This tutorial is aimed at helping you tighten your Windows security and proactively preventing performance degradation by identifying and monitoring critical Windows Events.
The tutorial is made available in two parts, with this first part covering topics focussed on what you need to know as a beginner about Event Logs and why they need to be watched. If you are a seasoned administrator or a network engineer, move on to part II and learn to set up Event Logs monitoring.
Event logs are local files recording all the 'happenings' on the system and it includes accessing, deleting, adding a file or an application, modifying the system's date, shuting down the system, changing the system configuration, etc. Events are classified into System, Security, Application, Directory Service, DNS Server & DFS Replication categories. Directory Service, DNS Server & DFS Replication logs are applicable only for Active Directory. Events that are related to system or data security are called security events and its log file is called Security logs.
The following sections provide more details on Windows Event Logs and what mandates their monitoring:
The Event logs are broadly classified into few default categories based on the component at fault. The different components for which events are logged include the system, the system security, the applications hosted on the system etc. Some applications log events in a custom category instead of logging them into the default Applications category.
| Event Log Type | Description |
|---|---|
| Application Log | Any event logged by an application. These are determined by the developers while developing the application. Eg.: An error while starting an application gets recorded in Application Log. |
| System Log | Any event logged by the Operating System. Eg.: Failure to start a drive during startup is logged under System Logs |
| Security Log | Any event that matters about the security of the system. Eg.: valid and invalid Logins and logoffs, any file deletion etc. are logged under this category. |
| Directory Service log | records events of AD. This log is available only on domain controllers. |
| DNS Server log | records events for DNS servers and name resolutions. This log is available only for DNS servers |
| File replication service log | records events of domain controller replication This log is available only on domain controllers. |
Each event entry is classified by Type to identify the severity of the event. They are Information, Warning, Error, Success Audit (Security Log) and Failure Audit (Security Log).
| Event Type | Description |
|---|---|
| Information | An event that describes the successful operation of a task, such as an application, driver, or service. For example, an Information event is logged when a network driver loads successfully. |
| Warning | An event that is not necessarily significant, however, may indicate the possible occurrence of a future problem. For example, a Warning message is logged when disk space starts to run low. |
| Error | An event that indicates a significant problem such as loss of data or loss of functionality. For example, if a service fails to load during startup, an Error event is logged. |
| Success Audit (Security log) | An event that describes the successful completion of an audited security event. For example, a Success Audit event is logged when a user logs on to the computer. |
| Failure Audit (Security log) | An event that describes an audited security event that did not complete successfully. For example, a Failure Audit may be logged when a user cannot access a network drive. |
The Event Viewer lists the event logs like this:
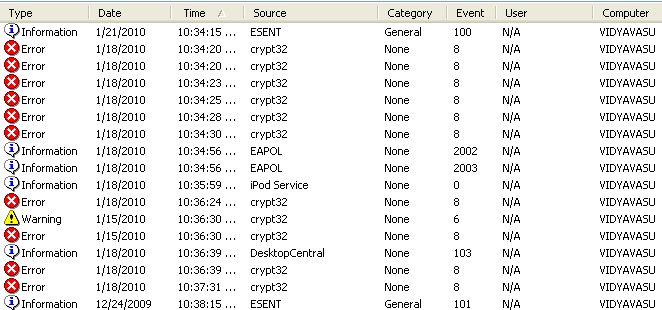
Events are listed with Header information and a description in the Event Viewer.
| Header | Description |
|---|---|
| Date | The date the event occurred |
| Time | The time the event occured |
| User | The user who has logged onto the computer when the event occurred |
| Computer | The computer where the event occurred |
| Event ID | An event number that identifies the event type. Helps to know more about the event |
| Source | The source which generated the event. It could be an application or system component |
| Type | Type of event (Information, Warning, Error, Success Audit and Failure Audit) |
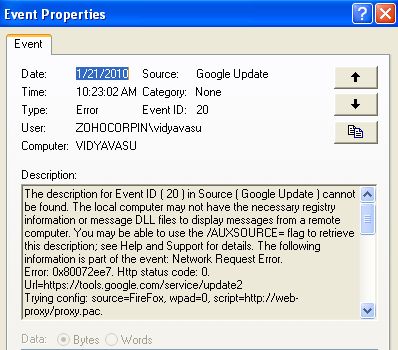
Double-click an event to see the details:
Security is the biggest concern every business faces today. Incidents like hacks and data thefts are continuously on the rise, exposing all segments of business to risks and leaving the administrators red-eyed. Various industrial researches reveal that majority of the hacks and thefts take place due to illegal authentication attempts. Auditing illegal or failed login attempts could prevent (or reduce) data thefts.That said, it is important that we know what an operating system can provide by way of security and what we must do to implement operating systems with the required security.
Events are not logged by default for many security conditions which means that your resources are still exposed to hacks.You have to configure audit policies to audit the security events and log them.Critical security events that need auditing:
It is not necessary to configure all the audit policies. Doing so would result in logging for each and every action that take place and will increase the log size. The logs roll-over and depending the size of the roll-over configured, the older logs are deleted. Configuring the right policies that are really critical to your environment will improve the security.
Auditing critical events are enabled by default for domain controllers. For the other Windows devices, configure the audit policies available under Local Security Settings. The audit policies available are:
The need to adhere to security compliances such as SOX, HIPAA etc for the publicly traded companies, health care industry etc, necessitates implementing security management process to protect against attempted or successful unauthorized access. Securing the information on your network is critical to your business with or without having to comply to some standards. Windows event logs is one of the sources using which the login attempts can be tracked and logged. A manual check on every Windows device is tedious and impossible and warrants automated auditing and monitoring of event logs on a regular basis.
Enabling Security Audit in Windows