Firmware Vulnerability DB sync
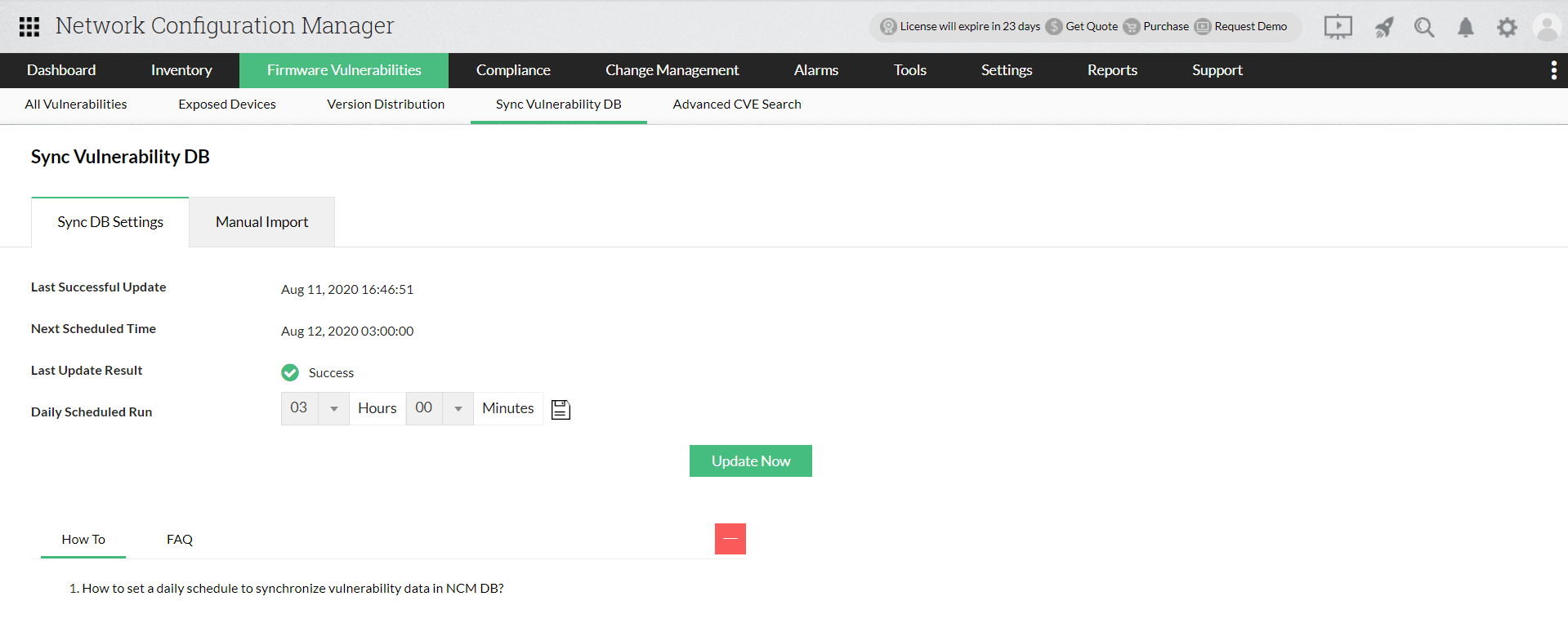
Firmware vulnerability data from NIST vulnerability management can be synced with the DB of Network Configuration Manager. Users can set a time of schedule in order to sync data on a daily basis. When a schedule time is set, the synchronization of vulnerability data happens automatically at the exact time of schedule. Network Configuration Manager also allows you to edit/change the time of schedule as per your convenience. If no schedule time is set, sync happens every night at 2 a.m by default.
Note: For firmware vulnerability sync, we get data from Network Configuration Manager's ManageEngine database: https://ncm.nimbuspop.com. Customers must allow access to the domains "https://ncm.nimbuspop.com" and "https://www.manageengine.com" from NCM installed server in order to retrieve the data.
If you wish to update the Vulnerability data in the NCM UI immediately instead of the scheduled time, you can give the "Update Now" option. When "Update Now" is given, the latest firmware security vulnerability data will be updated in the Network Configuration Manager's DB.
Vulnerability DB sync for closed networks
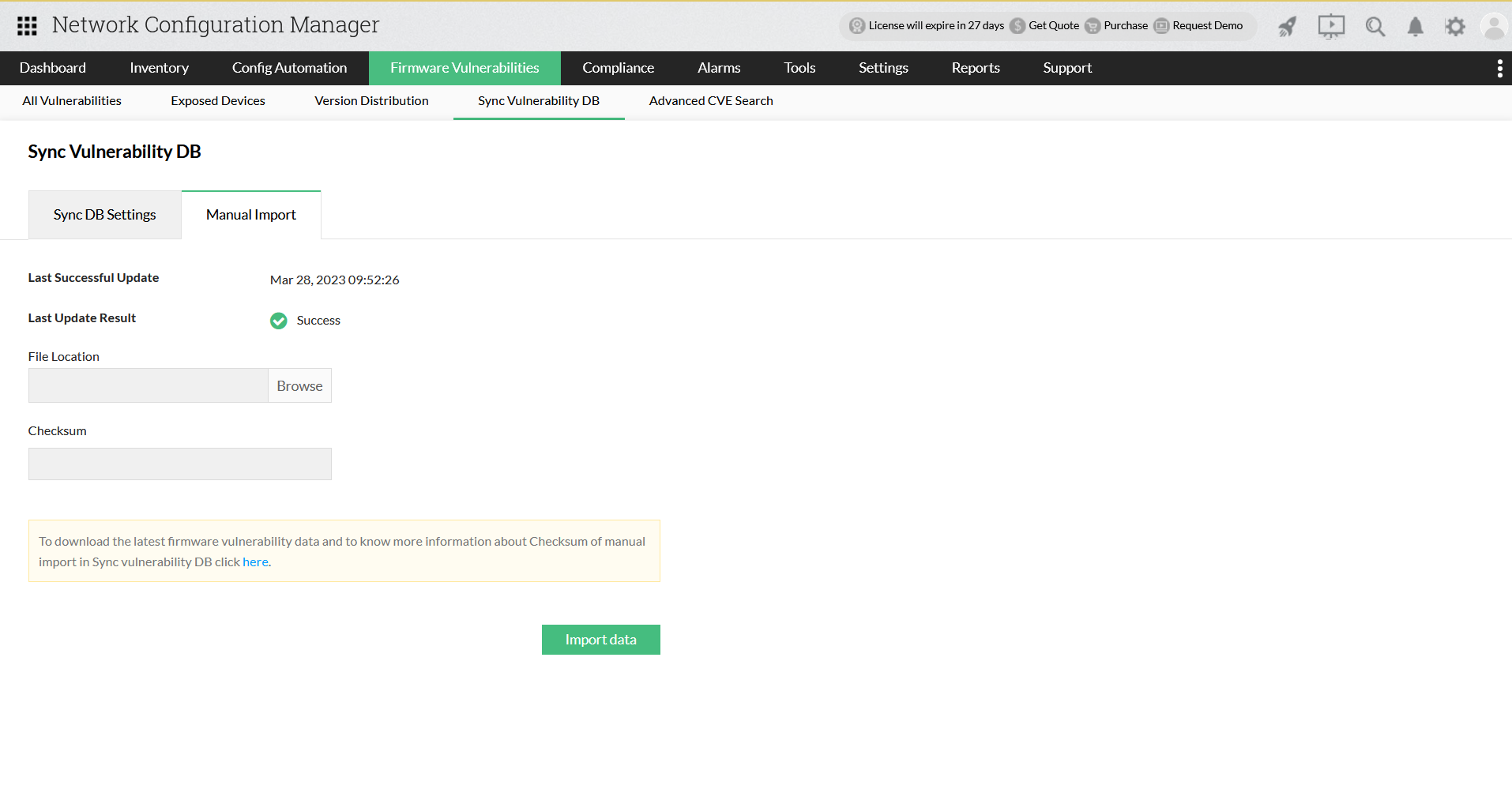
If your network is closed, you will not be able to update vulnerability database automatically using firmware vulnerability scanning with data from NIST vulnerability management. In that case, you can go for a manual import of vulnerability data.
- A "Checksum" feature has been developed to verify the file's authenticity and integrity. Please enter the checksum given below in the input box provided in Network Configuration Manager's UI.
- Import the downloaded file. Once you import the new file, the previous dump will be deleted and replaced with the latest data.
Note: Modification of the imported dump by the customer may lead to corruption of vulnerability dump present in Network Configuration Manager.
Thank you for your feedback!