Frequently Asked Questions
Network Configuration Management, Network Change & Configuration Management Software, Network Device Management, Configure Switches, Routers, Firewalls & Other Network Devices
- General Product Information
- Logging in to the Web Interface
- Inventory (Devices)
- Discovery (New Version)
- Discovery
- Credential
- Credential Rule
- Backup
- SysObjectID
- Device Template
- Device Template (New)
- Inventory & Change Detection
- Label Configurations
- Scheduling
- Configlets
- Configlet Group
- Programmable Configlets
- NCM Regex
- REST Configlets
- Firmware Vulnerability Management
- Syslog Blocked Host
- Exclude Criteria
- NCM Terminal Tool
- Export Configuration
- Third Party Syslog Server
- Database Administrator
- Password Management - PMP
- Password Management - PAM360
- System Details
- Upload Request
- Change Notifications
- Compliance Policies
- Device Group
- Reports
- Advanced Reports
- Security Aspects
- Miscellaneous
General Product Information
What is ManageEngine Network Configuration Manager?
ManageEngine Network Configuration Manager is a comprehensive Network Change and Configuration Management (NCCM) solution that enables the Network Administrator to efficiently and effortlessly manage the configurations of Network Devices. Network Configuration Manager offers multi-vendor network device configuration, continuous monitoring of configuration changes, notifications on respective changes, detailed operation audit and trails, examining device configurations for compliance to a defined set of policies and standards, real-time compliance status reporting, easy and safe recovery to trusted configurations, automation of configuration tasks and insightful reporting. For more details, click here.
What does Network Configuration Manager do?
Network Configuration Manager can manage network devices such as switches, routers, firewalls wireless access points and integrated access devices etc. from multiple vendors such as Cisco, HP, Nortel, Force10, D-Link, Juniper, NetScreen, Juniper, NETGEAR, Dell, 3Com, Foundry, Fortinet, ADTRAN, Enterasys, Huawei, Extreme, Proxim, Aruba and Blue Coat. It discovers network devices, builds up an inventory database and allows IT administrators to take control of configuring the devices from a central console. The web-based administrator console provides the User Interface to perform all the configuration operations. Additionally, it can be accessed from anywhere using any standard web browser.
How does Network Configuration Manager work?
Network Configuration Manager will establish SSH / Telnet connection by using IP address and credentials provided. After that, commands like "show running-config" is executed in device to fetch configuration. If TFTP / SCP protocol is used, configuration will be pushed to TFTP / SCP server after establishing connection with device. Later, it will be dumped in our database after encryption.
Can Network Configuration Manager manage Cisco device configurations?
Yes, Network Configuration Manager can manage Cisco device configurations. Cisco router configuration, Cisco switch configuration and Cisco firewall configuration can be done using Network Configuration Manager. Apart from Cisco devices, Network Configuration Manager can be used to manage the configurations of switches, routers, firewalls, wireless access points and integrated access devices from other vendors such as HP, 3com, Foundry, FortiGate and NetScreen.
Can Network Configuration Manager be used to manage router configuration / switch configuration / firewall configuration?
Yes, Network Configuration Manager can be used to manage router configuration, switch configuration and firewall configuration from multiple vendors such as Cisco, HP, 3Com, Foundry, FortiGate and NetScreen.
What are the devices supported by Network Configuration Manager?
Network Configuration Manager at present supports switches, routers, firewalls, wireless access points and integrated access devices. For new device support, send your request.
What are the vendors supported by Network Configuration Manager?
Network Configuration Manager at present supports Cisco, HP, Nortel, Force10, D-Link, Juniper, NetScreen, Juniper, NETGEAR, Dell, 3Com, Foundry, Fortinet, ADTRAN, Enterasys, Huawei, Extreme, Proxim, Aruba and Blue Coat. For new vendor support, send your request.
Is Network Configuration Manager available for evaluation or direct purchasing?
Network Configuration Manager is available for both evaluation and direct purchase. Please contact our sales team at +1-888-720-9500 or email sales@manageengine.com
Do I need any prerequisite software to be installed before using Network Configuration Manager?
There is no prerequisite software installation required to use Network Configuration Manager. MySQL, TFTP server and Syslog server are bundled with the product itself. If you want to received change management notifications via email, you need to configure an external SMTP server (optional).
What is the Licensing Policy for Network Configuration Manager?
Professional Evaluation Edition download valid for 30 days, capable of supporting a maximum of 50 devices. Free support would be offered during evaluation.
Professional Edition - Licensing based on the number of devices support needed. Priority support would be offered. For more information / to get license, contact sales@manageengine.com
Free Edition - download valid for ever, capable for supporting a maximum of two devices.
Do I have to reinstall Network Configuration Manager when moving to the Professional Edition?
No. You need not have to reinstall or shut down the server. You just need to enter the new license file in the "Register" link present in the top right corner of the Network Configuration Manager web interface.
What are the browser versions supported by Network Configuration Manager?
Web Interface requires one of the following browsers** to be installed in the system:
- IE 7 and above (on Windows)
- Firefox 2.0 and above (on Windows and Linux)
** Network Configuration Manager is optimized for 1024 x 768 resolution and above
What are the System Configuration Requirements for Network Configuration Manager?
Refer to the information available in the System Requirements section.
What is network backup ?
Network backup is a process of saving your existing configuration files of network switches, routers, firewalls and load balancers.
What does network backup software do in NCM?
NCM will backup configuration files of network devices like switches, routers, firewalls and load balancers. Also it will create a repository with all versions stored in incremental versions.
Why network backup software is important?
If any network device goes down in our network, we can use NCM tool to recover the well known configuration version from repository and it can be uploaded to device to make it live.
How to backup network?
- Go to "Inventory" >> "Devices" >> Select the device or devices whose configuration has to be backedup
- Click on More actions >> Select "Backup" from the drop-down
- Once backup is over, the status will be marked as "Backedup" with a green mark. If the operation fails, a red mark is displayed.
What is network automation?
Network automation is way of automating networks and security in a network environment to maximize efficiency by reducing human workload along with human errors.
Why is network automation important?
Network automation enables seamless configuration, management, testing, and deployment of network changes and other IT operations. It improves the efficiency of your network admin team and helps ensure that your network is responsive to business needs.
What are the benefits of network automation?
- Reduced costs
- Reduced errors
- Improve service levels
- Improved analytics
- Admin efficiency
- Increased business agility
How does network automation work?
Network automation works via a medium or tool called as network automation tool. It automates all the critical tasks so that there is no need of human intervention at all. This also gives another advantage where you can efficiently finish the task without any human errors.
Logging in to the Web Interface
I forgot the password to login to Web Interface
You can a get a new password for an account using the Login Name and Email Id of that account (the Email id should match with the one that was configured for the user earlier)
- Click 'Forgot Password?' link in the login screen
- Provide the Login Name in the text filed
- Provide the Email Id configured for the service
- The password will be mailed to your mail account
- Use that auto generated password for logging into the service which you can choose to change later on
How do I change the password of my login account?
Login to the Network Configuration Manager Web Interface
Users with admin privileges can change their Login Password through the 'Edit Account Settings' functionality of "Admin" Tab. Ordinary users (that is, users who do not have admin privileges) can change their Login Password through the 'Edit Account Settings' functionality present in left-hand side of "Home" Page.
To Change Login Password,
- click "Admin" tab >> "Change Password "
- enter the old password
- enter new password
- confirm the new password
- click "Save"
- password is now reset
Inventory (Devices)
What is Config Conflict and how to resolve it?
- Please select one or more devices from the list in Inventory.
- Click on the 3 horizontal dots
 on the top right corner of the page to get more options.
on the top right corner of the page to get more options. - Click on "Sync Configuration".
What is Compliance Status?
A set of rules can be defined for the configuration of any device. These rules can be anything like, a particular keyword or line(s), must or must not be present in a particular configuration. One or more of these rules can be combined into a Compliance policy and then these policies can be associated with a particular device or a group of devices. If any particular device configuration is violating the associated rules, Network Configuration Manager will show a compliance violation for that particular device. To resolve the compliance status, please change the device configuration accordingly. Alternatively, if any remediation configlet is associated with the said rule, you can choose to execute that to make the required changes to the configuration automatically.
What is Baseline Conflict and How to resolve it?
- Click on the device that has the baseline-running conflict.This will open the device details page.
- Check the Current Version and the Baseline version in front of Running Config header.
- Click on the "Current Version" to see the configuration details.
- In configuration details page click the More Option Icon
- Click on "Set as Baseline". This will change the status back to "In Sync".
Unlike Startup Running conflict, there won't be any major impact if the Baseline Running conflict is ignored. Baseline configurations are just the well-known labelled configuration. The conflict status shows you the changes made from that well-known configuration till date. If you consider your current running configuration as well set and want to save it as baseline you can choose to do that. Please click here to see how to do that.
 is grayed in the device list?
is grayed in the device list? Credential icon  in device list indicates whether the credentials for a particular device are provided or not. So if the credential icon is grayed out, it means there are no credential associated with the device and you won't be able to take the backup of the device. To know more on how to provide credential to a device, please click here
in device list indicates whether the credentials for a particular device are provided or not. So if the credential icon is grayed out, it means there are no credential associated with the device and you won't be able to take the backup of the device. To know more on how to provide credential to a device, please click here
Yes, the same set of credentials can be provided to any number of devices. Please click here to see how to provide credentials to a set of devices at a time. You can also choose to create a device group with a set of devices and then apply the credential to that group from Device Group page in inventory. Also if you find yourself using the same credentials multiple times, please save those credentials as a credential profile, and next time while applying the credential just select the profile and Network Configuration Manager will fill all the necessary details.
If a device is in the unmanaged state, you won't be able to perform any important operations like Configuration Backup, Upload Config, Automatic Change Detection, Sync Configuration, Compliance Management or Change Management etc. Any schedule that contains the unmanaged device won't perform the scheduled task for the said device, even if the schedule was created when the device was in the managed state.
Yes you can use either a SSH or a Telnet session to connect to a device and run the CLI commands. Please follow the steps given below to open a CLI session with a particular device:
- Click on the device, in Inventory page to open the Device Snapshot
- Click on either the SSH icon
to open SSH session with the device, or the Telnet icon
to open telnet session. These icons can be found in the action menu provided at the top of snapshot page.
- Using either of the icons will open a terminal session in a slide where you can login to the device by providing appropriate credentials.
Yes, a network route can be traced using Network Configuration Manager for any device. Click on the device in the Inventory page for which you want to check the route. This will open up the device snapshot, you can click on the "Trace Route" icon
 icon ?
icon ? By clicking "Browse To" icon
Click on the device from Inventory to open device snapshot. Then click on the "Notification" icon
Click on the device from Inventory to open device snapshot. Then click on the "Alarm" icon
Click on the device from Inventory to open device snapshot. Then click on the "Workfflow" icon
Click on the device from Inventory to open device snapshot. Then click on the "Ping" icon
Show Commands give you the ability to run a few pre-defined commands on a particular device. You can select and execute any command from a given list and check the device's response in a console window. This response can also be exported to a file using the "Export" option provided in the show command slide.
Please follow the steps given below to check the audits for a particular device:
- Click on a device to open the device snapshot with all the device details
- Click on the action button on the top right of snapshot page
- Select "Audit History" from the newly opened list
- This will open up a slide with all the device history in a timeline format.
From version 128100 and above, any devices that have been marked as "Unmanaged" will now be found in the "Inventory -> Unmanaged Devices" tab. From here, you can either manage or delete them as needed.
From the version 128100 and above, due to licensing constraints, any additional or extra devices will be automatically categorized as "Unmanaged" upon applying the license. Any devices that have been marked as "Unmanaged" will now be found in the "Inventory -> Unmanaged Devices" tab. From here, you can either manage or delete them as needed.
Discovery (New Version)
What happens when existing devices are rediscovered?
If a device is already discovered and added to Network Configuration Manager successfully, there won't be any effect if you run the discovery process again and try to discover the same device. Network Configuration Manager will show the device as 'Already Exist in Inventory' in the discovery report.
Why are the reachable devices not added to Network Configuration Manager?
A device will be shown as 'not reachable' in discovery reports and won't be added to Network Configuration Manager in case of the following errors:
- Device is not reachable: Make sure the device is up and running and is reachable via ping.
- SNMP is not enabled: Network Configuration Manager can discover only SNMP enabled devices, so make sure that SNMP is enabled for the device.
- Wrong credentials: Make sure the selected credential profile applies to the device you are trying to discover.
- SysObjectID is not present in Network Configuration Manager: If all the above mentioned criteria's doesn't apply to the device you are trying to discover, then check the list of SysObectID's supported by Network Configuration Manager under Settings > Network Configuration Manager > SysObjectID Finder. Click on Add and provide the device ip address and other required information and click next. Network Configuration Manager will find the SysObjectID for the device and you can assign it to appropriate device template.
You can get more information about adding SysObjectID and their usage here. If you are still having trouble discovering your device(s), please contact Network Configuration Manager support team.
Alternatively, you can add the device(s) manually. To do so, go to Discovery Reports under Settings > Discovery > Discovery Reports and select the failed devices from the respective discovery report and click 'Add to Inventory button'. This will give you the option to select the Device Template and Vendor to add the device. Select the appropriate Vendor and Device Template and add the device(s).
Where can I see the discovery reports or history of all the discoveries done till date?
- Go to Settings > Discovery > Discovery Reports
- In the Discovery Report tab, you will be able to see the list of all the discoveries done till now sorted in descending order starting from recent.
- You can click on any profile to view the details of devices discovered during the discovery.
Where can I view / edit the credential profiles for discovery?
To view/edit any credential profile use the following steps:
- Go to Settings > Discovery > Credentials
- All the available credentials will be displayed under SNMP tab.
- You can click on any of the credential to open the edit wizard.
- You can also delete a particular credential by clicking the bin icon.
Can I choose multiple credential profiles while creating a discovery profile?
Yes, there is no restriction on the number of credential selection, so you can select as many credentials as you like.
Can I choose the devices to be added after they get discovered?
By default, Network Configuration Manager will add all the successfully discovered devices to Inventory automatically. But, you can change this default behavior and choose the device(s), that you wish to add to Inventory after the discovery is complete. Follow the steps given below to change this option and to know more about how to select the devices after discovery:
- Go to Settings > Global Settings > Client / Server Settings
- Uncheck the "Add devices after discovery without user intervention" option. Save the settings.
- Now go to Settings > Discovery > Network Discovery
- Trigger a new discovery. Click here to know more about how to discover your network.
- Once the discovery is triggered you will be redirected to Settings > Discovery > Discovery Reports
- Select the latest report to view the progress.
- Once the discovery is 100% complete, you can choose the devices which you want to add to inventory and click on 'Add to Inventory'.
Discovery
I have my devices listed in a text file. Can I import them to the inventory of Network Configuration Manager?
Network Configuration Manager provides the option to import devices from a text file and add them to the inventory. To import devices from a text file, Network Configuration Manager requires that the entries in the file conform to a specific format. For more details, refer to the section on "Device Addition" in help documentation.
Can I apply same set of credentials to multiple devices as a bulk operation?
Yes. You can apply the same set of credentials 'as they are' to multiple devices. In such cases, to avoid the cumbersome task of entering the credentials for each device separately, Network Configuration Manager offers the flexibility of creating common credentials and sharing the common credentials among multiple devices. This is called as 'Credential Profile'. For more details, click here.
What happens when existing devices are rediscovered?
- Device is not reachable: Make sure the device is up and running and is reachable via ping.
- SNMP is not enabled:Network Configuration Manager can discover only SNMP enabled devices, so make sure that SNMP is enabled for the device.
- Wrong credentials: Make sure the selected credential profile applies to the device you are trying to discover.
- SysObjectID not present in Network Configuration Manager: If all the above mentioned criteria's doesn't apply to the device you are trying to discover, then please check the list of SysObectID's supported by Network Configuration Manager under Settings > Network Configuration Manager > SysObjectID Finder.
- Go to Settings > Discovery > Discovery Reports
- There you can see the list of all the discovery profiles created earlier.
- You can click on any profile to edit it.
- You can also delete the profile by clicking on the bin icon for the respective row.
- Go to Settings > Discovery > Discovery Reports
- Click on the profile you want to reschedule, this will open the edit discovery page, at the bottom of the page, expand the schedule section and edit the parameters as required.
- Click Save to save the changes.
- Go to Settings > Discovery > Credentials
- All the available credentials will be displayed under SNMP tab.
- You can click on any of the credential to open the edit wizard.
- You can also delete a particular credential by clicking the bin icon.
Credential
- It eases the process of applying credentials to multiple devices at a time.
- You can name common credentials, to make them easily identifiable.
- You won't have to provide every single parameter multiple times for devices that are using same credentials.
- If any parameter for accessing multiple devices is changed and all those devices are associated with a single credential profile, then you can simply edit the credential profile instead of changing credentials for each device one by one.
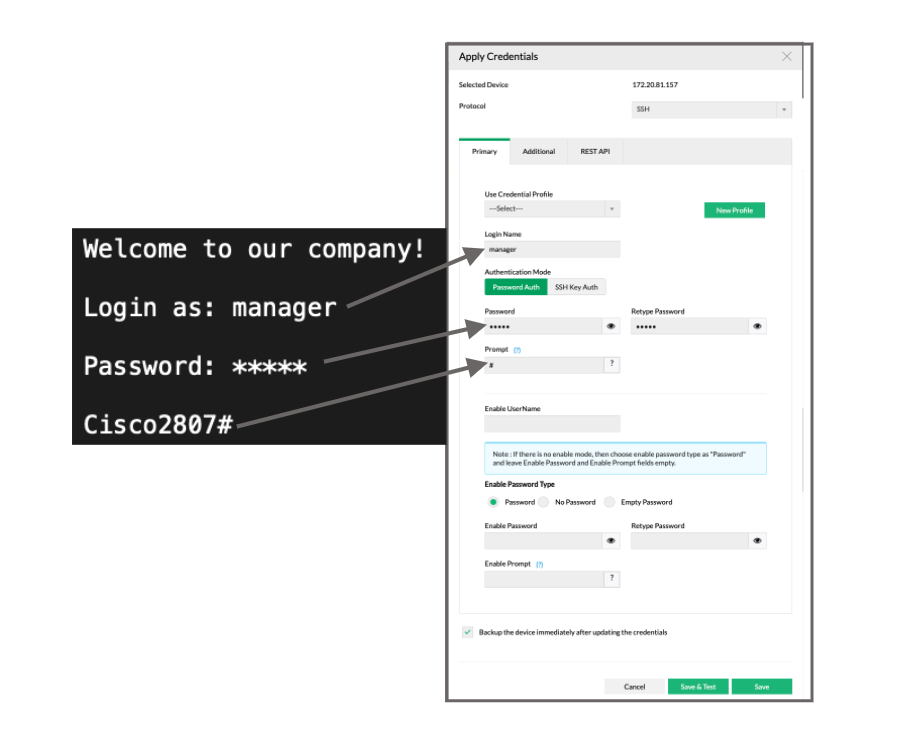
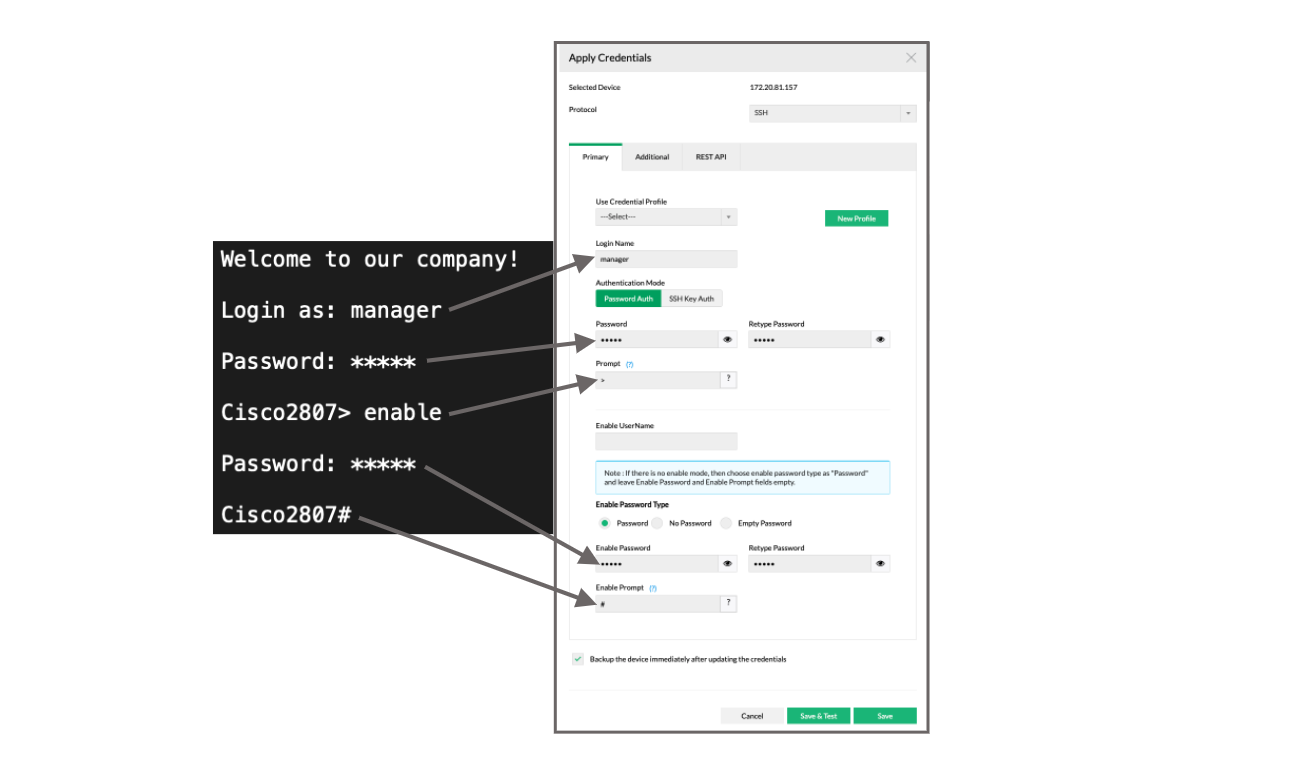
- Click on the credential icon
 for the said device from device list. Alternatively you can select the device and click on the 3 horizontal dots
for the said device from device list. Alternatively you can select the device and click on the 3 horizontal dots  on top right and click on "Apply Credentials".
on top right and click on "Apply Credentials". - Select the desired protocol
- Select "---Select---" option from "Use Credential Profile" dropdown to disassociate the device from the credential profile
- Make the necessary changes to credential parameters.
- Click on Save.
Credential Rule
Network Configuration Manager already has a feature know as Credential Profiles, where the user can set up a profile with all the required credential parameters for different protocols and then the credential profile can be associated with the devices and based on the protocol selected in device credentials, appropriate credentials will be applied to the device automatically.
Now with credential rules, the process of applying the credential profiles to the devices can be automated by creating a credential rule and providing either a particular device group(s) or a criteria to select devices based on multiple parameters. User will also need to provide the protocol and the credential profile that will be applied to the devices which fulfil the criteria for the particular credential rule.
Any new device that is added into Network Configuration Manager will go through all the credential rules available in the product at the time and if the device fulfills the criteria for a particular credential rule, the associated credential profile will be applied to the device.
If a device fulfills criteria for multiple rules, the rule with the lowest rule order will be selected.
Network Configuration Manager tries to match devices with credentials rules starting from the lowest rule order. Hence, a priority can be set by giving a small rule order number to a particular rule. Rule orders can be changed by dragging and dropping the rows in the Credential Rules grid.
Any non-disabled credential rule can be executed for existing devices. Please follow the steps given below to run a credential rule through selected devices:
- Go to Config Automation > Credentials > Credential Rules
- Click on the "Run Through" icon in the grid for particular Credential Rule
- Select the devices in the newly opened slide
- Click on Run
Credential Rules work hand in hand with Credential Profiles. A Credential profile may contain credentials for multiple protocols (SSH, Telnet etc...). While creating/modifying credential rules, users can select the particular protocol credentials to be associated with the device if the device fulfills the criteria for the particular credential rule.
As of now, REST credentials profile cannot be created in Network Configuration Manager, hence we cannot use the Credentials Rule to apply REST Credentials. We are working on bringing support for features like these and we will be adding REST credentials to credential profiles soon.
A disabled credential rule will not be considered while applying credentials to devices, even if the device fulfills the credential rule criteria.
Backup
Network configuration backup is a process of saving your existing configuration files of network switches, routers, firewalls and load balancers.
Network Configuration Manager will backup configuration files of network devices like switches, routers, firewalls and load balancers. Also it will create a repository with all versions stored in incremental versions.
If any network device goes down in your network, it will be hard for network admins to bring the device backup. With backed up configurations, admins can easily choose which is the stable configuration and upload it immediately.
Version count will be increased if any change is found in the configuration. That is, Network Configuration Manager backs up and adds the changed configuration as the latest version, thus increasing the version count.
SysObjectID
- Go To Settings > Network Configuration Manager > SysObjectID Finder
- Click on Custom in the top right corner
- Click on the SysOID entry you want to edit
- Provide the new device template, series and model information (latter two are optional)
- Click save
- You can also delete a particular entry by clicking the bin icon given in front of it
Device Template
- Communicate with the Device: Templates specify the commands needed to interact with the device, allowing you to retrieve information or change its settings.
- Perform Specific Tasks: They guide you through essential actions such as backing up device configurations or applying new settings.
- Check Device Details: Templates help you obtain important information about the device, including memory size and software version.
- Command to disable pagination in the devices.
- Command to fetch the startup configuration. (Only if the device supports startup configuration)
- Command to fetch the running configuration.
- Command sequence to fetch the configuration using Telnet or SSH.
- Command sequence to show the configuration version information.
- Command to enter configuration mode on the device.
- Command to exit configuration mode.
- Command sequence to upload configuration using Telnet or SSH.
- Command sequence to commit a configuration change on the device.
| Variable | Description |
| ${UserInput:tftp_server_address} | IP Address of TFTP Server which can be found under Settings > Network Configuration Manager > Server Settings > TFTP Server |
| ${UserInput:file_name} | Filename to save the configuration on TFTP or SCP server |
| ${UserInput:HostIpAddress} | IP Address of Syslog Server which can be found under Settings > Network Configuration Manager > Server Settings > Syslog Server |
| ${UserInput:LoggingLevel} | Syslog level on or above which |
| ${UserInput:scp_server_address} | IP Address of SCP Server which can be found under Settings > Network Configuration Manager > Server Settings > SCP Server |
| ${UserInput:scp_username} | SCP server username |
| ${UserInput:scp_password} | SCP server password |
- Try to check multiple device templates to get a hang of all the appropriate command syntax.
- Gather all the information required for your device template.
- Find out whether you need to use any pre-command or command variable while creating/editing the device template, if yes what are they and where to use them.
- Try to create a device template tweaking existing device templates instead of going for a completely new device template from scratch.
- Always make a backup copy of a device template before modifying it.
Device Template New
Prompt ActionID is a command mapped to a prompt, which gets automatically executed when a prompt match is found, during an operation execution.
Example: Consider a command that has prompt "[yes/no]"(this prompt might be mapped to a promptActionId) asking whether to proceed to the next command. When this prompt appears, we check if any promptActionId has been provided and if the prompt that appeared is mapped to this ActionId. In that case, the command (either yes or no) mapped to this prompt will get executed. If that prompt's value is "yes", we proceed to next command and if it is a "no" , the execution stops there. Also, if there is no definition of that prompt, the operation will wait till a response is provided.
NOTE: If a prompt Action ID is not defined for a prompt, the operation will not continue. This is why it is essential to map a prompt Action ID to a prompt, for commands that require a response/action.
Operation refers to any device configuration activity. Network Configuration Manager supports the following operations:
Backup Startup Configuration
Backup Running Configuration
Upload Startup Configuration
Upload Running Configuration
Enable Change Detection
Disable Change Detection
Sync Configuration
Get Hardware Props
Yes, you can use the same Device Template for SSH protocol. In order to make the operations available for SSH, go to Settings -> DeviceTemplate and click on the template which needs to be changed to SSH protocol. Once the protocol is changed, click on save icon. This template can now be used for both the protocols (SSH/Telnet).
Backup Response is an action which triggers a backup from a particular configuration command, if enabled. The response of the command whose backup response is true is read and downloaded from the device. (For the command from which you want a back up to be triggered, enable the radio button for BackupResponse).
BackupResponse is available only in SSH/Telnet Protocol for Backup Operation because, in file-transfer protocols such as TFTP, and SCP, the configuration file will be automatically downloaded from the device in a file format. Since SSH/Telnet are not file transfer protocols, we can only read the response of the command. Hence, Backup Response must be given in order to trigger a backup of a configuration file.
Inventory & Change Detection
One of the ways to detect configuration changes in a device is by monitoring syslog messages. Many devices generate syslog messages whenever their configuration undergoes a change. By listening to these messages, it is possible to detect any configuration change in the device. This comes in handy for administrators to keep track of the changes being made and to detect any unauthorized changes.
Network Configuration Manager leverages this change notification feature of devices to provide real-time change detection and tracking. A syslog server comes in-built with Network Configuration Manager. It occupies port 514.
Besides the real-time change detection, configuration changes could also be tracked through scheduled, periodic backup of device configuration. For more details refer to the section "Configuration Change Detection" in help documentation.
Real time change detection is a feature provided by Network Configuration Manager which allows you to monitor every single change made to a device's configuration and trigger an automatic backup and can notify you about any unauthorized change.
- How does it work?
Many devices generate syslog messages whenever their configuration undergoes a change. By listening to these messages, it is possible to detect any configuration change in the device. Network Configuration Manager leverages this change notification feature of devices to provide real-time change detection and tracking
- How does it benefit me?
This comes in handy for administrators to keep track of the changes being made and to detect any unauthorized changes. By enabling this, you can:
a. Capture configuration as and when changes happen
b. Get real-time notifications on change detection
c. Find information on who carried out the change and from where (the IP address)
d. Detect unauthorized changes on real-time
If you have configured the device for real time change detection, but you are not receiving the expected notifications and the backups are not working, please check following things once:
- Configured syslog server is up and running.
- Syslog services are running. You can check this and start the service if not running by going to Settings > Basic Settings > Server Settings.
- Check if the proper port is configured for the server.
- Check if the device is forwarding syslogs or not. You can use the ManageEngine's Syslog forwarder tool to detect this. It's free to use.
If all the above mentioned troubleshooting steps returns positive results and if change detection is still not working, please contact Network Configuration Manager support team, we will be more than happy to help you out
This message appears for one of the two reasons:
- The device is configured with SNMP credentials: If you have added the device using Network Configuration Manager discovery, then the device will be configured with SNMP credentials or if you have manually applied SNMP credentials to the device then the change detection can't be enabled for the said device. Network Configuration Manager can't detect syslog messages with SNMP credentials. Please change the credential protocol to either SSH or Telnet. If it still doesn't work, please contact the Network Configuration Manager support team .
- Configured device template doesn't support real time change detection: If the selected device template which was used to add the device to Network Configuration Manager does not support real time change detection, you will be shown this message. Please contact Network Configuration Manager support team to help you with the issue.
Each device has a pre-configured list of log levels or log types. These log levels are used to determine the severity of the change for which the syslog message is generated. Following are some example of syslog levels:
- Informational: These types of logs can be generated by the device to provide some basic information.
- Notice/Notification: These types of logs can be generated to provide a notification to the user.
- Warning/Alert: These are the most severe types of log and are generated to notify that something unusual has occurred with the device for example an unauthorized change.
Based on your need, you can set a level of logging while enabling real time change detection. This setting can be changed later using the same option. Once the logging level is set, Network Configuration Manager will notify you and will trigger a backup for all the logs that have the same or higher level as the one you have chosen.
Note: The above given list of log levels is just for example, and the actual type of log levels may differ for your device.
Yes you can enable/disable real time change detection for any number of devices simultaneously. Please click here to know how to enable/disable change detection.
Change Detection Status will be marked as enabled when the current configuration has the line matching the pattern provided under Config Automation -> Device Template -> Enable Change Detection Status. If you are not able to find the matching pattern by default, then we can add a new one. Please click here to know the steps to add new regex pattern.
Yes, more than one regex pattern can be configured for the same device type. However, all the regexes should have their current configuration matching to show the Change Detection Status as "enabled".
Label Configurations
Labelled configurations are normal device configurations but with a name (label) assigned to them. This helps us in distinguishing a configuration from all the other configurations for a particular device and allows us to find the necessary configuration easily. Any configuration that seems important, or may be needed in future, or if you want to save it as a fall back option if something goes wrong, can be associated with a label.
You can label a configuration to distinguish it from all the other configurations for a particular device. For example, you can label a very stable configuration as 'Stable' before making a critical change in the configuration. So if anything goes wrong, you can easily find your labelled device and revert to it. Since there are lot of configuration backups for a particular device, labeling a configuration helps you to easily identify a particular configuration among the hundreds of configurations for a specific device.
Scheduling
The following type of tasks can be scheduled using Network Configuration Manager:
- Configuration Backup
- Report Generation
- Compliance Check
- Configlets
- Sync Configuration
- Configuration Review
Yes, a schedule can be disable temporarily without removing it permanently. To do so, go to Settings > Schedule > All Schedules. Click on the Enable/Disable toggle button under Status column for the schedule which you want to Enable or Disable.
Yes, a schedule can be executed on demand before its scheduled time. To execute a Schedule on demand, go to Schedules page from Settings > Schedule > All Schedules. Click the "Execute Now" option from the Action column for the schedule you want to execute.
Yes, schedule execution history can be accessed from Settings > Schedule > Schedule Audit.
Yes, you can schedule a task for as many devices as you wish at a time. You can also select a device group for scheduling a task while creating the schedule. Click here to know more about how to create a schedule.
If any of the email addressees mentioned while creating the schedule are not receiving the notifications, then check the mail server settings under Settings > Basic Settings > Mail Server Settings. You can also send a test mail to ensure that the mail server is configured properly. If the mail server settings are working fine and if you are receiving the test mail without any issue, but you are still not getting the schedule notification, then please contact Network Configuration Manager Support team for further help.
Configlets
A configlet is a configuration script that is transformed to a CLI configuration string before being applied to a device. The dynamic elements (strings) in configlets are defined using variables. These variables act as an input to the process of transformation to construct the CLI configuration string. These variables can contain anything: the interface name, device name, description text, or any similar dynamic values. The values of these variables are either defined by the user or system, or determined by the context at the time of execution. The Configlets help in automating repetitive and time-consuming configuration tasks. All you need to do is to create a small Configlet containing the required commands and then execute the Configlet for carrying out repetitive tasks for many devices, multiple times. The Configlets can also be scheduled for execution at a certain point of time in future. This helps in executing the tasks without the intervention of the administrators. The Configlets enable the network administrator to apply the changes to multiple devices at one go. Also, the Configlets provide the benefit of carrying out exact changes with precision.
Yes a configlet can be imported/exported from and to a file. Go to Settings > Configlets page Click on "Import" to import a configlet. Provide a XML file containing configlet details, and click on Import. To export a configlet, select the configlet from the list and click on "Export".
Yes a configlet execution can be scheduled. To schedule a "configlet execution" please click on the Schedule icon 
You can add a particular configlet or a group of configlets to the Action menu of device snapshot using this option. Once you select a configlet or multiple configlets, click on 'Add to Snapshot'. This will open a slide where you can choose the device template which you want to associate the configlet(s) with. Once associated, configlet option can be seen in the Action Menu of Device Snapshot page under "Configlet Actions" section. This is useful if you execute the said configlet(s) very often for a particular device or device type.
Configlet Execution History can be checked under Settings > Configlets > Execution History tab. A report can be exported as PDF for each record in history. Click the PDF icon provided in the last column of the record to export the report.
SNMP can be enabled on Cisco switch by using automation templates called as configlets. You can select script execution mode and enter device-specific commands and execute it. This will instantly enable SNMP on Cisco switch.
There are certain device-specific commands that need to be executed to configure SNMP on Cisco switch. You can find the step-by-step procedure in this page.
Yes, SNMP can be enabled or disabled using Configlets. Refer to your device specific command to enable SNMP and use the same command to create the configlet using Script Execution Mode.
Yes, the basic idea behind configlets is to allow users to perform various bulk operations on multiple devices at the same time. Following are few practical applications of the same:
- Changing Passwords
- Getting 'show version' output of all devices
- Updating NTP server entries on your devices
- Synchronizing Running & Startup Configurations
Configlets offered by Network Configuration Manager are of two types:
TFTP Mode - for uploading a partial configuration change to a device/devices through TFTP.
Script Execution Mode - commands are executed on the CLI console one after another. Script execution is divided further into two types as below -
- Simple Script Execution
- Advanced Script Execution
The following table provides information about the each type of configlet and when to use them:
| TFTP Mode | Simple Script Mode | Advanced Script Mode |
|---|---|---|
TFTP mode is for uploading a partial configuration change to a device/devices through TFTP. | To execute a single command on the CLI console. | To execute a series of inter-connected commands on a device in command line. After the execution of one command, some input has to be provided before the next command is invoked. In such a situation, advanced scripting would be useful. |
example
| Example: Synchronizing Running & Startup Configurations. Through a single line in the script containing the command copy running-config startup-config, you can synchronize the startup and running configurations of any number of devices. Other Examples:
| Example: Backing up your current IOS image to a TFTP server. To do this, the following sequence would be used:
|
In all the above case, TFTP mode of configuration upload could be used. In general, for carrying out changes to existing configuration, this mode could be used. | The above sequence of command execution could be transformed into an advanced script as below: copy flash:/$SOURCE_FILE_NAME tftp $TFTP_SERVER_IP $DESTINATION_FILE_NAME | |
For other cases like executing a command on device, Script execution mode has to be used. |
|
At any step of configlet execution, if the command prompt changes then this change must be explicitly handled while creating the configlet. You can add an attribute called "Prompt" for the command which will use a different prompt value, and mention the prompt as the value to the attribute.
Example: copy startup-config tftp (Here, the prompt ? is placed within single quotes and following a closing square bracket. Everytime "<command prompt=']?'>copy startup-config tftp</command>" command runs, it will run with the prompt value '?')
Note: "Prompt" attribute is supported only in Advanced Script Mode.
While creating the configlet, in the text field 'Configlet Content', enter the configuration commands that are to be uploaded to the device. While entering the configuration command, use $ to create a Variable. For instance: snmp-server community $COMMUNITY RO. Here, "COMMUNITY" will act as a variable for the command. If a variable has been created/defined in the configlet. You have two options here to enter the desired value for the respective configlet variables.
Same value for all devices: If you want to specify the same value for a particular configlet variable for all devices, choose this option and enter the value. For example, for '$COMMUNITY', you can provide 'public' as the value. After entering the values(s), you can preview the actual configuration with full configuration commands and value for community variable(s).
A different value for each device: In case, you want to specify a different value for different devices, provide your input in the form of a text file. This option will be highly useful in cases such as providing passwords. You assign a unique password to each device in a single click through this option. Ensure that the entries in the text file are in the following format:
- Column headers should be the same as that of the Configlet Parameters defined in the configlet with the entries separated by a comma.
- "RESOURCE" column is mandatory and it should be the first column in the file to identify the devices on which the script needs to be executed.
- The value for RESOURCE should be either host name / ip address. One line can hold the entries for one device.
- Format: RESOURCE,,
- Examples: RESOURCE,PASSWORD 192.168.1.1,password-0 de-host,password-1
Flow Export Configlets are used to export the flow from the device to a particular server. You can create a flow export configlet and assign it to a particular device template.
How to create and assign a flow export configlet:
- Go to Settings>Configlet>All Configlets from Main Menu.
- Click on Add.
- Enter all the necessary details for the configlet.
- Save the configlet using the Save button.
- Go to Settings > Device Management > Device Template
- Click on the Device Template to which you want to assign the newly created configlet
- Go to "Flow Export Configlet" tab.
- Click on "Add Flow Configlet"
- Choose the newly created configlet and move it to the right hand side of the select box.
- Click on save
How to use the assigned Flow Export Configlet:
- Go to Inventory > Devices
- Select the device for which you want to export the flow
- Click on the 3 horizontal dots
 at the top right corner to get device option list.
at the top right corner to get device option list. - Click on Export Flow
- If the credentials are not assigned to the device, you will have to provide the device credential, if the credentials are already present, then this step will be skipped automatically.
- Select the interfaces in next step. Interfaces will be listed only after successful configuration backup for the device. You can skip interface selection if you do not want to configure interfaces.
- Select the newly created 'Export Flow Configlet' in next step.
- Check all the ip addresses and interface values are populated successfully in the configlet
- Click on Apply.
Yes, $Variable can be used in Script Execution and Advanced Script Execution Mode Configlets. These variables are used to define dynamic data to be used for Configlet execution.
We use ‘$’ to define variables in Configlets. To use '$' without variable definition, you must escape ‘$’ using this format "#[[$]]#".
Configlet Group
Configlet group consists of grouped Configlets with similar functionality or based on usage for easier accessibility.
Only default Configlets can be accessed by the operator and other low privileged users, making it difficult in managing Configlets among users and causing duplicate Configlets. With Configlet group, you can overcome this limitation. Admins can now assign the Configlet group created to other users so that it can be used by them too.
No, we cannot delete the Configlet group associated with another Configlet group.
Yes, we can delete the Configlet group assigned to users.
Only an administrator with full access can edit or delete the Configlet group created by other users. Kindly check your access privilege if you are unable to perform any edit operation.
Go to Reports -> Vulnerability & User Reports -> User Audit. You can find the user details on any operation performed on Configlet group.
Programmable Configlets
Programmable Configlets allow network administrators to automate configuration changes across multiple devices. Instead of manually applying changes one device at a time, Programmable Configlets let you define conditions and execute commands based on those conditions. This makes it easier to manage large networks, allowing for bulk changes and real-time adjustments.
- Conditional configuration
- Looping configurational operations
- Secure handling of sensitive data
- Efficient bulk configuration
Programmable configlets lets you define specific conditions and apply configuration changes only when the conditions are met.
Benefit: Streamlines processes by targeting only the necessary devices or components for configuration updates.
Utilize loops to iterate and apply configuration changes across multiple devices or components.
Benefit: Saves time and reduces manual effort for repetitive tasks, such as updating interface descriptions, enabling SNMP settings, or enforcing security policies on devices.
Provides enhanced data privacy and security by allowing sensitive information, like passwords, to be predefined and hidden variable within the template. This ensures that sensitive data remains secure and is not exposed to unauthorized users.
Benefit: Protects confidential information and reduces the risk of accidental exposure during configuration tasks.
Enable bulk operations to make large-scale changes across multiple interfaces or VLANs without manual intervention.
Benefit: Improves efficiency in managing network configurations, such as updating interface and VLAN settings in bulk.
Predefined variables do not require input from the user; they are automatically replaced with their corresponding values during configlet execution.
Following are the list of predefined variables,
| $scp_serverip | SCP Server IP |
| $tftp_serverip | TFTP Server IP |
| $sftp_serverip | SFTP Server IP |
| $scp_username | SCP Server Username |
| $scp_password | SCP Server Password |
| $sftp_username | SFTP Server Username |
| $sftp_password | SFTP Server Password |
Ex: $device.execute("copy filename scp://$scp_username@$scp_serverip/filename}")
In Configlet Parameter tab, $scp_serverip and $scp_username variable attributes will be automatically fetched and the same will be executed during configlet execution.
Users can create variables in Configlets by appending $ before the variable name. These are called user-defined variables.
Example: $device.execute("logging $SYSLOG_SERVER_IP")
Here, $SYSLOG_SERVER_IP is a variable, and its value will be provided by the user during execution.
Text:
This variable allows you to specify a regular expression.
Password:
This variable stores the password and can be hidden for security purposes.
Option:
You can add two options. Each option consists of a key (the display name) and a value, which will be used during the execution in the configlet.
Boolean:
This variable provides a prompt for the user to select a "Yes" or "No" answer. The available values can be tailored according to the device requirements.
Drop-down:
This variable contains a set of keys and values, and can support multiple entries. It functions as a drop-down menu, allowing the user to select a desired value during execution.
Multi-select:
This variable consists of keys and values, and supports multiple entries. It can be used to iterate over a dynamic list, where the entries can be added/removed/modified without affecting the existing configlet content.
To prevent sensitive data exposure, a variable can be declared as hidden. Once input is provided, it will not be displayed anywhere. To mark a variable as hidden, select the Hidden checkbox in the Configlet Parameter tab.
NCM Regex
Regex in NCM is used to validate inputs for configlet variables. For example, if a variable is meant to store an IP address, specifying a regex ensures that only valid IP addresses are accepted, preventing any mismatched values.
REST Configlets
A REST API is an application programming interface (API or web API) that conforms to the constraints of REST architectural style and allows interaction with RESTful web services. When it comes to configurations, most of the device vendors provide REST API support on different levels for reading and writing the device configuration in parts or as a whole during the backup process.
Network Configuration Manager uses the REST APIs to allow users to have a simplified UI experience. The users can focus on a particular part of the configuration without worrying about the command syntax and configuration hierarchy. On top of that, the REST API's GUI has been designed to resemble the device GUI for users' better understanding.
In NCM, REST API based configuration management works with REST Configlets.
Rest configlets are configuration objects such as address, policy, security rules etc. You can access Rest Configlets by going to Config Automation > Configlets > Rest Configlets (In case of OPM or NFA, this option is available under Settings > NCM > Configlets > REST Configlets).
Each configlet comes with a different set of operations such as Add, Edit, View, Delete, Rename, View All, Clone, Execute etc.
| Operation | Description |
|---|---|
| Add | Adds a new object to the device configuration. |
| Edit | Provides a list of objects available in the device. Users can then select a particular object. The details about the selected object will be fetched from the device and will be shown to the users. Users can update any particular detail/parameter for that object and then execute the configlet to save the changes in device. |
| View | Provides a list of objects available in the device. Users can then select a particular object. The details about the selected object will be fetched from the device and shown to the user in read only mode. |
| View All | Shows all the available objects in the device in a grid along with their details |
| Delete | Provides a list of objects available in the device. Users can select a particular object and execute the configlet to delete the object. |
| Rename | Users can select a particular object and provide a new name to rename the object in the device. |
| Clone | Users can select a particular object and provide a new name to clone the object in the device with the name provided along with its properties |
| Execute | Most of the non-firewall devices have objects that can only be viewed and executed as CLI commands. For such devices and configuration objects, there will be only one operation available, which is "Execute". It will execute the command in the device with the provided parameters. |
- While backing up whole configurations, REST APIs are much faster than a normal CLI backup. In fact all REST API operations are faster than CLI operations in general.
- One does not have to memorize command syntaxes while updating a particular part of a configuration.
- One does not have to worry about the hierarchy of objects in a configuration.
- The important objects in a configuration can be viewed in a grid format in NCM.
- NCM's REST Configlet feature provides a GUI that is similar to the device's GUI (Eg: Firewall GUI) and this makes it easy to update a part of the configuration directly from NCM.
If REST credentials are provided to a device, NCM will take backup and will upload configuration to the device using REST API's. Additionally user can execute REST Configlets to modify or view a part of configuration. Please click here to know more about REST Configlets and here to know about how to use them.
Yes, you can use both REST and CLI credentials to manage a device. In fact NCM recommends a user to use a combination of CLI and REST credentials to make the most out of the tool. Please click here to see how to apply REST credentials to a device.
Similar to CLI Device Templates, REST Device Templates are a set of instructions that helps NCM in performing the REST API operations on the device. It contains details about the operations that can be performed on a device, the list of parameters for each operation and also the REST Credential parameters that help NCM to connect with device using REST API.
One cannot associate a REST Device Template directly with a particular device, instead REST Device Templates are associated with CLI Device Templates and when a device is added with the CLI Device Templates, the respective REST template automatically gets associated with the device.
As of now, we have automatically mapped few CLI device templates with appropriate REST device Templates and this list cannot be modified. In the future, we may provide an option to create and edit REST device Templates, as well as to add and edit REST Configlets.
Please reach out to NCM support at ncm-support@manageengine.com with Device and Vendor information. We are continuously adding REST API support for more and more vendors and will be happy to prioritize your device once requested.
Base OS Version is the firmware version of the device from which the REST device template for that particular vendor is derived. Which means, if any API added, removed or modified before that version, it may not work in NCM.
Base OS Version is the firmware version of the device from which the REST device template for that particular vendor is derived. Which means, if any API added, removed or modified before that version, it may not work in NCM. We do not recommend to use REST API operations in NCM if the device's firmware version is older than the Base OS version.
Object Explorer is a list of object types (Address, Policy, Schedule etc) from device configuration that can be manipulated using REST API's. Once any of the object types is selected from the Object Explorer list, a new slide will open with the list of objects of the selected type. Here you can select any of the objects from the grid and click on "Hamburger icon"  on top right of the grid to see the list of operations that can be performed on the selected object. Add and delete operations are available on top of the grid (These operations will be available only if Add and/or delete operations are supported). Once an operation is selected, a new slide will open to execute the operation. Provide required parameters in the newly opened slide and click on execute. (This option will be available only if the operation is not read-only). Please note that not all the objects that support REST API are listed under Object Explorer. We have listed only the operations that are deemed most important in device configurations. To check the complete list of object types that supports REST API for a particular vendor please go to Config Automation > Configlets > REST Configlets (In case of OPM or NFA, this option is available under Settings > NCM > Configlets > REST Configlets)
on top right of the grid to see the list of operations that can be performed on the selected object. Add and delete operations are available on top of the grid (These operations will be available only if Add and/or delete operations are supported). Once an operation is selected, a new slide will open to execute the operation. Provide required parameters in the newly opened slide and click on execute. (This option will be available only if the operation is not read-only). Please note that not all the objects that support REST API are listed under Object Explorer. We have listed only the operations that are deemed most important in device configurations. To check the complete list of object types that supports REST API for a particular vendor please go to Config Automation > Configlets > REST Configlets (In case of OPM or NFA, this option is available under Settings > NCM > Configlets > REST Configlets)
Firmware Vulnerability
In order to see the severity status of all the vulnerabilities in your devices, you can click on the "Firmware Vulnerability" tab. On the top left corner, under "Firmware Vulnerabilities" you will see all the vulnerabilities in your network along with its severity.
Based on the severity, NCM groups vulnerabilities as Critical, Important, Moderate, Low and Unrated. By clicking on the severity, you can see all the vulnerabilities and the number of devices in your network environment which has those vulnerabilities. On top of that, NCM also provides a reference URL which provides the corrective measures to resolve a vulnerability.
Note: At present, NCM supports Firmware Vulnerability only for Cisco and Juniper vendors.
Network Configuration Manager categorizes the severity of vulnerabilities based on the "Base score" which is calculated based on a few metrics like Exploitability Metrics(Attack, Complexity, Authentication) and Impact Metrics (Confidentiality, Integrity, Availability). Here is the split up of how the severity is categorized:
- Base score 9.0 - 10 - Critical
- Base score 7.0 - 8.9 - Important
- Base score 4.0 - 6.9 - Moderate
- Base score 0 - 3.9 - Low
NCM helps identify risks to network security by detecting potential vulnerabilities in the following device types:
- Cisco IOS
- Cisco Adaptive Security Appliance (ASA)
- Cisco Nexus
- Juniper
NCM imports the firmware vulnerability warnings provided by National Institute of Standards and Technology (NIST), and correlates vulnerability data with nodes that it currently manages. If NCM finds a match, the Firmware Vulnerabilities resource on the Config Summary page displays information about the vulnerability and the number of affected nodes.
Network Configuration Manager fetches the data through an open network and updates the latest vulnerability data in NCM. NCM also allows users to set a time of schedule in order to sync data on a daily basis. When a schedule time is given, automatically the synchronization of vulnerability data happens at the exact time of schedule. NCM also allows you to edit/change the time of schedule as per your convenience.
If you wish to update the Vulnerability data in the NCM UI immediately instead of the scheduled time, you can give the "Update Now" option. When "Update Now" is given, the latest vulnerability data will be updated in the NCM UI.
Yes, with "Advanced CVE search" you can globally search for all the vulnerabilities by searching using the vendor name, CVE id, device OS number, version or a model. For eg: If you search "Cisco IOS 7000", all the vulnerabilities present in that particular model will be listed. On further clicking it, you will be able to see all the details of the vulnerability corresponding to a particular CVE id.
Under Firmware vulnerabilities, all the vulnerabilities will be listed along with its corresponding CVE id. You can select a required CVE ID and view its details. In the CVE details page, you will be able to see:
- The date the CVE id was published and the last updation date of the CVE id.
- Summary of the CVE id which provides information about what the vulnerability is and the device version of the vulnerability.
- The reference URL, which provides the optimal resolution measures.
- A comment section which allows users to add a required statement.
- A select box with options to mark the status of the vulnerability.
- Reported - The vulnerability has been reported.
- Confirmed - The vulnerability is confirmed but no resolution is planned.
- Resolution planned - Action to resolve the threat is planned but has not been taken.
- Resolved - The vulnerability is confirmed and the action to resolve the threat has been taken on the selected devices.
- Not applicable - The vulnerability does not apply to the selected devices.
Syslog Blocked Host
In an environment where the users login and logout of devices more frequently, flooding of Syslog messages tend to occur. This leads to increased CPU usage of the Network Configuration Manager server which in turn affects the performance of the machine. To prevent this, Network Configuration Manager blocks the syslog messages from that device and notifies the user about the device that has been blocked. The blocked devices are listed in Settings > Device Management > Syslog blocked hosts. Since backup automation relies on syslog messages, Network Configuration Manager does not detect changes automatically for the blocked devices until the devices are unblocked. You can unblock the devices at any point of time from the blocked list and before unblocking any device make sure that the problem is resolved for that particular device. Please click here to know more about how to unblock a device.
There are two things you can do to avoid syslog flooding:
- Temporarily turn off syslogs for the blocked devices.
- Lower the syslog level to restrict the number of syslog messages.
Network Configuration Manager will block any host that is flooding the system with syslogs, for two hours. Post 2 hours the host will be unblocked again, and Network Configuration Manager will receive the syslogs from the said host. If the number of syslogs are still high, then the host will be blocked again for two hours.
Yes, syslog flood prevention can be turned off at any time, though it's not recommended because a huge number of incoming syslogs will increase the CPU use and will slow down Network Configuration Manager. Take extreme precaution before opting to turn off syslog flood prevention. To turn off flood prevention, please go to Settings > Global Settings > Client Server Settings and uncheck the checkbox next to "Enable Syslog Host Blocking" option. Save your changes to turn off the syslog flood prevention. If you wish to turn it on, check the same checkbox again and save your changes.
A device will be blocked by NCM if it sends more than 200 messages in 2 minutes of time.
Yes, threshold for number of messages in 2 minutes, after which the device will be blocked, can be configured by changing the system property "syslog.PER_HOST_MSG_COUNT" in "system_properties.conf" file under "/conf" folder. Please add the property in the file if not already exist.
Exclude Criteria
Exclude Criteria is a line or part of a line or a regex that represents a line from the configuration, and that need not to be considered for calculating differences between two configurations. For example, timestamp for a configuration will change based on the time backup was taken. There may not be any other change between two backups but just because the timestamp is changed, Network Configuration Manager will show you difference on that particular line. To avoid this we can create a exclude criteria and assign it to a particular device template and Network Configuration Manager will ignore changes on that particular line.
Yes, Network Configuration Manager supports regex as exclude criteria.
Yes any number of exclude criteria can be created and associated to a particular device template.
No, exclude criteria's can only be applied to a device template and not to a particular device or configuration.
Block Exclude Criteria is used to exclude a block of configuration from being considered while identifying differences between two configuration versions. This only works when the regular expressions provided match with the start and end of the configuration block.
Additional Block Criteria is used when users want to specify if there is a particular string or regular expression that the configuration blocks should or should not contain for the block to be considered.
NCM Terminal Tool
Terminal tool provides you functionality to open a terminal session with any network device and perform CLI commands directly from Network Configuration Manager. Why is it needed? We already have terminal options in device snapshot for each device, then why do we need a separate tool for the same thing? Well, the terminal tool can be used to open terminal sessions with network devices that are not added in inventory, or the devices that you don't wish to add in inventory. For example, if you want to connect to a Linux machine and perform some commands, you can do so by adding the Linux machine directly under Tools > Terminal > Custom. It also allows the user to open terminal sessions for Inventoried devices with just one click.
A terminal session can be started using either SSH or Telnet protocol.
Inventoried tab lists all the available devices from Inventory > Devices. You can open a SSH or Telnet terminal session for the devices listed under this tab with a single click. You won't be able to add/modify or remove any device from this list directly from Terminal Tool.
No. While adding a Custom Terminal Device, you won't have a option to provide SNMP credential, but there can be an inventoried device with SNMP credentials listed under Inventoried tab. If you try to perform any terminal action for those devices, it will fail after a particular timeout period.
No, you can't add/modify/delete an inventoried device from Terminal Tool. If you wish to delete an inventoried device, delete it from Inventory > Devices.
Terminal Device Groups are similar to normal device groups in Network Configuration Manager, they are used to group similar custom terminal devices together. Now, we are not using the device groups for any particular action, but we have a plan to assign the groups to the users in future. So whenever a new device is added to a certain group, it will be available for all the users who have access to the said group.
History/Audits of all the Terminal Actions is available under Tools > Terminal > Audit History. You can filter the audit records based on device type (Inventoried, Custom or Both).
While adding a Custom Device to be used in Terminal Tool, you can chose the visibility of the device. Network Configuration Manager provides you 3 types of visibility for any particular device:
- Only Me: Device will be visible only to the user who has added it.
- Admin: Device will be visible to the user who has added it and all the admins in the system.
- Everyone: Device will be visible to everyone.
Visibility of a device can be changed at any point of the time.
Export Configuration
Currently Network Configuration Manager exports configuration only in text format (.txt files), and this can not be changed, but we are working on providing more export option soon.
Yes, you can give any preferred location to save the exported configuration files. To change the location, go to Settings > Global Settings > Export Configuration and provide the desired location under "Destination Directory" field.
If you are exporting the configuration using "Export Configuration" page under Settings > Global Settings, then Network Configuration Manager will export the latest versions of startup and running configuration of device. Although you can export a particular version from inventory by following the steps given below:
- Go to Inventory > Configs
- Click on the configuration that you wish to export
- Click on the version of configuration that you wish to export from 'Config Changes' table
- Click on the settings button on top right corner of the page
- Click on Export Config
History of the all the export configuration operations can be accessed from Settings > Global Settings > Export History.
Network Configuration Manager saves the exported configuration in a folder name with current date, so if you try to export configurations multiple times on same day, Network Configuration Manager will just overwrite the previously exported file and keeps the latest files in the same folder.
Yes, Network Configuration Manager notifies you once the export process is completed, you can mention the email id(s) where the notification needs to be sent under Settings > Global Settings > Export Configuration page. Select any particular frequency (Daily, Weekly or Monthly) to export the device configuration and mention the email id(s) under "Notify on completion by Email" field. Multiple mail ids can be provided in a comma separated list. You can also choose to receive notification only when the process fails by checking the 'Notify only on failure' checkbox.
If you are exporting the configuration using "Export Configuration" page under Settings > Global Settings, then Network Configuration Manager will export the latest versions of startup and running configuration of device. Although you can export a particular version from inventory by following the steps given below:
- Go to Inventory > Configs
- Click on the configuration that you wish to export
- Click on the version of configuration that you wish to export from 'Config Changes' table
- Click on the settings button on top right corner of the page
- Click on Export Config
Third Party Syslog Server
A Syslog Message will be sent to a default Network Configuration Manager Syslog Server if the configuration is changed and change detection is enabled for the device, but in some cases you may want the syslog messages on a specific server of your choice, in that case you can add the server ip addresses under Settings > Global Settings > Third Party Syslog Server. Network Configuration Manager won't forward the messages to these servers, messages will be directly sent by the device.
Yes, multiple syslog servers can be configured to receive syslog messages. Please click here to know about how to configure external servers for syslog messages.
Database Administration
Network Configuration Manager doesn't keep a backup of any records that are being removed during cleanup. Everything will be deleted permanently. Hence, it is advised to be extra caution while giving the parameter values for the no. of days for which the records need to be kept after cleanup.
Network Configuration Manager performs DB clean up once a day. The default time for the cleanup is 2 AM, but this can be changed to any time of the day from Settings > Global Settings > Database Administration, under "DB Cleanup Time" heading.
Yes, the default time for the cleanup is 2 AM, but this can be changed to any time of the day from Settings > Global Settings > Database Administration, under "DB Cleanup Time" heading.
No, for now Network Configuration Manager does cleanup only once a day and this frequency cannot be altered, although you can change the time of the day at which Network Configuration Manager performs the cleanup.
Since the deletion operation performed during cleanup is permanent, if any of the device audit records deleted during the DB cleanup, you will not be able to see the details for those particular audits thereafter.
Network Configuration Manager gives more priority to the baseline configuration version than the conditions provided for cleanup, so for example, if you have chosen to keep only the last 10 configuration version and your latest version is 30 but the baseline version in 8, Network Configuration Manager will keep all the configuration starting from 8 to 30 instead of keeping just the versions 21 to 30.
Password Management - PMP
Password Manager Pro or PMP is a password vault developed by Manage Engine which allows you to save all your device credentials in one place and once it is integrated with Network Configuration Manager, you can sync the credential changes for all the devices with a single click. Click here to know more about how it works and how to configure it.
Yes, the passwords can be changed manually even after synchronizing it with PMP but if you wish to change the password for a particular device manually, remove the association of that device with PMP first, if not, PMP will change the password back to the original one whenever you choose to sync it next time.
Network Configuration Manager does not support automatic syncing yet but we are in process of developing the feature to schedule the sync process. The option will soon be available under Schedule page in Network Configuration Manager. For now users have to intervene, to sync the passwords with PMP. Please click here to know more about how to sync the passwords with PMP.
Password Manager - PAM360
Where can I view the list of accounts shared from the Password Manager?
Follow the steps below to view the list of accounts shared from the Password Manager:
- In the Configure page of PAM360, locate the Actions button at the top-right corner.
- From the drop-down menu of the Actions button, select View Shared Resources. This will display the shared resources.
- Drill down into any of the devices to view the shared accounts.
Note: The PAM account name will not be displayed for the resource until it is used in the Network Configuration Manager.
How to export the SSL certificate from NCM?
- Open Command Prompt as Administrator
- Execute the following command to export the SSL certificate:
keytool -exportcert -keystore "<OpManager_Home>\conf\itom.keystore" -alias <alias_name> -file "<Destination_Directory>\public-key.cer"
- Replace <OpManager_Home> with your OpManager installation path.
- <alias_name> depends on your OpManager edition:
- Central Server: centralssl
- Probe Server: probessl
- Other Editions: opmssl
- Replace
with the path where you want the certificate saved.
(Note: This command requires the keytool utility, which is part of the Java Development Kit (JDK). Verify that keytool is installed and available on your system. You can check if keytool is available by typing keytool -help in the command prompt.)
Important Terms:
- <OpManager_Home>: Path to your OpManager installation (e.g., C:\Program Files\OpManager).
- <alias_name>: The alias for the certificate:
- Central Server: centralssl
- Probe Server: probessl
- Other Editions: opmssl
- <Destination_Directory>: Directory where the exported certificate will be saved.
Do we sync the account credentials when the Password Manager is disabled in NCM?
No, NCM will not sync account credentials when the Password Manager is disabled.
Where can I generate /regenerate the Password Manager integration token if the previously generated token is lost?
The integration token is used to securely connect the Password Manager with NCM. It’s important to store this token safely (e.g., in a vault) to ensure it is not exposed.
Note: Regenerating the PAM authentication token will invalidate the current token. After regeneration, you must manually update the new token in all integrated applications to prevent any API failures or disruptions in service.
Follow these steps to regenerate the integration token:
- Go to Settings > Integrations. This will redirect you to the Integrations Summary page.
- In the Password Manager category, locate the Generate Key / Regenerate Key option and click on it. The integration token will be regenerated.
System Details
In the device, there are three fields that network admins can configure to provide extra information about the device. These fields are known as "System Location," "System Description," and "System Contact." The "System Location" field is typically utilized to indicate the physical placement of the device within the network. The "System Description" field can contain any additional important details that need to be conveyed to other users. Lastly, the "System Contact" field holds information about the designated contact person for the device. By updating these values in the Network Configuration Manager, users can conveniently access them directly from the device snapshot page, eliminating the need for executing any extra commands on the device.
To review the System Details, navigate to the device snapshot page and locate the corresponding headings: 'System Location,' 'System Description,' and 'System Contact.' Under each of these headings, you can find the relevant information pertaining to the system.
To access a device's snapshot page, go to Inventory > Devices and click on any device.
Yes, System Details of multiple devices can be updated in one go. Please click here to know how to update System Details.
Yes, When updating the System Details, you have the flexibility to select multiple SNMP profiles. Network Configuration Manager will intelligently choose the suitable SNMP credentials for each device automatically.
Upload Request
What is an upload request and when are they created?
An upload request is created whenever an operator user is trying to run a configlet, or trying to upload a configuration or draft for a particular device. All the admins will be notified about this request and any one of them can approve/reject the request. Only after the approval of the request, respective changes will be carried out to the device.
Can I change the status of an already approved/rejected request?
No, a request, once approved or rejected can't be changed back to its original state or to any other status.
What happens when a request is approved or rejected?
An upload request is generally created when an operator is trying to make changes to a device configuration by either uploading a configuration, a draft or for running a configlet. These changes don't have any effect until the request is approved. As soon as the request is approved, the respective changes will be made to the selected device(s).
Change Notifications
What is change notification?
A change notification is a notification which can be sent to a user/server whenever there is a configuration change in the startup, running or both configurations of any device(s) or device group(s). You can create a change notification under the Change Management tab in Main Menu. Click here to know more about how to create a change notification. These notifications can be sent as an email, SNMP trap, Syslog messages or tickets. You can also choose to rollback the changes back to the previous version or to the baseline configuration version using these notifications. Please click here to know more about the different types of notifications and how to configure them.
What are the different types of Change Notification Actions?
A user can select a preferable notification type, out of 5 different types of actions that can be carried out whenever there is a configuration change for the selected device(s). Multiple actions can also be carried out for a single notification. Following are the different actions that can be selected while creating or editing a change notification:
- Email: An email can be sent to multiple recipients alerting them about the change. You can compose the subject and the email body for the mail that will be sent. For both the subject and the body you can choose to select some useful variables that will give you more information about the change. These variables are listed in front of the Subject and Message field. Some commonly used variables are $CONFIGTYPE (to get the configuration type that is changed.), $DEVICENAME (to get the device name for which the configuration is changed.), $CHANGEDBY (to get the user/system name who made the configuration change.) etc.
- SNMP Trap: A v2 trap will be sent to the specified host. SnmpTrapOid = .1.3.6.1.4.1.2162.100.4.1.2.1 Varbinds will include the name & ip address of the device whose configuration is changed and also the type of configuration changed. Please refer to the ADVENTNET-DEVICEEXPERT-MIB bundled with the product
- Sylog: A Syslog Message will be sent to the specified Syslog Server if the configuration is changed. Syslog Message will include the configuration type (CONFIG_TYPE), change type (CHANGE_TYPE), ip address (IP_ADDRESS) and changed by (CHANGEDBY).
- Ticket: A trouble ticket can be sent to the support team email(s) that can be specified under 'Send Trouble Ticket To' field. The configuration of the trouble tickets are similar to that of a mail notification.
- Rollback: You can also choose to rollback the changes that caused this notification. There are two options available for rollback. You can either choose to rollback to the previous version or you can rollback to the baseline version.
Can multiple actions be carried out for a single change?
Yes, you can select any combination of actions from the given 5. Please click here to know more about these actions.
Compliance Policies
What are Compliance policies?
With the increasing security threats to network resources, enterprises are required to follow standard practices, and execute internal/external security policies to remain compliant with the latest industry standards. Therefore, ensuring network compliance has become a priority for network administrators. But, it is a mammoth task to scrutinize and make changes in a networking environment consisting of network devices from multiple vendors. Network Configuration Manager helps administrators analyse network devices to achieve auditable network compliance across industry-specific compliance policies. Every time a configuration is backed up, Network Configuration Manager will automatically run a compliance check on those configurations. Network Configuration Manager also alerts and generates reports whenever a rule/policy gets violated.
What are Compliance Rules?
Conditions or lines that should be either compulsorily present or not be present in a configuration file are called compliance rules. A typical example for a rule is checking the access list configuration or checking the community string. Decide what amounts to violation - presence or absence of a particular line or a set of lines in the configuration file. There are 3 different types of criteria that you can define to create a rule. To know more about these criteria, please click here.
What is a Remediation Template?
A remediation template is a configlet that can be defined while creating a rule, so that if a policy is violated because of the defined rule, Network Configuration Manager will execute the configlet automatically and fix the issue with the configuration to make it compliant with the policy. Please click here to know more about how to create a configlet.
What is an Adhoc Test?
During any stage of compliance policy creation (rule creation, rule group creation & policy creation), you can perform checks on adhoc basis to test the validity of the rule/rule group/policy added by you. The adhoc tests depict the results then and there. After adding a rule, you can perform adhoc test for a device/device group by clicking the "Adhoc Test" button present under Compliance > Rules page. Similarly, adhoc tests can be performed for rule group from Compliance > Rule Groups page and for Policy from Compliance > Policies page.
Can I generate a report for all the policies at once?
Yes a consolidated report for all the policies can be created at once. Go to Reports > Compliance report and click on the PDF icon provided in the top right corner of the page to generate the report. You can also select the device group for which you want to create this report.
What is HIPAA compliance?
HIPAA stands for Health Insurance Portability and Accountability Act. HIPAA Compliance is the process by which covered entities need to protect and secure a patient's healthcare data or Protected Health Information.
What is required for HIPAA compliance?
- Privacy: patients' rights to PHI
- Security: physical, technical, and administrative security measures
- Enforcement: investigations into a breach
- Breach Notification: required steps if a breach occurs
- Omnibus: compliant business associates
Why is HIPAA compliance important?
Being HIPAA-compliant means that a healthcare provider has adequate measures in place to protect patient data. Compliance makes it easier for patients to trust you, and since trust is the backbone of every business entity, they are likely to choose you as their go-to healthcare provider.
How to ensure HIPAA compliance?
- Develop a cohesive privacy policy
- Hire a dedicated security staff
- Have an internal auditing process
- Stipulate specific email policies
Device Group
What is a device group?
Sometimes, you might have to group devices based on some logical criteria. For example, you may wish to create groups such as a group containing all cisco routers, or a group containing all cisco switches or group based on device's physical locations etc., This would help in carrying out certain common operations with ease.
What operations can be performed on device groups?
Almost any operation that can be performed on a single device is also applicable on a device group. Some of the most common operations that can be performed on a device group are as follows:
- Setting Credentials
- Configuration Backup
- Configuration Upload
- Configuration change management
- Defining compliance rules/policies
- Generating a report
- Creating a schedule
Where can I check the devices associated with a device group?
List of devices associated with the device group can be checked by clicking on the device group name in 'Grid View' of device group page under Inventory > Groups. To check the list of devices in 'Widget View', click on the expand icon  present on the top right corner of each widget.
present on the top right corner of each widget.
Reports
Can I receive automatically generated reports on Device Configuration in my mailbox?
Yes, Network Configuration Manager provides option to mail reports to email IDs. You can schedule reports to be generated at any point of time and reports will be mailed to your email ID.
Can Network Configuration Manager generate email alerts?
Yes, Network Configuration Manager can be configured to send email alerts whenever there happens a change in configuration. For more details refer to the section "Change Management " in help documentation.
Does Network Configuration Manager maintain historical data about Device Configuration?
'Yes it maintains historical data of device configuration. The historical data are available in the device properties page of each device. For more details refer to the section "Device Configuration Details" in help documentation
What are the different types of reports available in Network Configuration Manager?
Network Configuration Manager can generate 17 different types of reports which are classified into 4 different categories. Following is the list of reports available in Network Configuration Manager with their respective categories.
Network Reports:
- Hardware Inventory: Hardware details listing the components and their status of the devices
- Firmware Inventory: Firmware details listing the OS version and associated information of the devices
- Device Inventory: Device details listing the model number, series and type of the devices
- Network Health Status: Overview of the conflicts and compliance status of the device configurations
- Device Management Status: Overview of device management setup status like credentials, real-time change detection etc
- Device Audit: Details on 'who', 'when' and 'what' of all the operations performed on the devices
Configuration Reports:
- Startup-Running Conflict: Details on the devices whose startup and running configurations differ
- Configuration Changes: Details on the devices that have undergone changes in configuration
- Configuration Change Trend: Details on the number and type of configuration changes, during a specific time period
- Configuration Analysis Report: Complete details about device configuration settings
- Security Audit Report: Details on the findings of security audit together with the impact and recommendations
User Reports:
- User Access: Details on user access permission for all the devices
- Configuration Upload Request: Overview of the status of configuration upload requests raised by the users
- User Audit: Details of the operations performed by various users using the application
Other Reports:
- EOL/EOS: End-of-Life and End-of-Sale details of the devices
- Compliance: Details on the violations and compliance of the associated policies of the devices.
- : The status of Configuration Review made by the specified administrator/ operator as to whether the reviews are pending or completed, are presented in this report.
What are the different file formats, in which a report can be exported?
A report can be exported in either PDF or CSV format. You can also choose to mail a report and it will be sent as a PDF. To know more about how to generate a report, please click here .
Advanced Reports
No. Default advanced reports cannot be edited or deleted.
Advanced reports can be exported as PDF, CSV, or XLS.
Device details such as Backup Status, Baseline Conflict, Compliance Status, Credentials Status, Custom Column 1, Custom Column 2, Custom Column 3, Device Template, Device Type, End Of Sale Date, End Of Support Date, Host Name, IP Address, Image File Name, Last Backup at, Last Operation Status, MAC Address, Managed Status, Model, OS Type, OS Version, Protocol, Real-Time Change Detection, Serial Number, Series, Startup Conflict, System Description, System Location, and Vendor can be selected and generated as a report.
Security Aspects
How much security does Network Configuration Manager offer to my configuration?
Network Configuration Manager offers a good level of security to your configuration as all the configuration information retrieved from devices are encrypted and stored in DB. Also device credential information are also encrypted and stored in DB.
Can we install our own SSL certificate? How?
Yes, you can install your own SSL certificates in Network Configuration Manager. Please follow the steps below to do that:
If you are using keytool utilities for certificate generation
The Network Configuration Manager runs as a HTTPS service. It requires a valid CA-signed SSL certificate with the principal name as the name of the host on which it runs. By default, on first time startup, it creates a self signed certificate. This self signed certificate will not be trusted by the user browsers. Thus, while connecting to Network Configuration Manager, you need to manually verify the certificate information and the hostname of Network Configuration Manager server carefully and should force the browser to accept the certificate.
To make the Network Configuration Manager server identify itself correctly to the web browser and the user:
- you need to obtain a new signed certificate from a CA for the Network Configuration Manager host or
- you can configure an existing certificate obtained from a CA with wild-card principal support for the Network Configuration Manager host
Step 1: The first step is to create the public-private key pair that will be used for the SSL handshake
- Go to <Network Configuration Manager_Home>/jre/bin folder
- Execute the command "./keytool -genkey -alias Network Configuration Manager -keyalg RSA -keypass <privatekey_password> -storepass <keystore_password> -validity <no_of days> -keystore <keystore_filename>"
- The command will prompt you to enter details about you and your organization:
- For the 'first and the last name' enter the FQDN of the server running Network Configuration Manager
- For other fields enter the relevant information
- <keystore_password> is the password to access the keystore, <privatekey_password> is the password to protect your private key and <no_of_days> is the validity of the key pair in number of days, from the day it was created
- This will create a keystore file named <keystore_filename> in the same folder, with the generated key pair
Step 2: Create a Certificate Signing Request (CSR) for submission to a certificate authority to create a signed certificate with the public key generated in the previous step.
- Go to <Network Configuration Manager_Home>/jre/bin folder
- Execute the command "keytool -certreq -keyalg RSA -alias Network Configuration Manager -keypass <privatekey_password> -storepass <keystore_password> -file <csr_filename> -keystore <keystore_filename>"
- Note that the <csr_filename> that you choose should have .csr extension. The <privatekey_password>, <keystore_password> and <keystore_filename> are the ones used in the last step
- This will create a CSR file named <csr_filename> in the same folder
Step 3 : Submit the CSR to a Certificate Authority (CA) to obtain a CA signed certificate
- Some of the prominent CAs are Verisign (http://verisign.com), Thawte (http://www.thawte.com), RapidSSL (http://www.rapidssl.com). Check their documentation / website for details on submitting CSRs and this will involve a cost to be paid to the CA
- This process usually takes a few days time and you will be returned your signed SSL certificate and the CA's certificate as .cer files
- Save them both in the <Network Configuration Manager_Home>/jre/bin folder
Step 4: Import the CA-signed certificate to the Network Configuration Manager server
- Import your SSL certificate into your keystore
- Go to <Network Configuration Manager_Home>/jre/bin folder
- Execute the command "keytool -import -alias Network Configuration Manager -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <your_ssl_certificate>"
- <your_ssl_certificate> is the certificate you obtained from the CA, a .cer file saved in the previous step. The <privatekey_password>, <keystore_password> and <keystore_filename> are the ones used in the previous steps
- Now copy the <keystore_filename> to the <Network Configuration Manager_Home>/conf folder
Step 5: Finally, configure the Network Configuration Manager server to use the keystore with your SSL certificate
- Go to <Network Configuration Manager_Home>/conf folder
- Open the file server.xml
- Search for the entry 'keystoreFile', which will have the default value set to "conf/server.keystore". Change the value to "conf/<keystore_filename>" where <keystore_filename> is the one used in the previous steps
- Also search for the entry 'keystorePass' (which will infact be next to keystoreFile), which will have the default value set to "RGV2aWNlRXhwZXJ0". Change the value to "<keystore_password>" where <keystore_password> is the one used in the previous steps
- Restart the Network Configuration Manager server and connect through the web browser. If you are able to view the Network Configuration Manager login console without any warning from the browser, you have successfully installed your SSL certificate in Network Configuration Manager!
Note 1: Tomcat by default accepts only the JKS (Java Key Store) and PKCS #12 format keystores. In case, the keystore is of PKCS #12 format, include the following option in the server.xml file along with the keystore name,
keystoreType=”PKCS12″
This tells tomcat that the format is PKCS12. Restart the server after this change.
To configure existing wild card supported SSL certificate,
- Go to <Network Configuration Manager_Home>/conf folder
- Open the file server.xml
- Search for the entry 'keystoreFile', which will have the default value set to "conf/server.keystore". Change the value to "conf/<keystore_filename>" where <keystore_filename> is the one belong to the existing wild-card certificate.
- Also search for the entry 'keystorePass' (which will in fact be next to keystoreFile), which will have the default value set to "RGV2aWNlRXhwZXJ0". Change the value to "<keystore_password>" where <keystore_password> is the one used to protected the existing wild-card certificate keystore.
- Restart the Network Configuration Manager server and connect through the web browserconsole. If you are able to view the Network Configuration Manager login console without any warning from the browser, you have successfully installed your SSL certificate in Network Configuration Manager!
Note 2: Please refer your CA's documentation for more details and troubleshooting
If you are using OpenSSL / Microsoft Utilities
Follow these steps to enable using your own certificates :
- Generate the certificate signing request and generate the certificate using MS CA, as you did before (or use the cert generated before). DO NOT use the one generate using keytool
- Have tested here with the Base64 encoded certs, so use the same
- Download OpenSSL from here http://www.slproweb.com/download/Win32OpenSSL_Light-0_9_8e.exe and install it in your system
- After install, go to the OpenSSL\bin folder
- Copy the private key (generated with your CSR), your certificate and the root certificate into this bin folder
- Run this command on the command prompt : openssl pkcs12 -export -in <cert_file>.cer -inkey <private_key>.key -out <keystore_file>.p12 -name Network Configuration Manager -CAfile <root_cert_file>.cer -caname Network Configuration Manager -chain, where
- cert_file is the certificate with the .cer extention
- private_key is the private key file with a .key extension
- keystore_file is the keystore that will be generated with a .p12 or .pfx extension
- root_cert_file is the root certificate with a .cer extension
- provide extension to all the file entries on the command line
- When prompted for password, enter 'RGV2aWNlRXhwZXJ0'
- This will generate the keystore file <keystore_file>.p12 on the same folder
- Copy this file to <Network Configuration Manager_Install_Folder>\conf folder
- Move to <Network Configuration Manager_Install_Folder>\conf folder
- Open the file server.xml and do the following changes
- Search for the entry 'keystoreFile', which will have the default value set to "conf/server.keystore". Change the value to "conf/<keystore_file>.p12"
- Make sure the entry for 'keystorePass' is set to "RGV2aWNlRXhwZXJ0"
- Add a new entry keystoreType=”PKCS12″ next to the keystorePass entry
- Save the server.xml file
- Restart the Network Configuration Manager server and connect through the web browser. If you are able to view the Network Configuration Manager login console without any warning from the browser, you have successfully installed your SSL certificate in Network Configuration Manager!
I want to prevent unauthorized configuration changes to my core devices.
You can make use of the 'Change Management' feature of Network Configuration Manager. For more details refer to the section "Configuration Change Management " in help documentation.
ManageEngine ServiceDesk Plus Integration
Can we integrate NCM with ServiceDesk Plus while ServiceDesk Plus uses a third-party SSL certificate?
- Copy the sdp.keystore file from the SDP installation which is under the sdp\conf folder to OpManagerhome directory.
- We have to get the keypass and storepass used while generating the sdp.keystore file in Service Desk plus
You can open the file "server.xml" located under "‹SDP installed directory›\server\default\deploy\jbossweb-tomcat50.sar\" and see keypass & storepass, mostly keypass and storepass will be the same. - We have to identify the exact alias name used while generating sdp.keystore. You can get that by running the below command from the Network Configuration Manager administrative command prompt.
Execute below command from the Network Configuration Manager installed directory using command prompt with run as administrator:
\\ OpManager‹.\jre\bin\keytool -list -v -keystore sdp.keystore After executing the above command, you will get the alias name from the result. - Once you have the alias name, keypass and store pass, replace them in the below command and execute it.(which is the first part of ssl_servicedesk.bat), this will create a file called sdp_cert.txt
\\ OpManager>.\jre\bin\keytool -export -v -rfc -alias ‹asc› -file sdp_cert.txt -keystore .\conf\sdp.keystore -keypass ‹sdpsecured› -storepass ‹sdpsecured›
In the above command, we have to change the alias name(), keypass value() and storepass value () with the respective alias name, keypass and storepass values. - Execute the below command(second part of ssl_servicedesk.bat)
\\ OpManager>.\jre\bin\keytool -import -alias SDPSSL -keystore .\conf\ OpManager.truststore -file sdp_cert.txt -storepass OpManager -noprompt
Once it is done, go to to OpManager\bin directory and open the ssl_servicedesk.bat and do the below changes
Replace this line
%NMS_HOME%\jre\bin\keytool -export -v -rfc -alias asc -file sdp_cert.txt -keystore %NMS_HOME%/conf/sdp.keystore -keypass sdpsecured -storepass sdpsecured
with
%NMS_HOME%\jre\bin\keytool -export -v -rfc -alias ‹alias name› -file sdp_cert.txt -keystore %NMS_HOME%/conf/sdp.keystore -keypass ‹keypass value› -storepass ‹storepass value›
where ‹alias name›, ‹keypass value› and ‹storepass value› is the alias, keypass value and the storepass value that you used in fourth step.
Save the file and restart the OpManager service and verify the integration.
Can we integrate NCM with ServiceDesk Plus while ServiceDesk Plus uses a .pfx certificate?
Applying .pfx certificate in SDP does not involve creating keystore file which is required for integration. Please follow the below steps to create a Keystore file.
- Run the below command to convert pfx certificate to JKS format from OpManager\Jre\bin directory.
>keytool -importkeystore -srckeystore sdp_pfx_cert.p12 -destkeystore OpManager.truststore -srcstoretype pkcs12 -deststoretype JKS
It requires Destination password, give it as OpManager.
Source password which is the pfx certificate password. - Place the output file OpManager.truststore in OpManager_Home\conf folder. Also have a copy of this file named as sdp.keystore and place it in OpManager home directory.
- Try configuring SDP integration from Network Configuration Manager UI with sdp.keystore. No need to wait for the connection success message.
- Try configuring Log a Ticket notification.
If it fails, restart OpManager service and try once again.
Can we integrate NCM with any version of ServiceDesk Plus?
There are a few version-related restrictions when it comes to integrating ServiceDesk Plus with Network Configuration Manager. Please refer the table below to know the compatible version of Network Configuration Manager and SDP.
| ServiceDesk Plus version | Suggested NCM Version | Compatibility Status |
|---|---|---|
| 10513 and below | 124031-124096 | Compatible |
| 11000 - 11127 | 124097 and above | Compatible |
| 11128 - 11137 | 125214 and above | Compatible |
| 11138 and above | 125410 and above | Compatible |
On a general note, it is HIGHLY RECOMMENDED for users with SDP version 11.0 and above to integrate it with Network Configuration Manager version 125410 and above to ensure the integration runs smoothly and to avoid any sort of compatibility issues.
SSH Private Key Authentication
Which permission should private key files have?
In Linux, private key file should have permission 600 that denotes only users can perform read and write operation.
For Windows, if we generate a key pair, the file will contain "inherited privileges". Users have to remove them using "icacls" command and grant permission for Administrators and Systems.
How to change file permissions for private key file in Linux?
Use "chmod" command in terminal.
Example: chmod 600
How to view inherited privileges for private key in Windows?
Use "icacls" command in Command Prompt with Administrator privileges.
Example : icacls
How to remove inherited privileges for private key in Windows?
Use "icacls" command in Command Prompt with "Administrator" privilege.
Example : icacls/inheritance:r
How to grant inherited privileges for private key in Windows?
Use "icacls" command in Command Prompt with Administrator privileges.
Example : icacls/grant SYSTEM:(F)
icacls/grant BUILTIN\Administrators:(F)
Miscellaneous
I have enabled syslog-based change detection for my device. But the product does not seem to detect any configuration changes.
Configuration change messages will be generated only at certain logging levels. So check if the logging level in the device is set to one of the values listed in the "Syslog Config for Change Detection" - logging level drop-down. Also, ensure if syslog server is running and the syslog port (514) is free for Network Configuration Manager's use.
Has Network Configuration Manager been reviewed by any independant reviewers?
Yes. Network Configuration Manager has been reviewed by the following magazines/reviewers:
- SC Magazine, the world's longest running monthly publication focusing on information security has reviewed Network Configuration Manager.
- 3d2f, a web portal featuring reviews on software products has reviewed Network Configuration Manager. Report available here.
How to reduce the transactional log size (MSSQL database)?
Network Configuration Manager provides extensive workflow operations:
You will find a print to the following effect in the logs: Caused by: java.sql.SQLException: The transaction log for database 'OpManagerDB' is full. To find out why space in the log cannot be reused, see the log_reuse_wait_desc column in sys.databases..
To check the used % : DBCC SQLPERF(LOGSPACE)
Steps to clear the logs:
- Shutdown Network Configuration Manager server.
- Change the Recovery Model to Simple by following the steps below:
- Go to SQL server-->OpManagerDB properties-->Options-->Recovery Model-->Simple.
- Connect to MSSQL Server-->OpManagerDB. Execute the following query
- DBCC SHRINKDATABASE (database name , target percent) for eg DBCC SHRINKDATABASE (OpManagerdb,20)
- alter database
MODIFY FILE (Name = " _log",MAXSIZE=1 GB) - for eg alter database OpManagerdb MODIFY FILE (Name = "OpManagerdb_log",MAXSIZE=1 GB) (If the transaction log is too huge without any backup, it can not be shrunk. So run this query and then follow the above steps.
- Restart Network Configuration Manager server.
Ensure you upgrade to the latest build.
If you still get transaction logs filled up issue, check if you have free disk space where the database and transaction log files are saved.
If the drives are filled up, move them to different drive.