Role Based Access Control Tools
Role based access control (RBAC) is the process of restricting user access to network configurations and resources and provides RBAC security. In role based access control, RBAC solutions are provided to users who are assigned roles depending on the resources they need access to. All other parts of the network are rendered inaccessible to them, ensuring no unauthorized accesses or changes are made to network resources.
Example of How Role Based Access Control Works
Network Configuration Manager, also known as RBAC software or RBAC tool, comes with two predefined role based access controls that restrict users from accessing certain devices or device groups under role based access control feature.
| Access level (role) | Definition |
|---|---|
| Administrator | These users have privileges to access, edit, and push configurations to any device. Only administrators can add devices to the inventory, add users, assign roles, and assign devices. In addition, administrators can approve or reject requests pertaining to configuration uploads (pushing configurations) by operators. |
| Operator | These users have privileges to access and edit configurations of specified devices. They can also send requests for configuration uploads (pushing configurations) to administrators. |
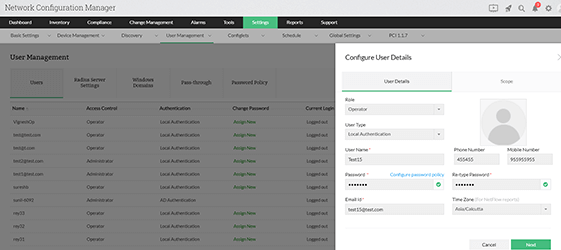
Why RBAC and configuration approval in Network Configuration Manager are so important
Since Network Configuration Manager runs on a multi-user network environment, it's vital to restrict user access to network devices using a RBAC system. A faulty change to the network can lead to network issues, which can cause either a network disaster or a full-blown network outage. Reversing such outages can be time-consuming, which is why all changes should be checked and approved by network admins and role based access control is necessary..
Role based access control (RBAC) example
Role-based access control helps you define the scope of access for users so you can control what changes they can make to the network. Let's say a user is assigned to the Cisco device group as an operator in Network Configuration Manager. The operator can view the status of all devices in the device group, schedule backups, and request changes.
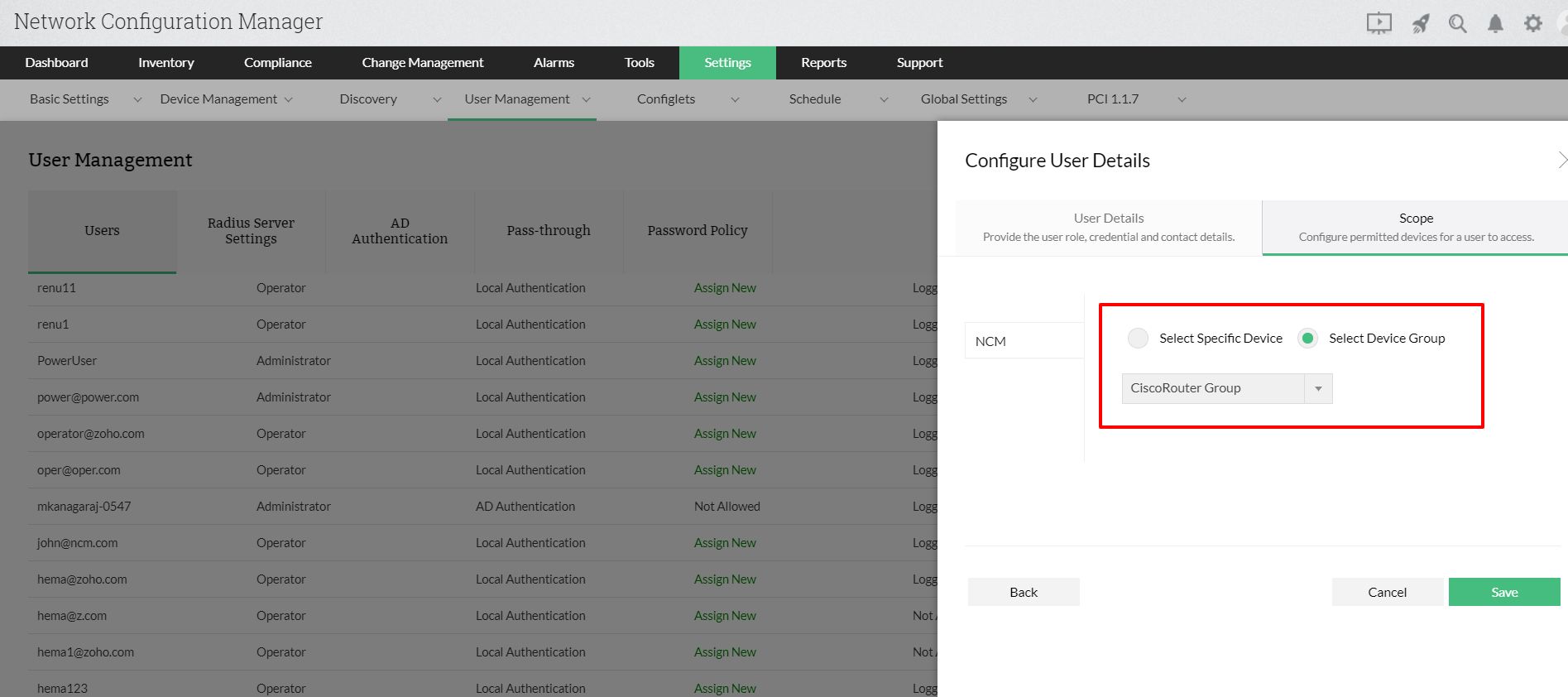
When the operator requests a configuration upload, the admin receives a notification. The admin can compare configuration drafts with the baseline configuration of the devices. The admin can choose to accept or reject configuration uploads with appropriate comments. Once the changes have been processed, operators receive notifications with the admin's comments.The entire process of RBAC configuration of change approval mechanism under role-based access control helps maintain control over what goes on in your network devices.
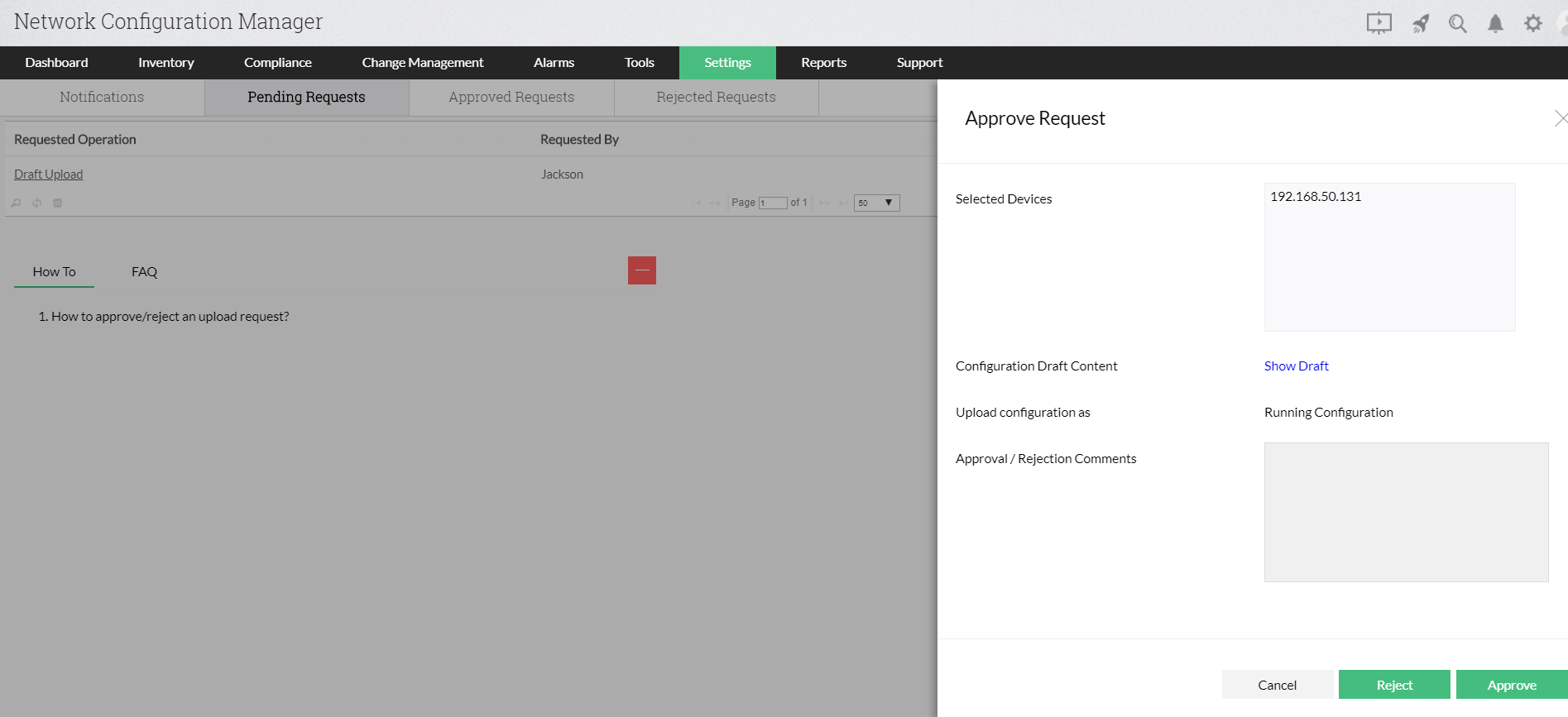
Network Configuration Manager offers advanced configuration change management functionalities like Diff View, real-time change detection and notifications. Get started with securing your network from configuration change mishaps and outages with your free trial of Network Configuration Manager.
Customer reviews
Case Studies - Network Configuration Manager
FAQs about Role Based Access Control (RBAC) Tools
1. What is role based access control (RBAC)?
+2. Why is role based access control important?
+3. How to use role based access control?
+4. How does role-based access control (RBAC) work?
+5. How RBAC improve cyber-security ?
+

