- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Key features
Monitor Linux logs from a central console
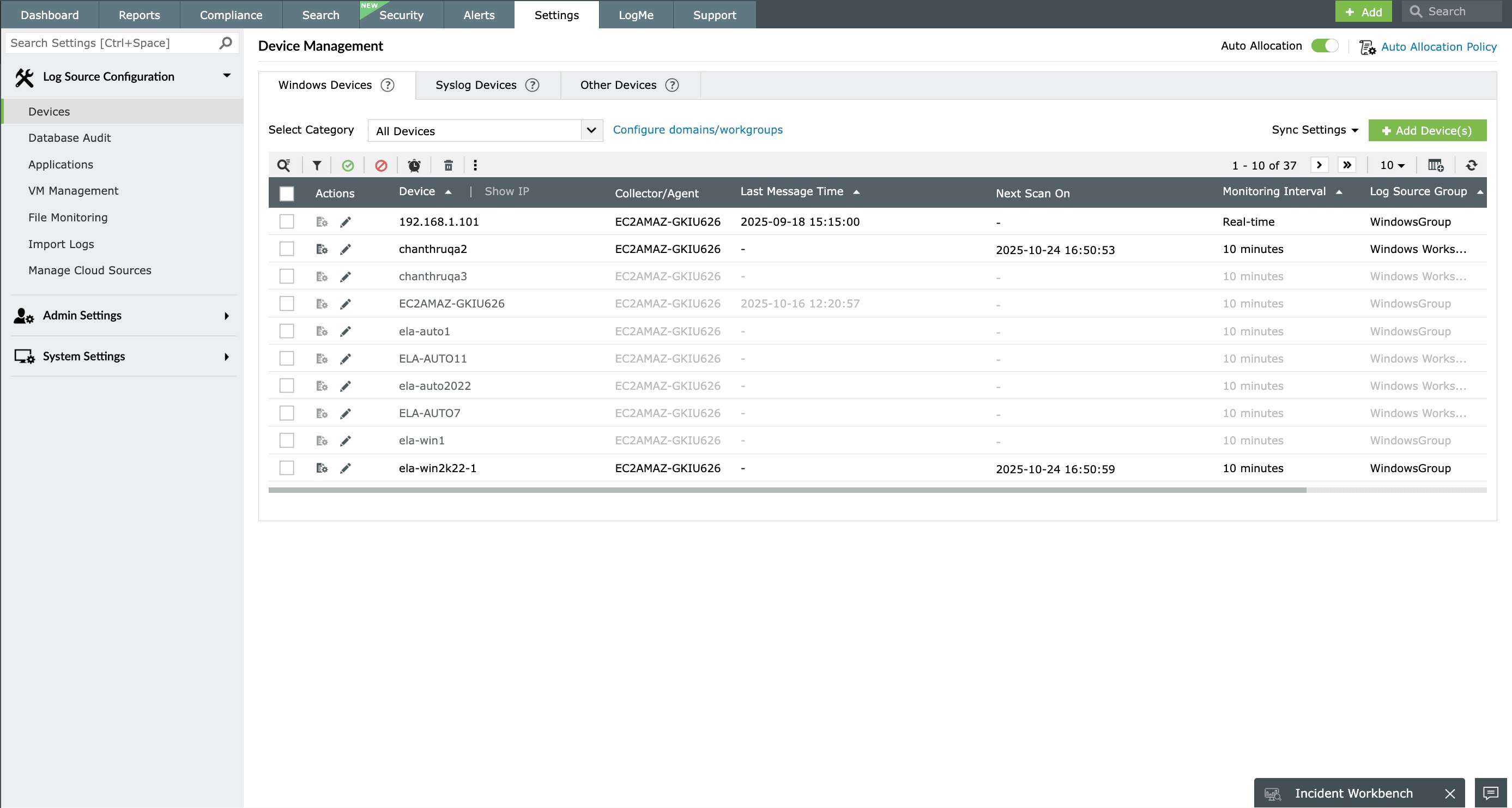
Collect logs from Linux devices as well as various other log sources, and monitor them from a single console to understand your network activities easily. EventLog Analyzer automates aggregation of logs from disparate sources, including Linux syslogs, Windows event logs, applications, network devices, databases, and servers. Real-time log monitoring gives you complete control over the security and management of your network.
Audit logon activities in Linux devices
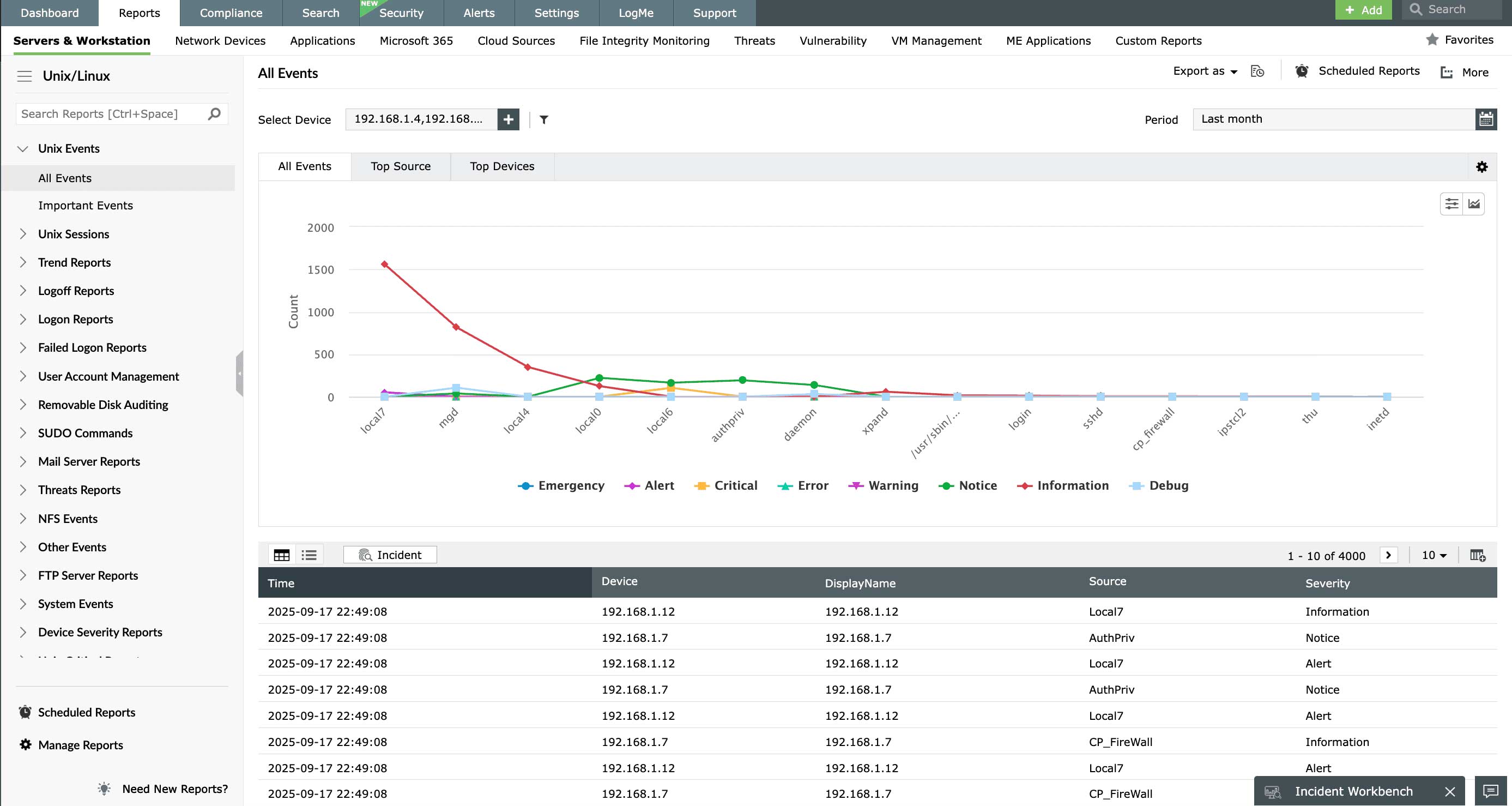
Stay aware of critical security events that happen in your network with the real-time auditing capabilities of EventLog Analyzer. The Linux log management tool tracks all Linux processes including system login and logout history, changes to user accounts and groups, sudo command executions, and actions and errors in FTP and Linux email servers to identify any potential security threats promptly.
Generate exhaustive reports on Linux system activities
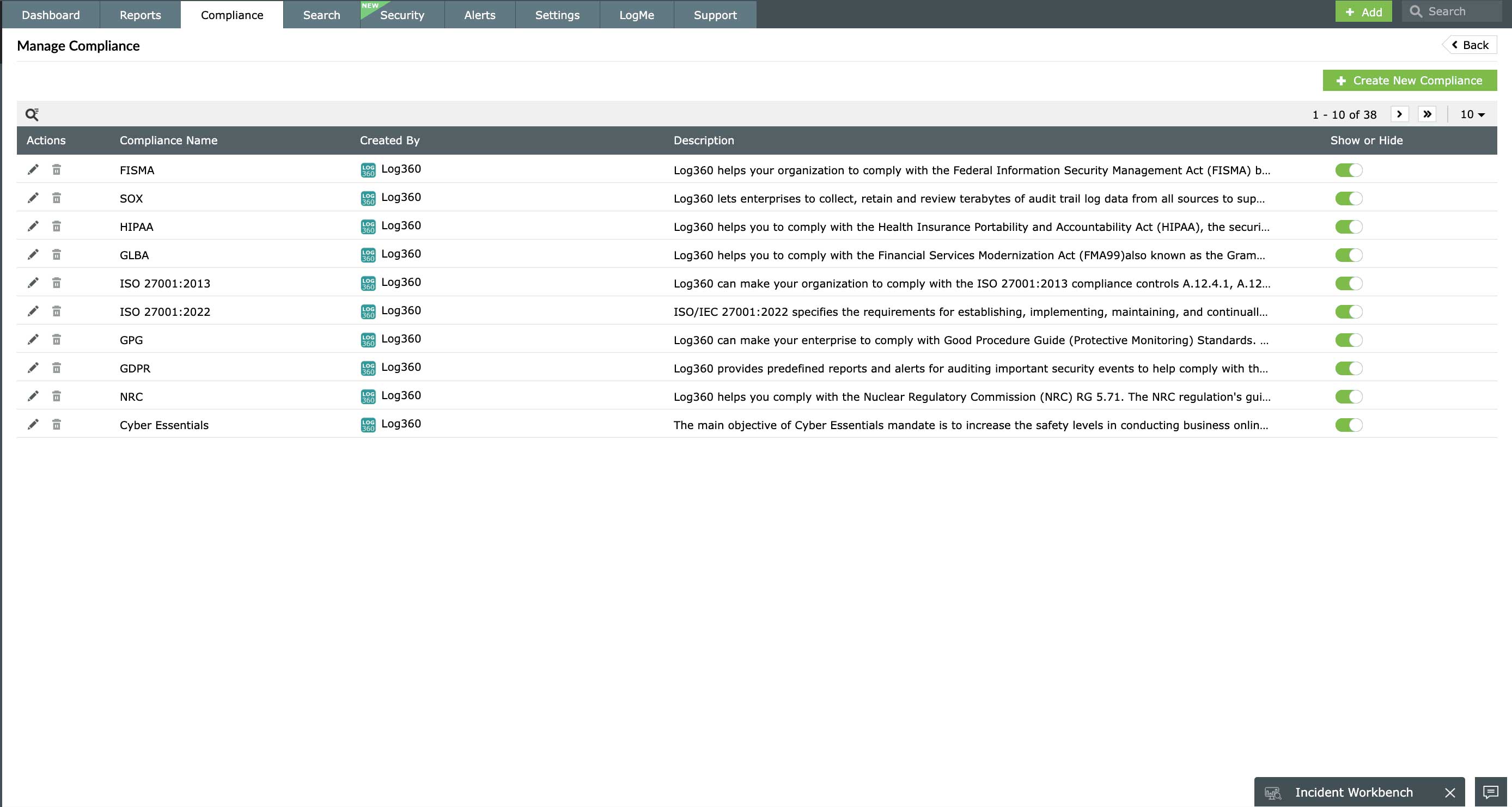
Meet IT compliance requirements for various regulatory mandates and internal audit policies of your organization with the report templates and custom report builder available in EventLog Analyzer. It contains over 100 predefined reports for Linux systems, including server error, server usage, and security reports. You can customize, schedule, and export these readily available reports to suit your requirements.
Track and analyze security events of interest with log correlation
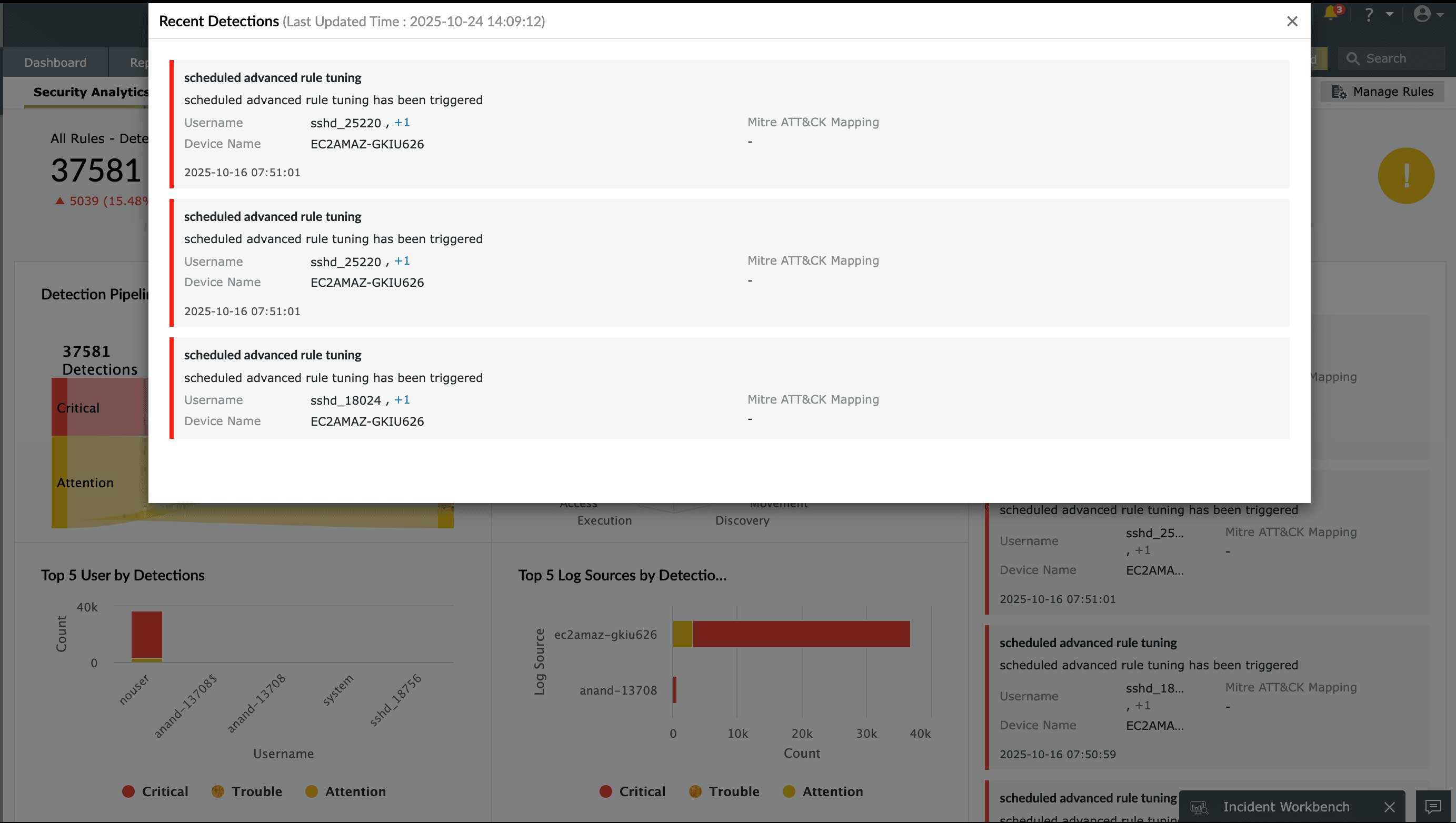
Correlate and analyze key events from across your Linux systems with EventLog Analyzer's event correlation engine. The solution contains over 30 pre-built correlation rules, designed to detect common cyberattacks like brute-force attacks, SQL injections, account lockouts, web server attacks, and more. It also has a custom drag-and-drop correlation builder to allow you to configure rules specific to your network. A powerful log search engine with basic and advanced search options also helps in swift location of malicious log entries to mitigate attacks.
Manage and resolve security incidents
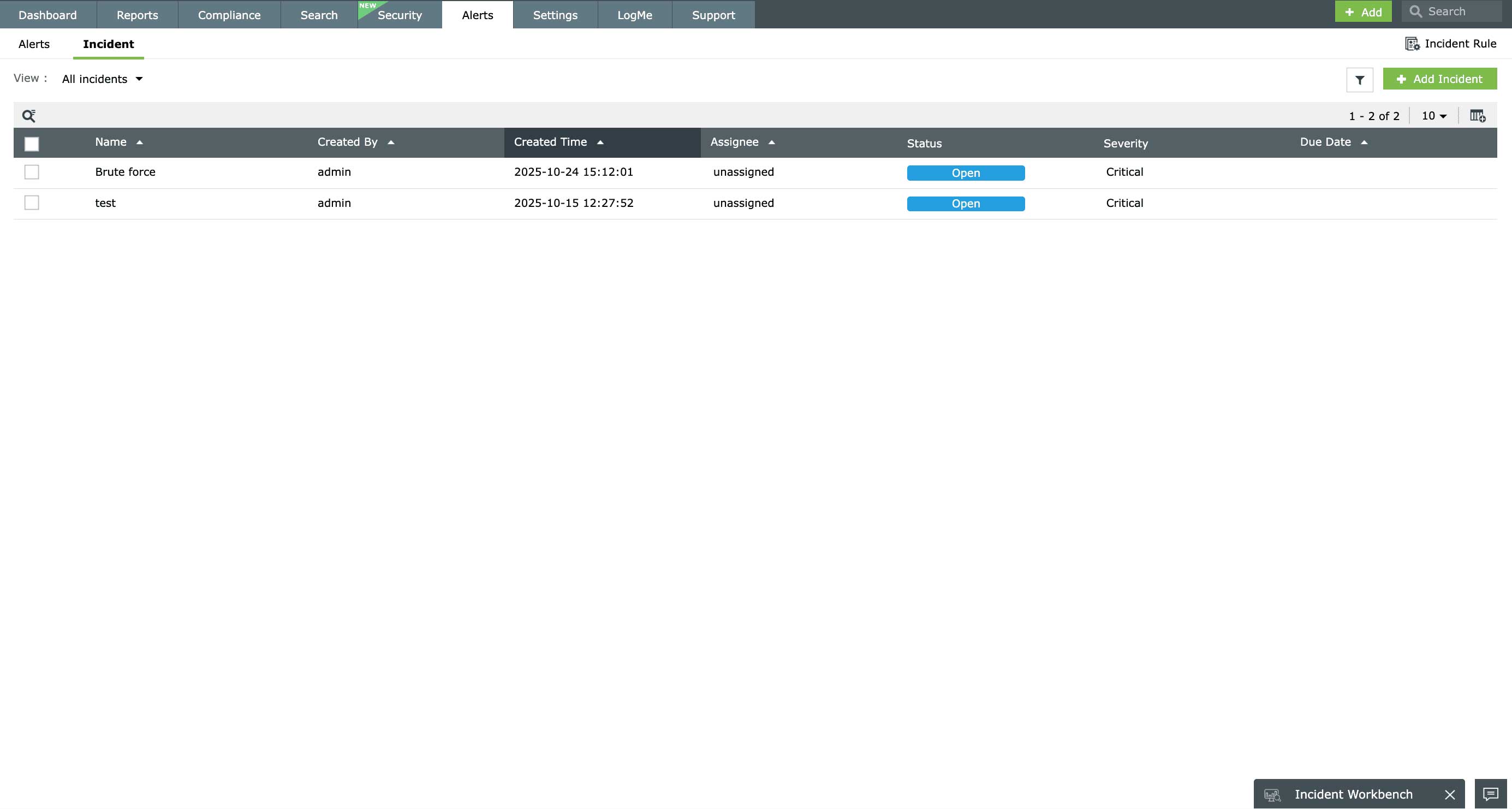
Ensure timely remediation with incident workflows that define the sequence of action for various types of security incidents that may occur in your Linux systems. EventLog Analyzer detects cybersecurity threats and events, analyzes them, classifies their severity level, and alerts the relevant team members. The solution also supports integration with external ticketing tools to expedite incident resolution.
Other features
SIEM
EventLog Analyzer offers log management, file integrity monitoring, and real-time event correlation capabilities in a single console that help meeting SIEM needs, combat security attacks, and prevent data breaches.
Windows event log monitoring
Analyze event log data to detect security events such as file/folder changes, registry changes, and more. Study DDoS, Flood, Syn, and Spoof attacks in detail with predefined reports.
Application log analysis
Analyze application log from IIS and Apache web servers, Oracle & MS SQL databases, DHCP Windows and Linux applications and more. Mitigate application security attacks with reports & real-time alerts.
Active Directory log monitoring
Monitor all types of log data from Active Directory infrastructure. Track failure incidents in real-time and build custom reports to monitor specific Active Directory events of your interest.
Privileged user monitoring
Monitor and track privileged user activities to meet PUMA requirements. Get out-of-the-box reports on critical activities such as logon failures, reason for logon failure, and more.
Log forensic analysis
Perform in-depth forensic analysis to backtrack attacks and identify the root cause of incidents. Save search queries as alert profile to mitigate future threats.
Need Features? Tell Us
If you want to see additional features implemented in EventLog Analyzer, we would love to hear. Click here to continue
Frequently asked questions
Linux operating system logs contain multiple log files with detailed information about the events that happen in the network. Every action performed on your server can be traced with the logs, including kernel events, login attempts, user actions, and more. You can find the logs on your Linux system under the /var/log directory. The directory will contain operating system, service, and application logs running on the system. Here are some of the important log files that should be monitored:
- /var/log/auth.log: Contains failed and successful authentication attempt details.
- /var/log/wtmp.log: Contains login, logout, and reboot information.
- /var/log/lastlog.log: Contains timestamped login details of each user on the system.
Real-time log audits and reports of network activities can help network administrators find anomalies in network events as soon as they happen. This will not only help you overcome operational and security bottlenecks but also effectively prevent cyberattacks in the network. Reporting can also help organizations meet regulatory compliance and internal audit requirements easily.
EventLog Analyzer, a comprehensive syslog management solution, monitors all logs to maintain a secure Linux environment. It tracks the following actions in Linux systems:
- Login and logoff activities: Tracks all logons and logoffs, including individual methods for logging on such as SU, SSH, and FTP logons.
- Failed login attempts: Tracks all the failed login attempts and reveals users with most failed attempts and consecutive authentication failures.
- User account management: Discovers and tracks all user accounts and groups that have been added, removed, or renamed.
- Removable disk auditing: Audits the use of removable devices on Linux systems.
- Sudo commands: Tracks all the successful, failed, and frequently used sudo commands.
- Linux mail server activities: Monitors email server usage patterns; trends associated with sent and received emails; and error messages like mailbox unavailable, insufficient storage, bad sequence of commands, and more.
- Linux system events: Tracks important system events, including stopping and restarting of syslog services, low disk space, and executions of the yum command.
- Other events: Tracks FTP activities, successful and denied network file system mounts, cron jobs, errors, security threats, and more.











