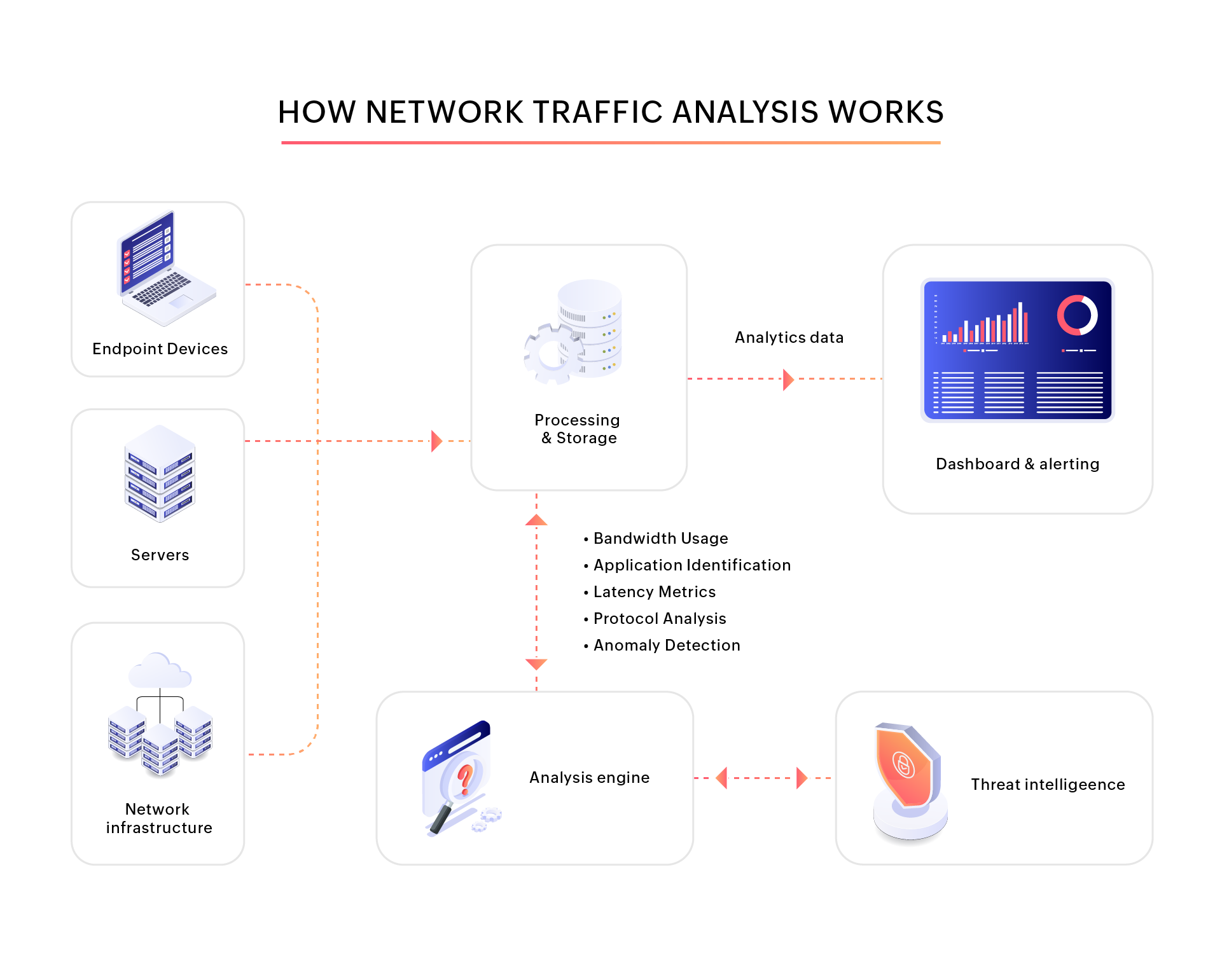
Challenges in network traffic analysis
Despite its clear advantages, network traffic analysis (NTA) is not without challenges. The scale and complexity of modern networks introduce obstacles that can make analysis difficult without the right tools and strategies in place. From data overload to encrypted traffic, IT teams must navigate a range of hurdles to extract meaningful insights.
1. Data overload
Today’s networks generate staggering amounts of flow records and packet data. With thousands of devices, SaaS applications, and remote endpoints contributing traffic, the sheer volume of telemetry can overwhelm traditional monitoring systems. Without advanced filtering, baselining, and analytics, teams may struggle to separate actionable insights from background noise.
2. Encryption visibility
The widespread adoption of TLS 1.3, VPN tunnels, and encrypted application traffic has dramatically reduced what deep packet inspection (DPI) can reveal. While encryption is essential for privacy and compliance, it also blinds security and operations teams to what’s happening inside the traffic flows. Solutions must now rely on metadata, flow patterns, and fingerprinting techniques to maintain visibility without compromising security.
3. Alert fatigue
Even the most capable NTA systems can become a burden if they are not tuned correctly. Poorly configured thresholds often generate floods of false positives, burying real threats under a pile of low-value alerts. This leads to alert fatigue, where teams either ignore alerts altogether or miss critical incidents. Intelligent baselining, machine learning models, and context-aware correlation are now necessary to ensure that alerts remain meaningful.
4. Integration complexity
NTA data delivers the most value when it is connected to the broader IT ecosystem. Integration with SIEM platforms strengthens security correlation, ITOM tools expand infrastructure visibility, and AIOps platforms enable predictive analytics. Building these connections is not always straightforward, since systems often rely on different data formats. Achieving full alignment requires planning, governance, and in some cases, custom connectors.
Selecting the right NTA platform often comes down to how well it can overcome these limitations with features like AI-driven filtering, scalable analytics, and tight ecosystem integrations.