- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
F5 Networks, Inc. develops devices that enable application services and application delivery networking (ADN). Since F5 devices play a key role in the delivery, performance, availability, and security of web applications, it's vital to audit F5 device logs to ensure network security. Your F5 devices generate huge volumes of F5 logs every day, and it's impossible for you to examine all of them on your own.
ManageEngine EventLog Analyzer simplifies the monitoring and auditing process by sifting through the logs for you regularly, enabling you to keep tabs on the critical events occurring in your network. EventLog Analyzer also provides out-of-the-box support for F5 devices by providing you with a rich set of predefined reports and alert profiles along with correlation and forensic analysis.
EventLog Analyzer F5 Load Balancer Log Monitoring Tool
Logon Reports
View the list of all successful logons to the devices, including the hosts and users with the most number of logons. You can also view the overall trend in logon patterns.
Failed Logon Reports
See all failed logon attempts to the devices, hosts, and users with the most number of failed logons. You can also view the trend in failed logon patterns.
LTM Health Monitoring
Monitor the Local Traffic Manager (LTM) module with out-of-the-box reports such as Monitor Status, Node Status, Pool Status, Pool Member Status, and Virtual Server Status.
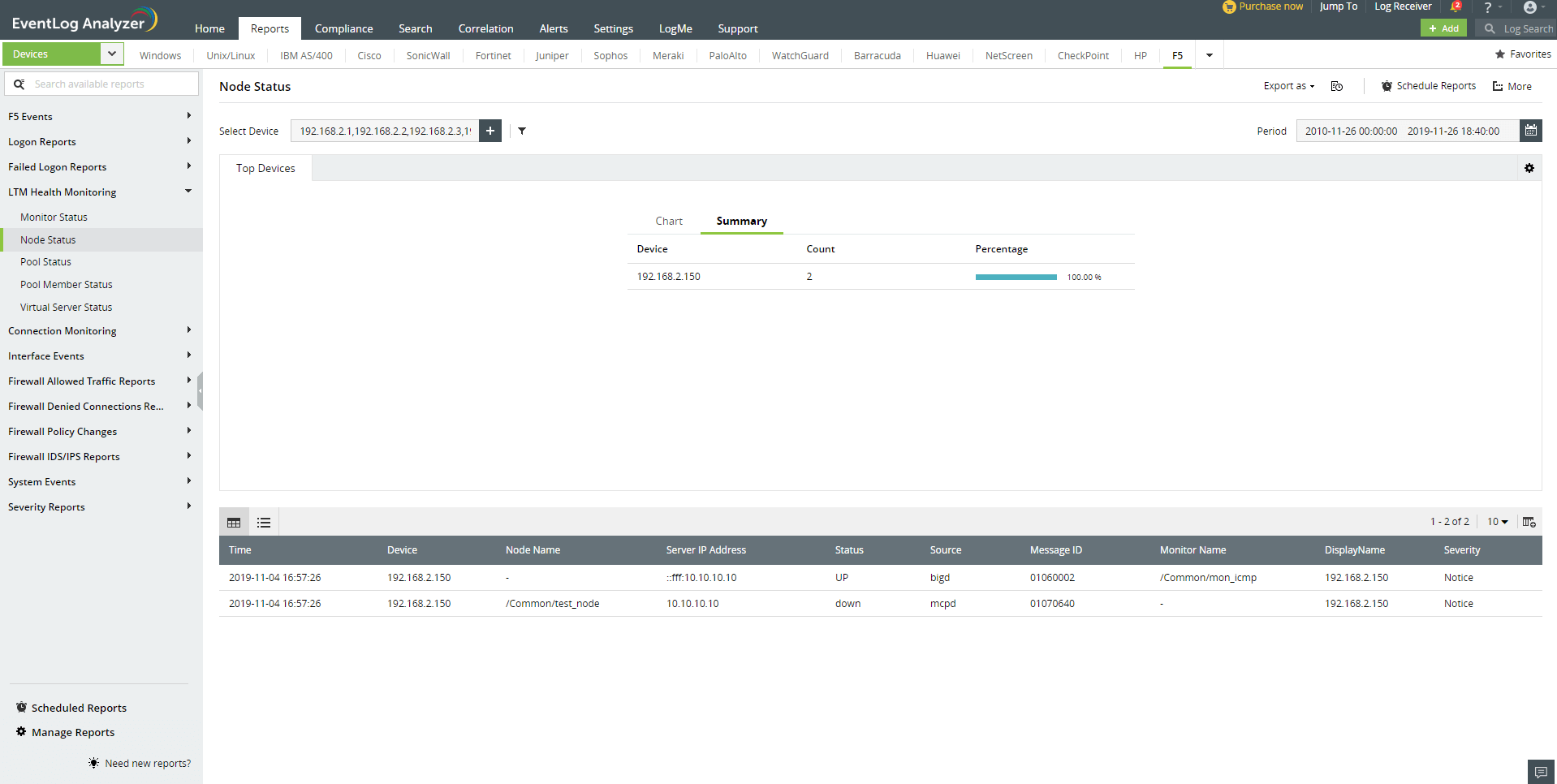
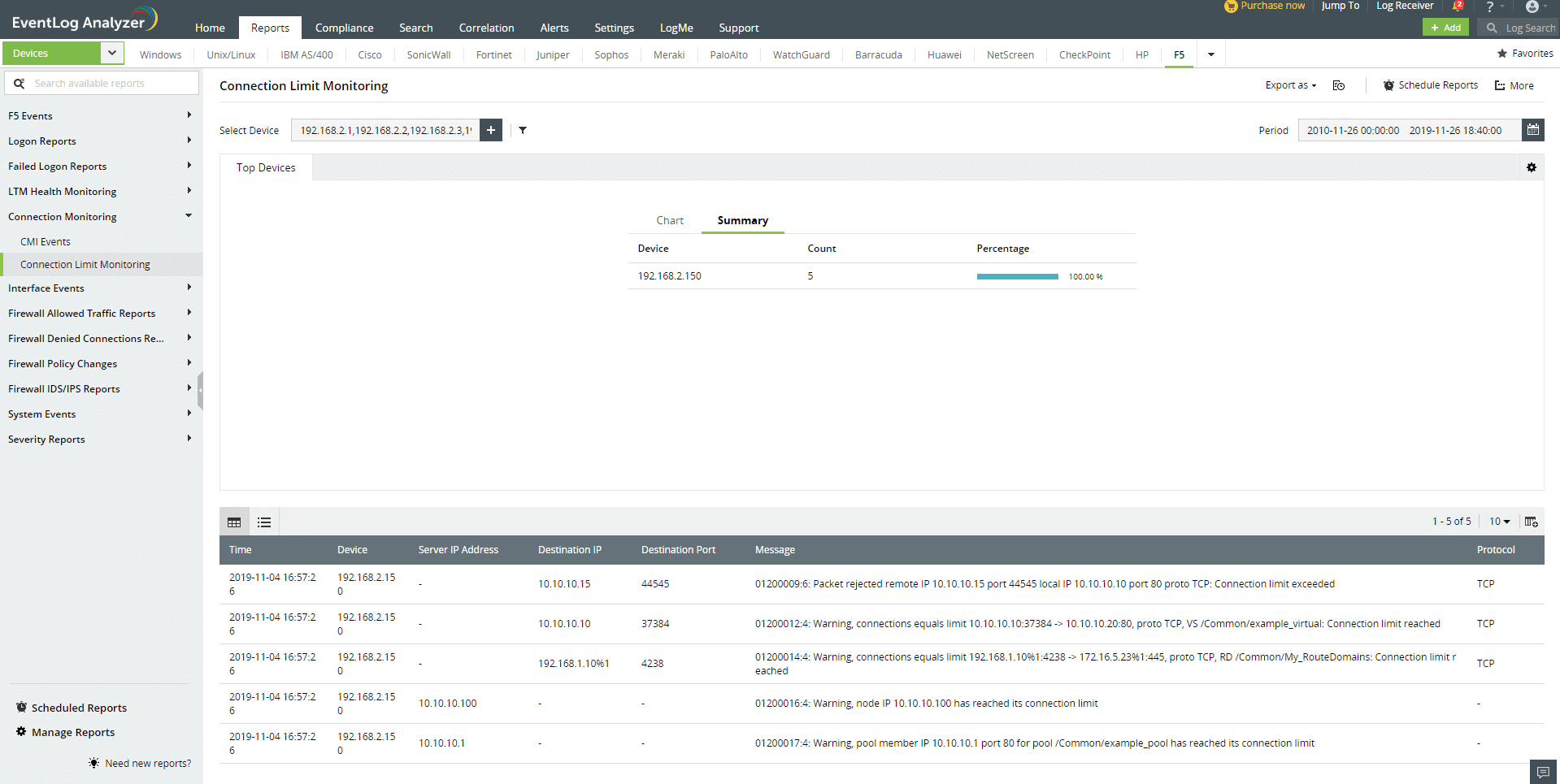
Connection Monitoring
These reports present insights on all the network connections to your F5 devices.
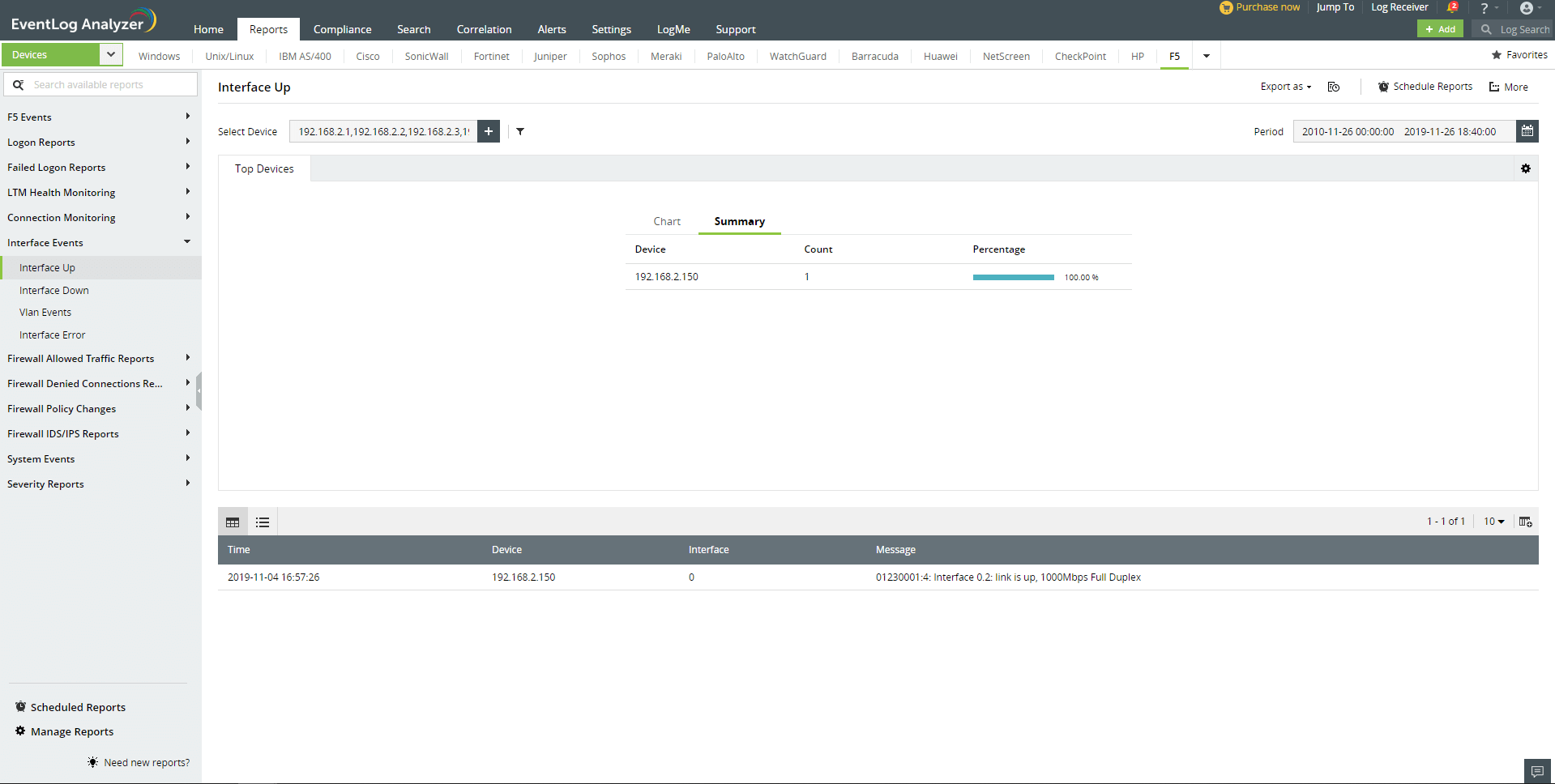
Interface Events
These reports show all events related to the interface including Interface Up, Interface Down, Interface Error, and Vlan Events.
Firewall Allowed Traffic
These reports present insights on all the connections that pass through the F5 firewall and into your network so you can monitor traffic patterns and trends more easily.
Firewall Denied Connections
Similar to allowed traffic reports, these reports detail all the connections that are denied access to the network, providing you with traffic patterns and trends as well.
Firewall Policy Changes
Firewall policies decide how the incoming and outgoing network traffic should be treated. Insiders with malicious intent can gain access to the network by tampering with security policies employed by your F5 devices. With firewall policy management reports, you can monitor all the added, deleted, enabled, and disabled policies in your F5 firewall.
Firewall IDS/IPS Reports
These reports list possible and critical attacks, as well as identify the source and destination devices most frequently involved in attack attempts. You can also view an attack trend report.
Severity Reports
Analyze F5 logs to gain a clear picture of the events happening in your network based on their severity such as emergency, alert, critical, error, warning, notice, information, and debug.
F5 Events
View the list of important events and all events happening in your F5 network.
System Events
Manage F5 system events such as license expirations, power failures, restorations, systems reboots, shutdowns, command failures, and configuration changes.
EventLog Analyzer's correlation feature helps you find the missing link between multiple yet seemingly irrelevant security incidents. With powerful forensic capabilities, you can drill down to the root cause of such security incidents in your network.
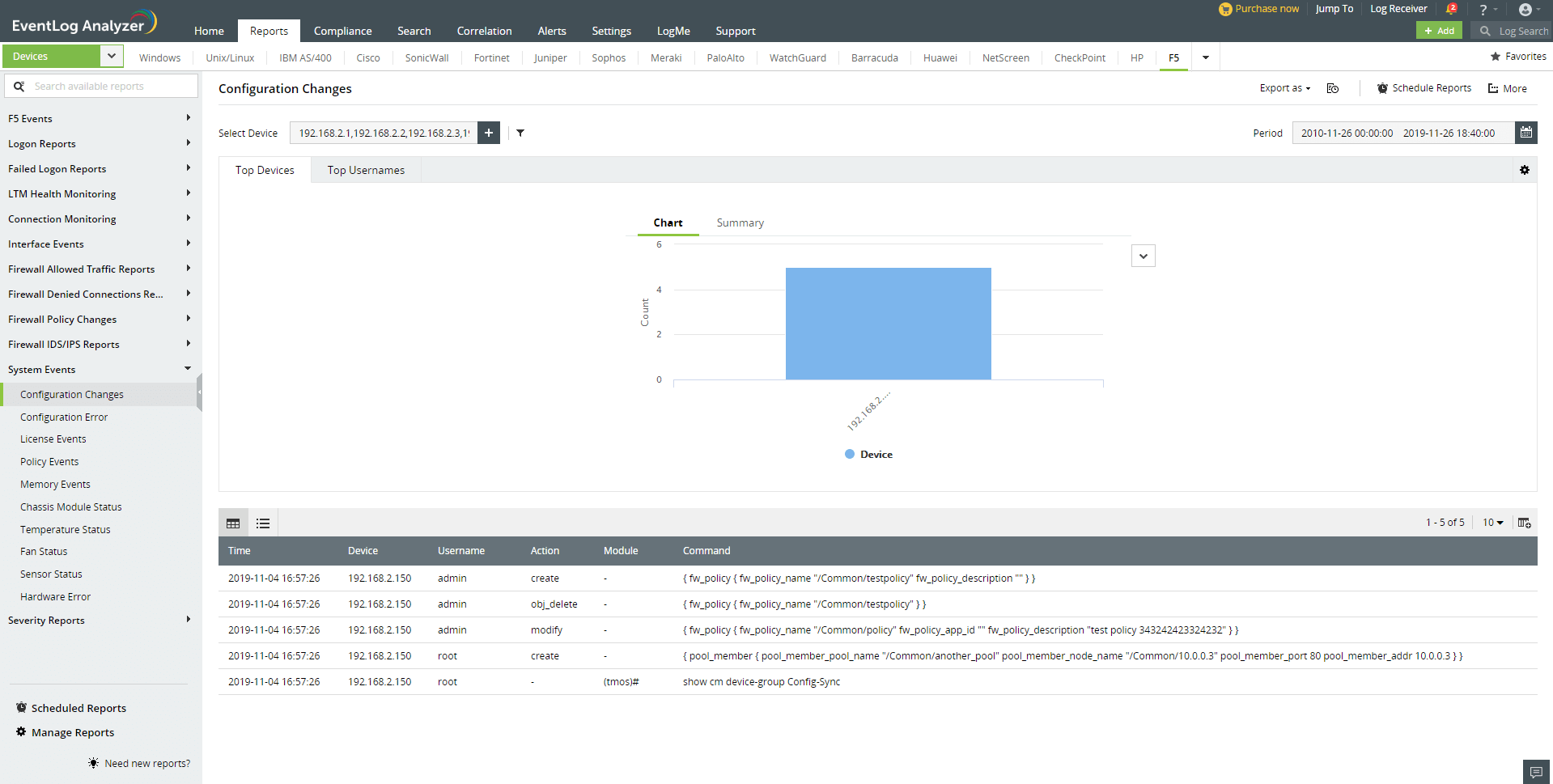
ManageEngine EventLog Analyzer provides you with:
- An easy-to-use interface with an intuitive dashboard.
- Over 60 out-of-the-box reports for F5 devices that aid in security and compliance auditing.
- Customizable report templates for F5 traffic logs to meet internal policy needs.
- Custom compliance reports fulfilling growing compliance standards.
- Real-time email and SMS alerts on events of interest.
- F5 monitor logging and powerful log forensic analysis with a high-speed log search engine that uses various search algorithms including boolean, range, wild card, group searches, and more.











