- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Check Point Next Generation Firewalls aggregate several security technologies within a single appliance, namely those of a firewall, IDS, IPS, and an antivirus solution. Sorting through the log data generated by each of these applications will give you a clear picture of what's happening in your network. You can use this information to bolster your security policies and also gain an edge in the fight against evolving threats.
With built-in support for the Check Point log format, EventLog Analyzer helps you efficiently manage these devices with features such as automatic, centralized log collection; in-depth forensics; and secure archival. EventLog Analyzer also offers predefined reports on various device functionalities, and alerts you via email or SMS when it detects suspicious activity.
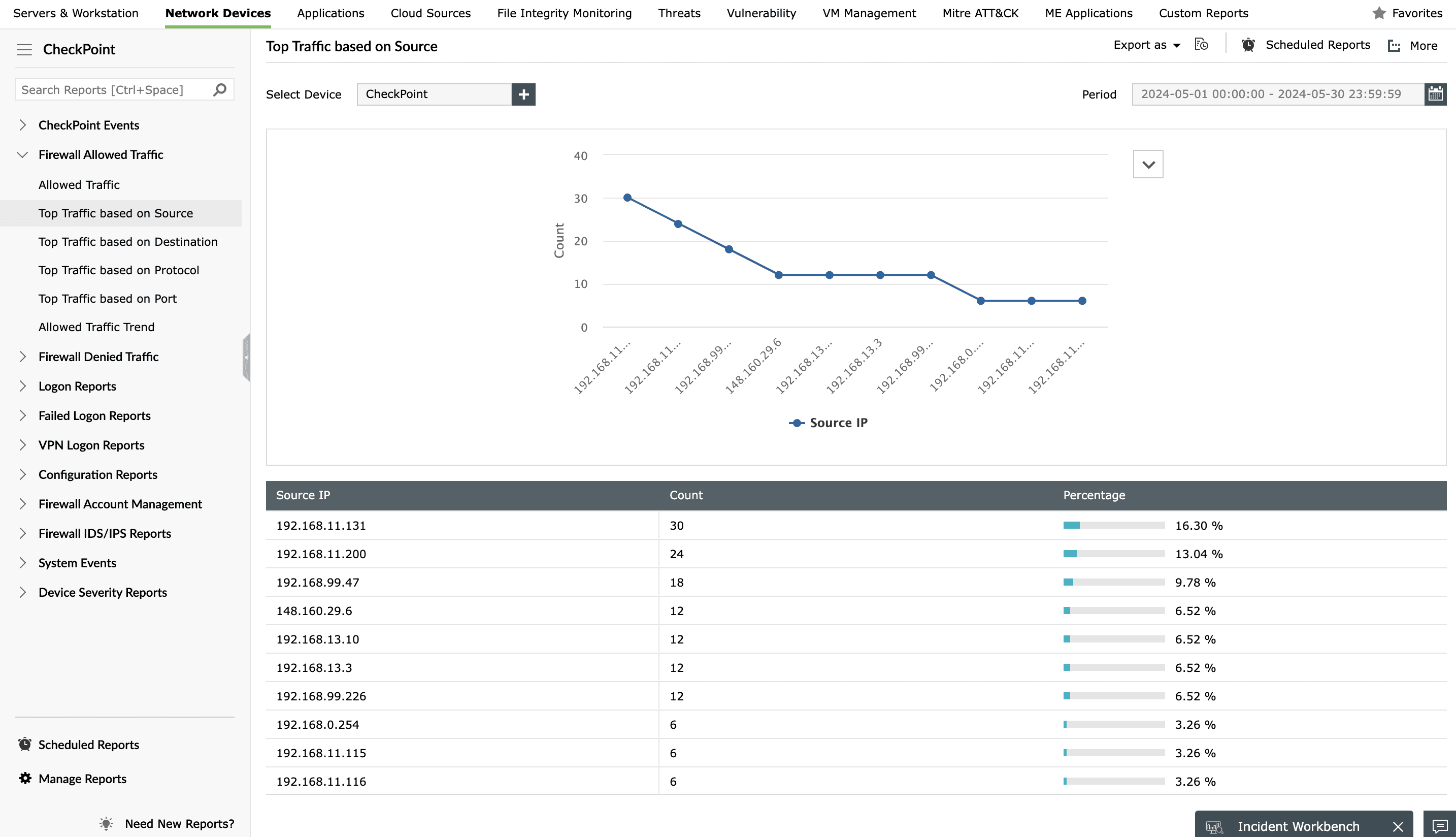
Analyze network threats using Check Point log reports
Check Point Firewall Allowed Traffic reports
Analyze Check Point traffic logs and sort through reports for allowed and denied traffic to learn where your network traffic is coming from. You can analyze the traffic based on its source, destination, port, or protocol.
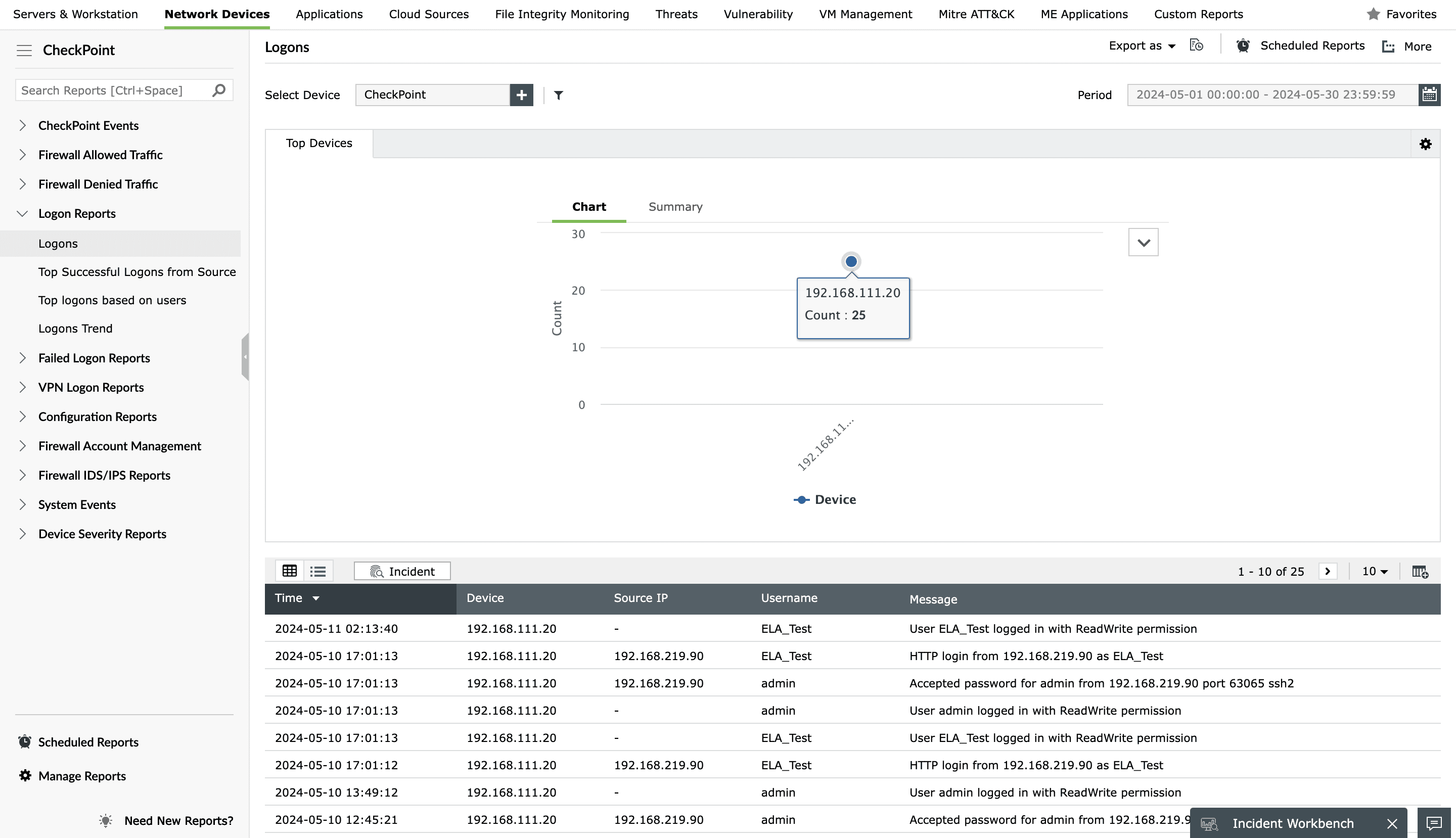
Check Point Logon Reports
You can also monitor successful and failed Check Point logons, identify devices used frequently, and view the users who access your Check Point devices often. Monitoring access helps you keep device usage and activity in check.
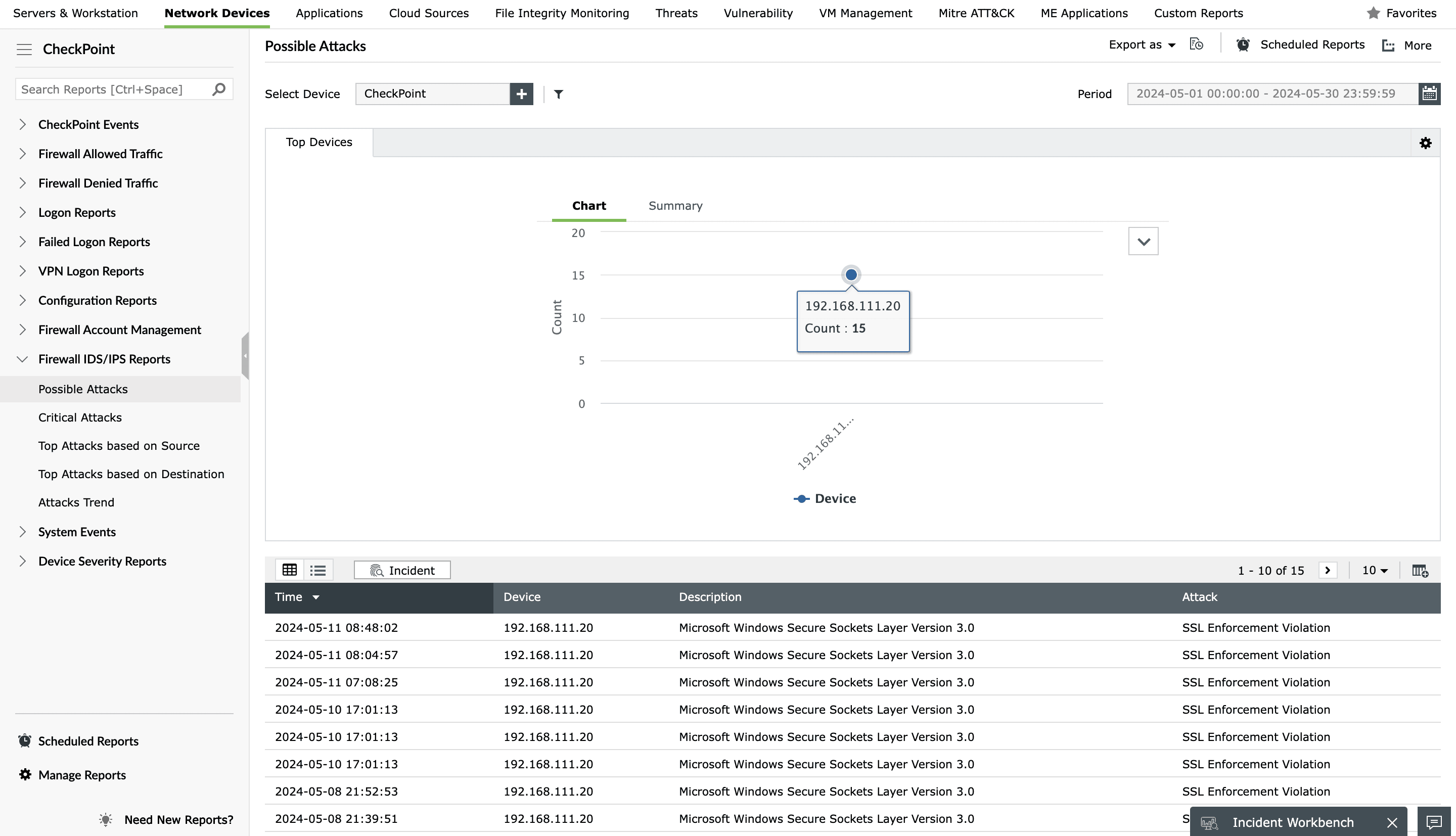
Check Point Firewall IDS/IPS Reports
Guard against network attacks with security reports based on Check Point IDS/IPS logs. View a list of positively identified attacks, critical attacks, and potential threats to your network that need further investigation. You can sort these Check Point security reports by source or destination.
Check Point VPN Logon Reports
Check Point VPN Logon Reports help you monitor various VPN activities, such as successful and failed VPN logons, VPN logouts, or VPN user status.
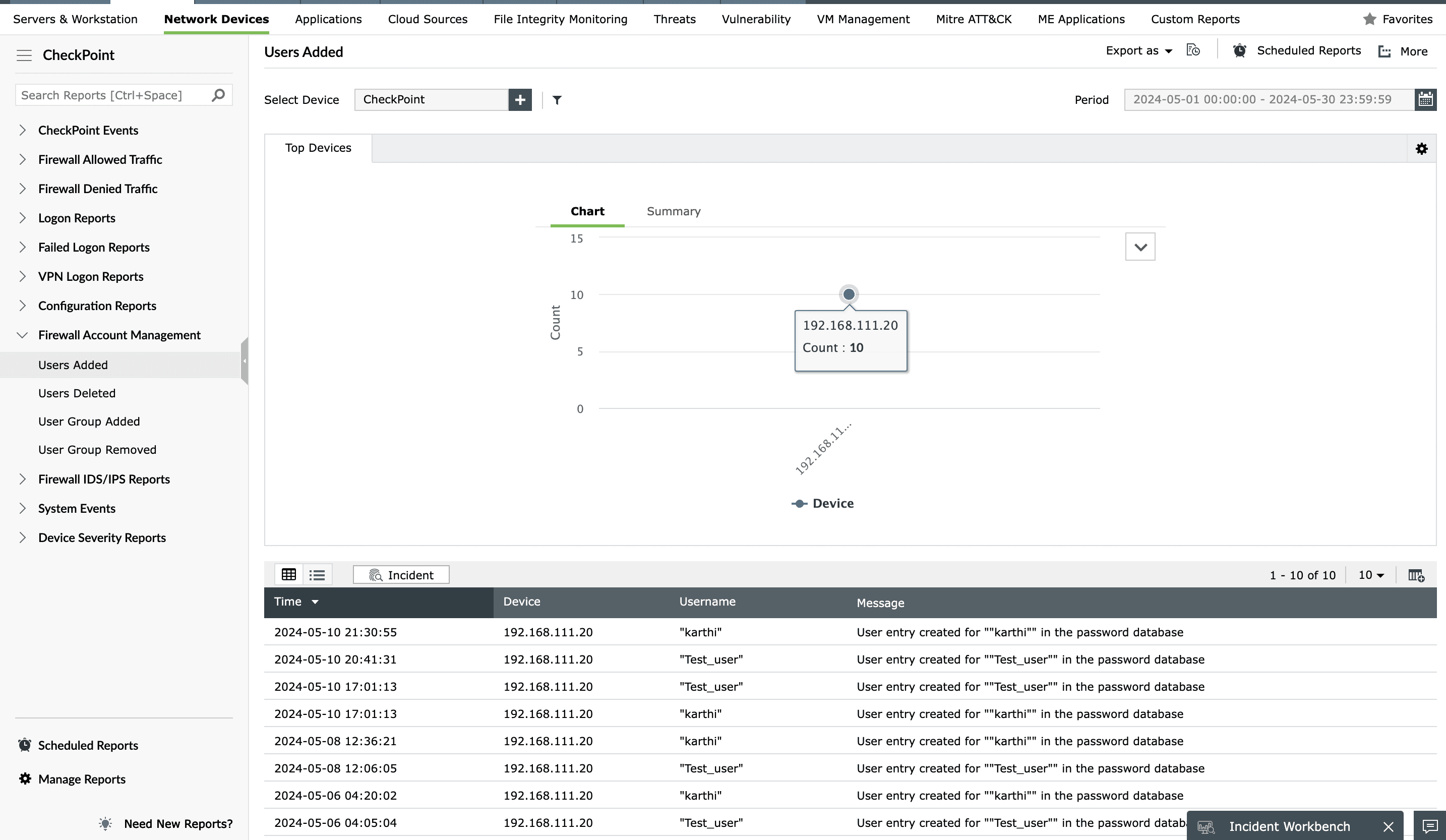
Check Point Firewall Account Management Reports
Monitor every user account on your Check Point devices and ensure only trusted accounts exist. Use the Account Management Reports to view lists of users and user groups that were added or deleted.
Check Point Configuration and System Events reports
Monitor Check Point configuration changes, commands executed, interface availability, and more using EventLog Analyzer's Check Point Configuration Reports. You can also view a list of clock updates and devices that have shut down to ensure that your devices are functioning properly using System Events reports.
Check Point Device Severity Reports
EventLog Analyzer's Checkpoint Device Severity Reports help you analyze various events by categorizing them based on their severity levels: Emergency, Alert, Critical, Error, Warning, Notice, Information, or Debug.












