- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
The Linux operating system generates logs that are crucial for ensuring smooth security and network operations. Collect, analyze, search, correlate, and generate reports on Ubuntu systems with a simple yet efficient Ubuntu log management tool: EventLog Analyzer.
Here's how EventLog Analyzer makes Ubuntu log monitoring seamless and hassle-free.
Automated syslog collection
EventLog Analyzer can automatically discover and collect logs from Ubuntu systems and other Unix and Linux systems. Our solution discovers the network devices based on the IP and Classless Inter-Domain Routing range and provides an option for users to configure the Ubuntu systems to send their logs to the built-in syslog server.
The built-in syslog server listens to and analyzes syslog messages from different sources, such as Ubuntu SSH logs, Ubuntu Apache logs, and Ubuntu error logs, from multiple network devices using UDP. This helps minimize system downtime and improve the security policies of enterprises.
Logon and logoff monitoring
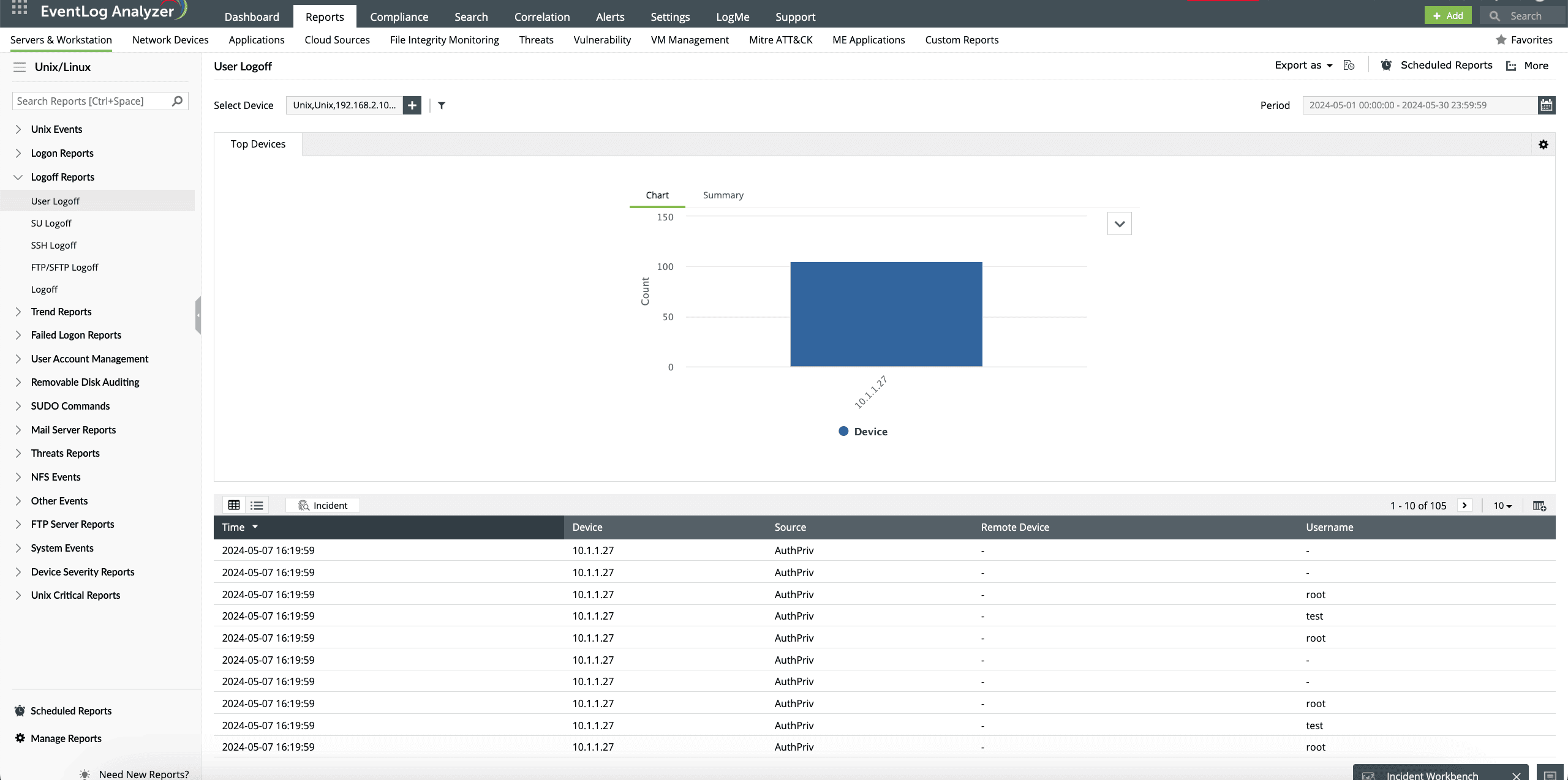
With EventLog Analyzer, you can monitor Ubuntu users' activity, such as logons and logoffs, and identify patterns for both successful and failed logon attempts. Get in-depth visibility into the types of logons, including SSH, switch user (SU), and FTP, and logons via remote devices.
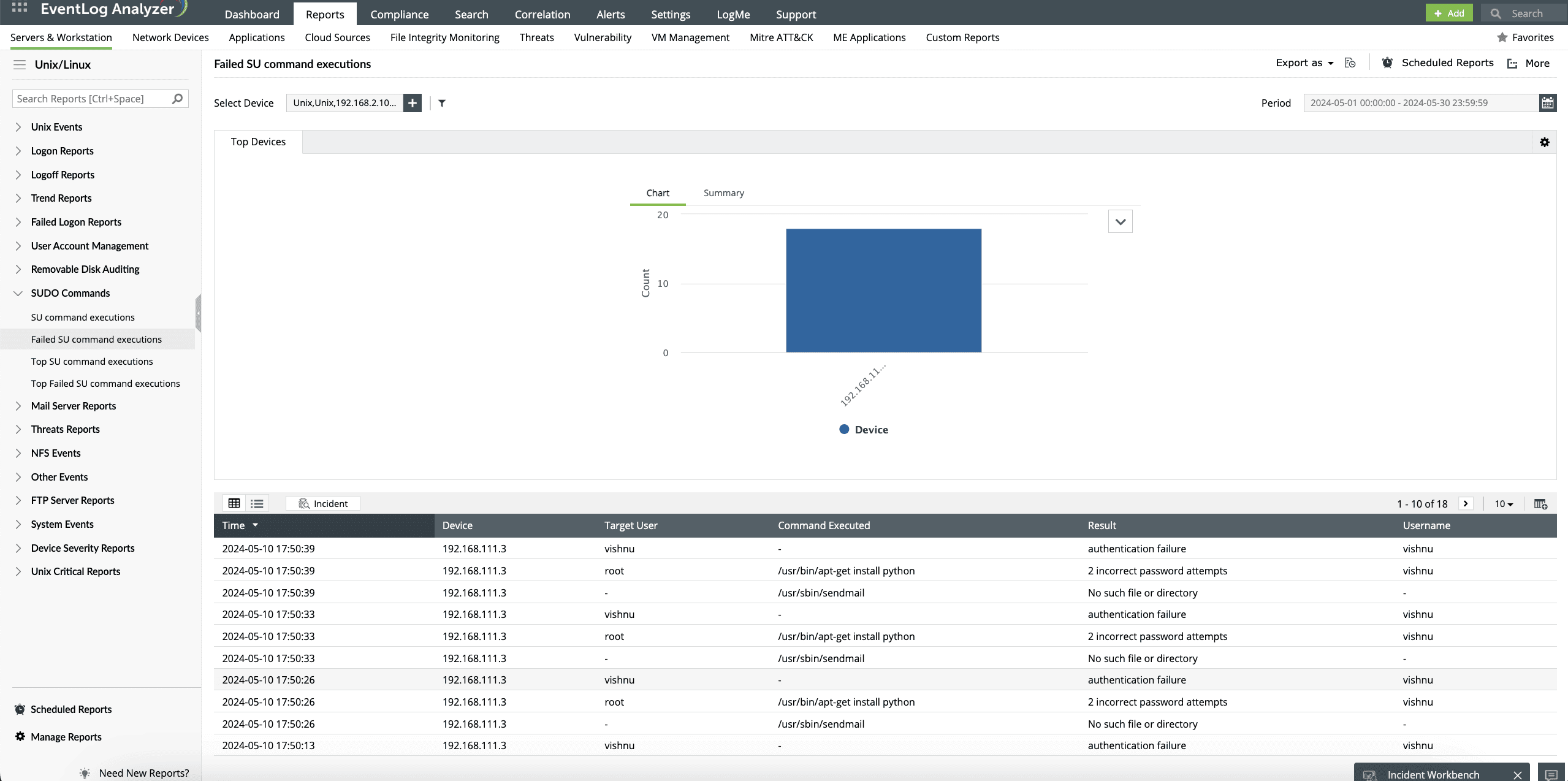
sudo command tracking
EventLog Analyzer allows you to track all sudo command activities. The execution details of critical sudo commands, such as changing interactive shell, running a command through a different user, and running a Linux command with sudo access, can be monitored.
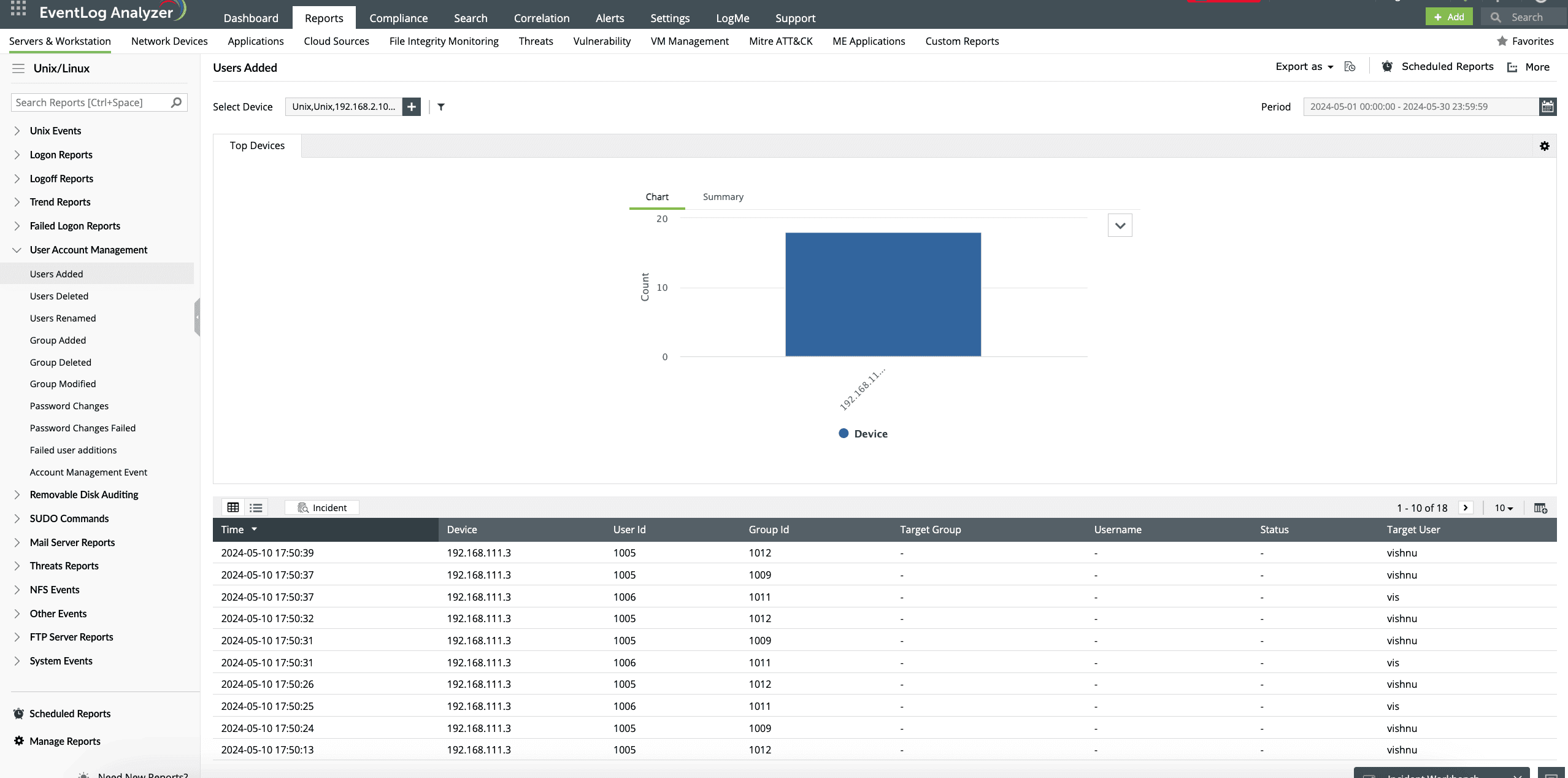
User account management
With EventLog Analyzer, easily manage your Ubuntu user accounts. Keep track of all the users added, deleted, and renamed with predefined analytical reports. With security analytics, track and audit Ubuntu user group changes and password changes for Ubuntu systems.
Critical reports and threat reports
Secure your Ubuntu systems by getting greater visibility into the threats they face. Get reports based on risk level, including reports on risk trends, top risks by hosts, remote hosts, and the risk overview.
Related solutions offered by EventLog Analyzer
Log management
Get a complete picture of your network by centralizing log collection, correlation, analysis, and storage.
Event log correlation
EventLog Analyzer's correlation engine analyzes the sequences of Ubuntu log files and the devices they originated from, then alerts you about possible incoming attacks.
Advanced threat analytics
Get more insights into the malicious sources targeting your Ubuntu systems with EventLog Analyzer's built-in global threat intelligence database and its Advanced Threat Analytics add-on.
IT compliance management
Comply with regulations like the PCI DSS, FISMA, the GLBA, and SOX with built-in, predefined audit reports and compliance violation alerts.
Incident response
Automate responses to known incidents with workflow profiles. Associate workflows with alert profiles or correlation rules to mitigate threats automatically.
Forensic analysis
Conduct root cause analysis or post-breach investigations with intuitive search options, such as click-based, range-based, and Boolean-based.
5 reasons to choose EventLog Analyzer as your Ubuntu syslog monitoring tool
1. Correlation of Ubuntu logs with other network logs
EventLog Analyzer allows you to correlate Ubuntu logs with other network logs, proactively search for threats, and secure your system instantly. EventLog Analyzer also comes with over 50 out-of-the-box correlation rules that you can customize based on your preferences.
2. Automated workflows for Ubuntu systems
EventLog Analyzer automatically executes workflows after a security incident, enabling you to stay ahead of the curve, save precious time, and mitigate any potential damage.
3. Augmented threat intelligence to spot threats
With its built-in intuitive threat intelligence module, EventLog Analyzer can recognize over 600 million malicious IPs. Combined with its built-in global threat database, you can detect critical events that affect your network and block them instantly.
4. Secured archival of Ubuntu logs
EventLog Analyzer securely archives all Ubuntu logs in your system. These logs are invaluable when conducting forensic analysis and inspecting performance and other usage statistics.
5. Compliance management
EventLog Analyzer's hassle-free report creation helps you comply with regulations like the PCI DSS, HIPAA, and the GDPR. EventLog Analyzer also allows you to perform extensive auditing and obtain crucial information via intuitive dashboards and alerts.
Frequently asked questions
Ubuntu is the operating system for Linux and Unix devices. Ubuntu systems generate logs for every activity that happens, including user logons, logoffs, process starts, and permission changes. Monitoring these activities happening in Ubuntu systems by analyzing their logs is known as Ubuntu system log monitoring.
With log monitoring, the system will be able to recognize patterns of regular activities and filter out any abnormal activities that could signify a potential attack.
An Ubuntu log monitoring tool will help you convert activities hidden in the logs into useful, actionable information. A log monitoring tool like EventLog Analyzer also has real-time alerting; a powerful correlation engine; an Ubuntu log viewer; and built-in, predefined reports.











