- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
The network devices used in every organization generate a lot of log data, including syslog messages. It is vital to monitor them to identify any anomalies and troubleshoot issues. A syslog viewer like EventLog Analyzer can help you sort through this data, bring it together in an intuitive dashboard, and conduct real-time security audits to keep your network safe.
Here's how Here's how EventLog Analyzer simplifies log monitoring as a syslog viewer
Central management and analysis of logs
Hundreds of logs are generated every minute, and it is difficult to keep track of everything all at once. With EventLog Analyzer, you can manage and analyze all your syslog data. The solution supports logs generated from databases, applications, network devices, Windows systems, Unix and Linux systems, and more from a single intuitive dashboard.

Real-time log viewing
With a real-time syslog viewer tool, you can analyzelogs as they are generated. This means that you can quickly identify and respond to potential security threats, system failures, and other critical events as they occur. This can help you to minimize downtime, reduce the impact of security incidents, and ensure that your systems are operating smoothly and efficiently.
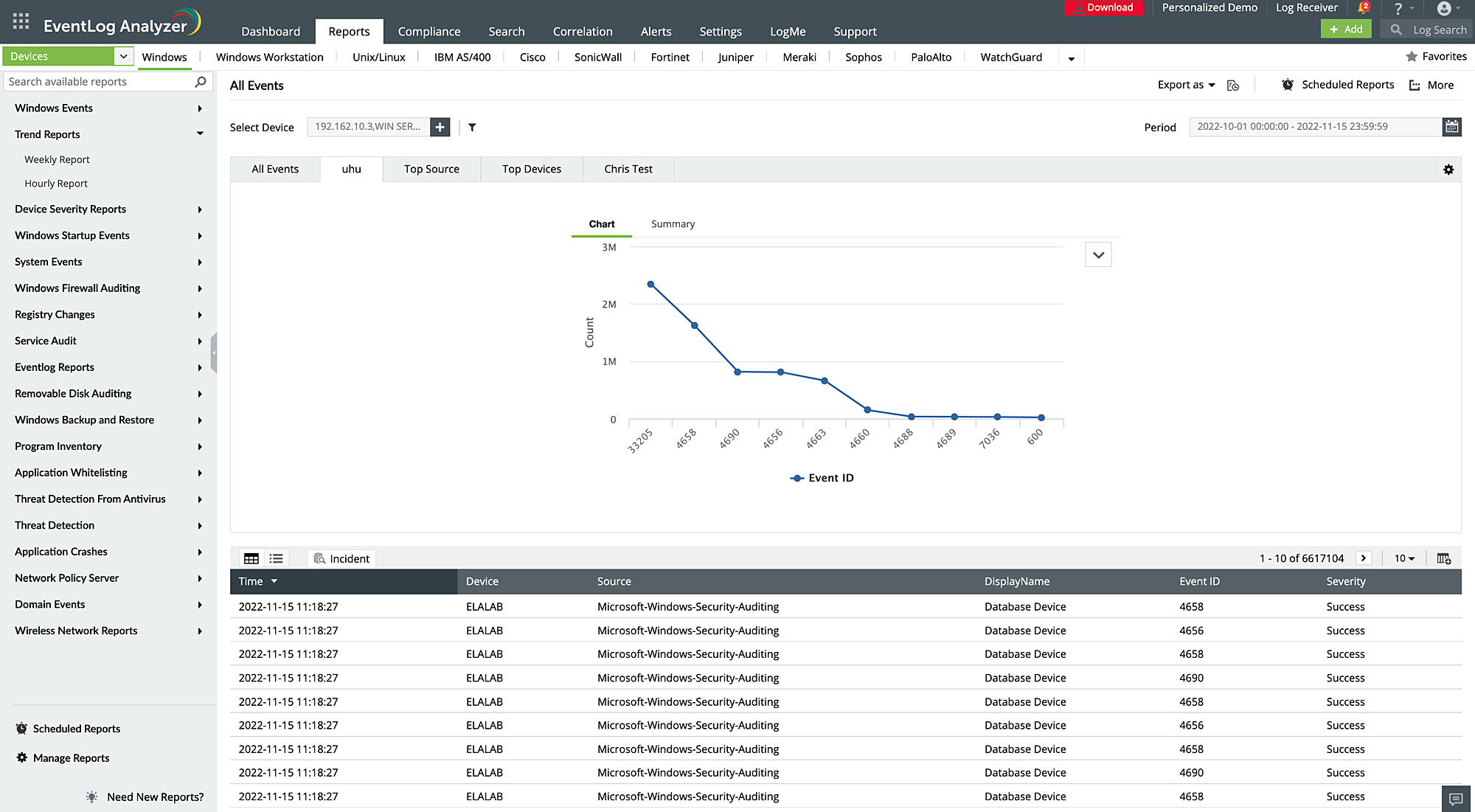
Search and filter capabilities
EventLog Analyzer allows you to quickly and easily locate specific logs and events based on a wide range of criteria, including date and time, source, event type, and severity. The solution offers several types of searches to facilitate easy searching, like keyword search, Boolean search, field search, and wildcard search. This makes it easy to find the information you need, even in large and complex log data sets.

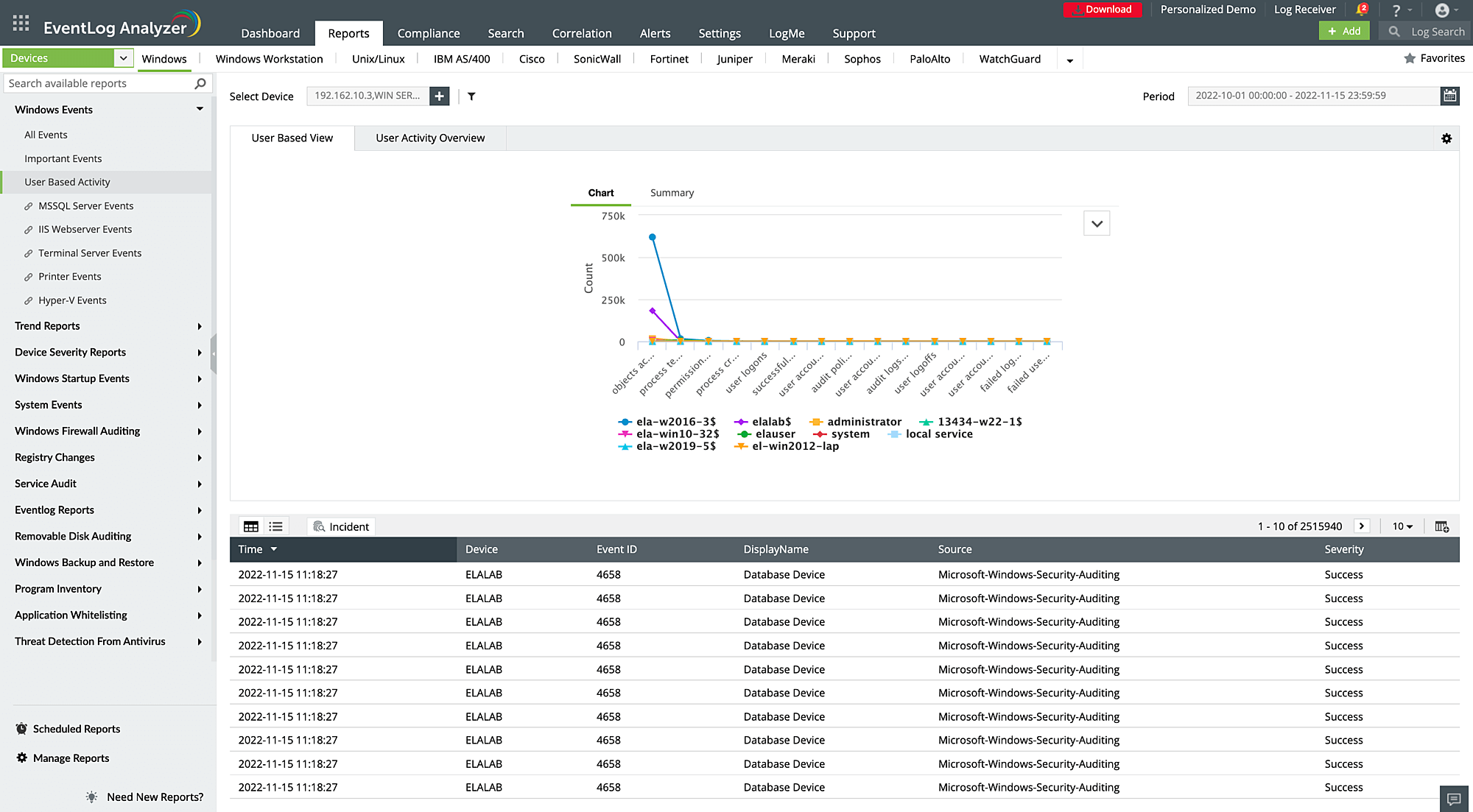
User activity monitoring
User activity monitoring allows you to control who can view and analyze confidential data, and ensures that sensitive information is only accessible to authorized individuals. This is especially important in large organizations where log data may contain confidential information or sensitive details about system configurations and security protocols.
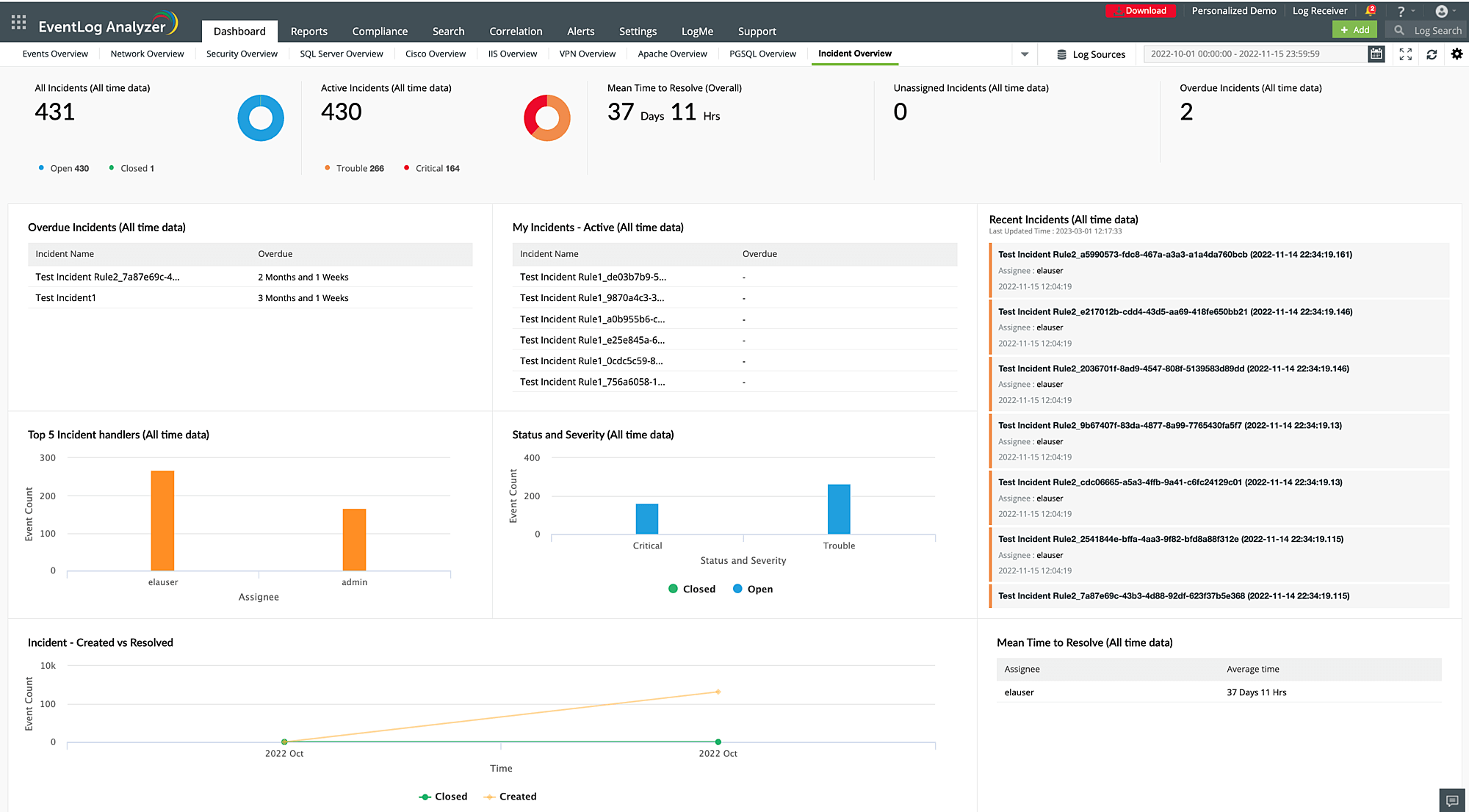
Automated incident and response management
EventLog Analyzer helps organizations to respond quickly and effectively to potential security threats, reducing the impact of incidents and minimizing downtime. You'll be able to identify the exact user and the system from where the event was generated to be able to fix it immediately. Automated incident and response management includes features such as real-time event monitoring, alert generation, and automated response actions.
Related solutions offered by EventLog Analyzer
Advanced threat intelligence
Detect and respond to potential security threats proactively with threat intelligence. EventLog Analyzer also has threat feeds and allows you to monitor for specific threat indicators.
Event log correlation
EventLog Analyzer's correlation engine analyzes the sequences of syslogs to identify possible incoming attacks and alerts you about the threat.
Application auditing
Look out for any critical changes or data theft, and keep track of disruptions in your applications, including databases and web servers, with EventLog Analyzer.
Incident response
Automate responses to known incidents with workflow profiles. Link alert profiles or correlation rules with workflows to automate threat mitigation processes.
Forensic analysis
Conduct extensive forensics and perform root cause analysis or post-breach investigations with intuitive search options, such as click-based, range-based, and Boolean-based.
5 reasons to choose EventLog Analyzer as your syslog viewer tool
1. Simplified syslog collection
With EventLog Analyzer, you can collect syslog data from routers, switches, firewalls, servers, and other network devices and manage it all from a single console. The solution also supports other log sources. This simplifies the process of collecting, analyzing, and managing log data, allowing organizations to gain a more complete and accurate view of their network activity.
2. A centralized database and security analytics
The syslog viewer's dashboard provides a centralized view of log data, allowing you to assess the status of your systems quickly and identify areas of concern. The security analytical capabilities use sophisticated algorithms to analyze log data and detect potential threats, reduce the risk of security incidents, and improve overall security.
3. Canned reports
With canned reports, you can quickly access the information you need without having to manually analyze raw log data. By automating the process of extracting and presenting key information, EventLog Analyzer's canned syslog reports help organizations to improve the efficiency and effectiveness of their log analysis.
4. Easier auditing
EventLog Analyzer helps make auditing easier by monitoring various actions such as logon and logoff events, SUDO commands, user account management, device severity reports, and other activities to detect suspicious behavior. The solution provides real-time alerts and notifications based on preconfigured thresholds, enabling organizations to quickly identify potential security incidents.
5. Log correlation
EventLog Analyzer can detect patterns and anomalies that may indicate a security breach or other type of incident. This information can then be used to respond to the incident and prevent similar incidents from happening in the future. By leveraging the 30+ built-in correlation rules, organizations can reduce their response times and increase their overall security posture by proactively detecting and mitigating potential threats.
Frequently asked questions
Syslogs contain valuable details about systems and networks. Analyzing them allows you to understand in-depth details about how they work and to spot any anomalies. A syslog viewer collects and displays the log data on intuitive dashboards for users.
A syslog viewer allows you to view in-depth details about your systems and network. It allows you to make decisions with quick turnaround times and prevents any security incident from turning into a full-blown attack.
An effective syslog viewer like EventLog Analyzer allows you to send instant alerts about any suspicious activities and generate reports with ease.