Firewall Policy & Rule Optimization
Firewall policies are the heart of network security and to get the best out of the firewall rules, you need to plan extensively and optimize your firewall rules periodically. Firewall Analzyer is firewall policy planning and optimization tool which helps in the following.
- Identify and rectify policy anomalies
- Reduce overly permissive rules
- Fine tune the existing firewall policies
The below given reports help deliver the policy planning and optimization capabilities of Firewall Analyzer.
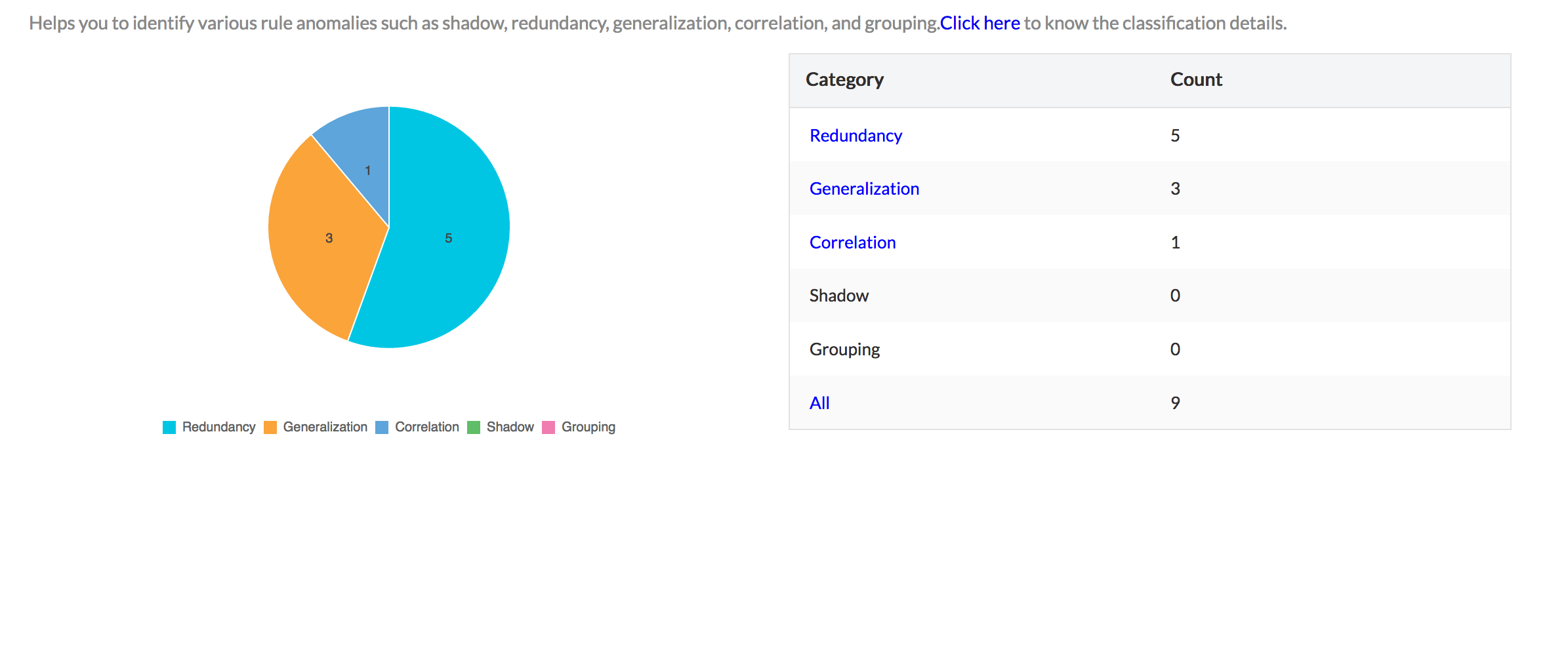
Firewall Policy Optimization Report
Firewall policy anomaly reporting allows security professionals to identify and rectify anomalies in their firewall policies and thereby secure their networks from external IT attacks. These reports empower security administrators to optimize policies (Firewall rule management) and plug all security holes as well as optimize the performance of their firewalls. Firewall Analyzer offers an exhaustive set of Firewall policy optimization reports. The anomaly reports are:
- Correlation
- Generalization
- Redundancy
- Shadow
- Grouping
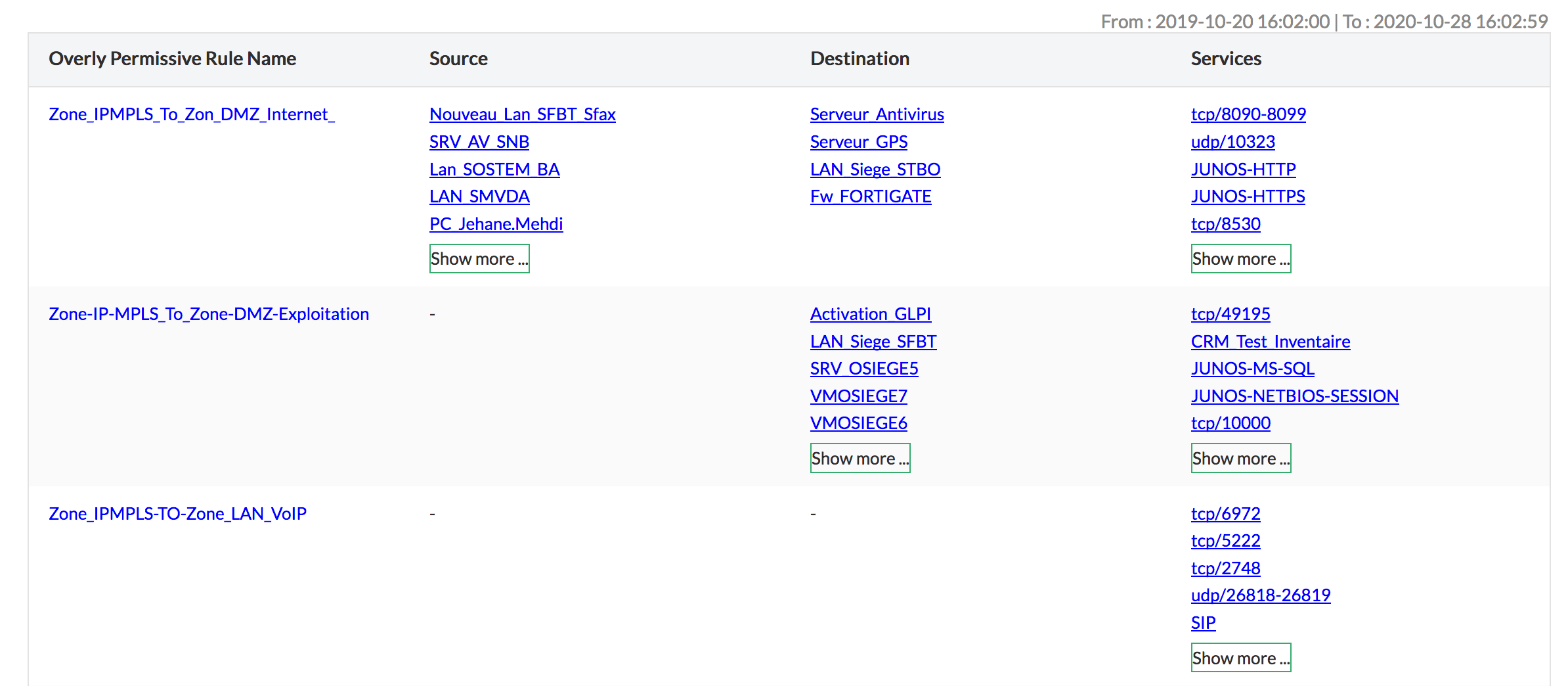
Firewall Rule Suggestion Report
A smart firewall policy strategy requires a reduced use of overly permissive rules as these rules can be exploited by hackers to get into the network. Firewall Analyzer does not only identify overly permissive rules, but also suggests how to reduce these rules.
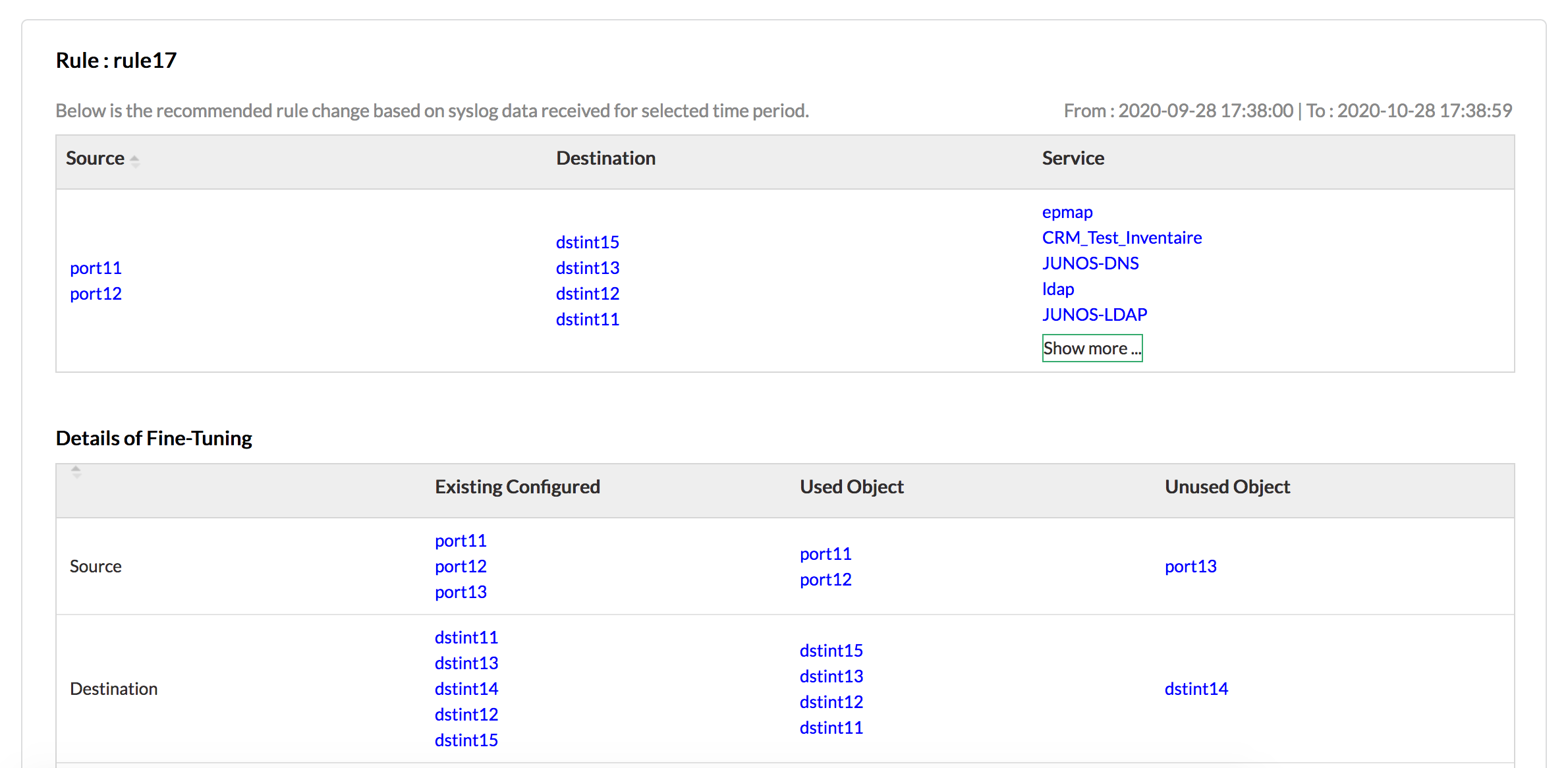
Firewall Policy Fine Tuning Report
Similar to overly permissive rules, any rule which is linked to "Any" or "All" services poses a threat to the network. Firewall Analyzer can identify these permissive services for a specific rule and also suggest appropriate changes to the rule. With this report you also get a list of used and unused objects linked to a specific rule, thus you can easily plan firewall policies and fine tune your rules by removing the unused objects.
With these network security policy reports, security administrators can efficiently plan and configure firewall rules. Download a free trial of Firewall Analyzer, optimize your firewall policies and secure your network.
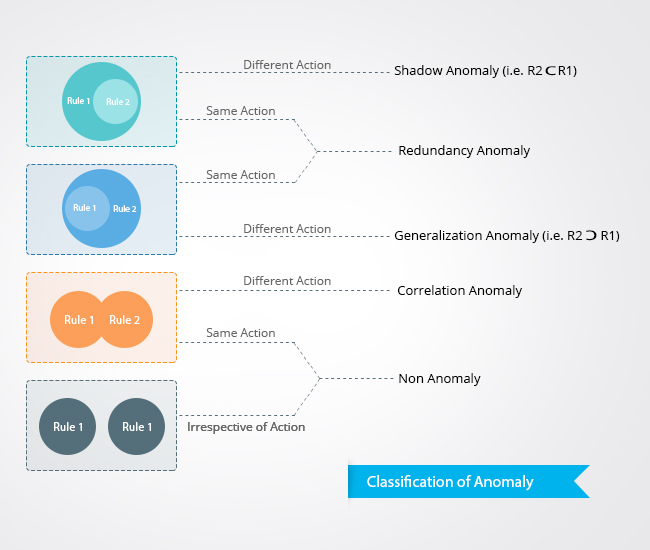
Classification of firewall policy anomalies
Firewall policy anomalies can be classified as shown in the diagram below:
Apart from the above mentioned anomalies, Firewall rules optimization report also provides 'Grouping' anomaly report. Refer to the Configure Firewall Rules page to know how to configure firewall rules.
Featured links
Firewall Reports
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!