Las campañas de certificación de acceso son un componente crítico de una solución robusta de gobernanza y administración de identidades (IGA). Estas soluciones garantizan que los derechos de acceso se revisen periódicamente y que los usuarios solo tengan los privilegios que necesitan para desempeñar sus funciones.
Estas campañas ayudan a las organizaciones a automatizar la gestión de acceso de los usuarios, mitigar los ataques relacionados con el acceso y demostrar el cumplimiento de las regulaciones de TI como el GDPR, PCI DSS, HIPAA y más.
La recertificación de acceso, desempeña un rol clave en el mantenimiento de la postura de seguridad y cumplimiento de una organización. Al revisar y revalidar periódicamente los privilegios de acceso de los usuarios, las organizaciones pueden garantizar que los empleados, contratistas o terceros solo conserven el acceso a los sistemas y datos necesarios para sus funciones.
La incorporación de la recertificación en las campañas de certificación de acceso permite adoptar un enfoque proactivo en la gestión de accesos, fortaleciendo así el marco general de seguridad de la organización.
El cumplimiento de las regulaciones, como el GDPR, HIPAA, PCI DSS y más, es esencial en el mundo actual basado en datos, donde las organizaciones dependen y generan datos en gran medida. El incumplimiento de estas regulaciones puede llevar a repercusiones legales como demandas y sanciones, así como aumentar el riesgo de violaciones de datos y ciberataques.
Prevenir el acceso no autorizado y proteger la información confidencial es un requisito vital establecido por los mandatos de TI, y las organizaciones deben establecer medidas y políticas que garanticen que las personas autorizadas tengan acceso a los recursos adecuados para garantizar la seguridad de sus redes. La recertificación de acceso ayuda a reforzar estas políticas, garantizando que solo las personas adecuadas tengan acceso a datos y sistemas sensibles.
La gestión de permisos de acceso para los empleados puede parecer sencilla, pero en realidad es una tarea desafiante. Es propensa a errores, consume mucho tiempo y puede aumentar los gastos administrativos. Por eso es esencial invertir en una solución confiable que no solo ayude a automatizar todo el proceso, sino que también facilite la auditoría a través de la certificación y la recertificación de acceso.
ADManager Plus es una solución de IGA que ofrece funciones de certificación de acceso a las organizaciones para agilizar sus métodos de control de acceso. Las campañas de certificación de acceso se pueden utilizar para asignar, recertificar y revocar los derechos de acceso de los usuarios e implementar el principio de mínimos privilegios, segregación de tareas y control de acceso basado en roles. Las organizaciones pueden implementar estos principios para frustrar los ataques de abuso de privilegios y salvaguardar sus redes.
Con las campañas de certificación de acceso en ADManager Plus, los derechos de acceso de los usuarios, como los permisos de NTFS o las funciones y aplicaciones de Microsoft 365, se pueden validar de forma masiva, lo que resulta en una mayor eficiencia operativa. Estos esfuerzos de certificación de acceso garantizan el cumplimiento continuo de los requisitos de auditoría interna y externa.
ADManager Plus también mejora la gestión del ciclo de vida mediante la automatización del aprovisionamiento de usuarios, la gestión de contraseñas y gestión de grupos, y proporcionando aprobaciones de los flujos de trabajo personalizados a varios niveles y notificaciones en tiempo real.
Un actor clave en el proceso que audita los derechos de acceso de los usuarios y toma medidas al respecto. Un certificador puede ser un administrador, técnico de la mesa de ayuda, gestor de un usuario, o el rol puede personalizarse según las necesidades de una organización.
Campañas de auditoría con políticas y criterios que se pueden utilizar para evaluar los derechos de acceso de los usuarios. Estas campañas se pueden programar y priorizar en función de los derechos que se van a revisar. La recertificación de acceso es parte de este esfuerzo continuo para garantizar un acceso adecuado.
Membresías de grupos de usuarios y permisos de acceso que el certificador validará.
Reglas que se pueden configurar para asignar certificadores dinámicamente.
When reviewing access during certification campaigns, ADManager Plus goes a step further by offering smart access recommendations. These suggestions are based on peer comparison and behavioral baselines, helping reviewers quickly identify unusual or excessive permissions. With this, reviewers can:
ADManager Plus also offers a risk exposure management feature that can be used alongside access certification to strengthen an organization's overall AD security. This capability gives a clear view of an organization's AD threat landscape by helping admins visualize potential attack paths in their AD environment.
Here's how using risk exposure management and access certification together can enhance an organization's security posture:
This ensures that access reviews are not just routine checks, but strategic, risk-driven validations that strengthen overall security.
Ensuring proper access controls isn't just good practice—it's a requirement. Here's how leading compliance standards emphasize robust access management:
| Compliance | Section/Article | Description |
| HIPAA | 45 CFR 164.308(a)(3)(i) |
Implement policies and procedures to ensure that all members of its workforce have appropriate access to electronic protected health information |
| 45 CFR 164.308(a)(3)(ii)(B) |
Implement procedures to determine that the access of a workforce member to electronic protected health information is appropriate | |
| 45 CFR 164.308(a)(4)(ii)(C) |
Implement policies and procedures that establish, document, review, and modify a user's right of access to workstations, transactions, programs, or processes | |
| PCI DSS v4.0 | Requirement 7.2.3 | Required privileges are approved by authorized personnel |
| Requirement 7.2.4 | All user accounts and related access privileges are reviewed at least once every six months to ensure accounts and access remain appropriate based on job function | |
| Requirement 7.2.5.1 | All access by application and system accounts is reviewed periodically based on targeted risk analysis frequency | |
| SOX | Section 302(a)(4)(A) | Signing officers are responsible for establishing and maintaining internal controls |
| Section 404 | Management assessment of internal controls over financial reporting | |
| ISO 27001:2022 | Control 5.15 | Rules to control physical and logical access to information and other associated assets shall be established and implemented based on business and information security requirements |
| Control 5.18 | Access rights to information and other associated assets shall be provisioned, reviewed, modified, and removed in accordance with established policies | |
| Control 8.3 | Access to information and other associated assets shall be restricted in accordance with established access control policies | |
| GDPR | Article 32(1)(b) | Implement appropriate technical and organizational measures to ensure ongoing confidentiality, integrity, availability, and resilience of processing systems |
| Article 25 | Data protection by design and by default: Implement appropriate technical and organizational measures to ensure data protection principles are integrated into processing | |
| NIST CSF 2.0 | PR.AC-1 | Identity and access management processes and procedures are established and implemented |
| PR.AC-4 | Access permissions and authorizations are managed, incorporating the principles of least privilege and separation of duties | |
| NIST SP 800-53 | AC-2 | Account Management: An organization manages system accounts, including establishing conditions for group membership, identifying authorized users, and reviewing accounts |
| COBIT 2019 | APO13.01 | Establish and maintain an information security management system |
| DSS05.04 | Manage identity and access rights: Ensure appropriate access to systems and data through proper identity and access management | |
| FISMA | Control AC-2 | Account management: An organization manages information system accounts, including authorizing access and reviewing accounts |
| Control AC-6 | Least privilege: An organization employs the principle of least privilege, allowing only authorized access necessary to accomplish assigned tasks | |
| NERP CIP | CIP-004-6 R4 | Personnel access authorization: Verify that individuals have authorization for access to designated storage locations of BES Cyber System Information |
| CIP-004-6 R5 | Personnel access authorization: Review access permissions to physical and electronic access rights to applicable systems at least once every 15 months | |
| FFIEC | Information Security Booklet | Access rights administration: Financial institutions should implement processes to grant, review, and revoke user access rights |
| COSO | Internal Control Framework | Control Activities: Policies and procedures that help ensure management directives are carried out |
ADManager Plus Access Certification Campaigns provide a comprehensive solution for meeting the diverse compliance mandates outlined above through systematic access governance and automated review processes. These campaigns directly address regulatory requirements by enabling periodic validation of user access rights, ensuring that employees maintain only the permissions necessary for their current job functions while providing the documentation and oversight required by auditors and regulatory bodies.
The campaigns support compliance-mandated review frequencies across different standards—from PCI DSS's six-month cycles to NERC CIP's 15-month requirements—through flexible scheduling that can be configured to meet specific regulatory timelines. Designated approvers and reviewers validate access appropriateness, ensuring that required privileges are approved by authorized personnel as mandated by frameworks like PCI DSS and HIPAA. This systematic approach supports the principle of least privilege by identifying and removing excessive access rights during regular review cycles, directly addressing requirements from NIST CSF, FISMA, and ISO 27001.
For healthcare organizations subject to HIPAA, the campaigns ensure that workforce access to electronic protected health information is continuously validated and appropriately restricted. Financial institutions benefit from structured access rights administration that meets FFIEC guidelines and supports SOX internal control requirements with documented approval workflows and management oversight. Critical infrastructure operators can maintain compliance with NERC CIP standards through verified access authorization processes and mandated review cycles for personnel accessing sensitive energy systems.
The solution generates comprehensive audit trails and documentation that support compliance assessments across all frameworks, from SOX Section 404 internal control evaluations to ISO 27001 certification audits. Risk-based scheduling capabilities align with targeted risk analysis requirements found in PCI DSS and COBIT 2019, while management acknowledgment workflows ensure executive oversight of access decisions as required by multiple compliance standards.
By automating these traditionally manual processes, Access Certification Campaigns reduce compliance burden while strengthening security posture, enabling organizations to demonstrate regulatory adherence through systematic access governance, documented review processes, and comprehensive audit-ready reporting across multiple compliance frameworks simultaneously.
Periodic validation of user access rights:
Compliance-mandated review frequencies:
Authorized personnel validation:
Management oversight and documentation:
Healthcare organizations (HIPAA):
Financial institutions (SOX, FFIEC, PCI DSS):
Critical infrastructure (NERC CIP):
Federal agencies (FISMA, NIST):
Reduce the risk of unauthorized access by identifying and removing users' inappropriate access rights through access certification.
Comply with mandates and organizational policies by maintaining an auditable record of access reviews, including access recertification and changes.
Periodically reviewing users' access rights can help detect and revoke unnecessary privileges and keep malicious insiders at bay.
Reviewing and revoking users' access to enterprise resources and group memberships helps reduce license and subscription costs.
Regularly review access permissions through access recertification to avoid the accumulation of privileges.
Streamline access management processes by running automated campaigns, including access recertification, to identify and revoke access for over-privileged accounts.
Make quicker, more informed certification decisions and simplify reviews with access recommendations.
Run a customized certification campaign to manage the privileges of accounts with access to sensitive information and revoke privileges as and when needed.
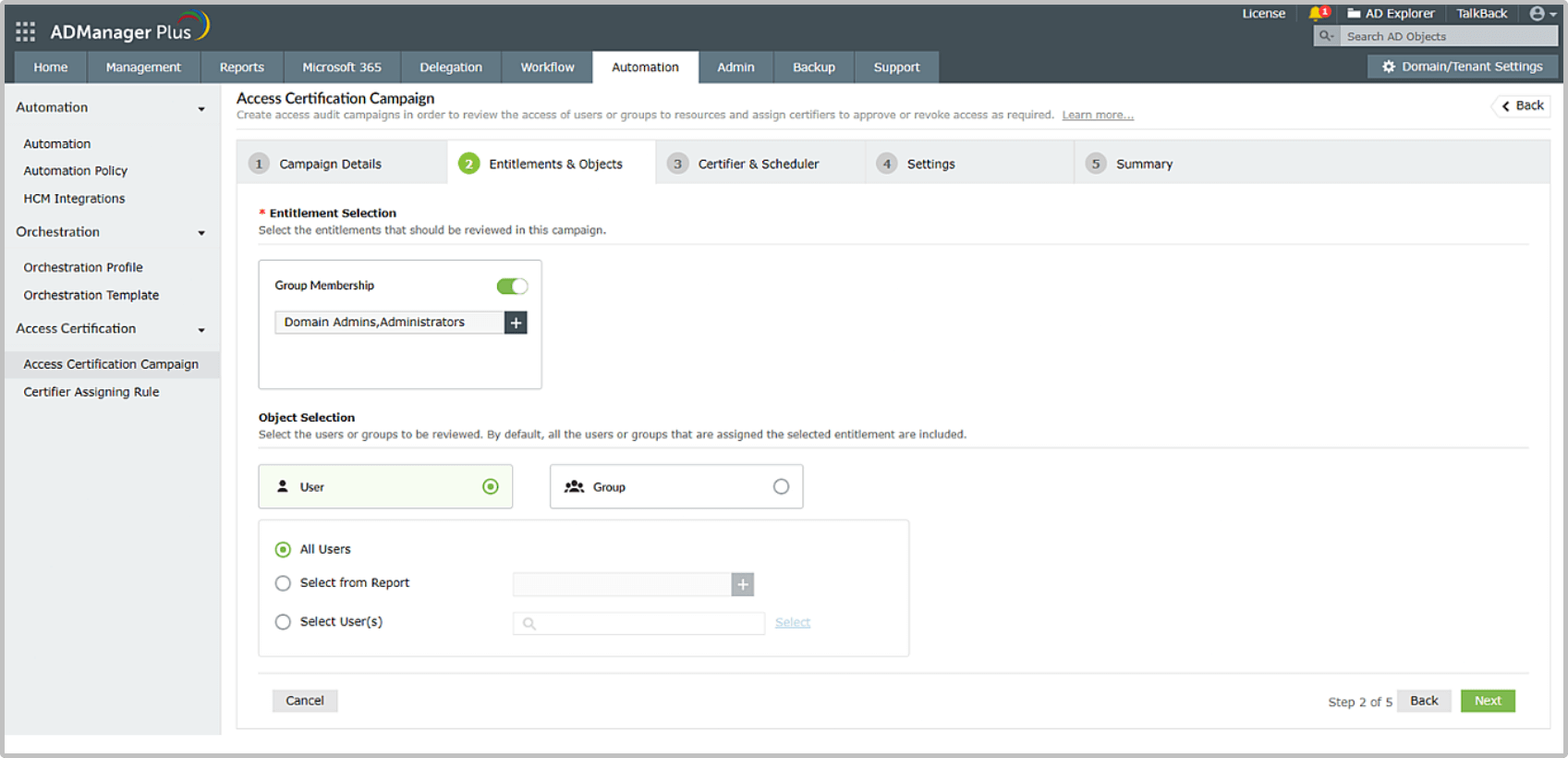
Each certification campaign that is conducted in ADManager Plus is stored and can be viewed by stakeholders. A detailed history of the campaign, including certifier name, action performed, comments added by the certifier, and more, is recorded. Auditors and compliance staff can use this during audit trials.
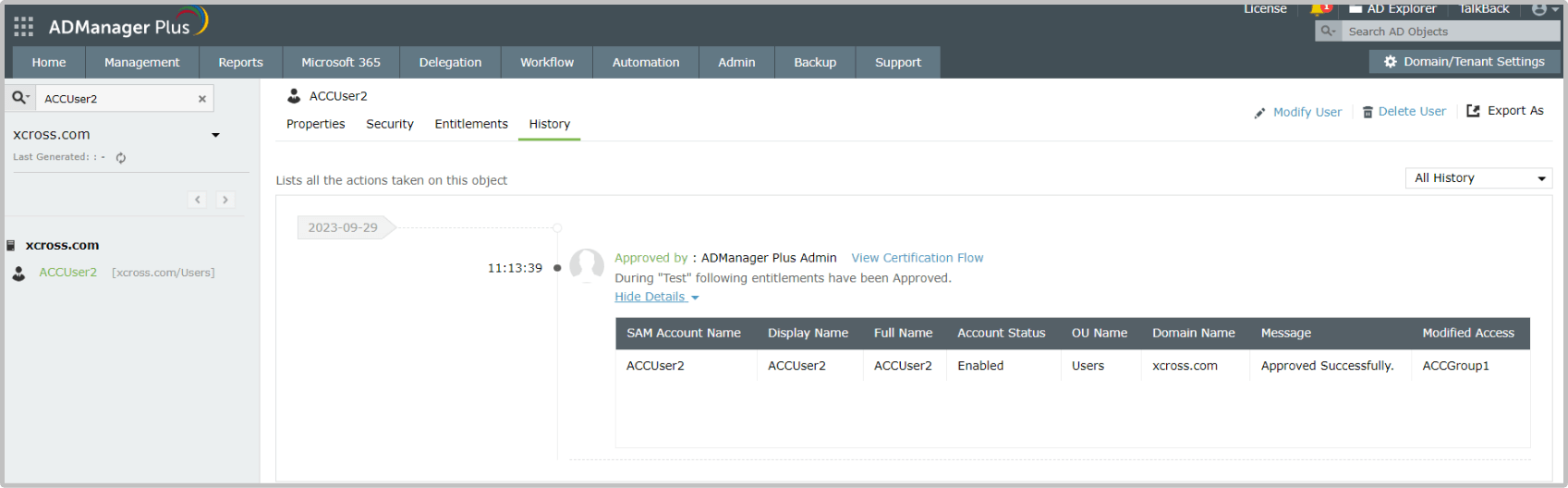
Schedule and run access certification campaigns frequently at a desired time to review and recertify users' access rights, ensuring that users' access is consistently validated and aligned with current roles and responsibilities.

Exhaustive reporting on Active Directory Users and user-attributes. Generate reports in user-activity in your Active Directory. Perform user-management actions right from the report interface!
Learn moreActive Directory reports to assist you for compliance to Government Regulatory Acts like SOX, HIPAA, GLBA, PCI, USA PATRIOT...and much more! Make your organization compliance-perfect!
Learn moreMake your everyday Active Directory management tasks easy and light with ADManager Plus's AD Management features. Create, modify and delete users in a few clicks!
Learn moreConfigure Active Directory Terminal Services attributes from a much simpler interface than AD native tools. Exercise complete control over technicians accessing other domain users' computers.
Learn moreGet rid of the inactive, obsolete and unwanted objects in your Active Directory to make it more secure and efficient...assisted by ADManager Plus's AD Cleanup capabilities.
Learn moreA complete automation of AD critical tasks such as user provisioning, inactive-user clean up etc. Also lets you sequence and execute follow-up tasks and blends with workflow to offer a brilliant controlled-automation.
Learn more