Simple Certificate Enrollment Protocol (SCEP)
Simple Certificate Enrollment Protocol (SCEP) is a certificate management protocol which is predominantly used for enabling certificate-based authentication. With SCEP, Mobile Device Manager Plus lets you enforce certificate-based authentication for Wi-Fi, VPN, and E-mail configurations on your managed Android devices.
Generally, in large scale organizations, it becomes a cumbersome task for the IT administrator to manually issue client certificates for all the Android devices within the organizational network. SCEP simplifies certificate configuration and distribution by providing a simple and scalable method for handling certificates within organizations.
The major advantages of certificate-based authentication using SCEP are as follows:
- Zero user intervention since users are automatically authenticated using certificates.
- Removes the burden of manually configuring user-specific client certificates.
- Secure network communication as the data is encrypted and authenticated using certificates.
- Client certificates also function as an additional layer of security by providing two-factor authentication; security threats caused by using unauthorized devices to access business data, or to connect to work related Wi-Fi or VPN networks can be avoided.
The device directly contacts the SCEP server to generate the certificate, therefore ensure the SCEP server is reachable from the device. It is not necessary for the SCEP server to be reachable to MDM MSP
Pre-requisites
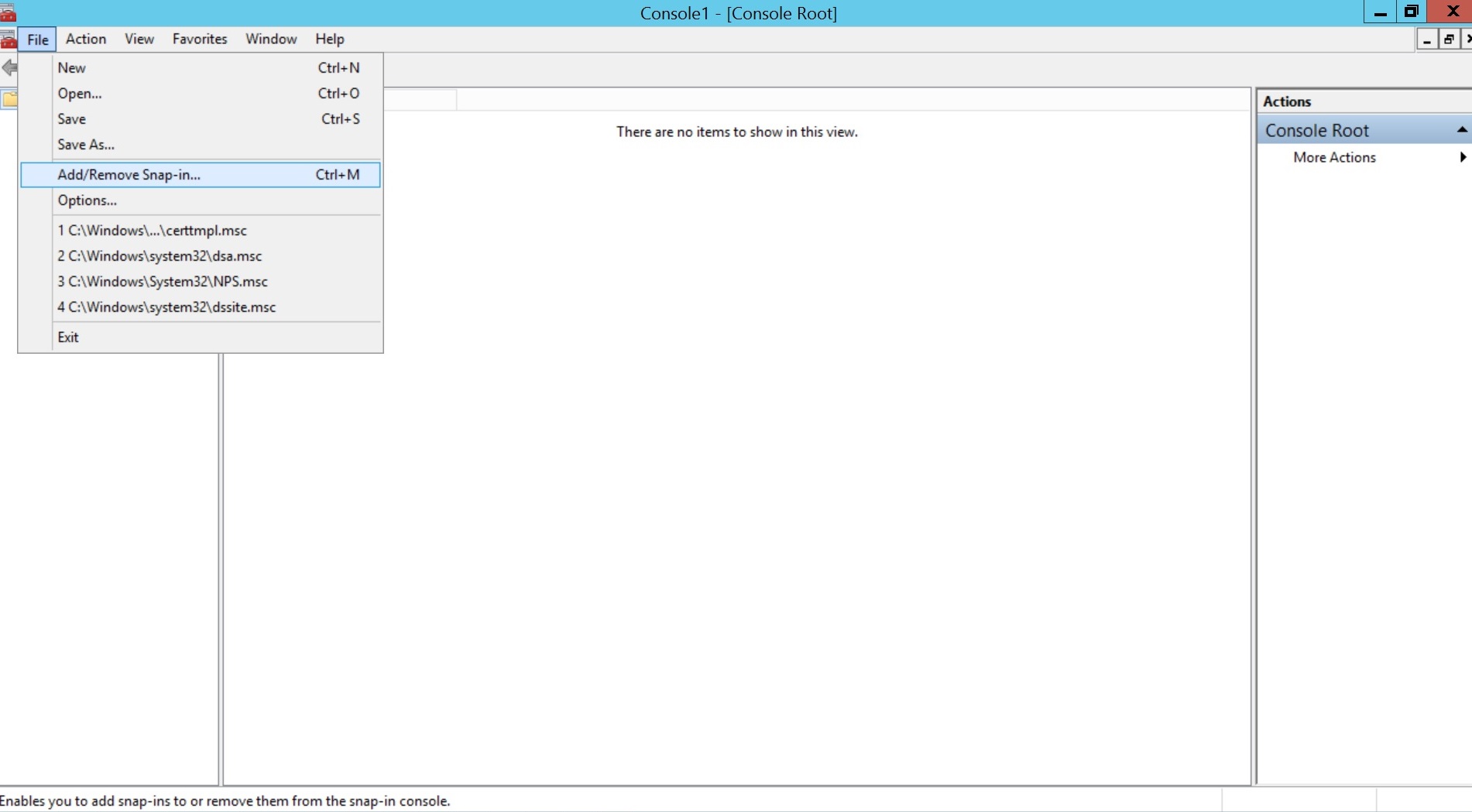
- Click on Start Menu, select Run, type mmc and click OK.
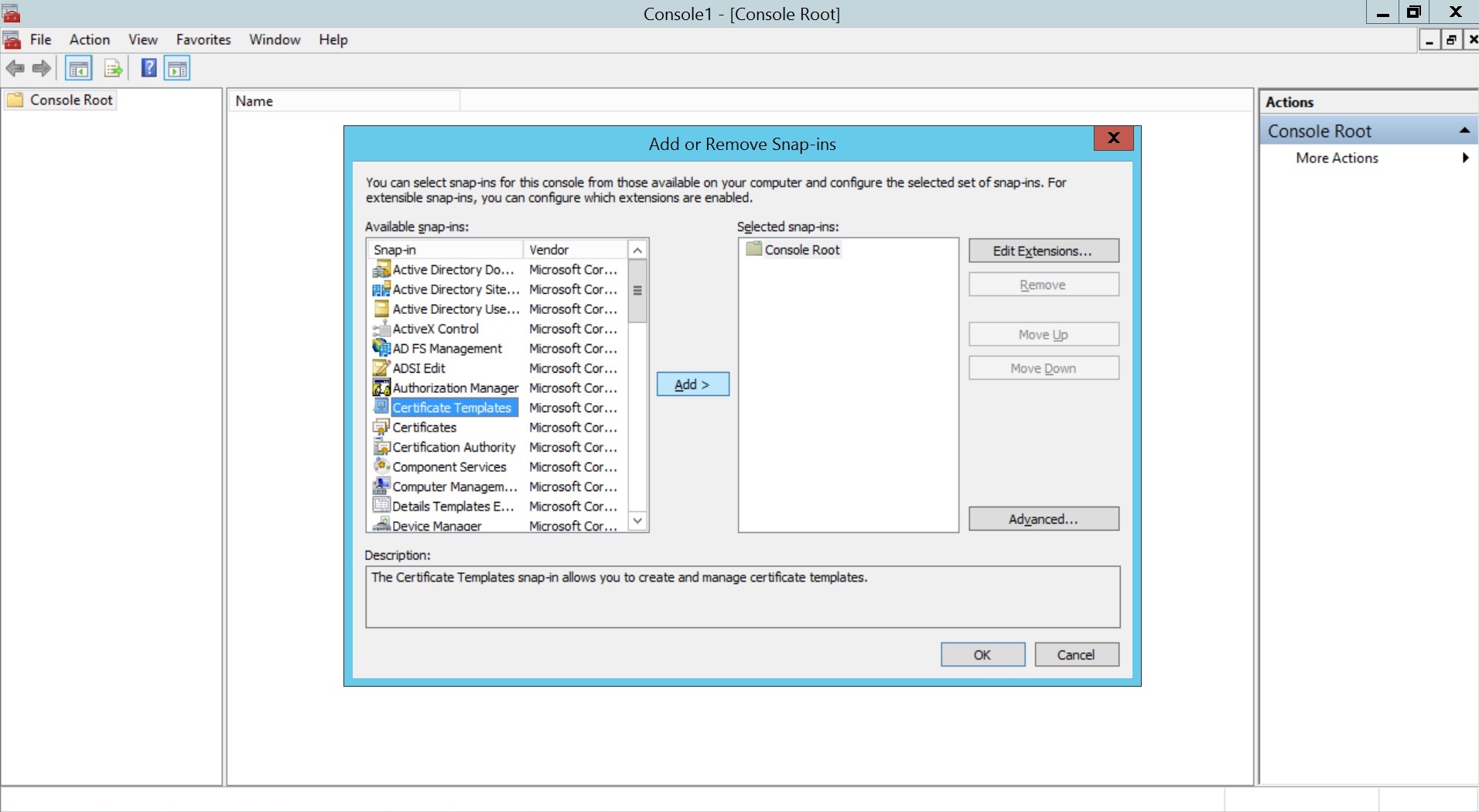
- Click File and select Add/Remove Snap-in....Select Certificate Templates, click Add and then click OK.
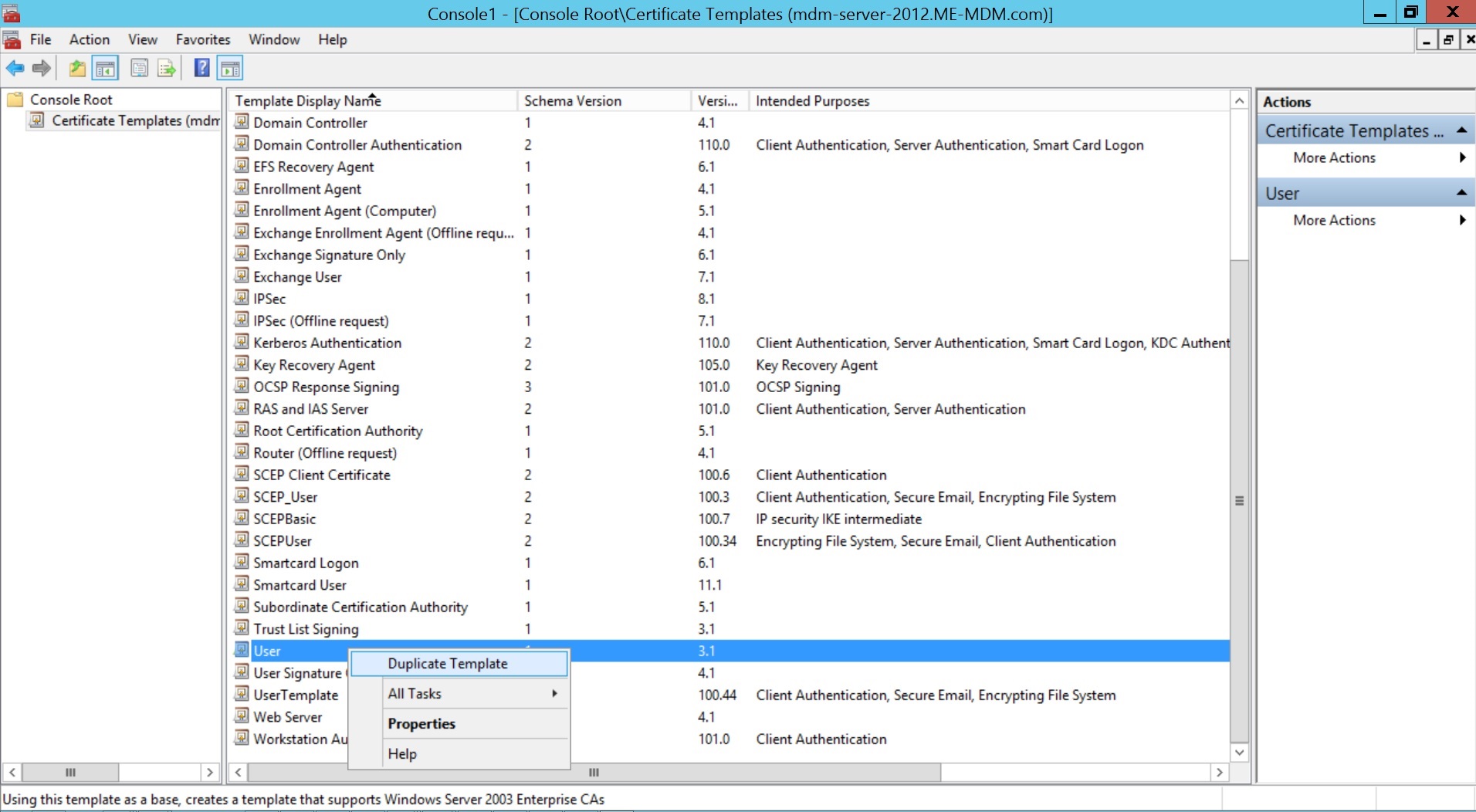
- Right click Certificate Template and select Manage.
- Click on User and select Duplicate Template.
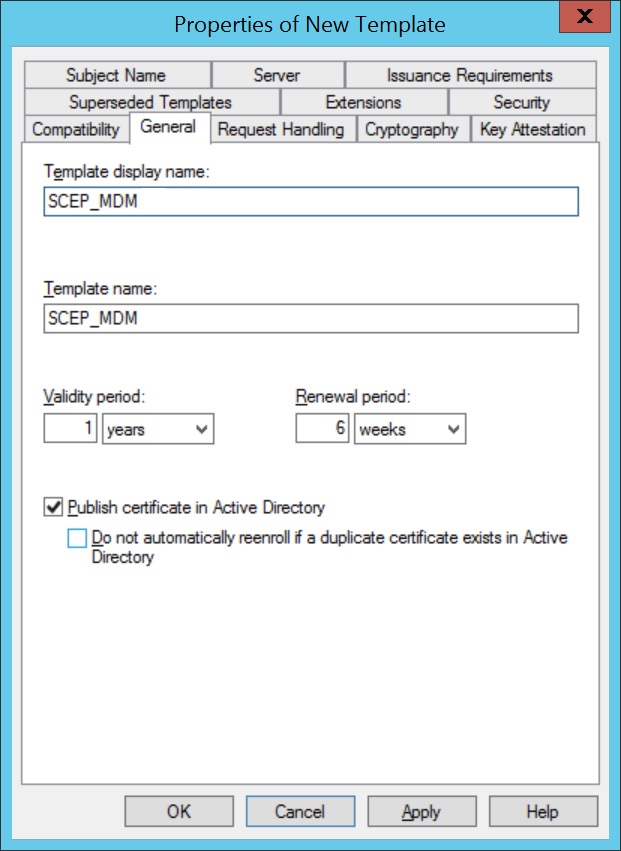
- Specify a Template display name and save it by clicking OK.
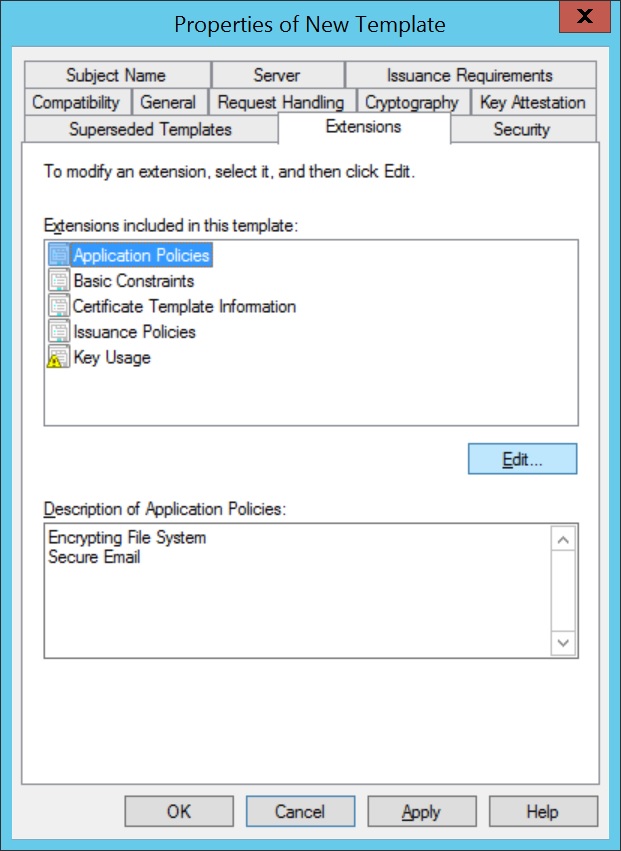
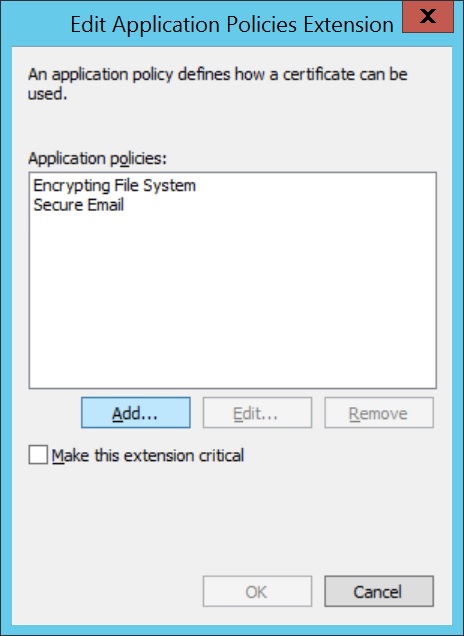
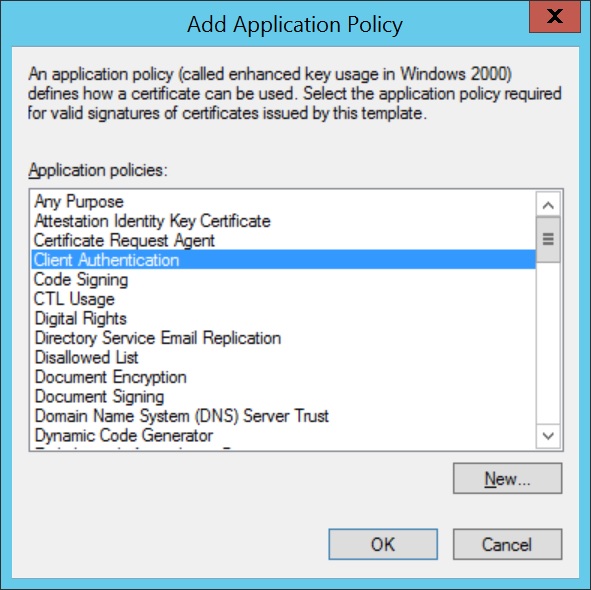
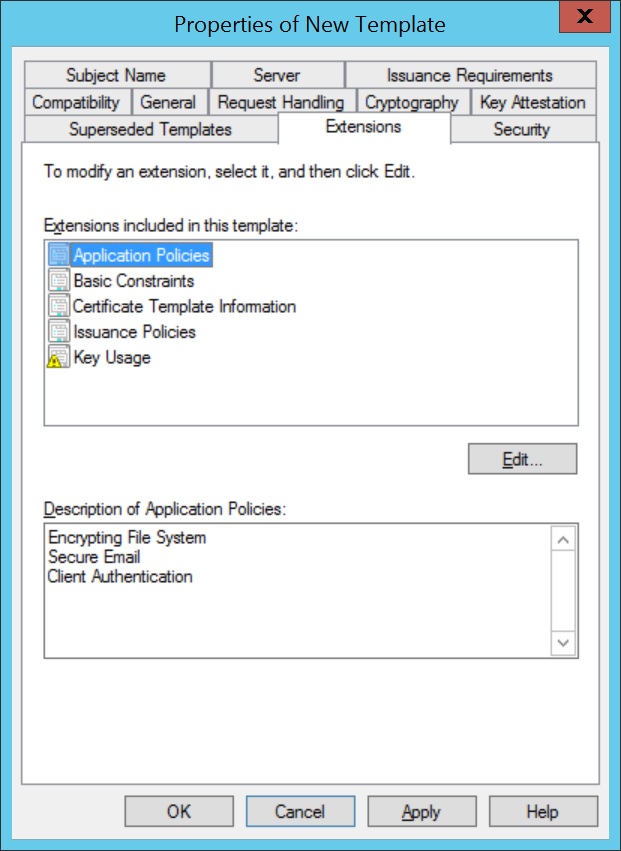
- Click on Extensions,select Application Policies. Click Edit and select Client Authentication, to add it to Application Policies.
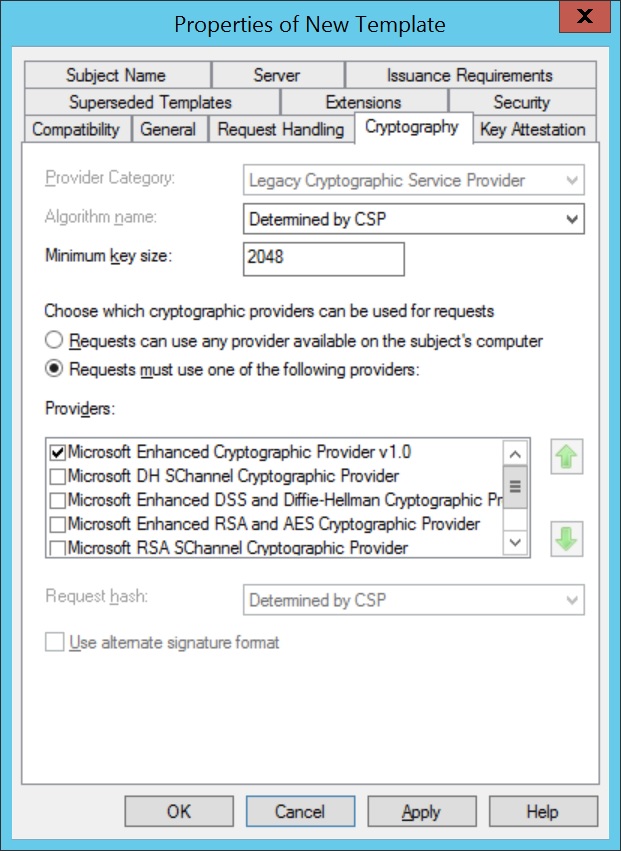
- Click on Cryptography and specify the Minimum key size. The recommended key size is 2048, as it enhances the security. This key size is to be specified while configuring SCEP in MDM MSP.
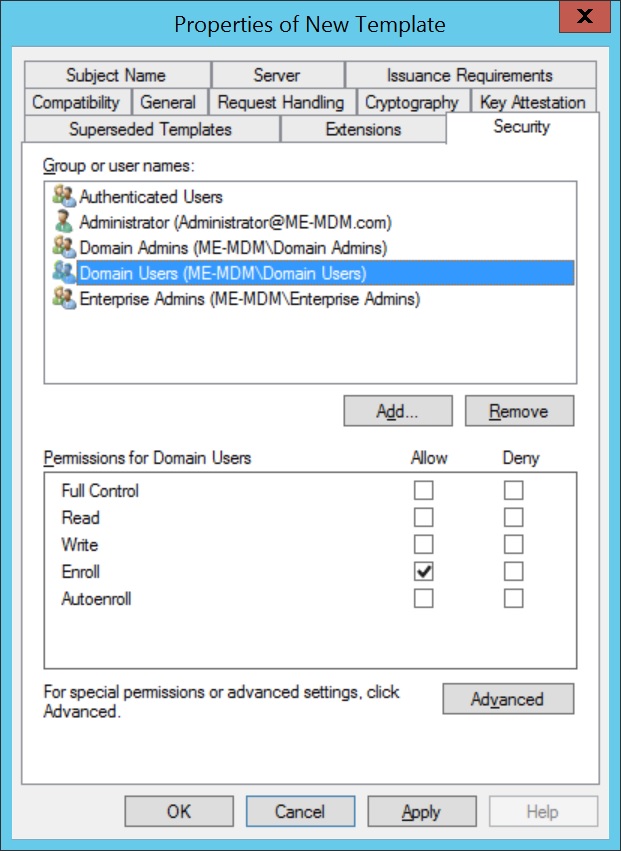
- Click on Security and select the Group(s), to which the policy is to be applied. Ensure Enroll is an allowed permission for the selected domain(s).
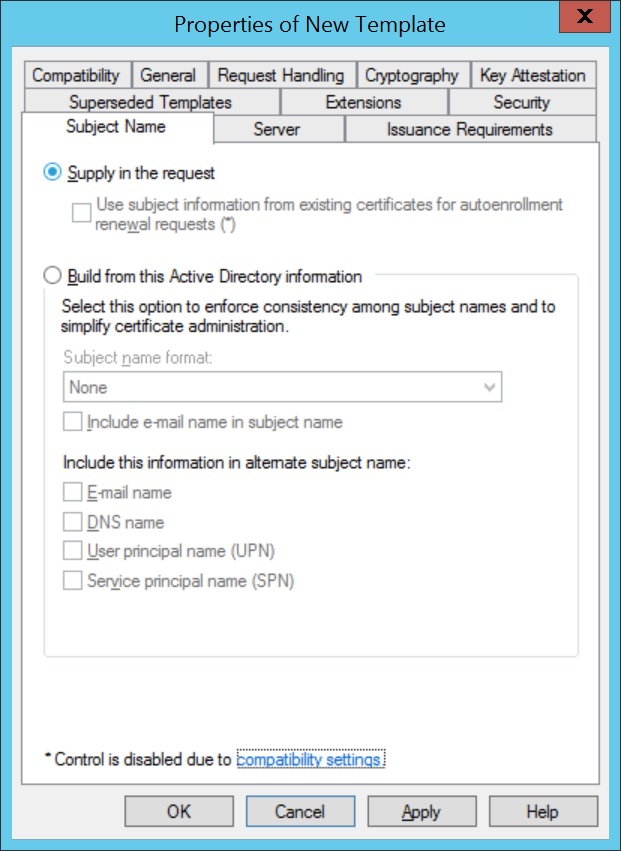
- Click on Subject Name and select Supply in the request, for subject names to be specified in the certificate request.
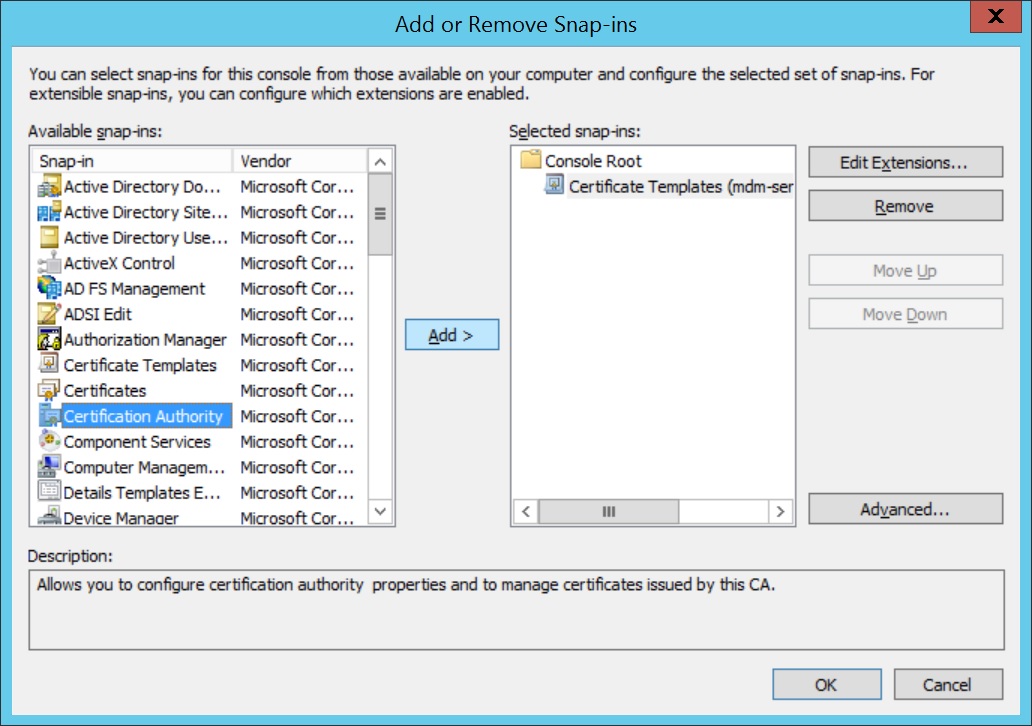
- Add Certificate Authority as a snap-in in the Microsoft Management Console(MMC).
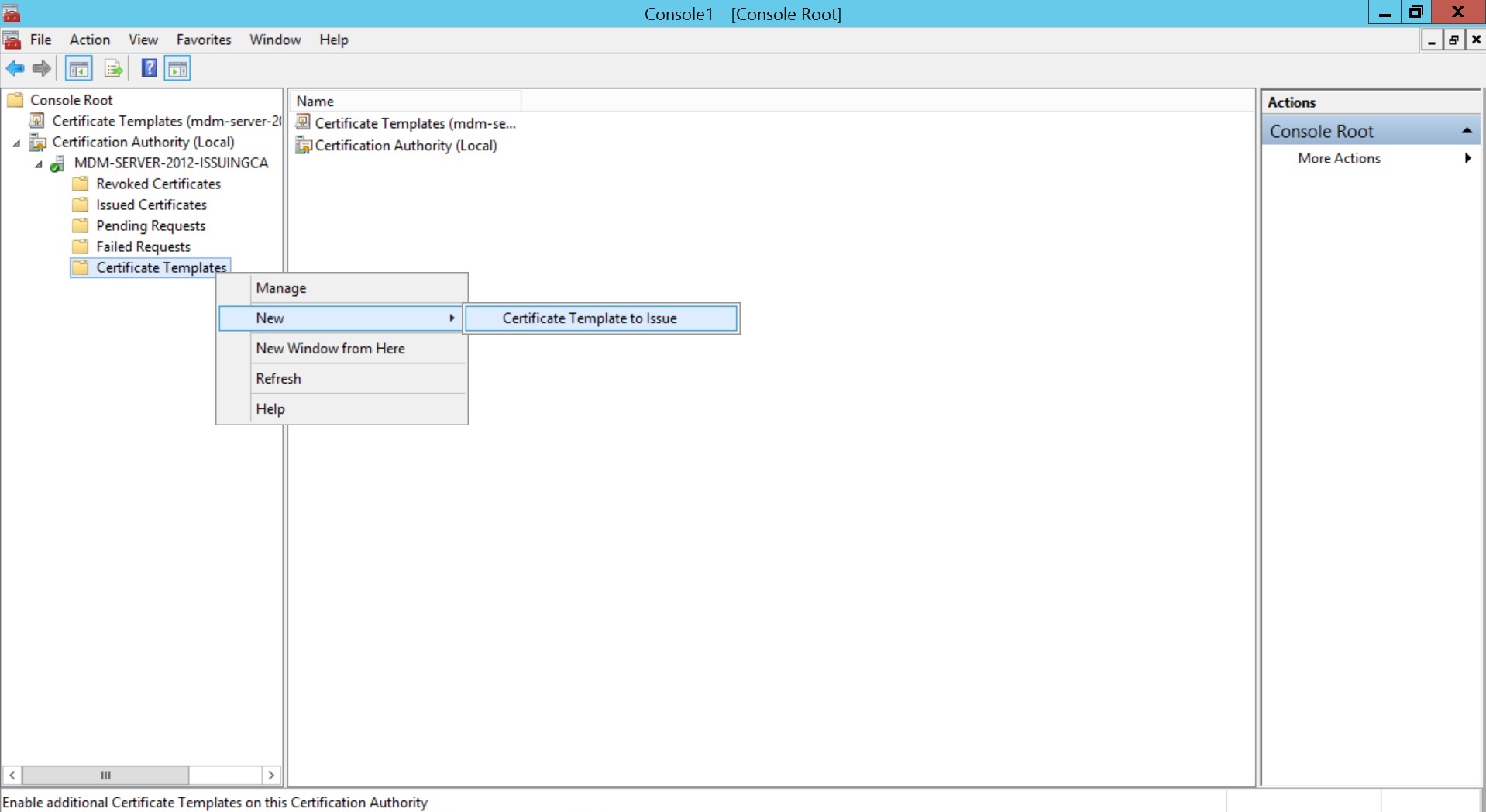
- Expand Certification Authority and right-click on Certificate Templates. Click New and select Certificate Template to Issue.
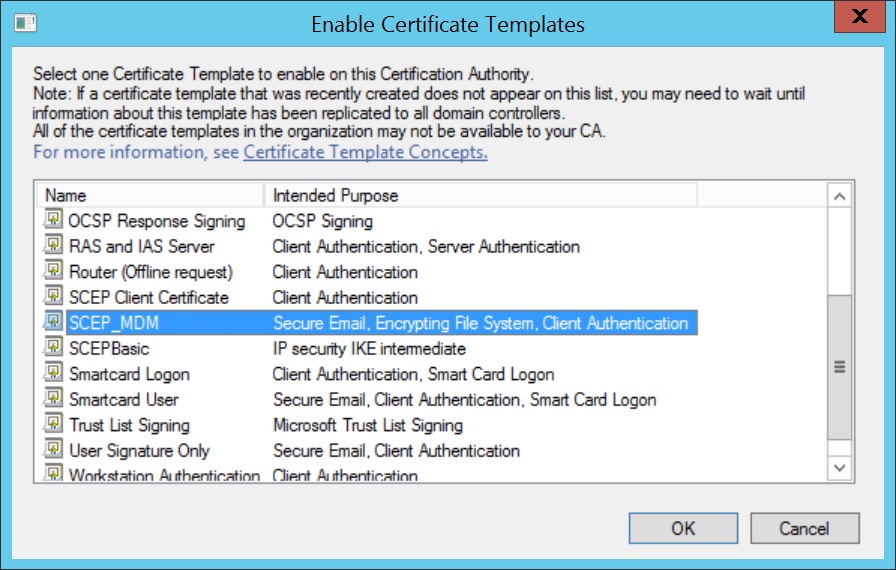
- Select the Certificate Template created before and click OK.
- Click on Start Menu, select Run, type regedit and click OK.
- Expand HKEY_LOCAL_MACHINE -> SOFTWARE -> Microsoft -> Cryptography -> MSCEP.
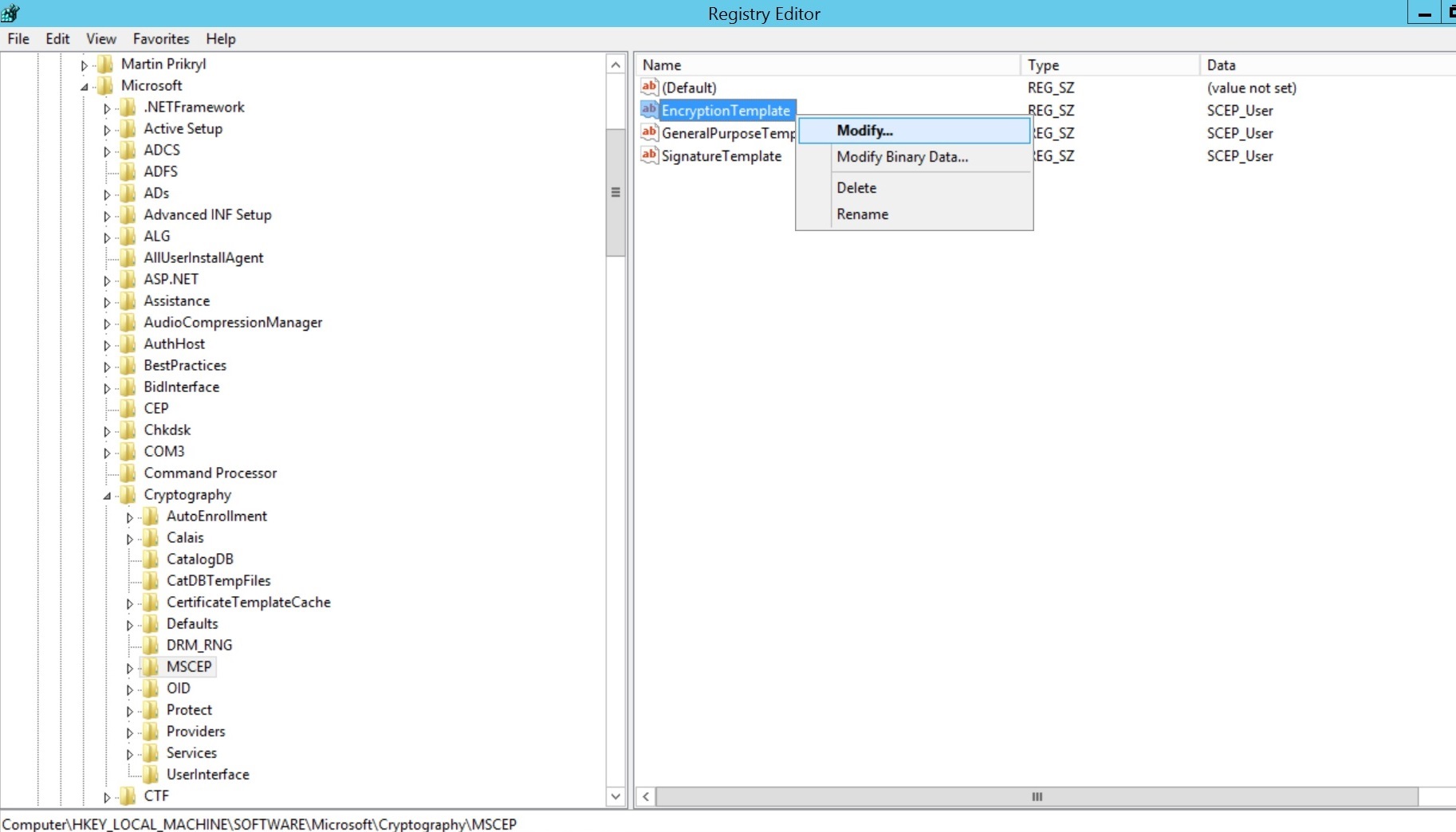
- Right-click on Encryption Template and click Modify.
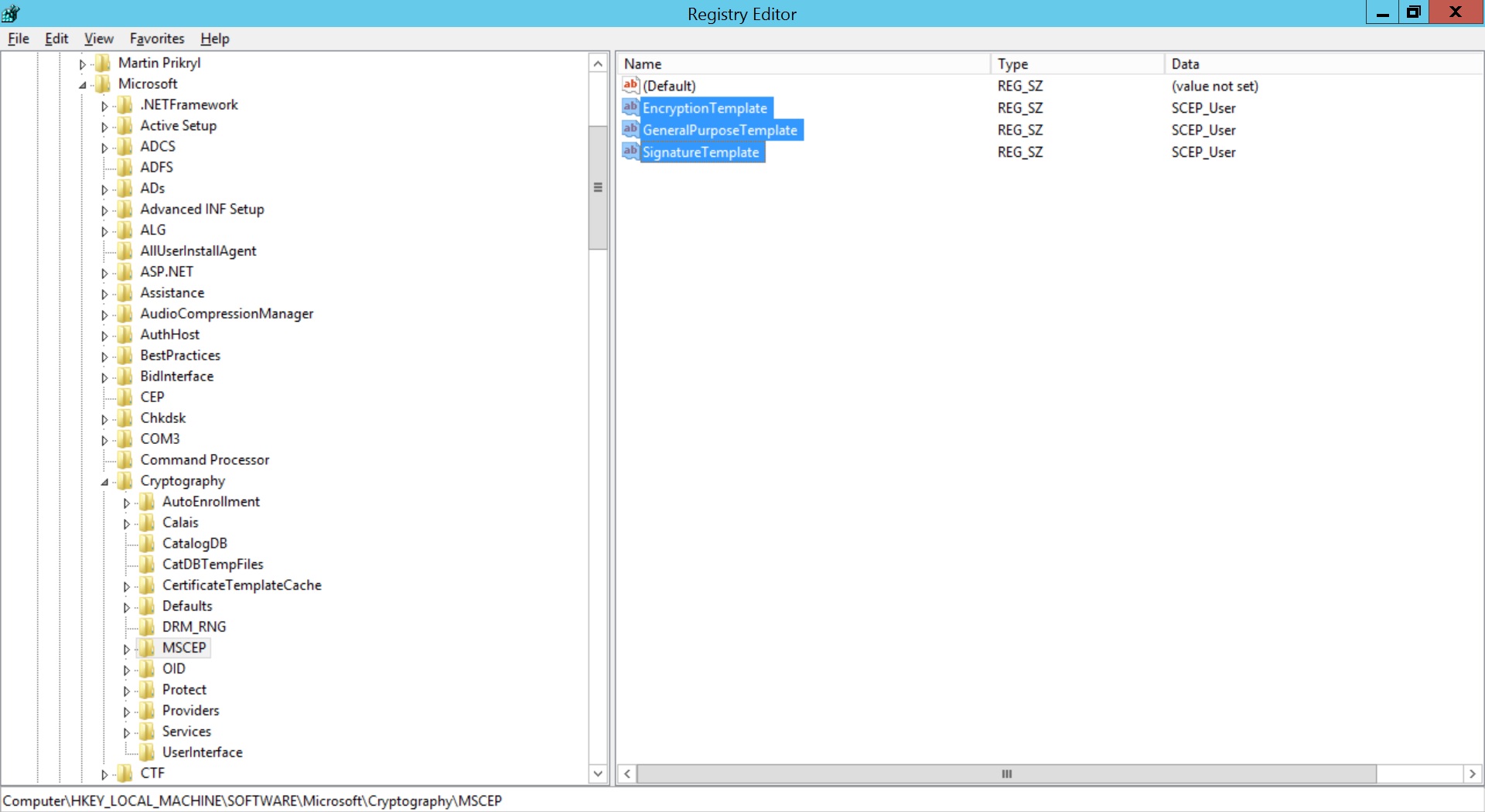
- Specify the name of the created Certificate Template for Value date. Repeat the same for GeneralPurposeTemplate and SignatureTemplate. Restart the server machine once for the changes to take place
To change the default certificate template used by Microsoft NDES, windows registry values are to be changed.
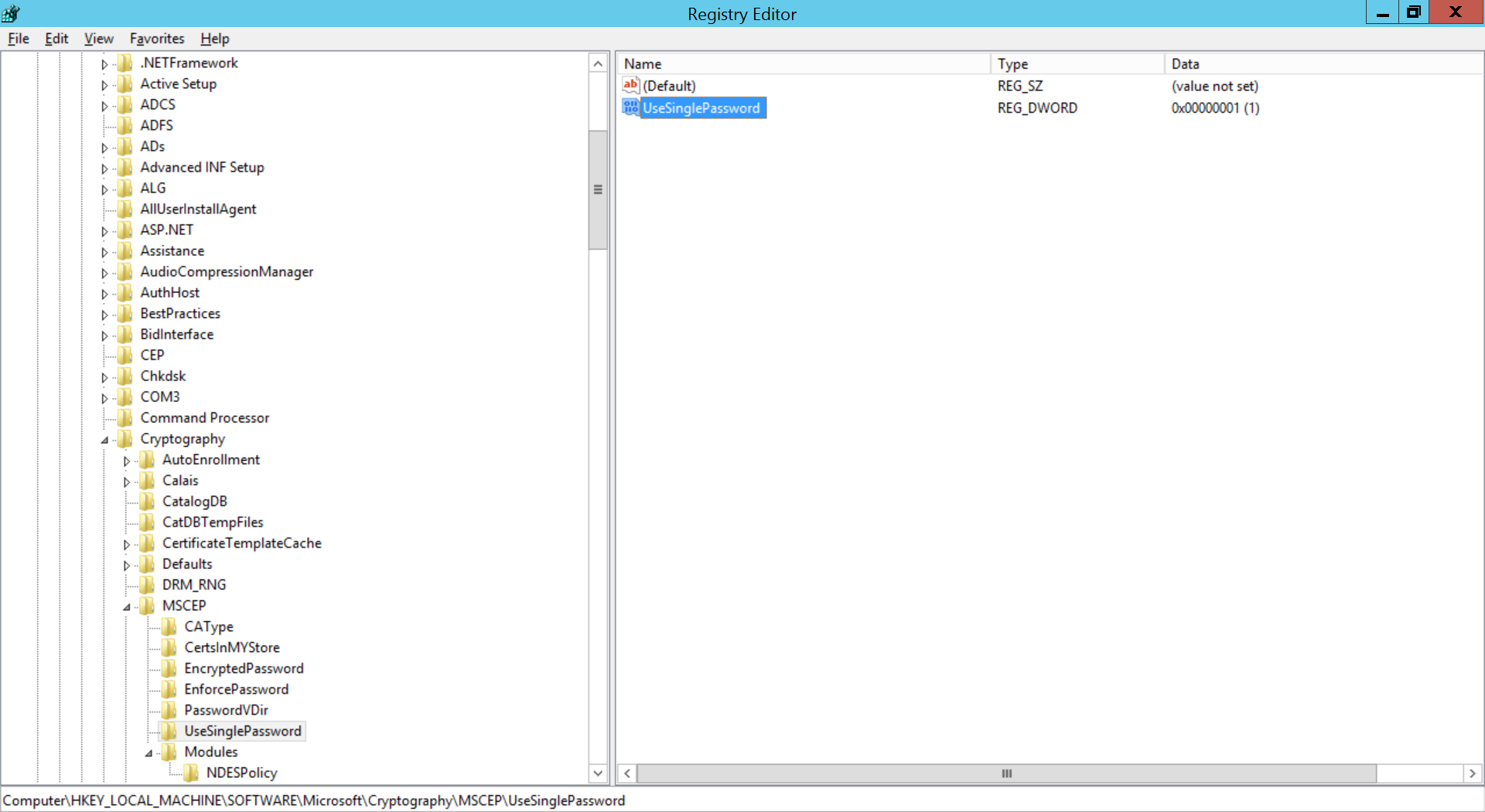
- Open regedit and expand HKEY_LOCAL_MACHINE -> SOFTWARE -> Microsoft -> Cryptography -> MSCEP -> UseSinglePassword.
- Right-click UseSinglePassword and change the value of data as 1.
If you're using Challenge password(recommended), then registry values must be modified to prevent expiry of Challenge password.
After configuration is complete, restart the NDES Server.
Configuring SCEP in MDM MSP
- The value for Subject should be in LDAP DN format as explained here.
- You can verify Server details such as enrollment challenge password from http://<your-server>/CertSrv/mscep_admin and http://<Your-Server>/crtsrv/mscep/mscep.dll.
- If the SCEP server is unreachable, try accessing the SCEP server URL in the format http://<your-server>/CertSrv/mscep/mscep.dll from the device. If the URL can not be reached, try accessing the URL after connecting to a local WiFi and then distribute the profile.
| Profile Specification | Description |
|---|---|
| SCEP Configuration Name | The user-defined configuration name, which is used to refer this configuration in other configurations such as Wi-Fi, VPN etc., |
| SCEP SETTINGS | |
| Server URL | The URL to be specified in the device to obtain certificate. Provide HTTP Server URL, if the SCEP server is within the organization network and not exposed to external networks. The certificate is requested through this URL. For NDES, the server URL format: http://<your-server>/CertSrv/mscep/mscep.dll |
| Certificate Authority Name | Specify the name of the Certificate Authority issuing certificates. |
| Subject | Specify the details(%username%, %email%, %domainname%,%devicename%) to map the corresponding details in the device. |
| Subject Alternative Name Type | Specify the alternate details(RFC 822 Name, DNS Name, Uniform Resource Identifier). |
| Subject Alternative Name Type Value (Can be configured only if Subject Alternative Name Type is configured) | Specify the value for alternative name type. |
| NT Principal Name | Specify the NT Principal Name used in the organization. |
| Maximum Number of Failed Attempts | Number of attempts to obtain the certificate from the CA. |
| Time interval between attempts | Time to wait before subsequent attempts to obtain certificate |
| Challenge Type | A pre-shared secret key provided by the CA, which adds additional layer of security |
| Enrollment Challenge Password | Provide the challenge password to be used. Challenge Password can be identified as explained here. |
| Key Size | Specify whether the key is 1024 or 2048 bits |
| Use as Digital Signature | Enabling ensures the certificate can be used as Digital Signature |
| Use for Key Encipherment | Enabling ensures the certificate can be used as Key Encipherment |
