

Endpoint Central's Privilege Management delivers a control layer that governs how applications obtain and use elevated rights. The following sections outline the behavior of the associated agent components and the mechanisms that enable Privilege Management to protect endpoint environments.
| Agent Process | Running Application Name | Bandwidth Consumption (Approximately) | CPU Consumption (Approximately) | Memory Consumption (Approximately) |
|---|---|---|---|---|
| Admin Accounts Scanner | DRAdminUsers.exe | NA | 0-1% | 1-5 MB |
| Process Notifier | AppCtrlToast.exe | NA | 0-1% | 20 MB |
| ACP Privileger | Privilager.exe | NA | 0-1.4% | 1-1.5 MB |
| Component Upgrade | dcconfig.exe | 3.5 MB | 0-1% | 1 MB |
After agent installation, a one-time scan is initiated. The agent runs a dedicated scan to identify local administrator accounts using DRAdminUsers.exe. This scan focuses exclusively on local admin accounts and executes during every 90-minute refresh cycle.
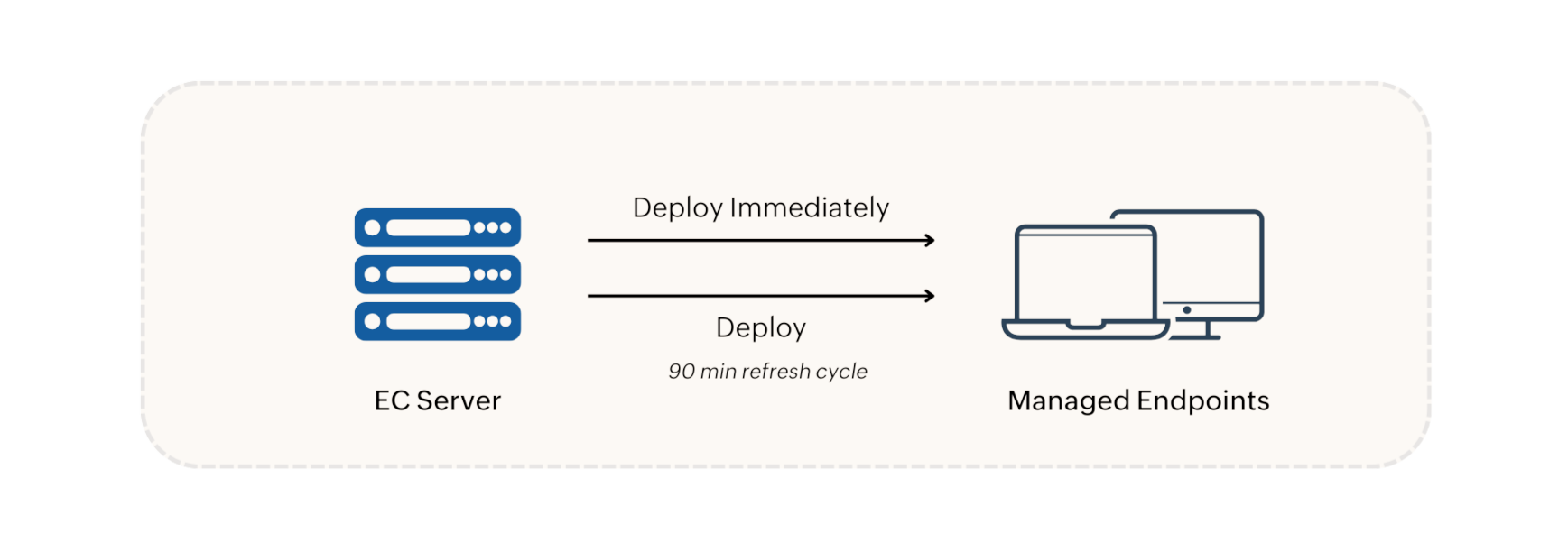
When an Application Control policy is created, it is deployed by dcconfig.exe in the following two options:
Policy modifications, deletions, group changes, and unmanaged application updates are synchronized with agent machines during refresh cycles. In environments with a Distribution Server, policies and configurations are replicated to the Distribution Server and then synchronized with agent machines during the 90-minute refresh cycle.
The Application Control policy will be received in the agent and VerifyTrustedFiles.exe will invoke Privileger.exe to elevate the processes according to the deployed policy. The elevated application events will be posted in the 90-min refresh cycle and will be updated every 7 days.
Once manual or automatic removal of admin rights is implemented, the specific admin accounts will be removed by DRAdminUsers.exe.
Just-In-Time policies provide time-bound elevation provision for specified applications. When a JIT policy is deployed, VerifyTrustedFiles.exe will invoke Privileger.exe to elevate the processes on the deployed machine/user, with the elevated privileges being automatically terminated after the specified duration.
The following table provides the supported extensions for each rule type:
| Extensions | Vendor | Product Name | Verified Executable | File Hash | Folder Path | CLS-ID |
|---|---|---|---|---|---|---|
| EXE, MSI | ✔ | ✔ | ✔ | ✔ | ✔ | ✗ |
| MSC | ✗ | ✗ | ✗ | ✔ | ✔ | ✗ |
| BAT | ✗ | ✗ | ✗ | ✔ | ✔ | ✗ |
| COM Components | ✗ | ✗ | ✗ | ✗ | ✗ | ✔ |
|
Related Articles: End-User Notifications of Privilege Management |