Correlation is the process of analyzing different events that happen in a sequence and identifying the relationship between them. Correlating the events happening in your network can provide a better context of the incident which would've been missed out while looking at an individual level.
For example, a single password failure is a normal event. But a hundred failures followed by a successful login within a minute can indicate a potential breach.
Correlation rules in Log360 Cloud is an expression that allows users to define the sequences of events which could indicate an anomaly or a security loophole.
The following image illustrates the parameters in a correlation rule:
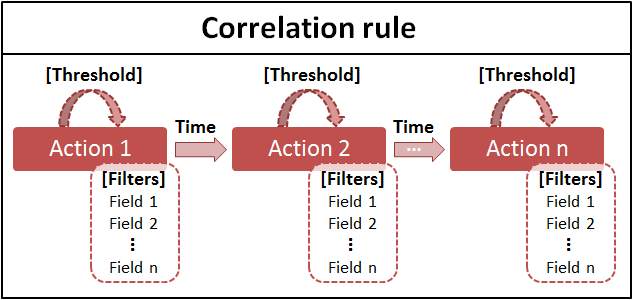
Action - Any event that happens in the network. For example, a failed logon.
Time window between the actions - Indicates the time gap between the different events specified in the logical sequence.
Threshold - The minimum number of times the action must occur within the specified time window.
Filters - Allows users to specify the conditions for each action. For example, you can include the range of IP addresses you need to monitor in the network