SIEM platforms are central to threat detection and compliance, but they often lack visibility into what’s happening inside applications. Critical signals such as application alarms, performance anomalies, configuration changes, and user access events remain trapped in APM tools, creating blind spots for security teams.
Without application-level data, SIEM correlations miss early indicators of attacks like unauthorized access, performance based exploits, or suspicious configuration changes. Investigations slow down, alerts lack context, audits become manual, and teams struggle with higher MTTR, alert fatigue, and increased compliance risk across standards such as GDPR, HIPAA, and SOC 2.
Applications Manager closes this gap by integrating directly with SIEM platforms that support Syslog including Splunk, Microsoft Sentinel, and ManageEngine Log360. It forwards application alarms, audit logs, and access logs in real time, enriching SIEM with deep performance and operational context. The result is faster threat detection, more accurate event correlation, streamlined incident response, and simplified compliance reporting, all from a unified view of application behaviour and risk.
Real time forwarding of application alarms and logs gives SIEM tools immediate visibility into abnormal application behaviour. Performance anomalies, unauthorized access attempts, and suspicious activity are detected early, allowing SOC and SecOps teams to act before issues escalate into security incidents or outages.
Centralizing APM audit logs and access logs in SIEM creates a complete, tamper-resistant record of configuration changes, privileged actions, and user activity. Security and compliance teams can quickly identify risky modifications, detect failed login spikes or privilege misuse, and investigate incidents with confidence, without relying on fragmented log sources.
Enriching SIEM events with application performance data provides critical context during investigations. By correlating security signals with response time degradation, error rates, or throughput anomalies, teams can distinguish attack-driven incidents from operational issues, reduce false positives, and significantly lower mean time to respond (MTTR).
Combining application data with infrastructure, network, and identity events expands the SIEM detection surface. This enables more accurate correlation, reduces alert noise, and helps uncover complex, multi-stage attacks that siloed data sources often miss.
Application-aware SIEM alerts enable automated response workflows based on both security and performance signals. This reduces manual triage, minimises alert fatigue, and helps incident response teams contain threats quickly, before business impact increases.
Centralized, immutable application logs in SIEM provide a single source of truth for investigations and compliance. Long-term log retention supports forensic analysis, regulatory audits (GDPR, HIPAA, SOC 2), and legal inquiries, without the overhead of manual evidence collection.
By unifying application monitoring data with SIEM, Applications Manager bridges the gap between SecOps, DevOps, and SRE teams. A shared, contextual view of application behaviour improves collaboration, shortens resolution cycles, and enables faster, better-informed decisions during incidents.
If you use Splunk for log analysis and security monitoring, Applications Manager integrates seamlessly to forward application alarms, access logs, and audit logs directly into Splunk.
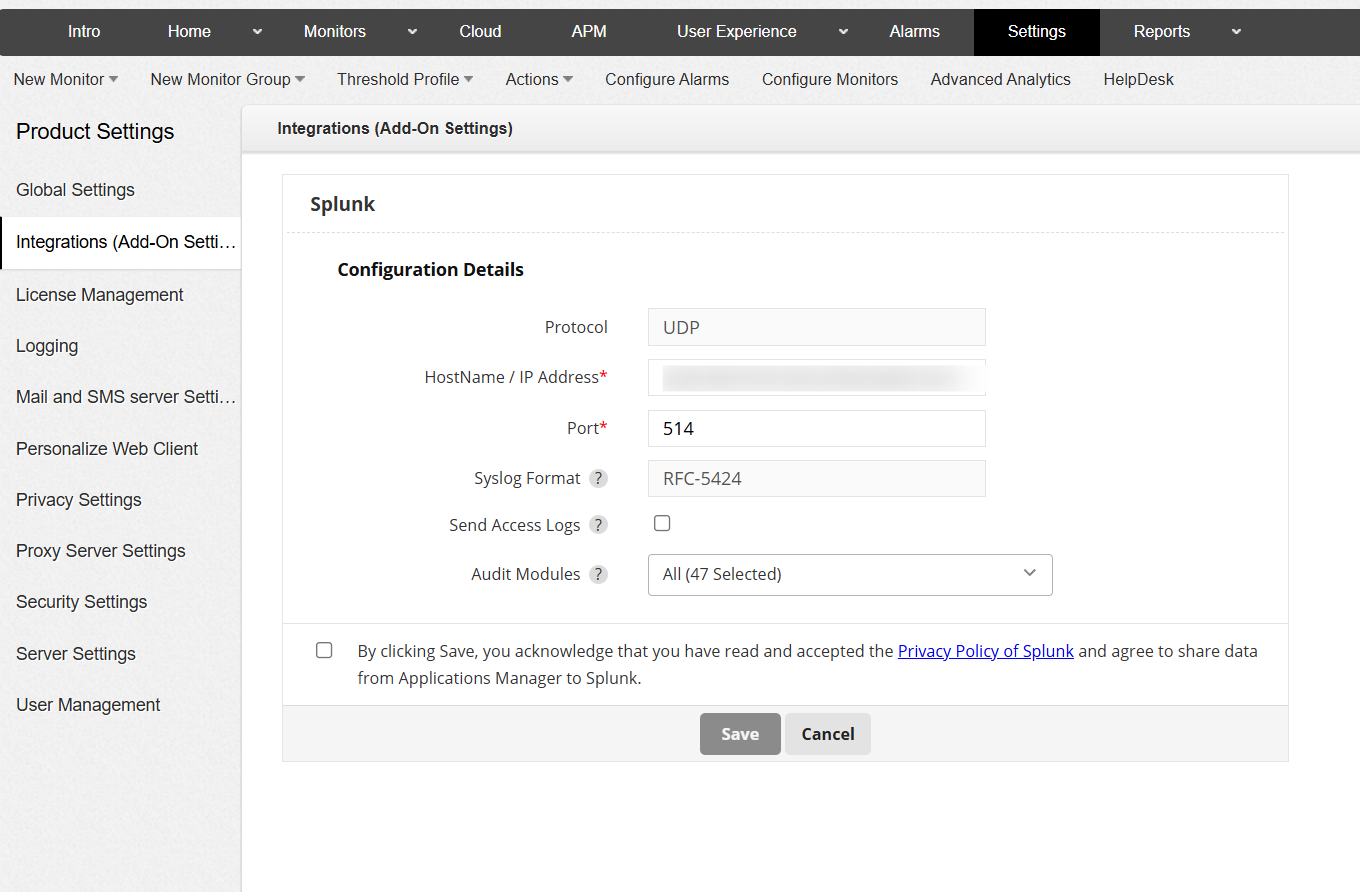
By combining Applications Manager’s deep application and infrastructure monitoring with Splunk’s powerful event correlation and analytics, you gain end-to-end visibility across on-premises, cloud, and hybrid environments, helping you monitor performance, detect threats earlier, and respond faster with confidence.
Stream application logs and security events to your SIEM and gain actionable insights from a unified monitoring platform. Download a 30-day free trial and simplify SIEM integration using Applications Manager.
It allows us to track crucial metrics such as response times, resource utilization, error rates, and transaction performance. The real-time monitoring alerts promptly notify us of any issues or anomalies, enabling us to take immediate action.
Reviewer Role: Research and Development
Trusted by over 6000+ businesses globally