What is event log monitoring?
Event logs are records of activities and changes within the system events, including access attempts, operations performed, and errors encountered. The primary aim of event log monitoring is to provide IT professionals and system administrators with insights into the health and security of their systems.
Event log monitoring involves checking system-generated logs for errors, security breaches, or malfunctions. This helps in quickly addressing issues, ensuring system performance, and enhancing security.
Important Windows event logs to monitor
- Security audit events
- Account management events
- System events
- Policy change events
Security audit events
Track successful and failed login events to get insights into potential security breaches or unauthorized access attempts. They are crucial for identifying both legitimate user activities and potential security threats.
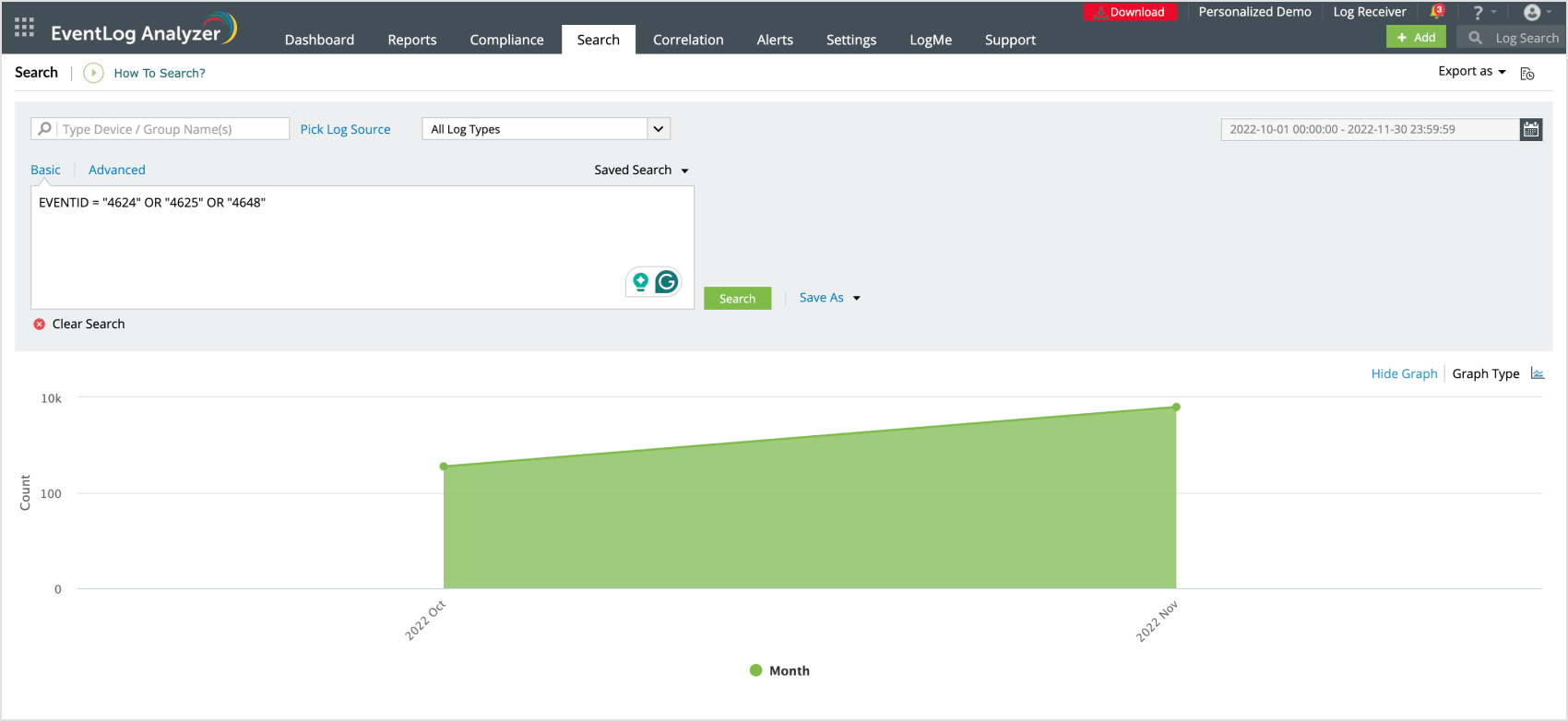
- 4624: Successful account logon event. This can indicate when a user or system account logs on to the system.
- 4625: Failed account logon event. Monitoring this can help identify unauthorized access attempts.
- 4648: A logon was attempted using explicit credentials. Indicates when a user attempts to log on with another user's credentials.
With EventLog Analyzer's powerful search console you can monitor these event IDs instantly with a simple query.
Account management events
Track the creation, modification, or deletion of user accounts and group memberships. Monitoring these events helps ensure that only authorized users have access to sensitive information and systems.
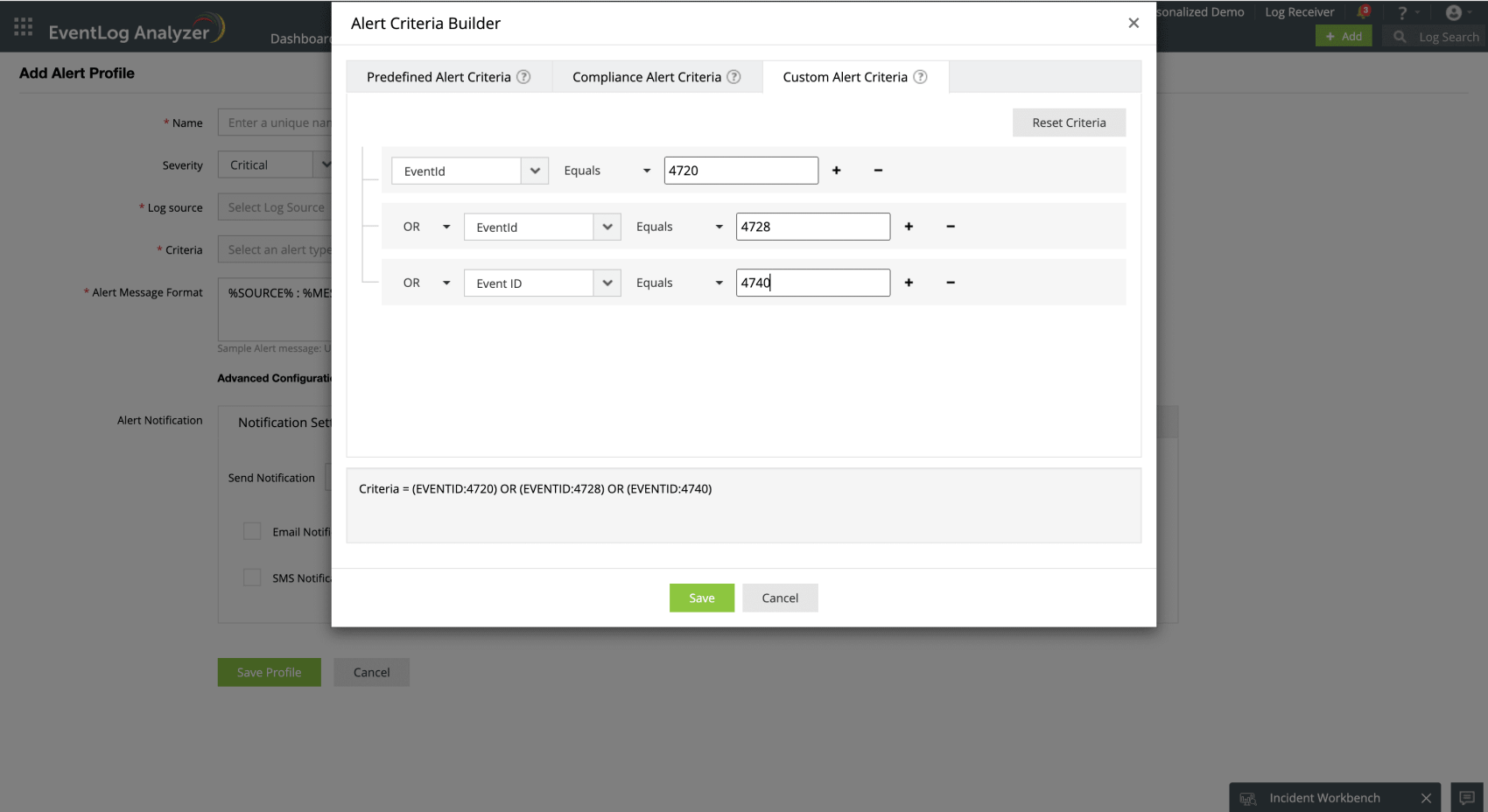
- 4720: A user account was created. This can signal the addition of new users to the system.
- 4728: A member was added to a security-enabled global group. Useful for tracking changes in group memberships that could affect security.
- 4740: A user account was locked out. Monitoring this helps in identifying potential brute-force attack attempts.
You can create custom alerts for specific Event IDs in EventLog Analyzer, and you'll be notified instantly via Email or SMS.
System events
Track unexpected system shutdowns and restarts for diagnosing system failures. Monitoring these event IDs ensures that the system operates as expected.
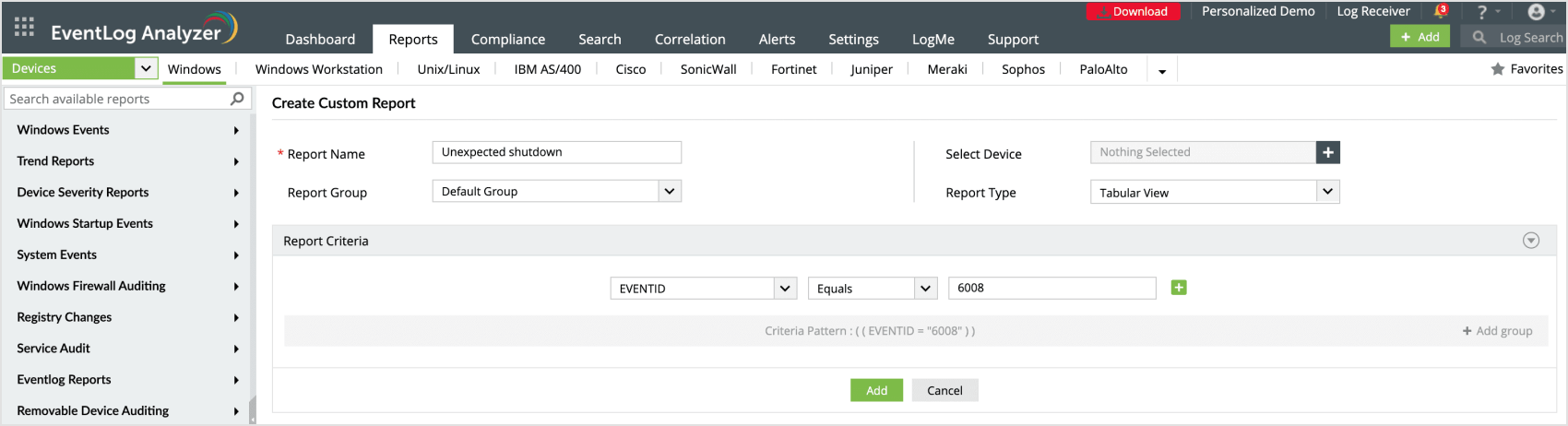
- 6008: Unexpected shutdown. This can indicate that the system was not shutdown properly, possibly due to a power failure or system crash.
- 1074: System shutdown or restart. This event provides details about who initiated a shutdown or restart and why, which is crucial for auditing system changes.
Apart from the 750+ pre-defined reports, EventLog Analyzer also allows you to create a custom report for monitoring specific Event IDs.
Policy change events
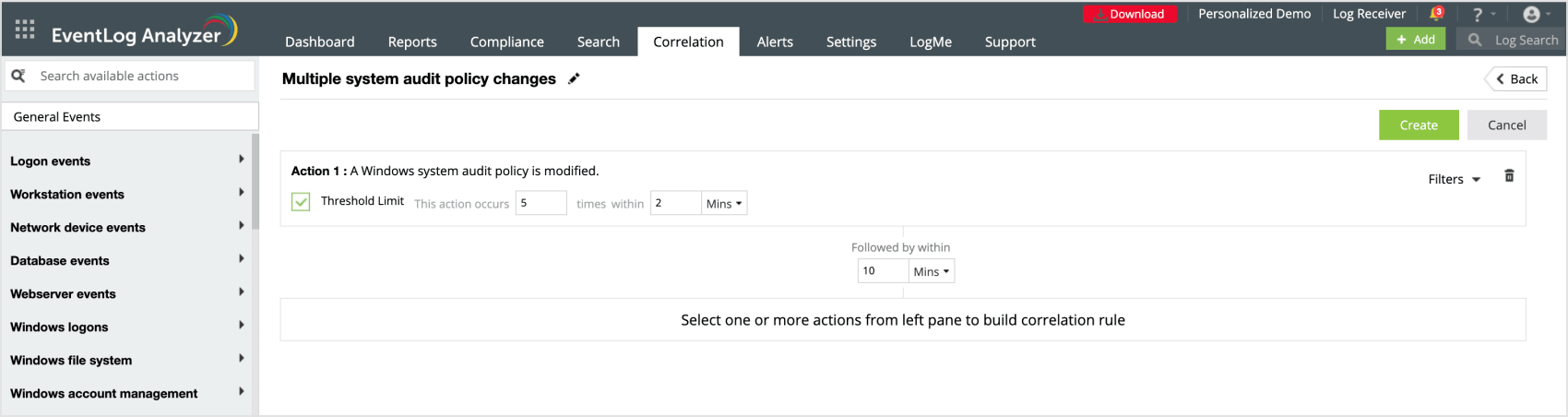
Track domain policy and system audit policy changes. Monitoring these event IDs are vital to maintain the security posture of the system and ensuring that policy changes do not introduce vulnerabilities.
- 4739: Domain policy was changed. Monitoring this event ID is vital in an Active Directory environment to track changes to security policies.
- 4719: System audit policy was changed. Indicates changes to audit policies, which could affect how events are logged.
EventLog Analyzer has out-of-the-box correlations reports to notify you about important events in your network. The correlation rule below will notify you about multiple changes in system audit policies.
For more details on what event IDs to monitor, check out Microsoft's appendix on Events to monitor.
Key features of EventLog Analyzer
- Auto-discovery
- In-depth log analysis
- Threat hunting
- Detailed reports
- Instant alerts
Auto-discovery
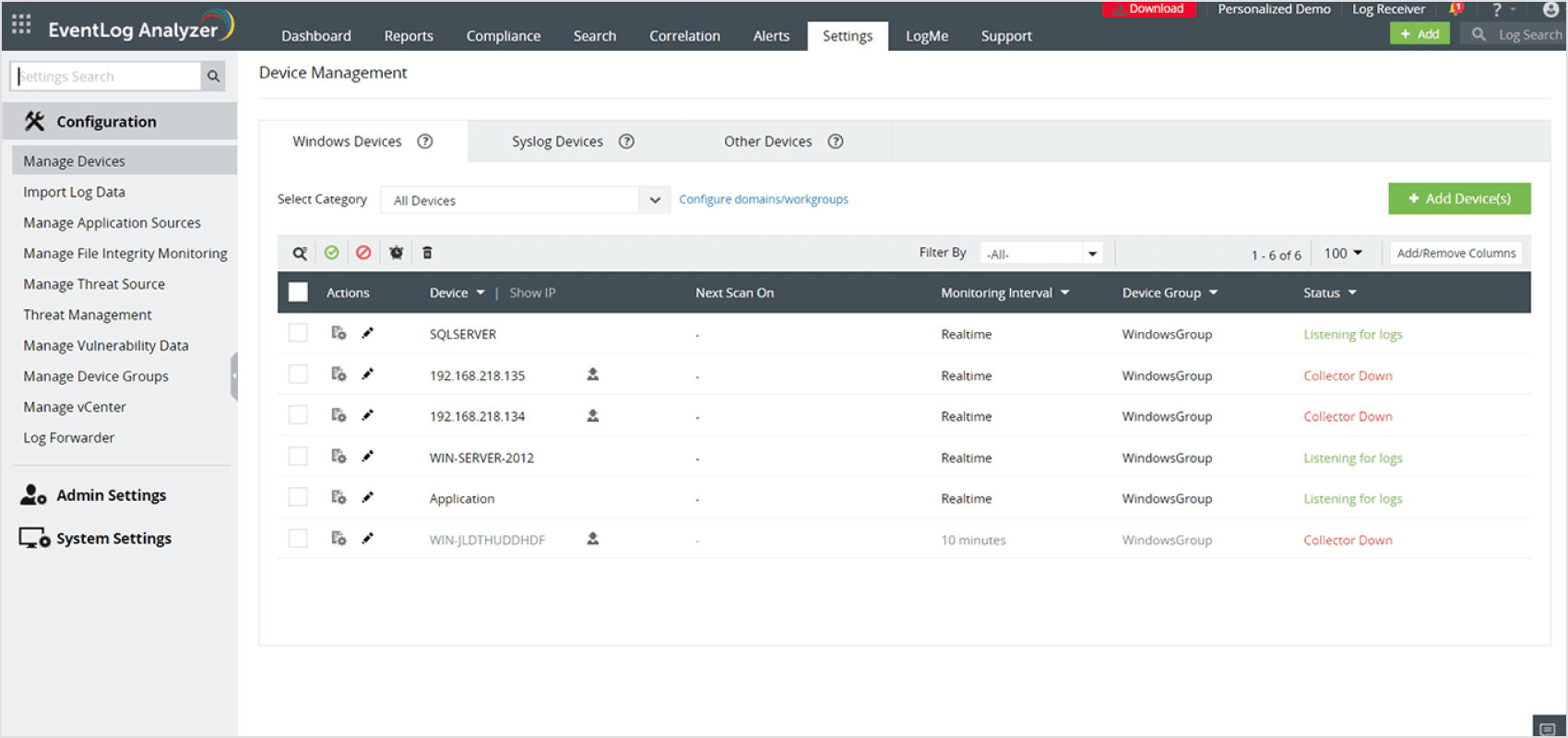
Auto discover log sources
Identify all Windows log sources in your domain and start collecting Windows event logs easily with EventLog Analyzer's auto discover option. The feature detects Windows workstations, firewalls, IIS servers, and SQL servers automatically. Simply select the critical sources and automate log file management to fortify your network.
In-depth log analysis
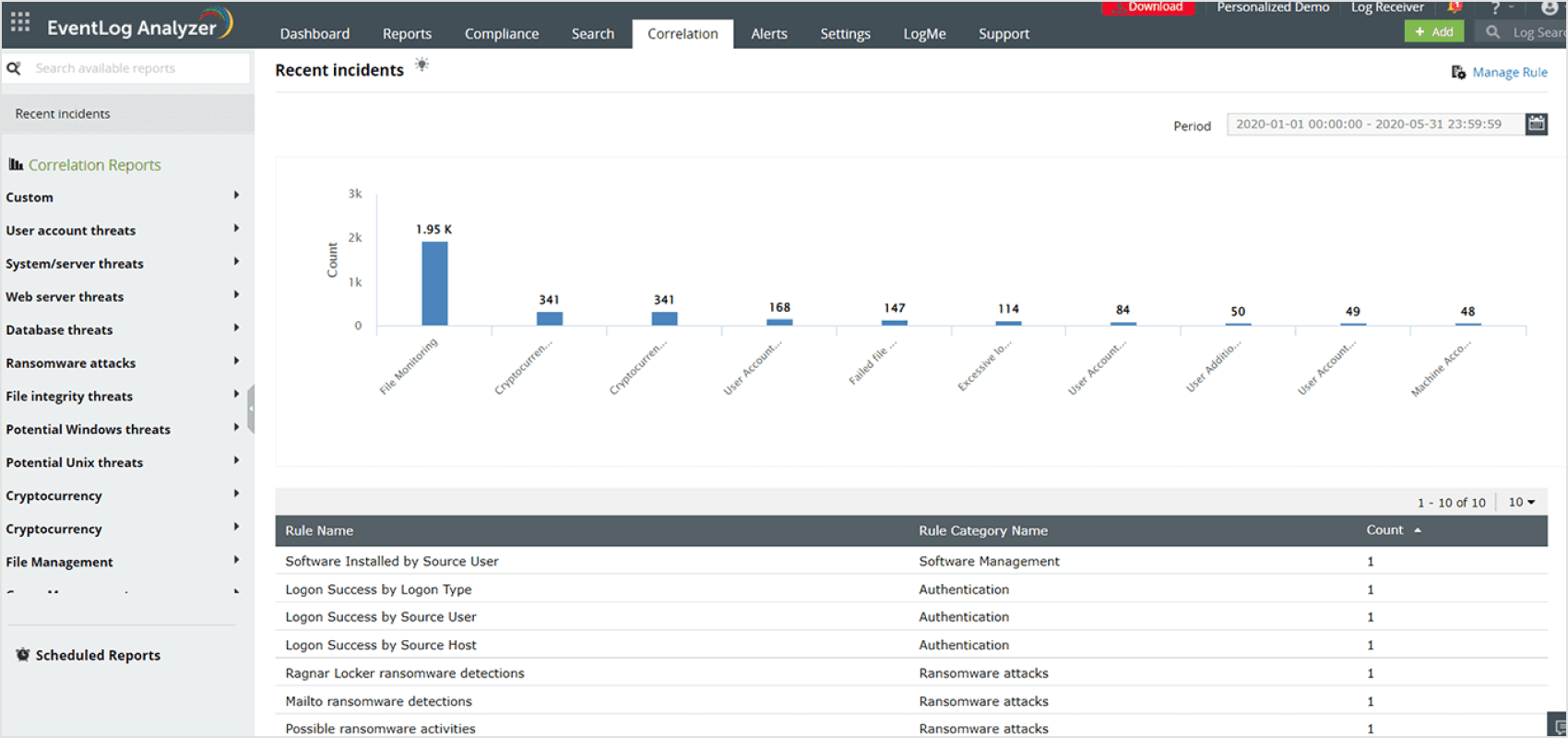
40+ predefined correlation reports
Create custom correlation rule
Utilize EventLog Analyzer's powerful correlation engine to gain comprehensive insights by making sense of log data from all the log sources present in the network. The Windows log monitoring tool contains over 40 pre-built correlation rules to detect the most common cyberattacks like SQL injection, DoS, and brute-force. You also have the option to build custom rules to detect more complex patterns.
Threat hunting
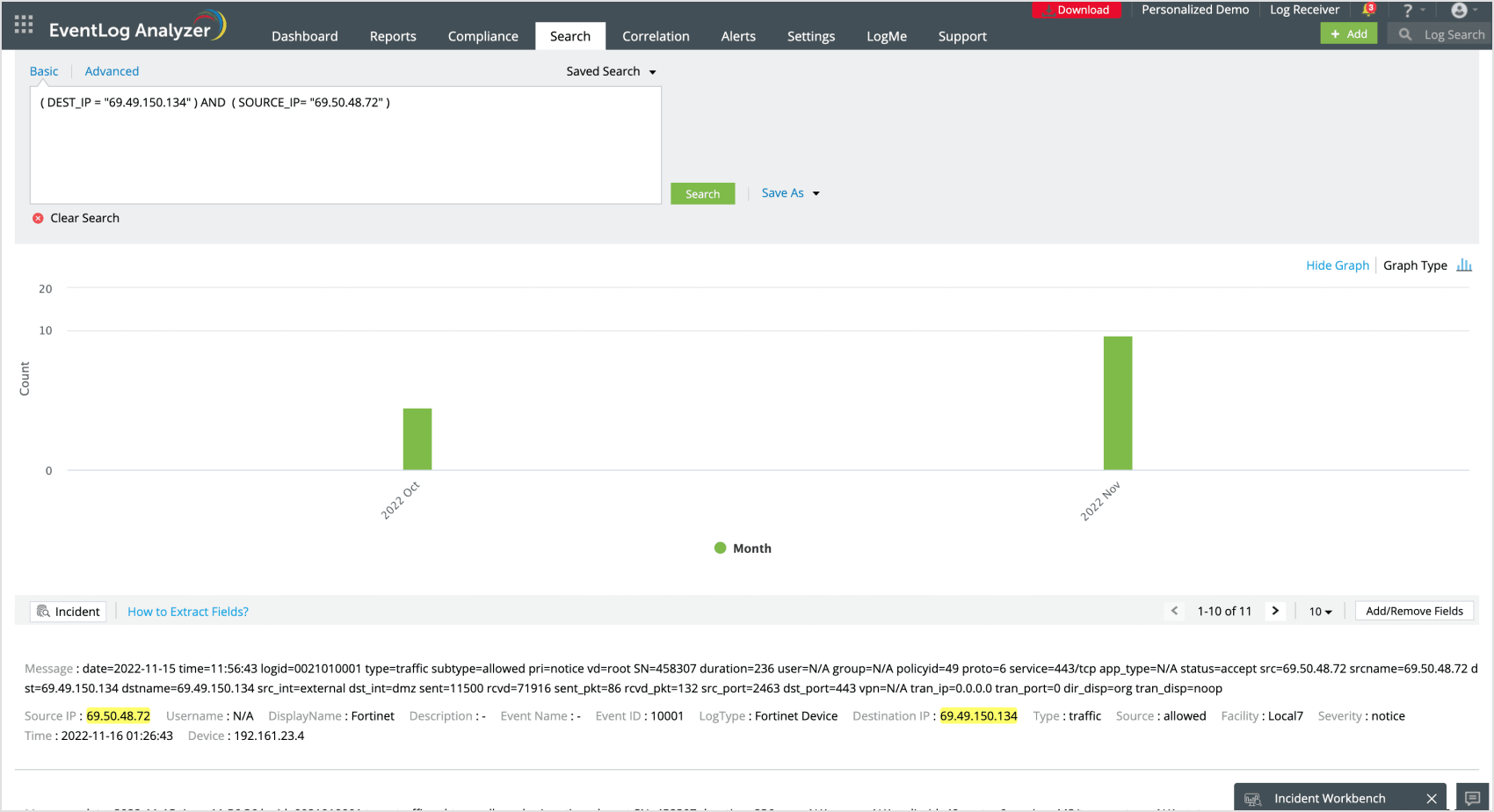
Perform in-depth analysis
Visualize critical data
Drill down to get key insights
Conduct root cause analysis for any security event in your network in minutes. EventLog Analyzer monitors Windows activity in real-time, allowing you to search through raw event logs and pinpoint the exact log entry that caused a security incident. The solution makes it easy for you to find mission-critical information about the detected incident, including the severity level, time, location, and the user who initiated the event. This helps you take the required countermeasures within a short timeframe to speed up incident resolution.
Detailed reports
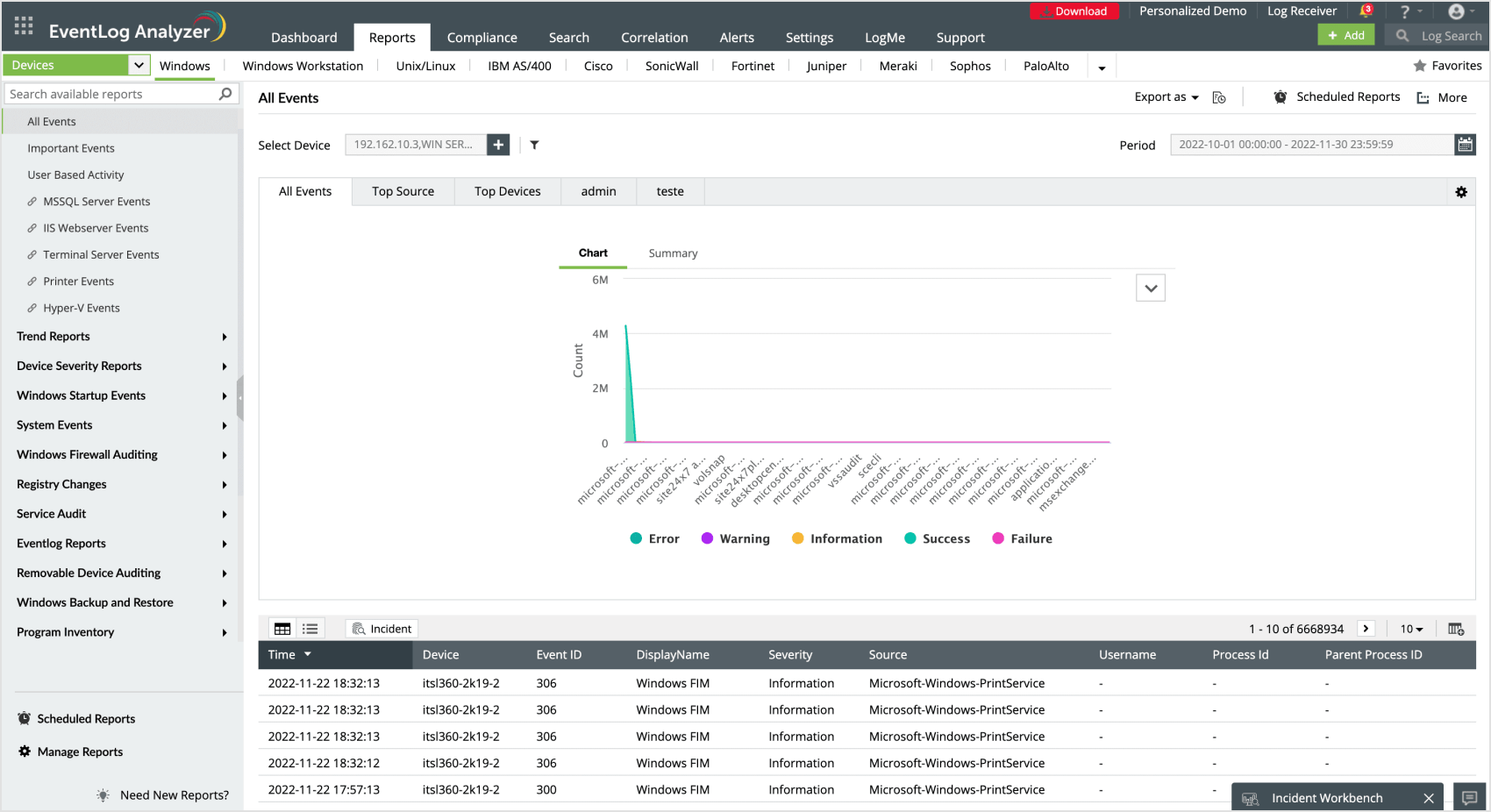
Compliance reporting made easy
750+ out-of-the-box reports
Export reports
Add to incident with a single click
Generate detailed reports based on event logs from Windows servers and workstations. EventLog Analyzer contains numerous Windows-specific report templates for security events like failed logons, account lockouts, and security log tampering. The solution also contains compliance-ready report templates for regulatory mandates like PCI DSS, SOX, HIPAA, the GDPR, and FISMA. You can also build custom reports to meet internal audit policies.
Instant alerts
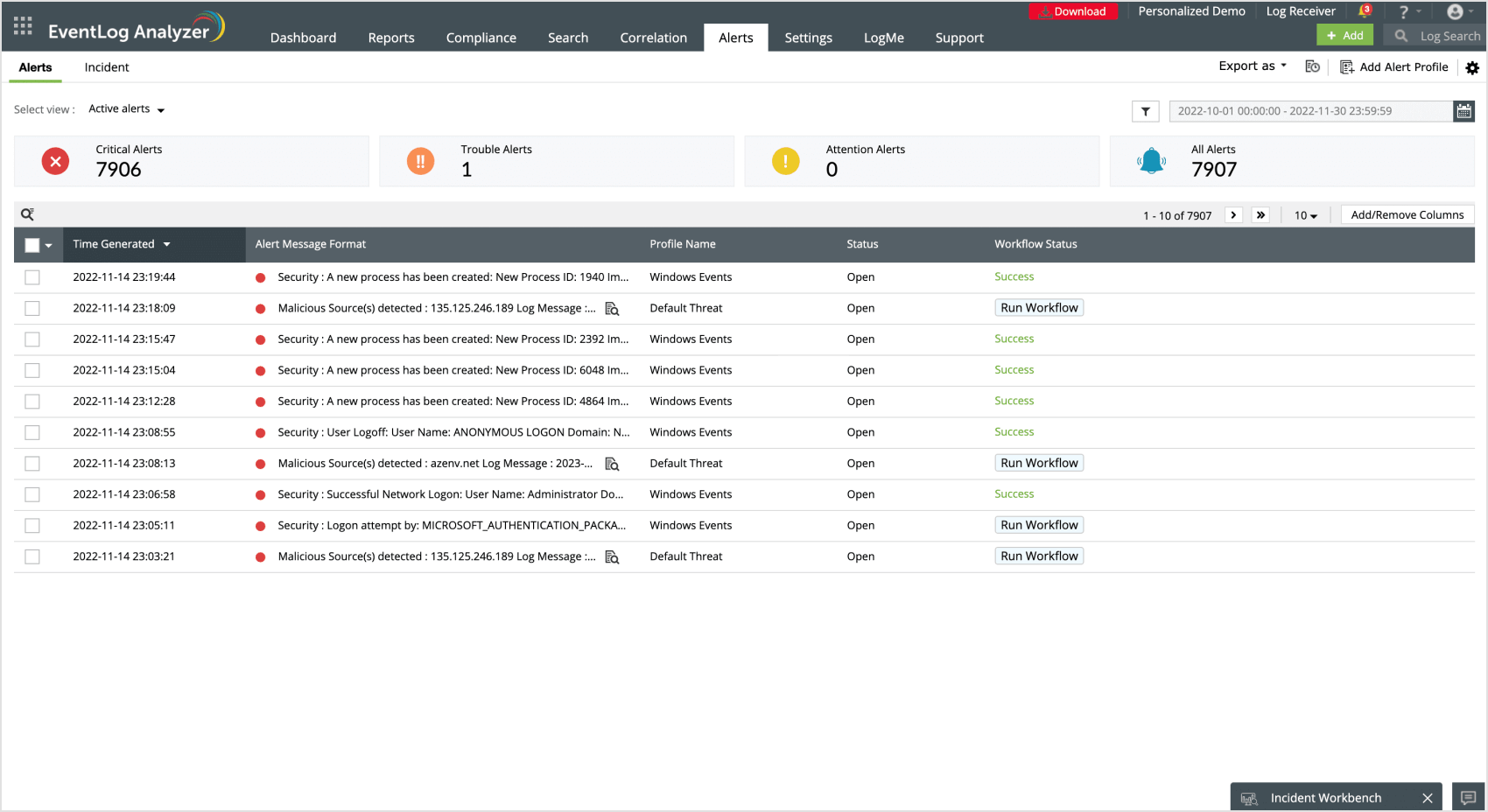
Create your own alert profile
Get notified instantly
Focus on the details
Stop threats in their tracks Run pre-defined workflows to stop an on-going threat
Detect security events happening in your network instantly and expedite the troubleshooting process. You can configure EventLog Analyzer to send real-time alerts to manage incidents based on logs generated with a specific log type, event ID, log message, or severity. It also supports integration with help desk software, so tickets can be raised automatically in your help desk software.
FAQs
What are Windows event logs?
Windows event logs are files that record all the activities taking place on a Microsoft system. In a Windows environment, events are logged for systems, security, and the applications hosted on the system. Event logs provide context with detailed information on the events, including the date, time, event IDs, source, event type, and the user who initiated it.
How does monitoring security logs help in mitigating cyberattacks?
Security event logs contain records of all the security-related events specified by the system's audit policy. This may include login and logoff attempts, modification of privileged information, and more. Windows uses event IDs to define the type of event. You should monitor the following event IDs for security-related incidents:
- 4740: Locked user account
- 4625: Failed account logons
- 4719: Changed system audit policy
- 1102: Cleared audit logs
- 4728, 4732, 4756: Added member to security global, local, and universal group
- 4777: Failed validation of account credentials by domain controller
- 4663: Attempt to access object
By monitoring Windows security logs at a granular level, you can spot anomalies, suspicious activities, and data breaches at the earliest stages to avoid full-blown cyberattacks.
How does EventLog Analyzer monitor Windows events?
EventLog Analyzer is a comprehensive log management tool that supports Windows event logs along with other log sources on a single console. The solution automates log collection through agent-based and agentless methods. Once the log is collected on a central server; it parses, analyzes, correlates, and archives the log data to complete the process. The insights drawn from the logs are presented in the form of intuitive dashboards and exhaustive reports.
EventLog Analyzer's wide range of features make it easy for network administrators to detect cyberattacks well in advance and play a vital role in keeping the network safe and sound.











