Virus Proxy Reports
Firewalls capture the viruses with signature and records in the logs. Same way proxy servers also capture the viruses with signature and mentions in the logs. Firewall Analyzer analyzes the proxy server logs and generates virus proxy reports. With these virus proxy reports, you have a secondary mode of detecting the virus attacks and initiate remedial action.
How does Firewall Analyzer help in identifying and removing proxy viruses?
Firewall Analyzer periodically collects syslogs of proxy servers. Its internal log processing engine comes with a built-in parser to identify proxy viruses for select vendors. Firewall Analyzer generates two types of reports:
1. A bar graph which shows the type of proxy virus along with the number of hits.
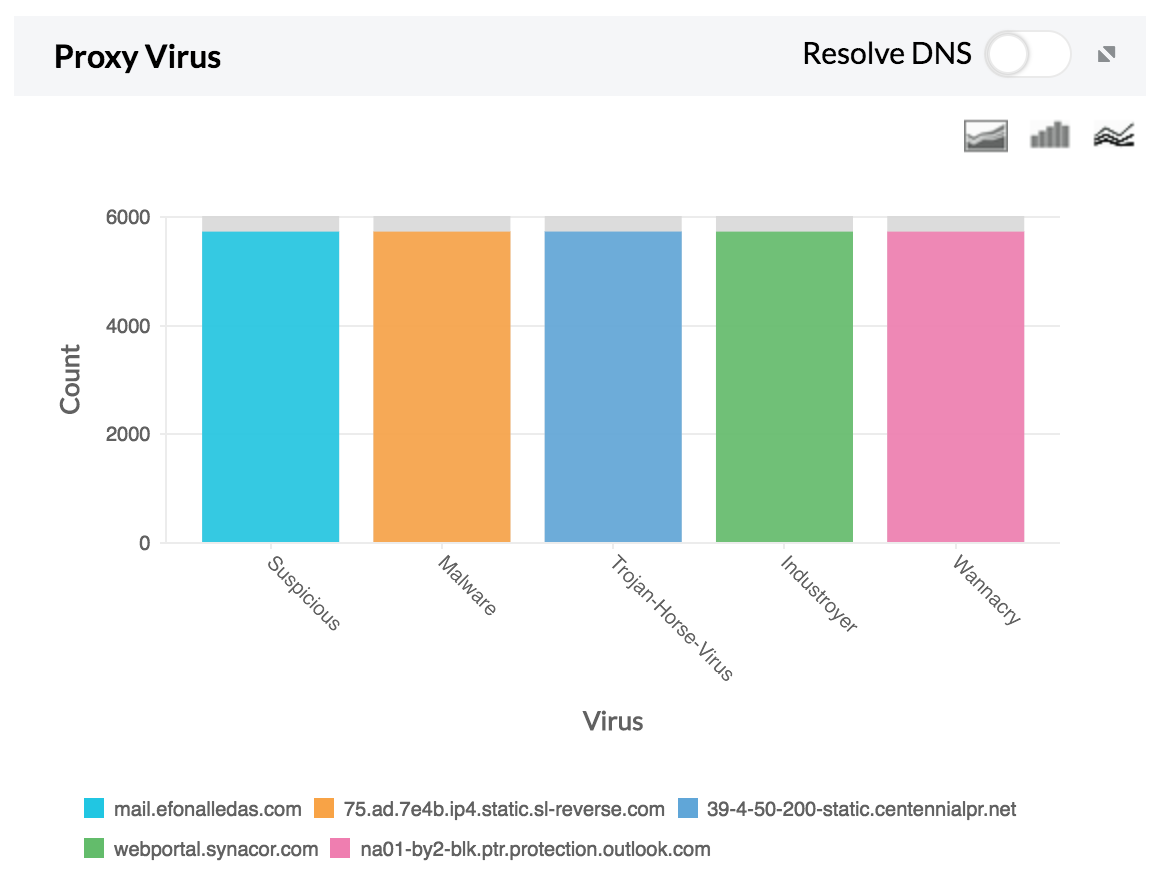
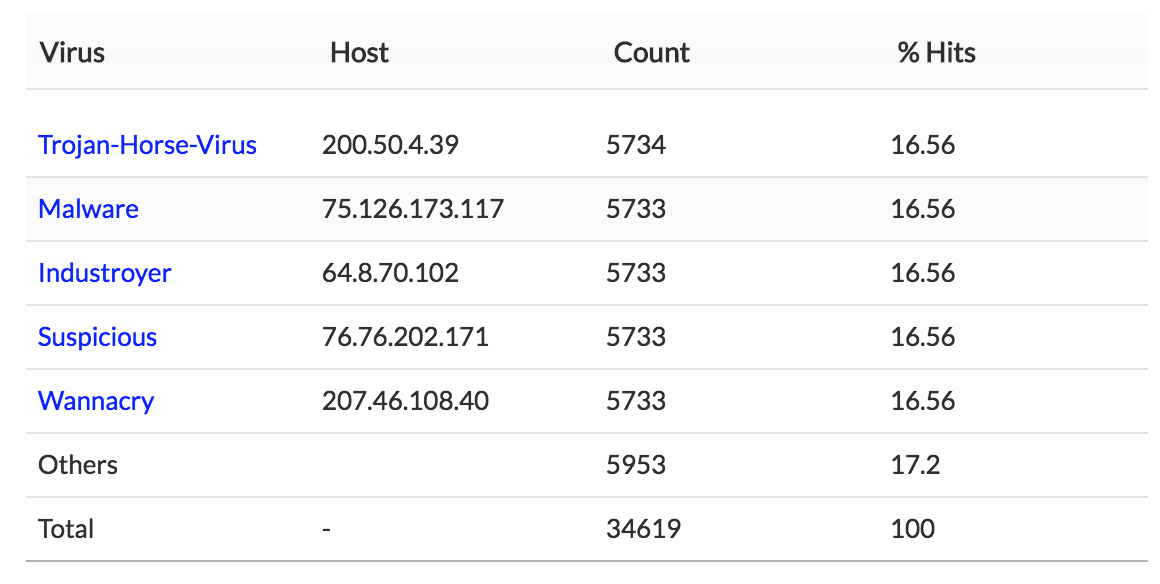
2. A table which provides the type of virus, host IP, number of hits, and percentage of hits.
Drill down on either of these reports to get a detailed view of the following fields: host IP, destination IP, status, protocol, and time.
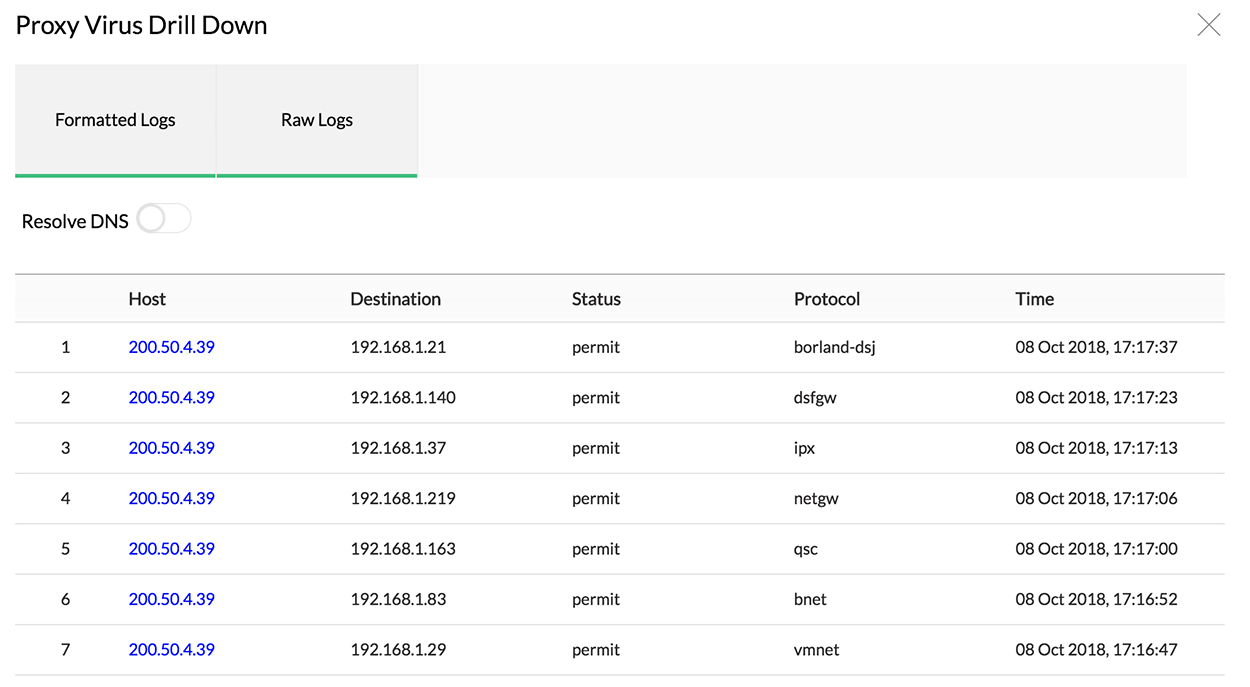
Having analyzed the data, security admins can detect malicious proxy virus hosts and block them in the individual proxy server. Admins can also detect the infected IPs and plan for a clean up on those devices.
Proxy virus
Proxy servers act as intermediaries between the company's network and the internet. When a host computer connected to a proxy server is infected by a proxy virus, the proxy virus can take over the proxy server and act as a proxy bot. Attackers can use these bots to stage anonymous attacks on networks. The whole point of a proxy virus is to breach a network by hiding behind a proxy server; the proxy bots make it look as though the attack is coming from multiple directions, making it harder to identify the true origin of the attack.
How does a proxy virus affect your network?
Similar to other viruses, the proxy virus disguises itself as a genuine software download or attachment, or piggybacks on a legitimate download or attachment. This virus gives attackers a chance to perform malicious activities such as credit card fraud, hacking, and other illegal activities with little risk of repercussion, since the true location of the attacker is masked. Aside from that, proxy viruses can collect information from the host computer and send it to the attacker.
Featured links
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!