- Quick Links
- Related features
- Windows log management
- Syslog management
- Server log management
-
Application log management
-
Network device monitoring
- Log management
- Related products
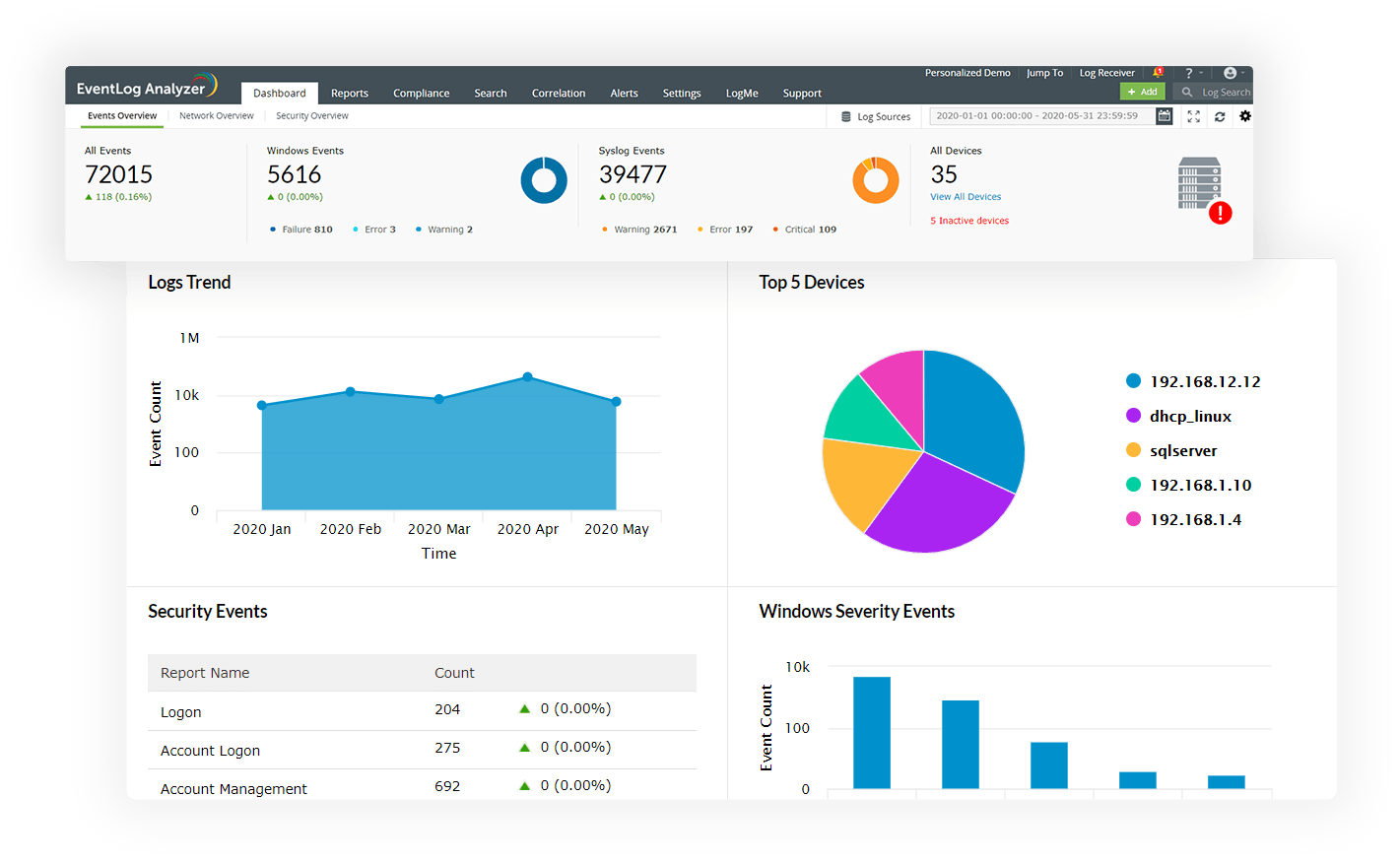
Gain actionable insights from your network logs with intuitive dashboards, predefined report templates, and alert profiles that are meticulously drafted to meet the security and auditing needs of organizations. This log analyzer software supports analysis of over 700+ log formats right out of the box.
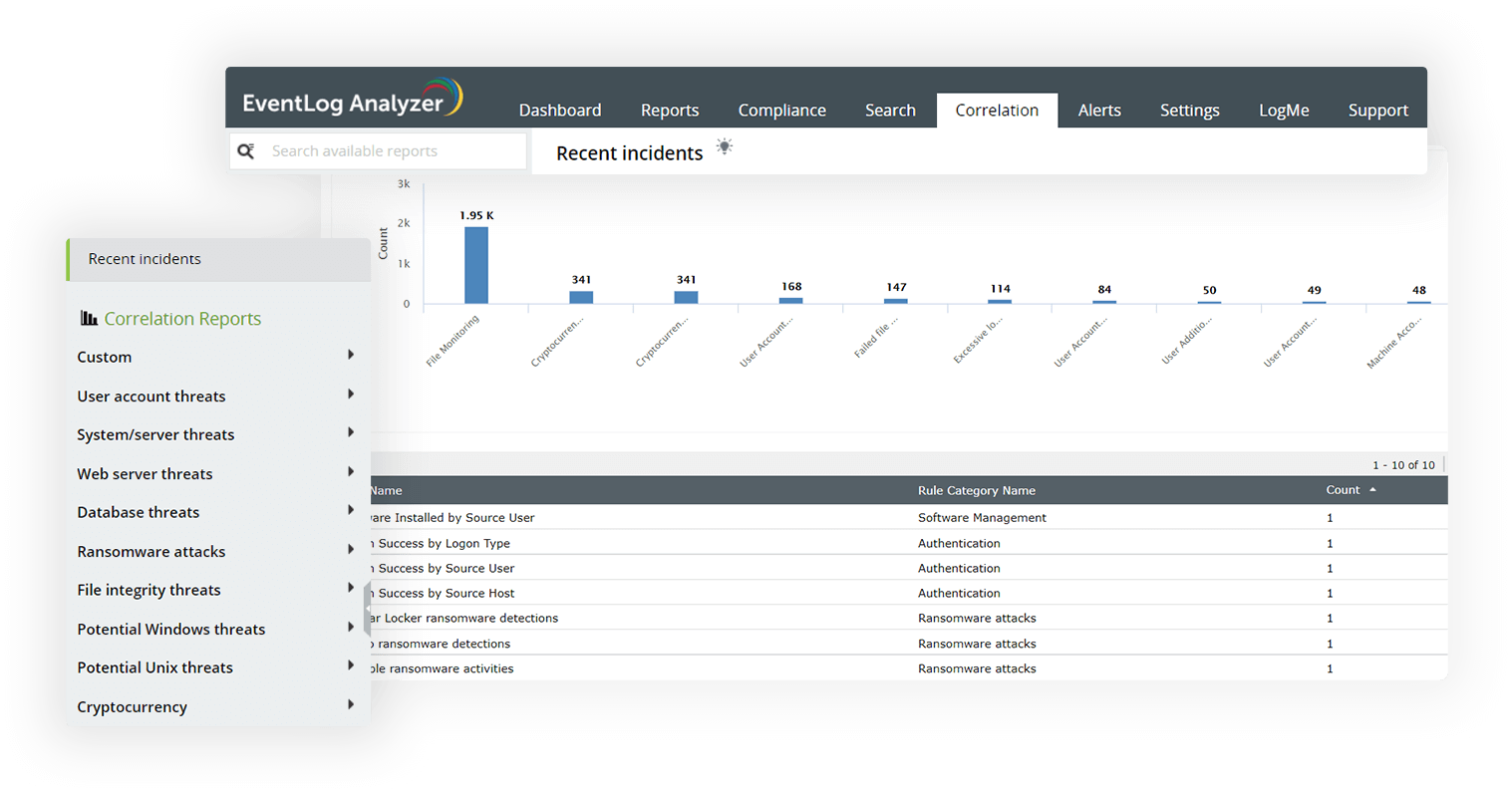
Centrally collect, monitor, analyze, correlate, search, and archive log data from devices across the network. This centralized log analytics tool helps you detect attack attempts and trace potential security threats faster. Ensure timely remediation of these threats using the automated incident response capabilities.
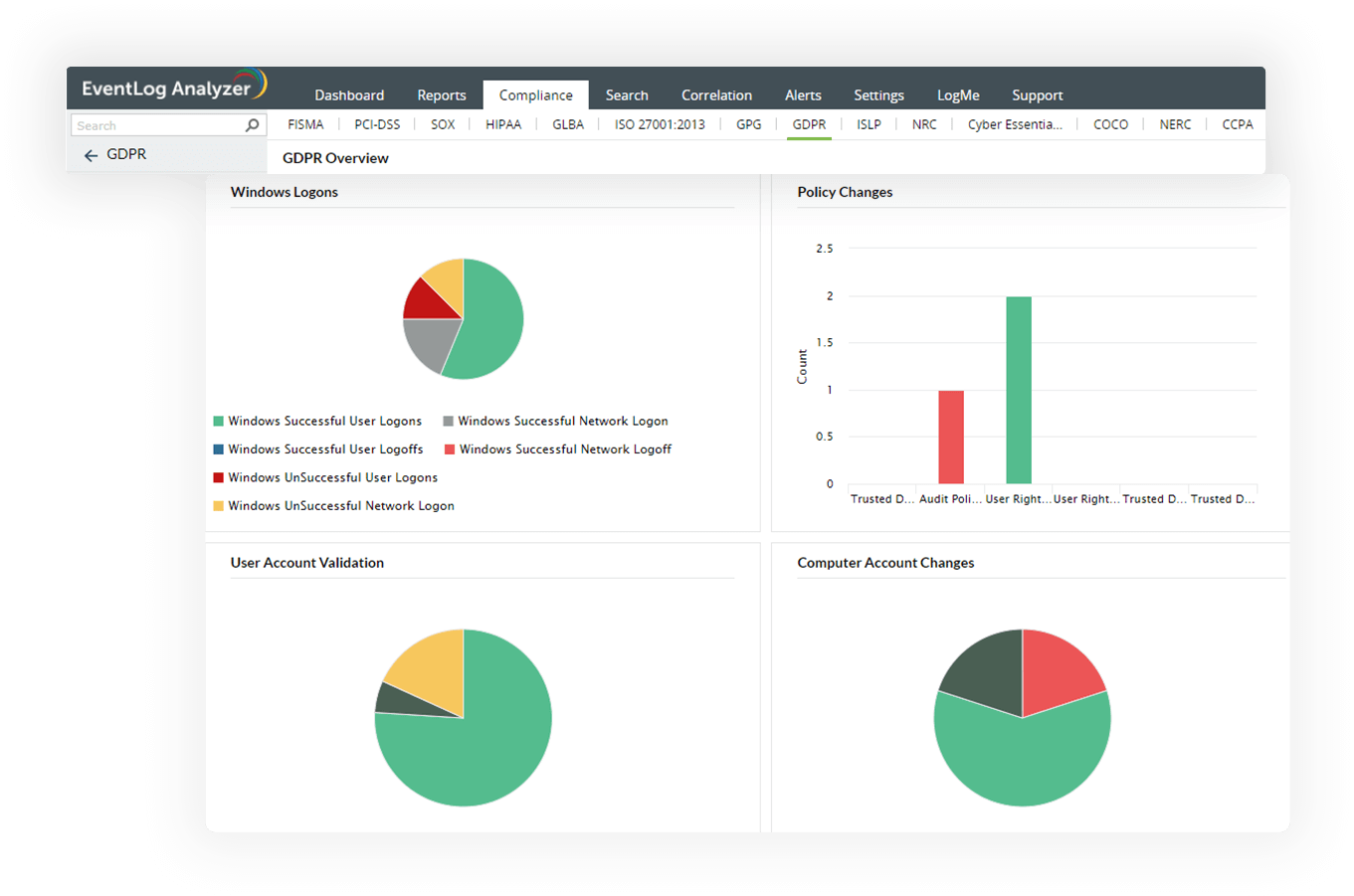
Meet compliance requirements for various regulatory mandates including PCI DSS, GDPR, FISMA, ISO 27001, and SOX with audit-ready report templates from EventLog Analyzer. Get notified in real time upon compliance requirement violations and build a custom compliance report to meet your internal security policy using the solution's integrated compliance management system.
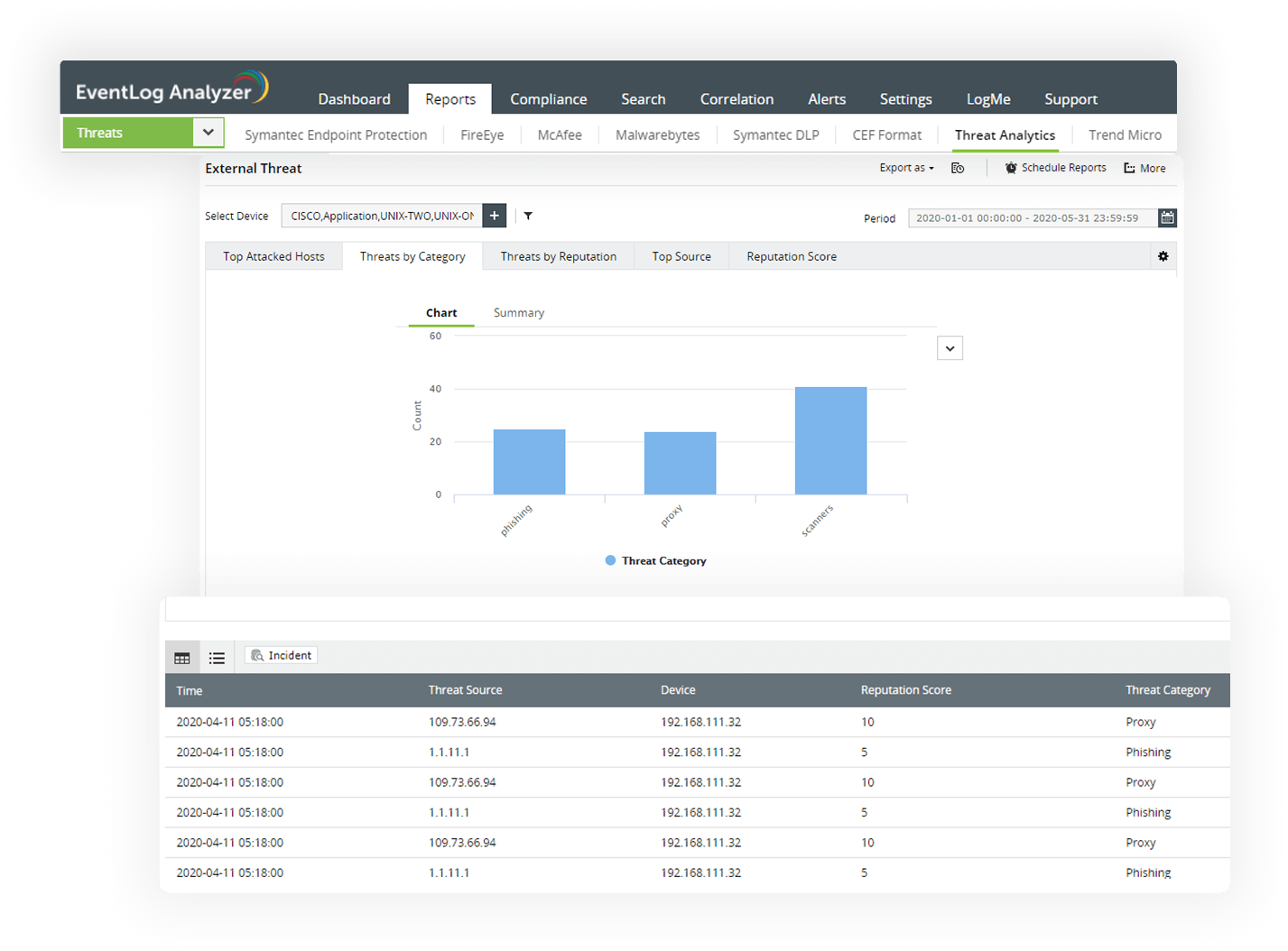
The log analysis software comes bundled with a global IP threat database and STIX/TAXII feed processor to detect any malicious inbound or outbound traffic. Analyze web server logs and firewall log data to identify traffic from and to blacklisted IP addresses and instantly block them with automated workflow profiles. Analyze Active Directory (AD) and domain name system (DNS) logs to instantly spot suspicious activities of insiders. Detect malicious activities such as privilege escalations, unauthorized access to sensitive data, first time access to critical resource, and more with effective AD and DNS log analysis.
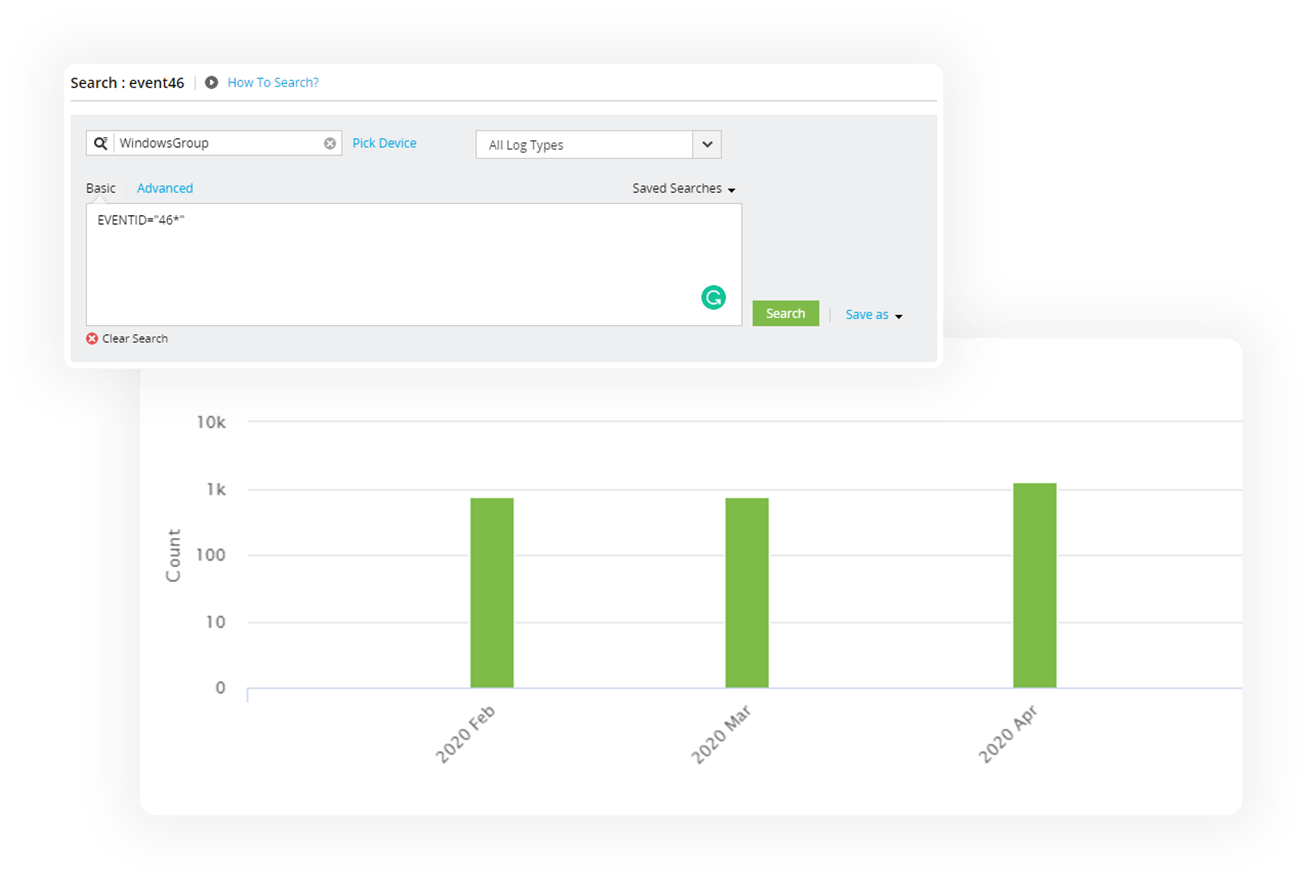
EventLog Analyzer, our log analyzer software, comes with a powerful log search feature for conducting root cause analysis. Search through raw and formatted logs and generate reports based on the results. Automate query building with an easy-to-use drag n drop interface. This log analysis solution comes with different search options such as boolean, range, group, and more to narrow down the search to the exact log entry within minutes. The powerful log search analytics can process up to 25,000 logs per second. This log analyzer software is capable of locating a malicious log entry and setting up remediation from within the log search console.
Log data contains valuable information on your network activities and provides insights that you need to spot issues that impact the proper functioning of your business. Log analysis tools like Eventlog Analyzer aggregate the logs from your network devices into a single location using an agent or agentless methods to monitor and raise alerts if anomalies are detected.
Cyberattacks are a continuous risk for organizations. But companies that periodically monitor their network logs will be able to identify anomalies better. Eventlog Analyzer is a log analysis software that can collect and monitor device logs and alert you in case anything suspicious is found. Even after an attack has happened, you can perform forensic analysis using the archived logs to identify the events that led up to an incident. This will help you discover the weaknesses in your network and formulate a better cybersecurity strategy for your organization.
Eventlog Analyzer is on-premises log analyzer software. So all the log collection and analysis happens only in the machine where the tool is installed. However, the product does collect the product usage logs for diagnostic purposes, which you can disable from the settings.
Yes. EventLog Analyzer is free for up to five log sources. Apart from the Free Edition, the solution also has Standard and Professional editions. Check out the differences between the editions here.