Vulnerability Reports
Your organization needs continuous access to devices' vulnerable information so that review and decision-making can be improved and any outside threats can be avoided. Vulnerability reports in Network Configuration Manager serve this purpose by presenting comprehensive data about the devices' firmware vulnerability status. This report provides various levels of vulnerability data within your network, helping you understand where the faults are and what needs to be rectified for better device security.
Whenever network downtime occurs, admins typically look for a configuration change as well as if any device is susceptible to firmware attack. In cases like this, vulnerability reports would present the full picture of all the devices that are present on the network along with their vulnerability levels. Moreover, admins should be able to track in real time all the devices' vulnerability levels. In the absence of vulnerability reports, such tasks become tedious, if not impossible. Within Vulnerability Reports, Network Configuration Manager offers a range of specific reports.
Types of vulnerability reports
- CVE ID Report
- Exposed Devices Report
- Firmware versions with vulnerabilities report
- Vulnerability Fix Trend Report
- Device Vulnerability History Report
All these reports present a quick summary of the devices' vulnerability status.
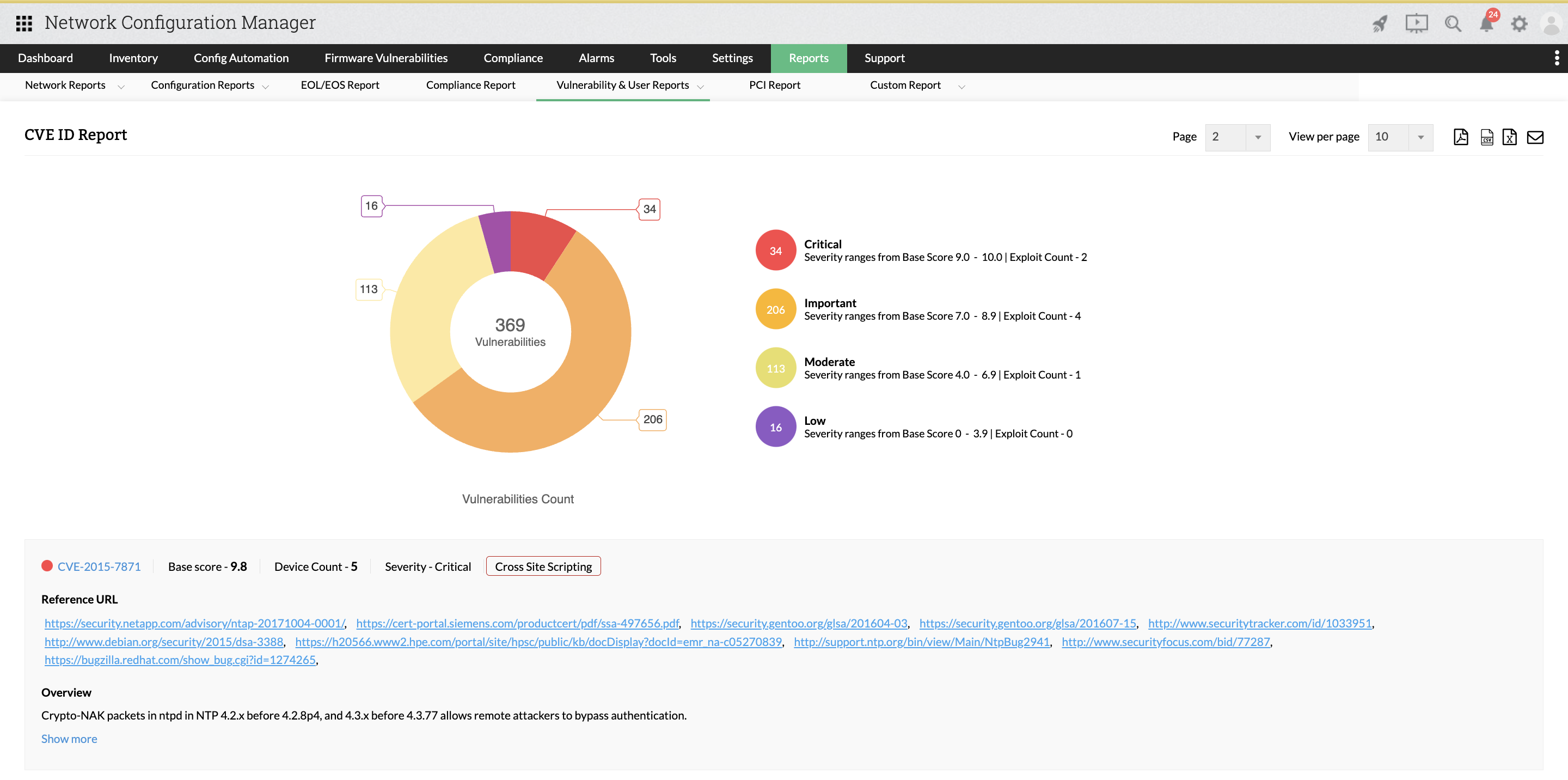
CVE ID Report
The results of the vulnerability scanning report are presented in this report. Firmware vulnerability report also contains information about a number of vulnerabilities present in the network and severity wise grouped data.
Also, in-depth information of each CVE including base score, summary, and reference URL along with published and updated time will be present.
To access this report, navigate to Reports -> Locate and click CVE ID Report within the Vulnerability & User Reports section.
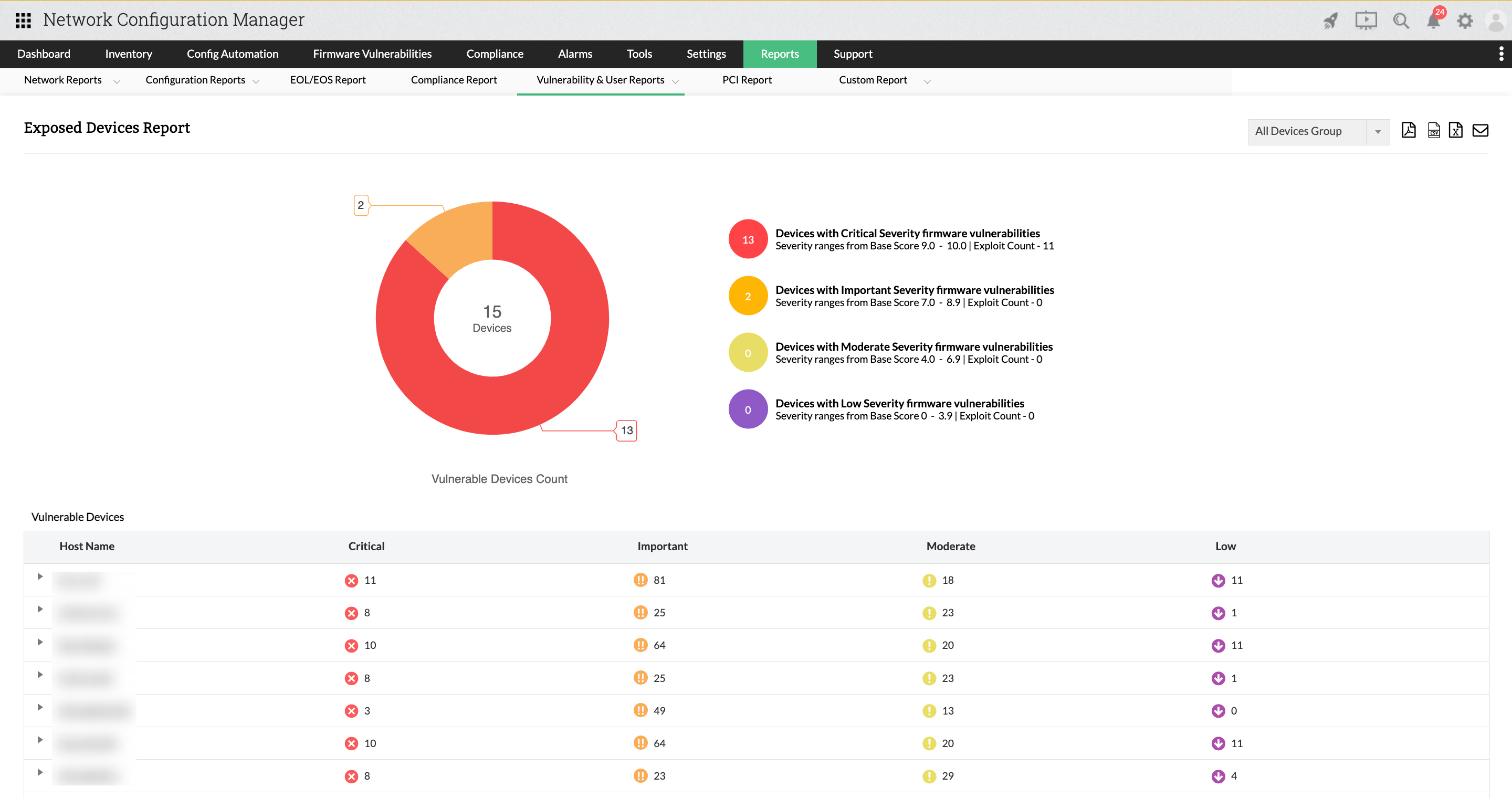
Exposed Devices Report
This report contains information about a number of exposed devices present in the network. Report is based on the exposed devices in Network Configuration Manager.
Vulnerabilities of each devices will be shown. Also, by expanding, you get the devices' complete information with CVE ID. The top most vulnerability level of the device is taken as its severity level. For example, if critical is the latest severity of the device, then that will be taken as that device's severity.
To access this report, navigate to Reports -> Locate and click Exposed Devices Report within the Vulnerability & User Reports section.
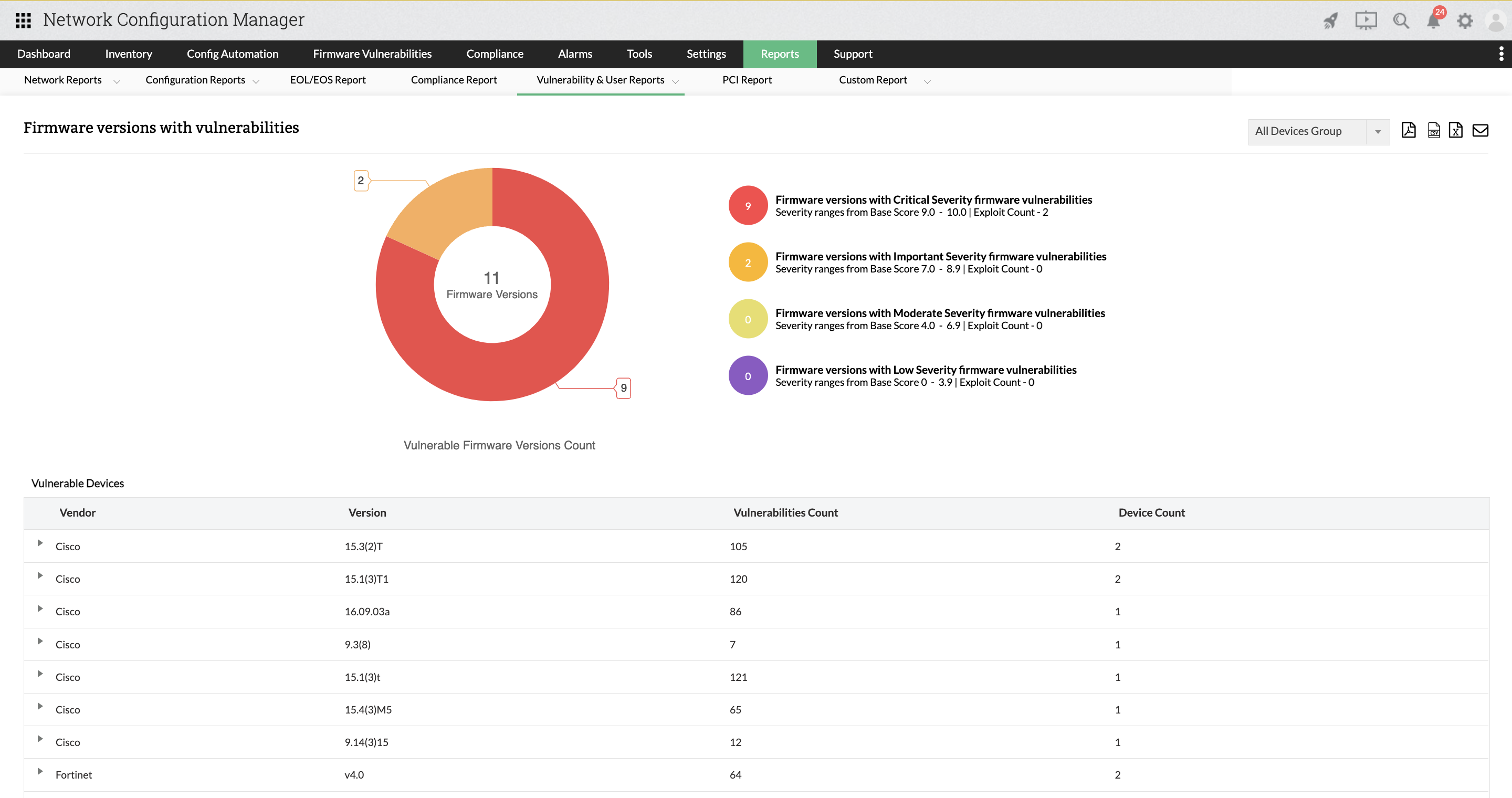
Firmware versions with vulnerabilities
This report contains information about firmware versions affected with vulnerabilities. Report is grouped by firmware versions of vulnerable devices available in Network Configuration Manager.
Vulnerabilities of each devices will be shown. Also, by expanding, you get the devices' complete information with CVE ID. The top most vulnerability level of the firmware version is taken as its severity level. For example, if moderate is the latest severity of the firwmware version, that that will be taken as that firmware version's severity.
To access this report, navigate to Reports -> Locate and click Firmware versions with vulnerabilities Report within the Vulnerability & User Reports section.
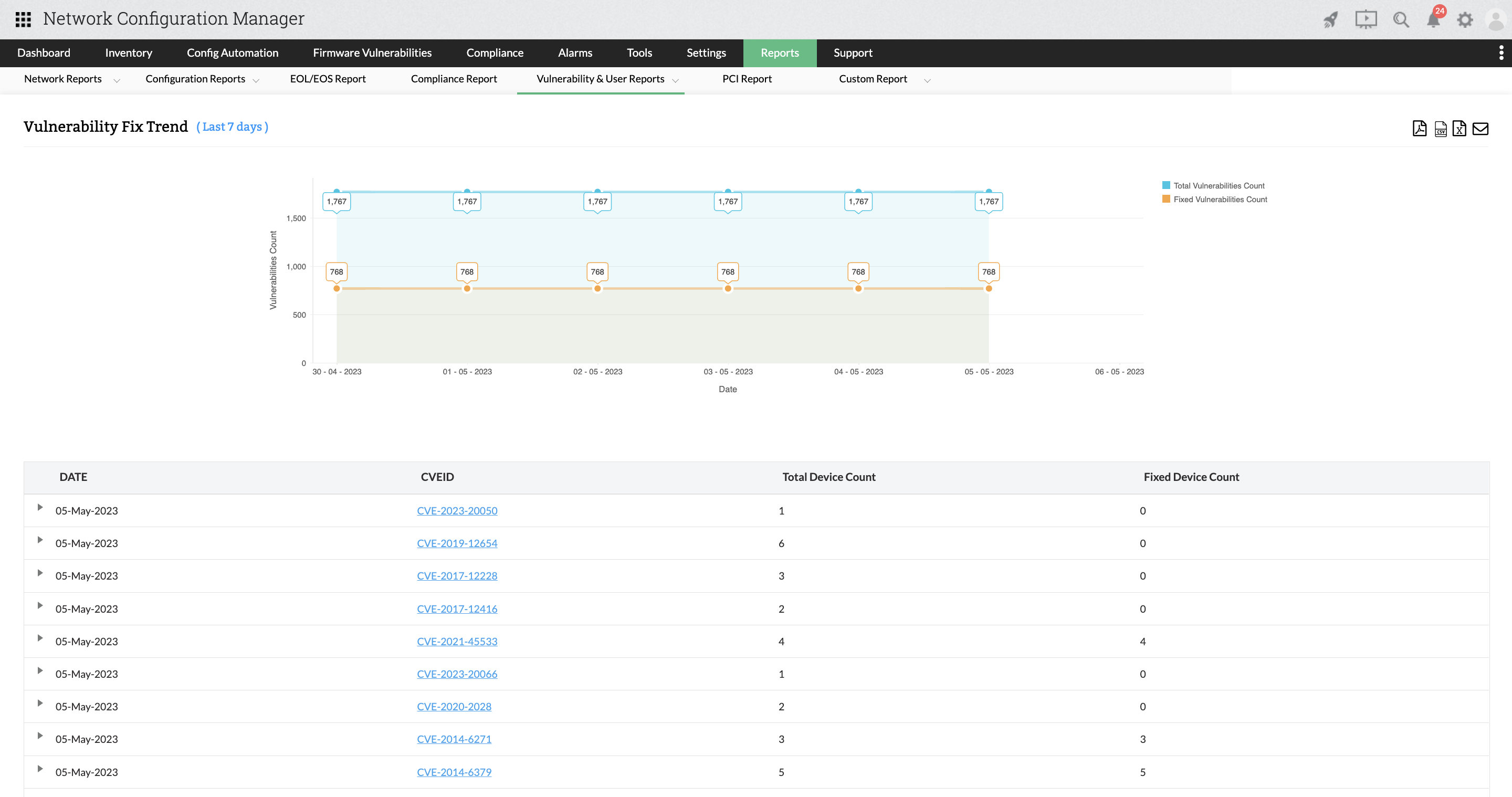
Vulnerability Fix Trend Report
This report provides a trend graph on total vulnerabilities in a day and how many are fixed in that day. It also lists a tabular column which contains the date, the CVE ID, total number of devices with vulnerability, and number of devices vulnerability has been fixed.
This report can be exported as PDF, CSV, Excel, or as email.
Note: If the vulnerability state is marked as resolved or not applicable, it will be considered as the vulnerability is fixed.
To access this report, navigate to Reports -> Locate and click Vulnerability Fix Trend Report within the Vulnerability & User Reports section.
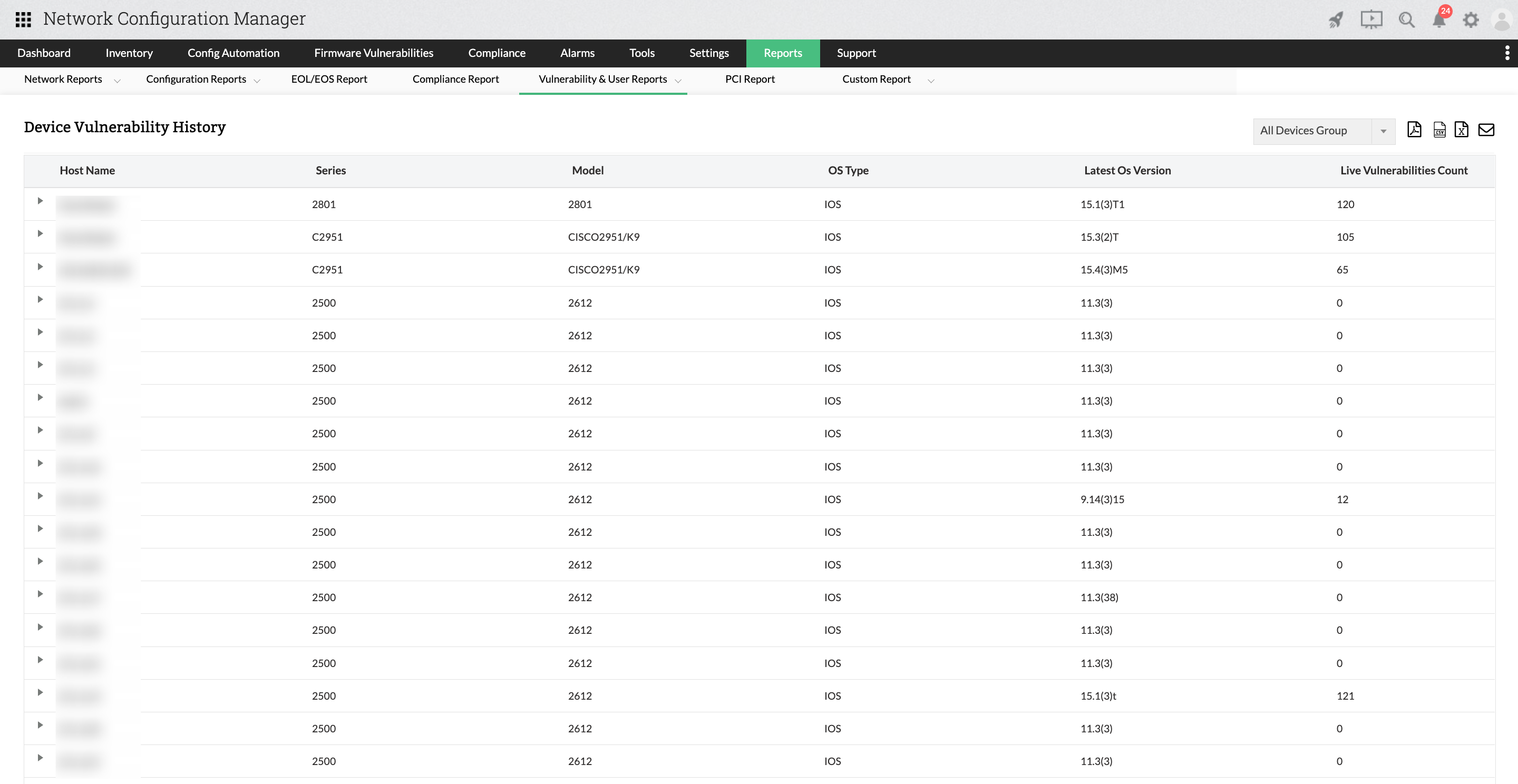
Device Vulnerability History Report
This report lists the history of the devices that had a vulnerability of any kind. The tabular column consists of host name, series, model, OS type, latest OS version, and the count of live vulnerabilities present in a device.
This report can be exported as PDF, CSV, Excel, or as email.
To access this report, navigate to Reports -> Locate and click Device Vulnerability History Report within the Vulnerability & User Reports section.
Download Network Configuration Manager now and enjoy these and various other kinds of reports and audits with a free, 30-day trail.
Want to see the solution in action? Request a free, personalized demo.
You can also get a price quote based on your usage and needs.