- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
What is GDPR compliance?
The General Data Protection Regulation (GDPR) is comprised of 11 chapters with 99 articles requiring enterprises to protect the personal data and privacy of European Union citizens. Complying with the GDPR is a tedious process as it requires changes to the enterprise's security strategy; the way the enterprise stores, handles, and processes sensitive data; and more. Noncompliance with the GDPR can result in organizations having to pay hefty fines up to €20 million or 4% of their global revenue, whichever is higher.
ManageEngine EventLog Analyzer, log and compliance management software, helps enterprises easily comply with GDPR requirements. It assists with complying with the GDPR requirement to have "the ability to ensure the ongoing confidentiality, integrity, availability, and resilience of processing systems and services" (Chapter 4, Article 32, 1(b)). Furthermore, EventLog Analyzer aids data protection officers in communicating the impact of a data breach with detailed incident analysis and reports.
Related content
Learn how EventLog Analyzer simplifies GDPR compliance
Breach notifications
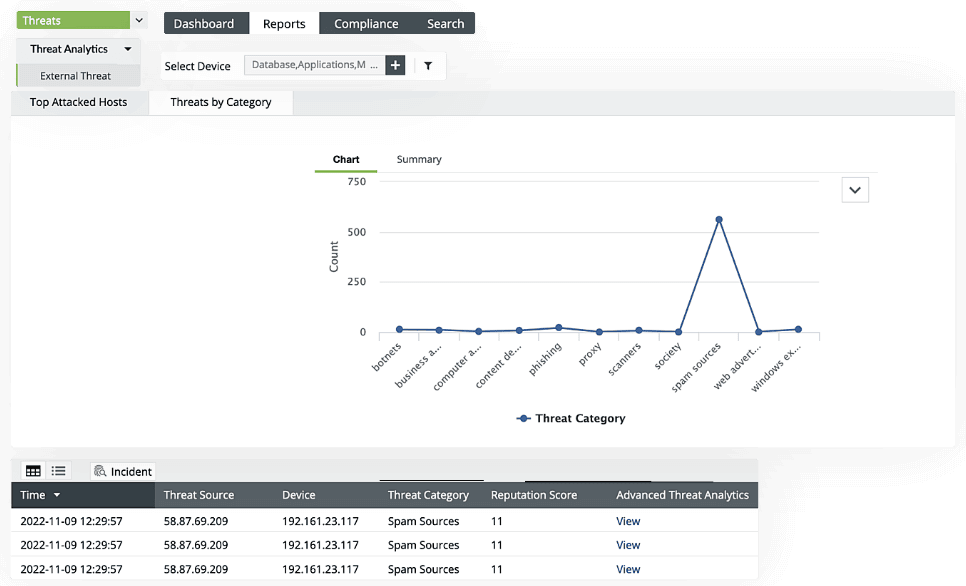
The advanced threat intelligence capability of EventLog Analyzer combined with the MITRE ATT&CK® framework help with the detection of data breaches and efficient incident response. EventLog Analyzer generates detailed incident reports that help in impact assessments. Get real-time alerts about correlations and GDPR breach violations with EventLog Analyzer's real-time alerting feature, then submit a data breach report to higher authorities within 72 hours of the occurrence. Moreover, EventLog Analyzer helps protect personal data from data exfiltration attempts and ensures the confidentiality and integrity of stored data is in accordance with Article 32 of the GDPR: Security of processing.
User monitoring and policy changes
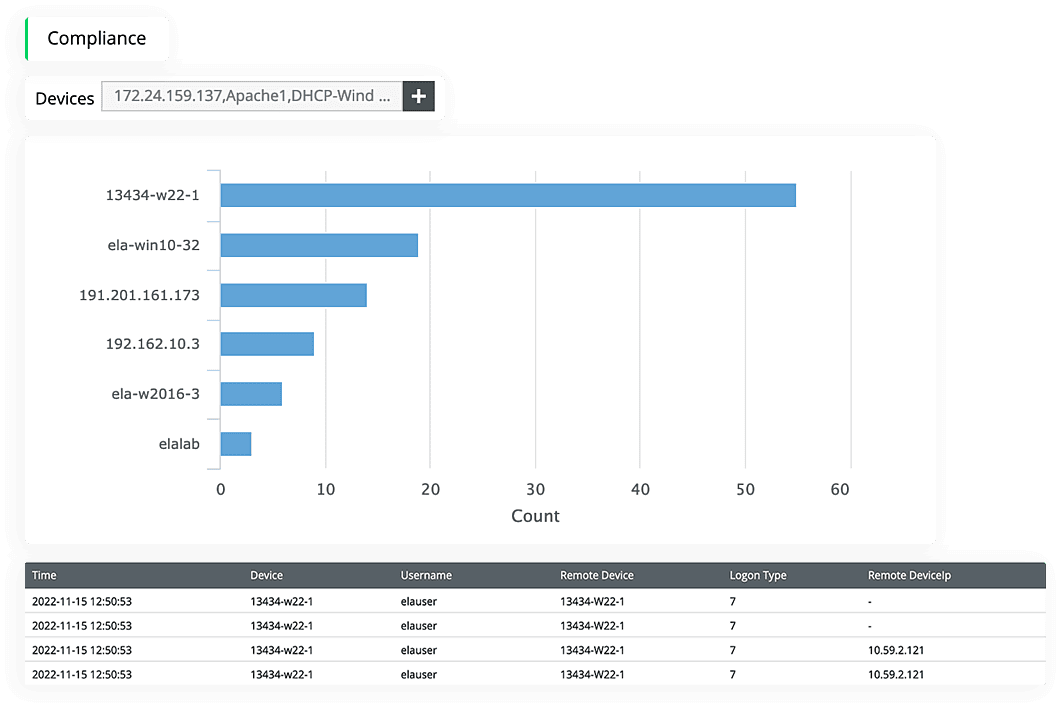
Your organization must be transparent and responsible in user monitoring and policy changes in order to comply with the GDPR. EventLog Analyzer strengthens your organization's data security posture and ensures privacy by enforcing proper security measures when personal data is handled. It provides contextual audit trails that capture all events to prevent potential security breaches. It also helps monitor account activities, user activities like successful and failed logons and logoffs, and database activities throughout your network, taking appropriate remedial action whenever necessary.
Conduct in-depth GDPR data auditing
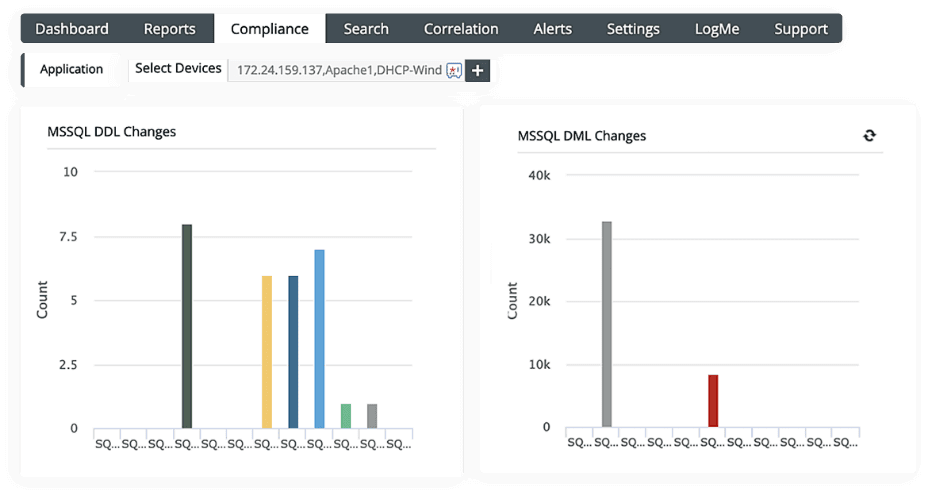
One of the requirements of the GDPR is maintaining the integrity and confidentiality of personal data stored in databases. EventLog Analyzer's real-time database auditing capabilities help you monitor all the changes made to your database tables, such as data definition language (DDL) and data manipulation language (DML) changes (like select, insert, delete, and update queries).
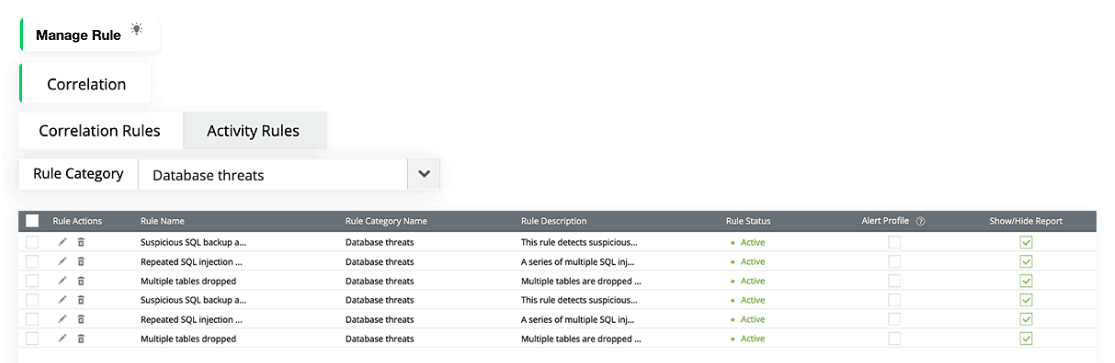
Additionally, EventLog Analyzer helps you detect database attacks like SQL injection and denial-of-service attacks. It also identifies data breaches like unauthorized database backups. The solution sends an instant alert whenever a critical change is made to a database where personal data is stored. EventLog Analyzer provides insights into your organisation's data processing activities and helps in identifying potential data breaches and noncompliance with the GDPR.
Ensuring personal data integrity
Complying with the GDPR's Article 32, which mandates the security of personal data processing, is a crucial responsibility for every organization. To aid organizations in meeting this requirement, EventLog Analyzer offers comprehensive solutions that guarantee the integrity, availability, and confidentiality of personal data.
With its file integrity monitoring (FIM) and column integrity monitoring capabilities for databases, EventLog Analyzer ensures that personal data is protected from any unauthorized access, modifications, or security threats. It monitors all file activities, such as new file creations, existing file modifications, file renames, and file deletions, to ensure that all changes made to executable files, folders, system configuration files, content files, zipped files, and zipped folders are thoroughly tracked. A deviations from established baselines will trigger alerts.
Additionally, EventLog Analyzer conducts detailed audit trails of user logons and permission changes to file servers that store personal data, consolidating all pertinent data in FIM reports. As a result, it assists organizations in ensuring that the confidentiality and integrity of their systems are not jeopardized.
Exhaustive incident reports to help with impact assessments
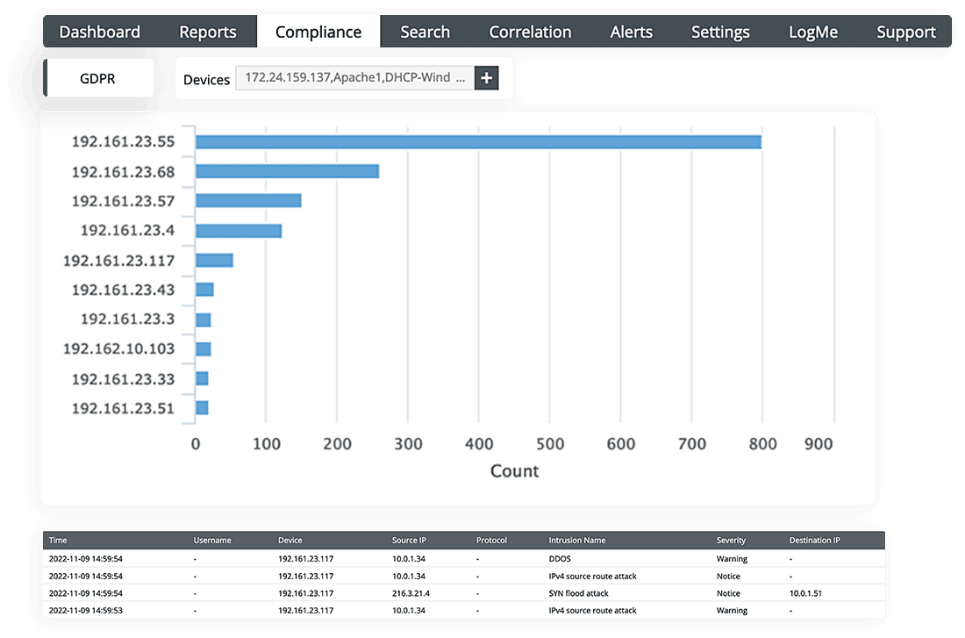
EventLog Analyzer correlates events across different network entities to accurately spot attack patterns. It helps create custom correlation rules that detect suspicious software installations and unauthorized backup activities. EventLog Analyzer's incident report feature also supports correlation by grouping related events together based on severity levels, sources, and timestamps, helping you assess the impact of these events on the affected systems.
The incident response and management console triggers automated workflows for incident alerts and responds as needed, without intervention from a security administrator, thus minimizing critical incident response times. You can also configure the solution to automatically raise tickets and assign them to the appropriate security admin so that the admins can act quickly in response to incidents. The solution's centralized incident manager console helps you identify all security incidents in one place, letting you prioritize threats and take quick remedial action.
Conduct log forensic analysis using a powerful log search feature
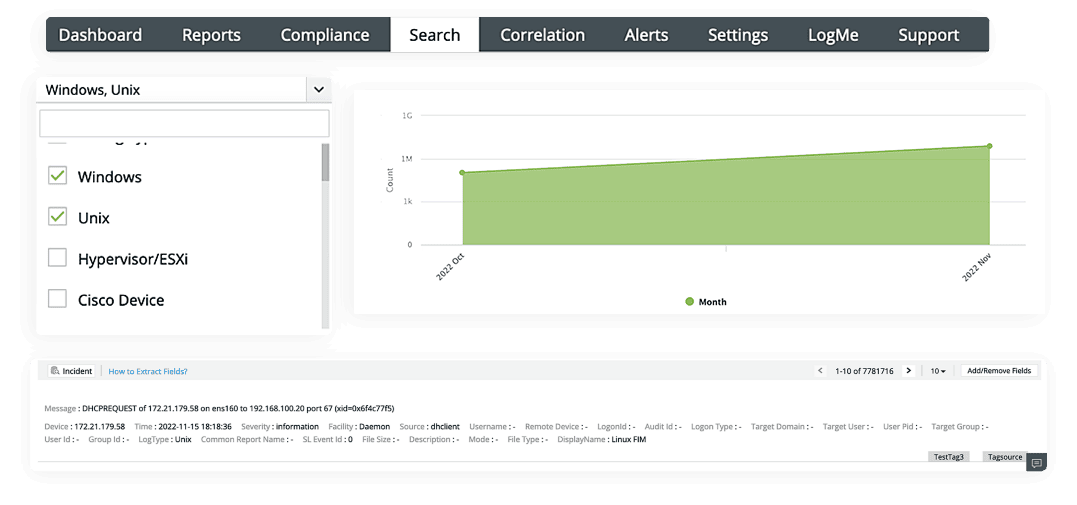
The GDPR requires organizations to document and report data breaches to the relevant authorities and affected individuals within 72 hours of discovering a breach. Log forensic analysis can help organizations meet this requirement by providing detailed information about the incident, including when it occurred, what data was affected, and how it was accessed or exfiltrated.
Conduct log forensic analysis with the help of the solution's advanced search capability and high-speed log processing. Drill down through raw logs related to any security incident with a wide range of search queries like wildcard, phrase, Boolean, and grouped searches. You can also search using the event IDs, severity, source, username, and IP address to detect unauthorized access, unusual logons, applications errors, and more.
Become GDPR-compliance-ready with EventLog Analyzer
| GDPR requirements | Reports by EventLog Analyzer |
|---|---|
| Article 5, 1(b) "Collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes; further processing for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes shall, in accordance with Article 89(1), not be considered to be incompatible with the initial purposes (‘purpose limitation’)" |
|
| Article 5, 1(d) "Accurate and, where necessary, kept up to date; every reasonable step must be taken to ensure that personal data that are inaccurate, having regard to the purposes for which they are processed, are erased or rectified without delay (‘accuracy’)" |
|
| Article 5, 1(f) "Processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures (‘integrity and confidentiality’)" |
|
| Article 32, 1(b) "The ability to ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services" |
|
| Article 32, 1(d) "A process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing" |
|
| Article 32, 2 "In assessing the appropriate level of security account shall be taken in particular of the risks that are presented by processing, in particular from accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to personal data transmitted, stored or otherwise processed" |
|
What else does EventLog Analyzer offer?
Simple configuration
Automatically discover and collect log sources from your network and spot malicious activities by conducting in-depth log analysis.
Learn moreNetwork log monitoring
EventLog Analyzer supports every network entity, including perimeter devices, network devices, databases, applications, web servers, and vulnerability scanners, in one console.
Learn morePrivileged user monitoring
Detect privilege abuse by keeping track of users who have access to critical business information.
Learn moreThreat intelligence
Receive prompt alerts when globally blocklisted IPs and URLs interact with your network.
Learn moreFrequently asked questions
The GDPR is a European data privacy law that provides EU citizens more control over their personal data and ensures organizations handle personal data responsibly. Every organization that does business in the EU must abide by the GDPR. According to the law, an individual can request companies to delete or stop processing their personal data at any time.
The three major concerns that the GDPR addresses are:
- Ensuring personal data is processed in a lawful, fair, transparent manner.
- Obtaining consent from the data subject before processing pPII and collecting only the necessary data (data minimization).
- Ensuring organizations that are not based out of the EU yet do business in the EU and process EU citizens' personal data also adhere to the GDPR.
According to the EU's GDPR, the eight key principles that organizations must follow to ensure personal data protection are:
- Lawfulness, fairness, and transparency: The processing of personal data must be lawful, fair, and transparent.
- Purpose limitation: Personal data must be collected for specific, explicit, legitimate purposes and must not be further processed in a way that contradicts those purposes.
- Data minimization: Personal data must be adequate, relevant, and limited to what is necessary for the purposes for which it is processed.
- Accuracy: Personal data must be accurate and, where necessary, kept up to date.
- Storage limitation: Personal data must be kept in a form that allows data subjects to be identified for no longer than is required for the purposes for which the personal data is processed.
- Integrity and confidentiality: Personal data must be securely processed to prevent unauthorized processing, accidental loss, destruction, or damage.
- Responsibility: Organizations must be held accountable for GDPR principles and be able to demonstrate compliance.
- The right to be informed: Data subjects have the right to be informed about how their data is collected and used.











