Effective network management with today's distributed network and cloud adoption is hard for organizations to follow. They need to change plans in terms of optimizing bandwidth, balancing the resource allocation process, and securing the network. However, the major challenges that come with cloud adoption are not associated with these aspects, but rather the complexity of network architectures, and lack of visibility and control. The first step in effective network management is finding a tool that provides a centralized console offering proactive monitoring, reporting, and administration.
One huge challenge with managing a network is not knowing what element can disrupt the service. Especially with the BYOD culture providing easy accessibility to corporate networks, there's little to no differentiating between internal network traffic and external networks traffic. Therefore, security and performance can become perturbed in all manners. Network forensics is an aspect of network management that can provide end-to-end visibility on the network, helping network admins investigate where it all went wrong. There are tons of network forensics tools in the market, choosing the right one for a business is crucial.
NetFlow Analyzer is an advanced bandwidth monitoring tool that not monitors but also manages enterprise network performance and security troubles with network forensic. Being a flow-based traffic analysis tool, it supports technologies such as NetFlow, sFlow, AppFlow, etc. so that you get complete traffic details.
Learn more on troubleshooting network issues faster using forensics report.
Register for a free, personalized demo now!
As an advanced network forensics tool, NetFlow Analyzer also helps you go beyond statistical bandwidth usage information with raw data reports that give you accurate insights about every nodes' traffic. Set criteria to include or exclude particular metrics based on your requirements by conversations, packets, applications, and so on.
Find which protocol has been overutilized and by which interfaces with respect to traffic volume along with application and network response times for TCP and UDP respectively. Know where exactly the problem arises and if its in anyway related to existing bandwidth capacity.
Our real-time network forensics tool also supports Cisco ASA (based on NetFlow v9), providing reports on traffic and bandwidth using NetFlow packets from ASA devices. This further cuts down the troubleshooting time and simplifies tracking configuration changes that impact network performance.
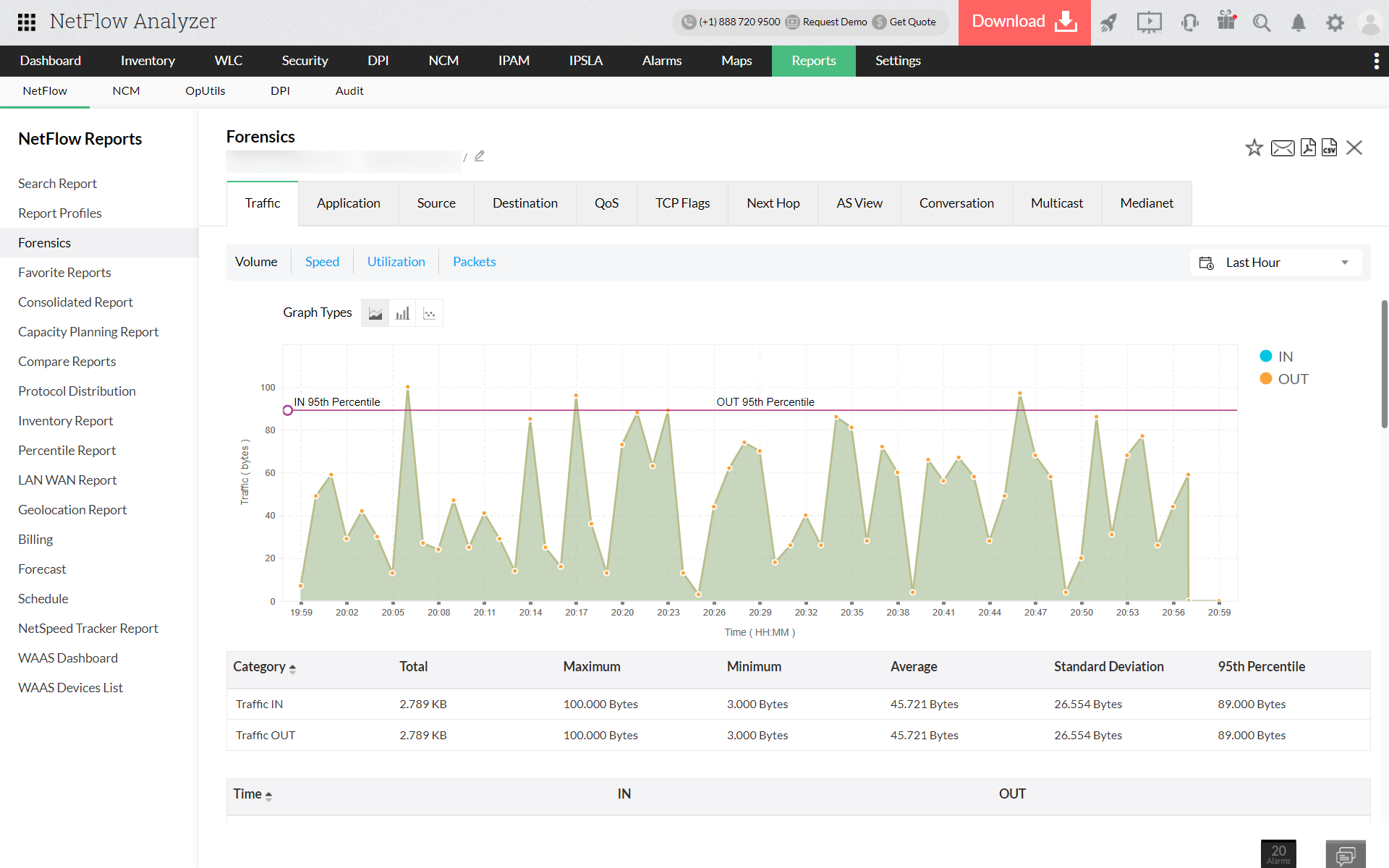
NetFlow Analyzer's network forensics feature will also help you find any irregularities in your network traffic to troubleshoot traffic spikes that can be followed by cyberattacks. On most networks, a hacker gaining entry to a network can go undetected for a long time. NetFlow Analyzer's network forensic tool can help you look back on historical data to see how network traffic behavior has changed and detect the severity of the issue. This way, you can reinforce the accessibility rules and limit or block certain IP addresses.
NetFlow Analyzer is the best network forensics tool that can:
Featured links
View how enterprise network bandwidth is used. Allocate enough bandwidth for applications critical to business.
Get real-time visibility into your network traffic using NetFlow Analyzer. Know who your top talkers are on the network in real-time.
Monitor critical factors affecting VoIP, Video performance and ensure best-class service levels. Ensure seamless WAN connectivity through WAN RTT monitoring.
Validate the effectiveness of your QoS policies using CBQoS reports from NetFlow Analyzer. Prioritize your network traffic accordingly.
Assess future network requirements based on capacity planning reports.