the network, they tend to move laterally, access database servers with system privileges, and use these permissions to enter other sensitive systems in the network. EventLog Analyzer uses its threat intelligence and correlation capabilities to analyze the behavioral patterns of specific users. If a user logs on outside of work hours, changes access permissions, and modifies or exfiltrates sensitive data, our SQLi attack mitigation tool raises an alert to drive your attention to this sequence of actions.
Additionally, our solution's integrity audit reports monitor for column integrity in database tables. If you mark sensitive columns in the table, EventLog Analyzer will raise an alert when the values in that column are altered.
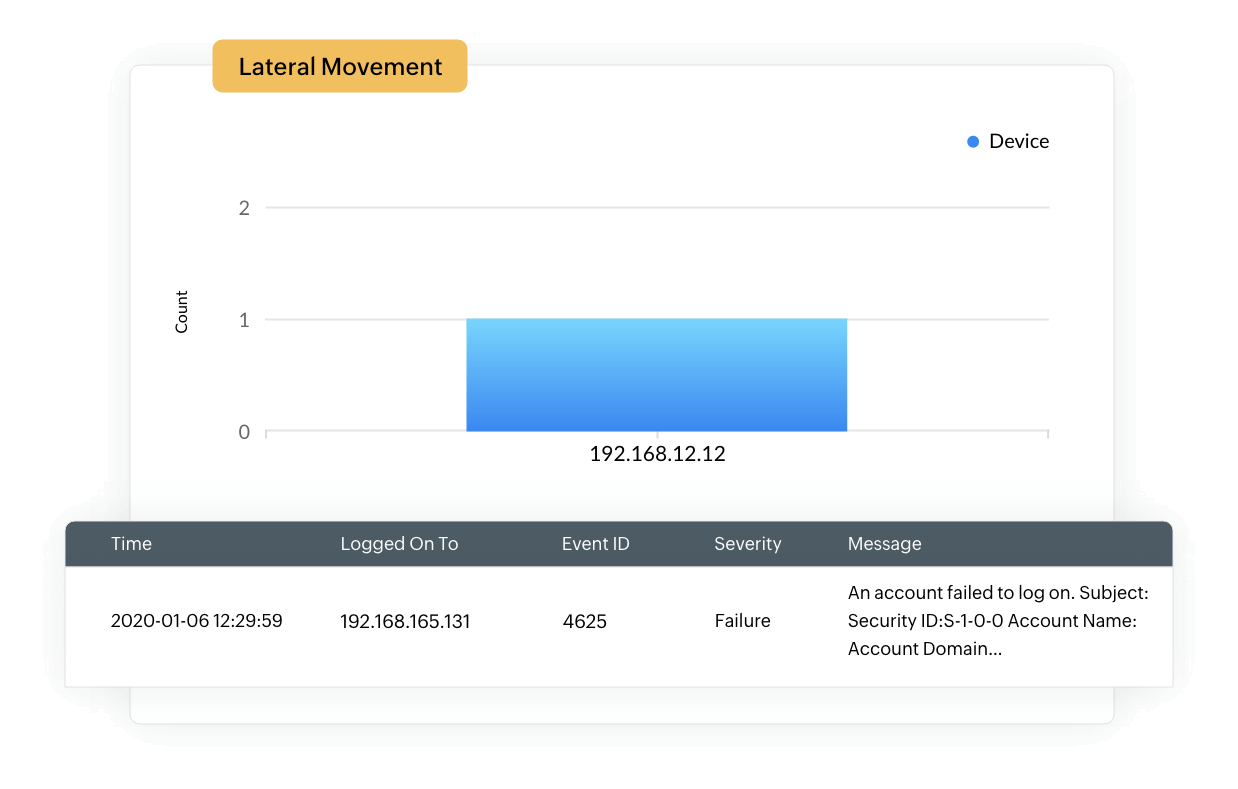
Privilege escalation
Another prominent course of action undertaken by attackers in an SQL injection attack is credential stealing, which is where they obtain privileged user credentials via malicious SQL queries and impersonate these users to access critical databases. Privileged users have unrestricted access to all the critical databases and applications, including permissions for creating or removing user profiles and managing user privileges.
EventLog Analyzer's privileged user monitoring tracks the session activities of users with escalated permissions for accessing sensitive data. Our solution will spot suspicious events, such as logon failures, unauthorized logons, and access attempts at unusual times.
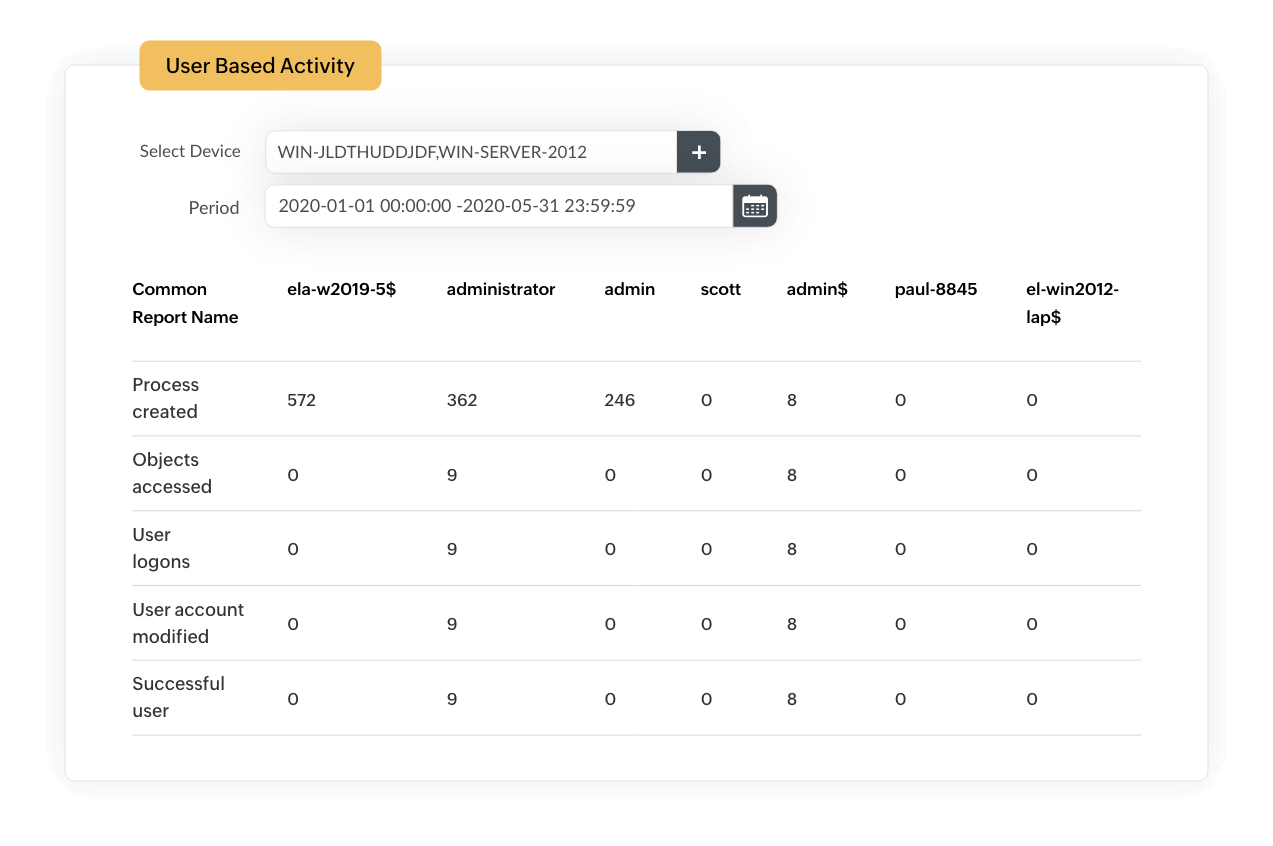
Unauthorized data access
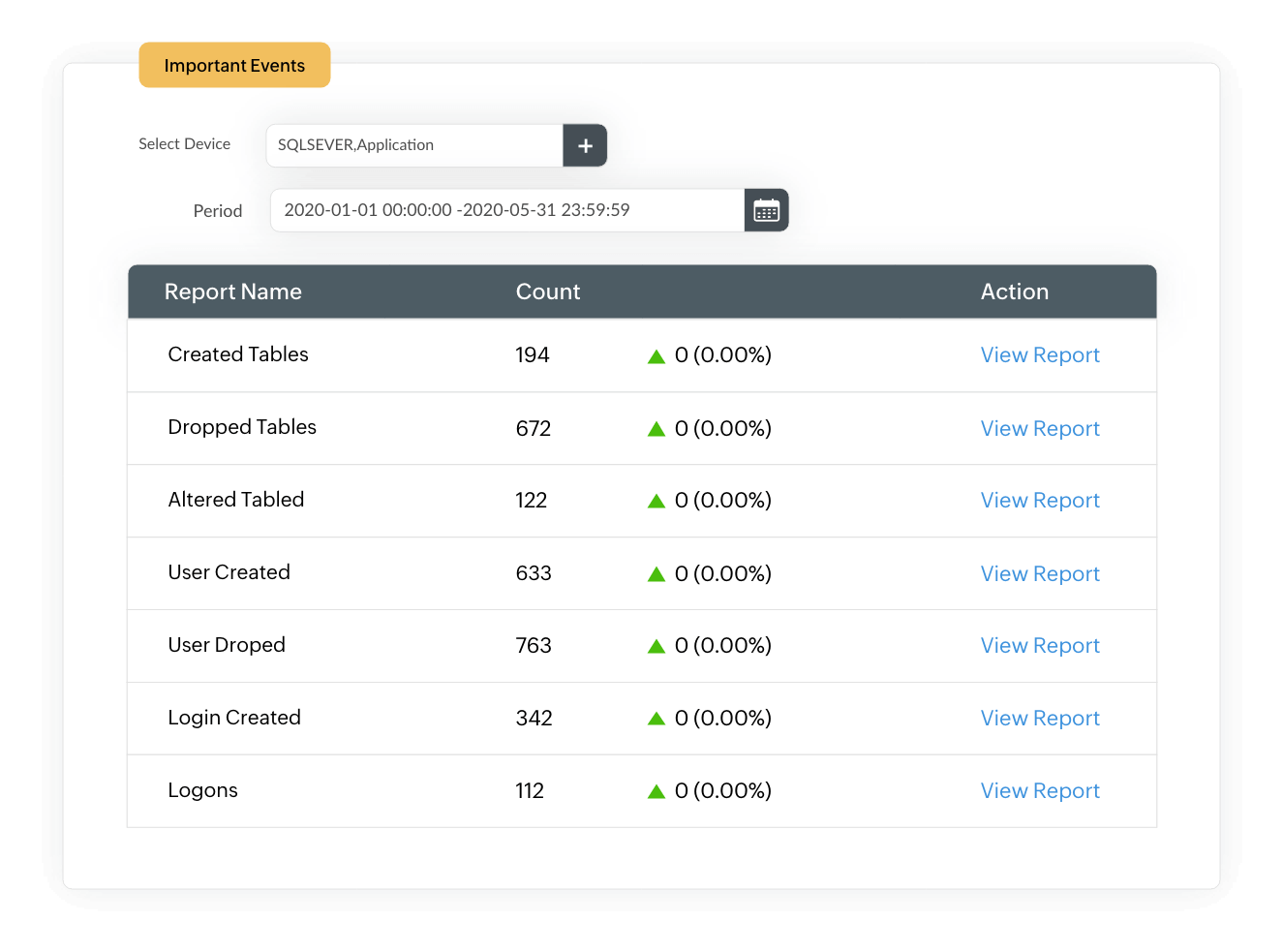
If an attacker gains unrestricted access to confidential data on your SQL severs, they can tamper with the existing data by altering, adding, and deleting entries or dropping entire tables. With EventLog Analyzer, you can audit DDL and DML activities to track functional- and structural-level changes in your databases.
The exclusive audit trails on your Microsoft SQL servers and other databases provide insights into additions, deletions, or modifications to tables, views, procedures, triggers, schemata, and data. They also present the data intuitively in the form of graphical reports to help administrators perform quick forensic analysis when required.
Other solutions offered by EventLog Analyzer
Network and endpoint device monitoring
Monitor every entity in your network by collecting, correlating, and analyzing logs. Gain insights into network activities through intuitive graphs and reports.
Server log management
Monitor all database and web server activities. Receive alerts about usage, access attempts, account changes, and attack attempts.
IT compliance management
Simplify compliance regulation management with predefined reports for popular mandates, like the PCI DSS, SOX, HIPAA, ISO/IEC 27001, the GDPR, FISMA, and the GPG.
File integrity monitoring
Audit sensitive files and folders to detect critical changes, such as creation, deletion, access, modification, and renaming. Receive instant alerts when suspicious activity is found.
5 reasons to choose EventLog Analyzer for SQLi detection and mitigation
1. Database auditing
Monitor database logs and improve your internal security framework with real-time insights into DDL, DML, server, account, and security modifications.
2. Application log management
Audit, manage, and track IIS, Apache, and DHCP web server logs to track critical events, like server events, security errors, and configuration changes, and gain insights into an attack.
3. Proactive attack management
Identify attack attempts at the first sign of compromise and automate remediation with predefined workflows to mitigate security attacks effectively.
4. Out-of-the-box SQLi reports
Generate SQL injection attack reports and gain key insights that assist in eliminating SQLi vulnerabilities.
5. Log forensics
Protect your network from future attacks by conducting forensic analysis and retracing the steps taken by attackers.
Frequently asked questions
Many organizations offer multiple dynamic, data-driven web applications to their users. These applications are dependent on databases for storing and protecting data. This can include business-critical data, confidential data, customer records, financial records, and the privileged or personal information of an organization. Generally, these applications use standard SQL queries, which are formed based on user inputs, to communicate with the database.
An SQL injection attack, also known as SQLi, is a common attack that threatens databases through web applications. A malicious user with sufficient knowledge of SQL can manipulate the inputs provided in the application to retrieve data to which they should not have access. An organization can face serious privacy and legal implications if data is stolen via a vulnerability in its application.
While applications usually run checks on the inputs to ensure a data leak does not happen, sophisticated attackers may still find vulnerable points in the application. Regularly auditing the database server and the web server that hosts the applications is therefore necessary to make sure the data is always protected. EventLog Analyzer's predefined reports and alerts make this audit and security process easy.
An SQL injection attack is a type of security exploit that allows hackers to manipulate vulnerabilities in a network's SQL database. You can minimize the risk of being a victim of this attack by following several SQL injection prevention best practices:
- Deploy a web application firewall (WAF) to identify and accept only permitted inputs for a given field.
- Authenticate user inputs to filter maliciously crafted external inputs.
- Monitor critical databases and web servers in real time.
- Update and patch applications and databases to keep them secure from network vulnerabilities.
- Monitor privileged user activity to avoid privilege abuse.
- Build a system to alert you about indicators of an SQL injection attack.
- Remove inessential database functions to prevent them from acting as entry points for attackers.
- Provide security awareness training to educate employees on how to keep the organization safe from threats.
EventLog Analyzer provides out-of-the-box SQLi correlation rules for the following:
- Database events
- Web server events
- Microsoft SQL Server security incidents
- Oracle security incidents
- IIS web server events
- Apache web server events
Additionally, you can create custom correlation rules to monitor any other specific events across your network.











