- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
Network devices generate various events that are logged locally, where they can be reviewed and analyzed by an administrator. However, if your network hosts a large number of devices, collecting event logs from each of these devices would be time-consuming and impractical.
Syslog, or System Logging Protocol, is a standard protocol that solves this issue by sending system logs or event messages to a central syslog server. This protocol is enabled on most network devices including routers, switches, and firewalls. Syslog is also available on Unix and Linux-based systems, and web servers like Apache.
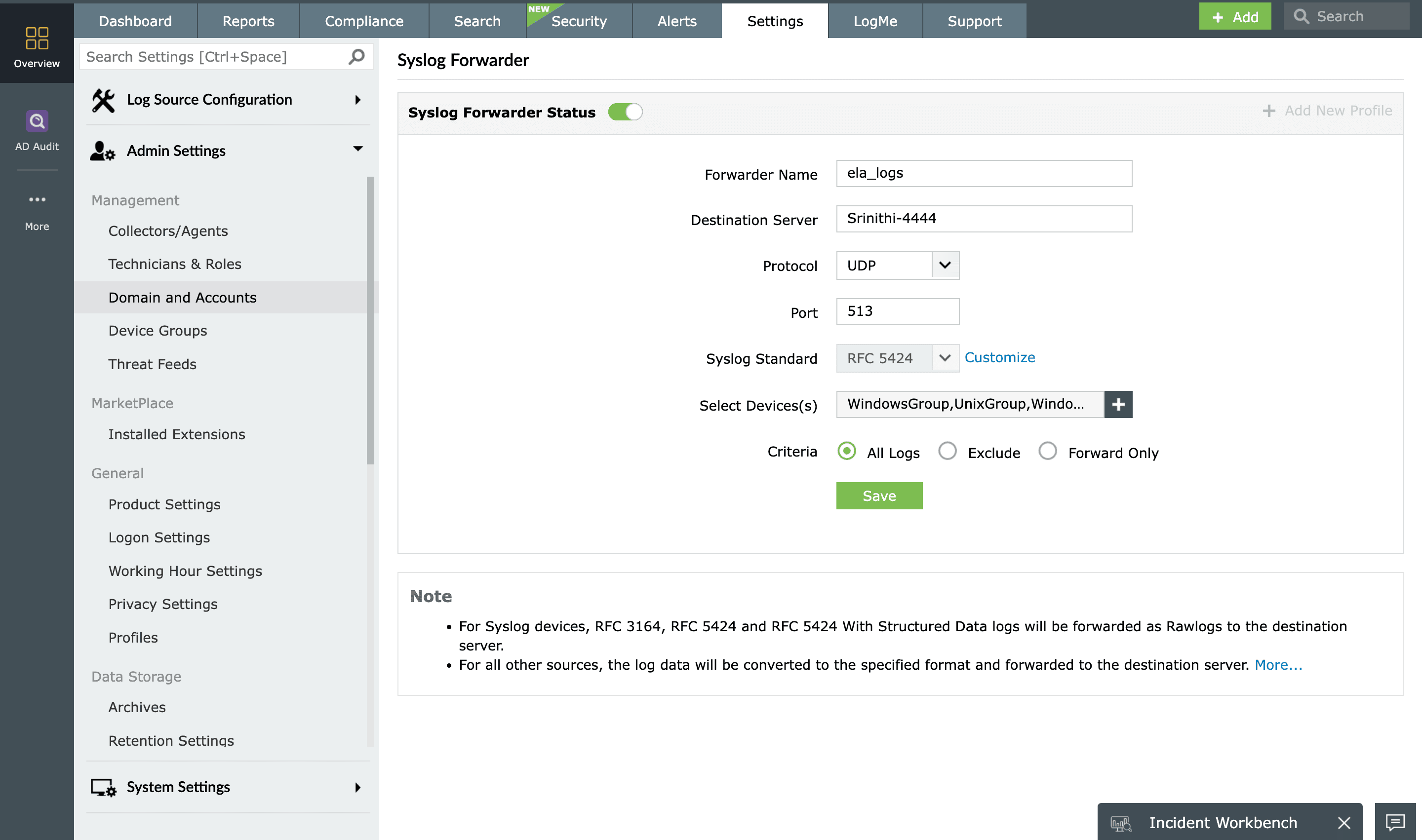
EventLog Analyzer acts as a syslog server and collects event messages from devices across your network. It's also capable of forwarding the collected logs to a third-party server or a security information and event management (SIEM) application.
How EventLog Analyzer's syslog forwarder works
EventLog Analyzer’s syslog forwarder is designed to receive syslogs and send the data to the appropriate system. EventLog Analyzer listens in on the designated User Datagram Protocol (UDP) port, which by default is port 513. On receiving the logs, the UDP forwarder in EventLog Analyzer forwards the information to the specified destination server. Logs from syslog devices are forwarded as raw logs, while logs from other event sources are converted to RFC3164 or RFC5424, and forwarded it to the desired destination host.
The biggest advantage of EventLog Analyzer is that it can function as both a syslog server and a forwarder.
The benefits of syslog forwarding
Syslog forwarding offers a way to ensure that critical events are logged and stored in a separate location from the original server. An attacker’s first move after compromising a system is to cover the tracks they left in the log, but these forwarded events will be out of their grasp. Replication of the collected logs in another server can be used as a backup if the original data is lost. The replicated data can also be used to cross-check if the original data has been tampered with.
Other features
SIEM
EventLog Analyzer offers log management, file integrity monitoring, and real-time event correlation capabilities in a single console that help meeting SIEM needs, combat security attacks, and prevent data breaches.
Windows event log monitoring
Analyze event log data to detect security events such as file/folder changes, registry changes, and more. Study DDoS, Flood, Syn, and Spoof attacks in detail with predefined reports.
Application log analysis
Analyze application log from IIS and Apache web servers, Oracle & MS SQL databases, DHCP Windows and Linux applications and more. Mitigate application security attacks with reports & real-time alerts.
Active Directory log monitoring
Monitor all types of log data from Active Directory infrastructure. Track failure incidents in real-time and build custom reports to monitor specific Active Directory events of your interest.
Privileged user monitoring
Monitor and track privileged user activities to meet PUMA requirements. Get out-of-the-box reports on critical activities such as logon failures, reason for logon failure, and more.
Log forensic analysis
Perform in-depth forensic analysis to backtrack attacks and identify the root cause of incidents. Save search queries as alert profile to mitigate future threats.
Need Features? Tell Us
If you want to see additional features implemented in EventLog Analyzer, we would love to hear. Click here to continue











