User Activity Monitoring Software
User activity monitoring plays an important role in network security and bandwidth management. Monitoring and tracking end user behavior on devices, networks, and other company-owned IT resources help identify internal threats in a network. If not performed by an efficient network monitoring tool, this continuous user activity monitoring (UAM) can become cumbersome.
What is User Activity Monitoring?
User Activity Monitoring refers to the practice of tracking and recording user actions on IT assets including desktops, servers, firewalls, applications, and network connections. This includes everything from websites visited and files accessed to VPN usage and firewall configuration changes. With hybrid and remote work becoming the norm, UAM has expanded beyond basic employee oversight. It now plays a critical role in detecting insider threats, preventing data leaks, analyzing network traffic patterns, enforcing regulatory compliance, troubleshooting network slowdown.
Benefits of user activity monitoring:
Monitoring user activity provides significant advantages, leading to enhanced security, compliance, and operational efficiency. Key benefits include:
- Enhanced security
- Threat detection: Identify suspicious activities such as unauthorized access attempts, policy violations, and unusual user behavior. Proactively detect and respond to security threats.
- Reduced risk: Quickly identify anomalies, deploy preventive measures, and prevent data breaches, malware, and other security events. This minimizes unintended downtime.
- Enhanced visibility: Gain comprehensive visibility into user activity. Monitor user actions, access patterns, and changes made to your firewalls.
- Improved compliance
- Audit trail: User activity monitoring maintains a detailed record of all user activities, providing audit trails to meet compliance mandates.
- Policy enforcement: In-depth user activity reports help maintain compliance by identifying violations and regulating access control.
- Simplified troubleshooting
- Root cause analysis: UAM facilitates faster issue diagnosis by drilling down into user actions and their impact on the network, enabling quicker troubleshooting.
- Configuration management: Monitor users and changes made to firewall configurations, making it easier to identify configuration errors and understand their impact.
- Heightened operating efficiency
- Increase accountability: UAM promotes accountability among network users by making sure all activities and monitoring, encourage responsible behavior.
- Improved decision-making: Gain valuable insights into user behavior and network activity, enabling you to make informed decisions for optimal network security.
Challenges in User Activity Monitoring
While User Activity Monitoring (UAM) is essential for security, compliance, and operational visibility, implementing and maintaining an effective UAM strategy comes with its own set of challenges. Organizations often face technical, operational, and policy-level hurdles when trying to monitor user behavior across distributed systems and hybrid IT environments. Below are some of the key challenges in user activity monitoring:
- 1. Data Volume and Noise : User activity monitoring generates massive volumes of log data across devices, applications, and endpoints. Sifting through this data to find meaningful insights is difficult, especially when most entries are repetitive or low-risk. The sheer amount of noise can overwhelm monitoring tools and lead to alert fatigue, causing critical issues to be overlooked.
- 2. Lack of contextual visibility : Many monitoring systems lack the ability to provide context behind user actions, such as whether access was authorized or unusual for a user’s role. Without understanding the "why" behind the "what," it becomes challenging to differentiate between legitimate and malicious behavior. This limits the accuracy of threat detection and can lead to both missed incidents and false alarms.
- 3. Encrypted traffic and VPN usage : Encryption and VPNs, while essential for security, limit visibility into user activity by masking traffic content and user locations. As more organizations adopt encrypted communication, traditional monitoring tools struggle to inspect traffic effectively. This creates blind spots in user behavior analysis and complicates anomaly detection.
- 4. Privacy and legal compliance : Monitoring user activity must be balanced with employee privacy and legal compliance, especially under regulations like GDPR and HIPAA. Over-monitoring without consent can lead to legal consequences and loss of employee trust. Organizations need to be transparent and follow clear policies to ensure ethical and lawful monitoring practices.
- 5. Diverse IT environments: Enterprises operate across hybrid environments—on-premise, cloud, and remote—which produce inconsistent log formats and monitoring challenges. Legacy systems may not support integration, while cloud services often follow different standards. This fragmentation makes it hard to maintain unified visibility and may lead to security gaps.
How to monitor user activity on network.
User activity monitoring can be performed using log analysis. Firewall logs help reveal information about infiltration attempts at the perimeter of a network, and on the nature of traffic coming in and going out of the firewall; this means security administrators can monitor user level security threats and traffic usage by optimally analysing the firewall logs. Security administrators need to also set user specific alarms by setting traffic and bandwidth triggers, this is helpful in identifying anomalous activities in the network
User activity monitoring tool
The goal of any user activity monitoring tool (UAM tool) should be to fetch, analyze, and filter out actionable information valuable for network security and bandwidth capacity planning. Firewall Analyzer is a smart UAM solution that helps in monitoring user activity and provides the following:
User activity and employee monitoring
User activity monitoring with Firewall Analyzer; you can continuously monitor user activity on network, individual user-level bandwidth and security anomalies (User activity monitoring solutions). The employee internet usage monitoring function inFirewall Analyzer helps you to monitor the overuse or misuse of company bandwidth. Apart from this,you also get user-level reports on:
- Internet sites accessed by the employees in your network.
- Protocols used for communication.
- Web usage details and trends.
- Employee internet transactions that led to an attack.
- Alarm notifications on restricted site accesses or attempts.
- Rules used by the employees and their usage pattern.
- Live internet bandwidth graphs with details of inbound and outbound traffic flows.
- Alarm notifications on traffic and security anomalies.
User activity monitoring reports not only help track user behavior, but also help identify internal threats in the network.
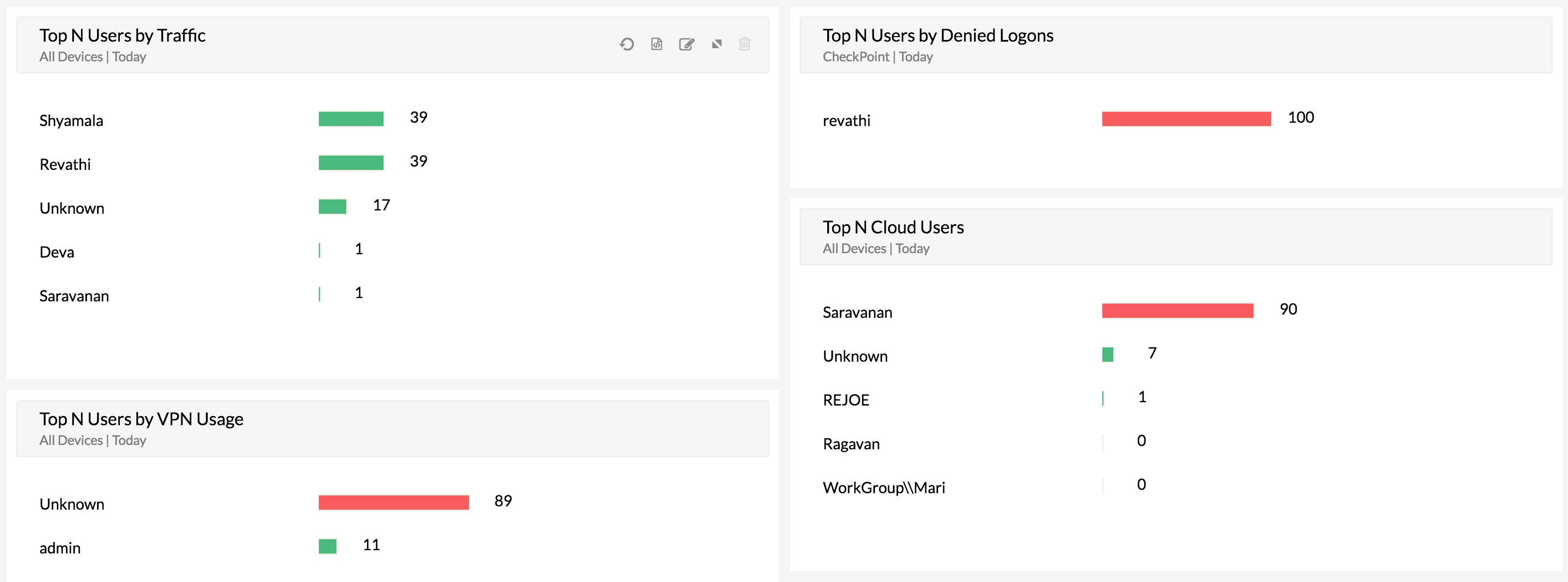
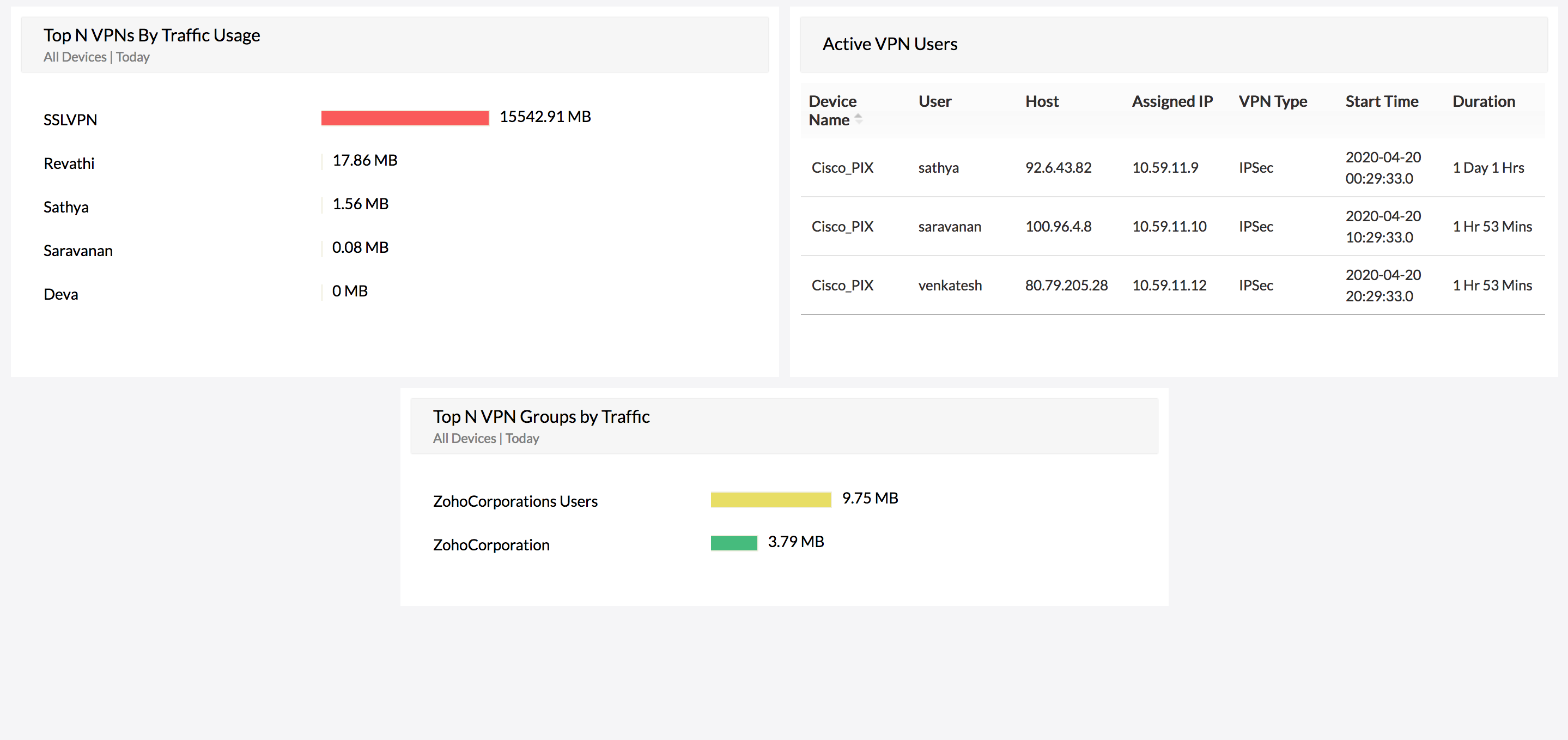
VPN activity monitoring
Firewall Analyzer (User Activity Monitoring Software) can monitor user sessions for both site-to-site virtual private network (VPN) and remote access VPN connections. With details on user session length, bandwidth usage, VPN device, and VPN type, you can closely monitor VPN users for bandwidth anomalies.
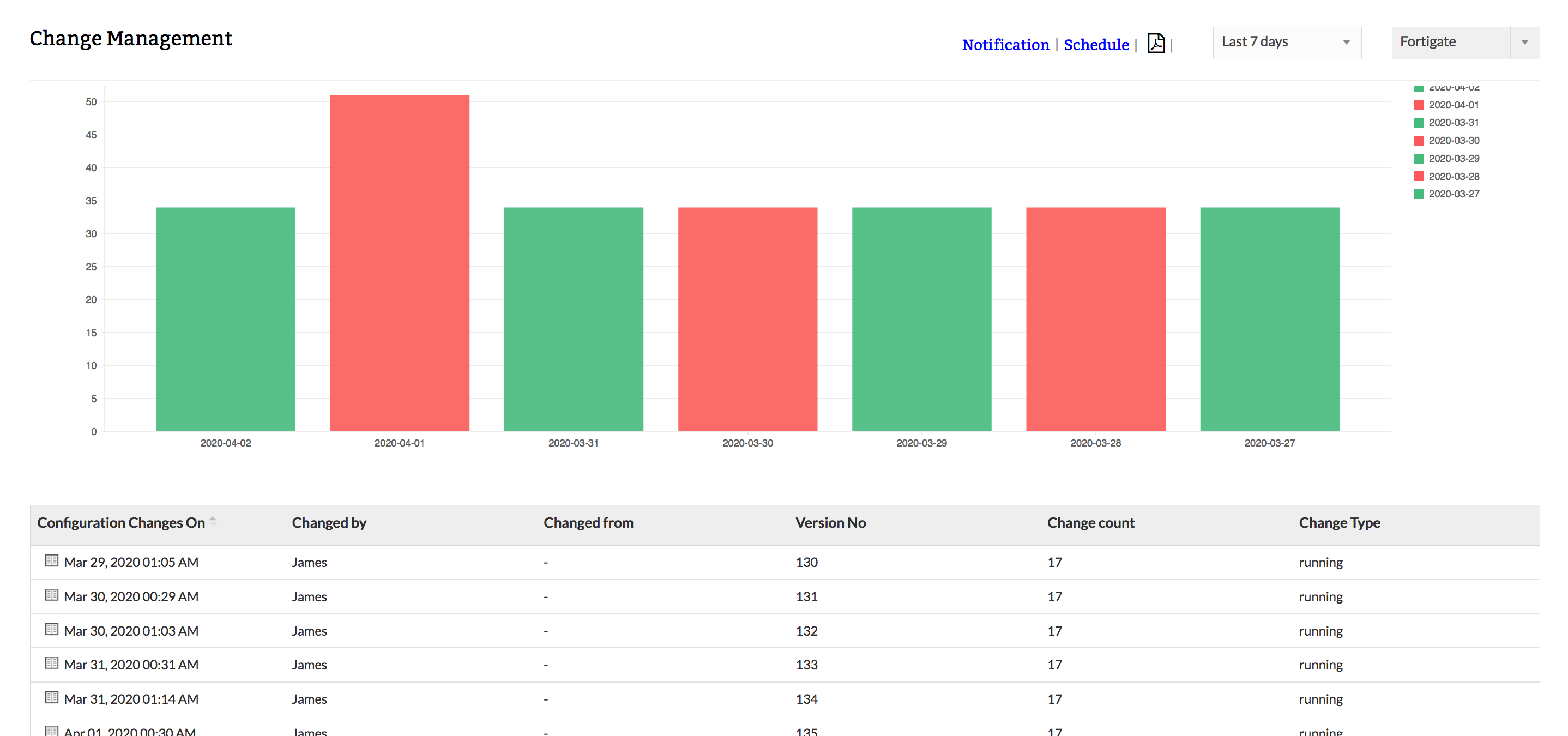
User configuration monitoring
Firewall Analyzer (User Activity Monitor) fetches the firewall configuration using the command-line interface (CLI) or application programming interface (API) from your firewall devices,and enables you to keep an eye on the changes being made to the network security infrastructure by a specific user. Firewall Analyzer's configuration change management reports precisely identify who made what changes to the firewall configuration, and when and why.
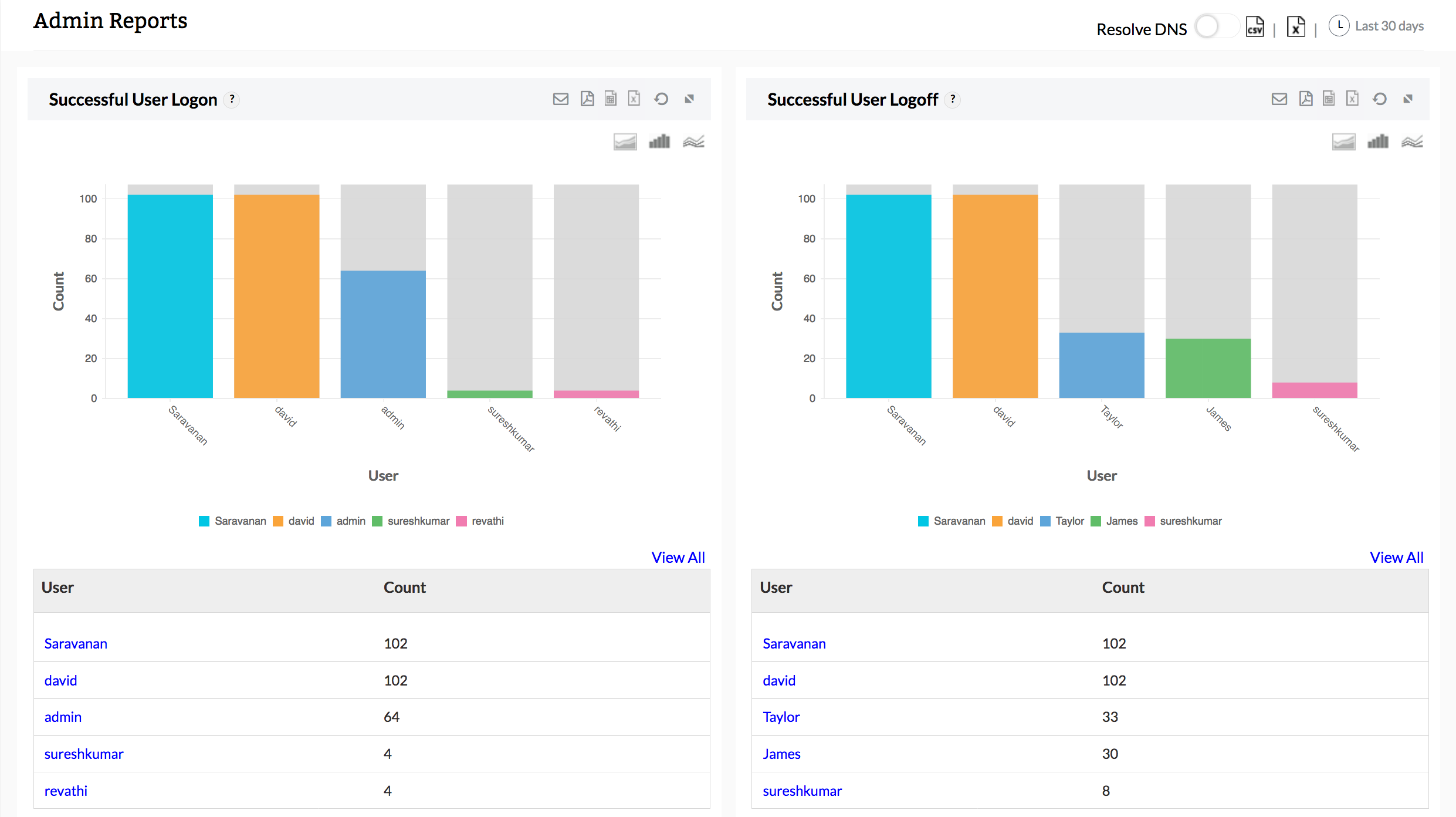
Firewall user credential activity monitoring
Firewall Analyzer (User Activities Monitoring) provides prebuilt Admin Reports, which provide information on user-level access and commands executed by a specific user on the firewall (User Activity Management). Apart from this, Firewall Analyzer also keeps track of user-level changes to the settings and firewall policies.
With these detailed reports, you can easily monitor user activities from end-to-end. Download a free, 30-day trial of Firewall Analyzer (User Activity Monitoring Software) and secure your network.
Thank you for your feedback!

